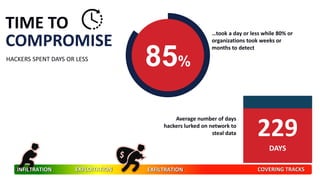
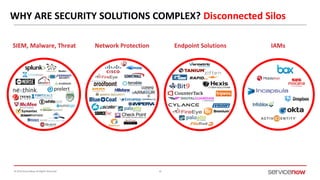
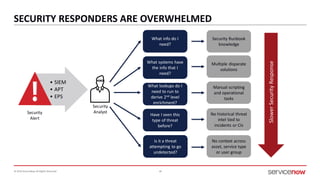
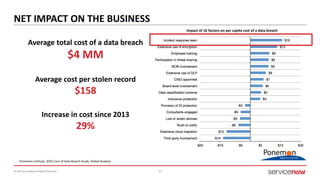
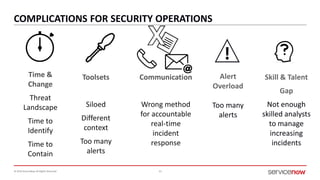
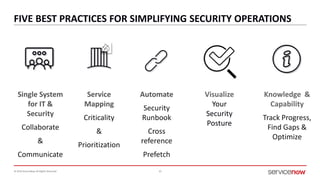
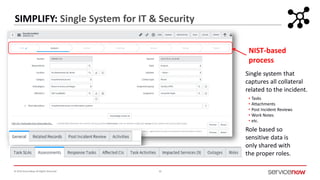
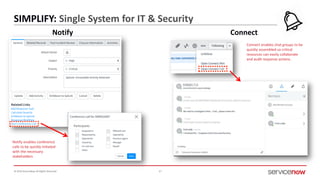
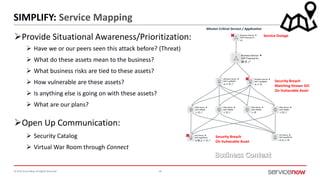
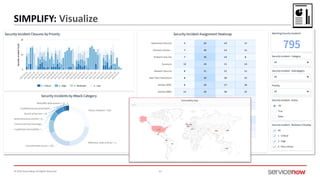
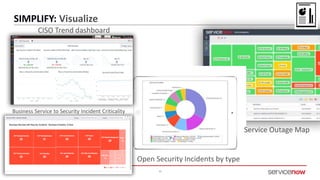
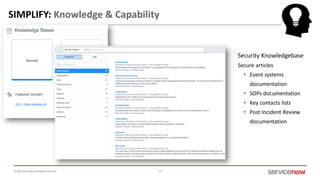
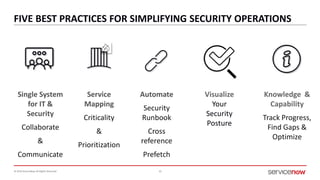
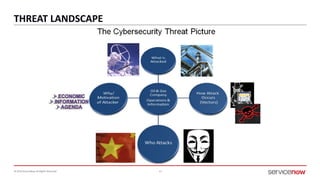
The document outlines a presentation by Bryce Schroeder on simplifying security operations within enterprises. It highlights the complexities security teams face, including the need for streamlined communication and standardized processes to improve incident response times. Five best practices are proposed for enhancing security operations, including using a single system for IT and security, automating security runbooks, and visualizing security postures.




![© 2016 ServiceNow All Rights Reserved 12
days on average to spot a breach
Mean Time to Identify [MTTI]
days to contain
Mean Time to Contain
[MTTC]](https://image.slidesharecdn.com/servicenowdecemberwebcast-simplifysecurityoperations-161202150406/85/ServiceNow-Webinar-12-1-Simplify-Security-Operations-Detect-Prioritize-and-Respond-9-320.jpg)