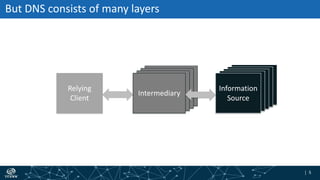
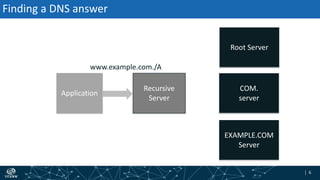
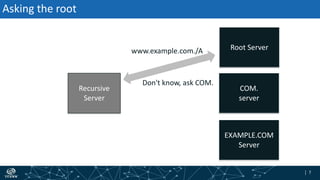
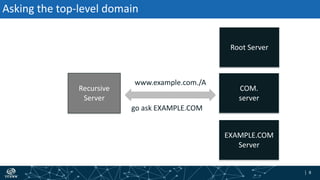
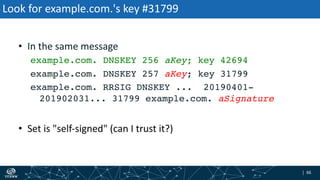
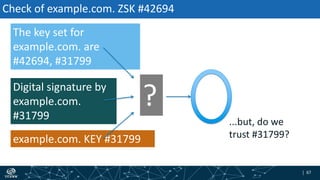
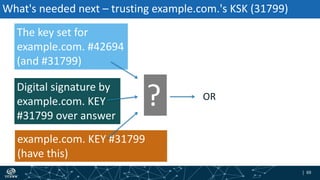
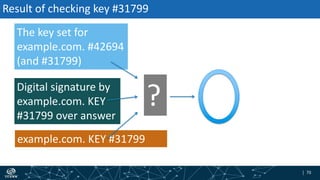
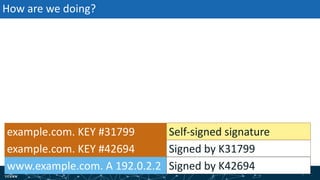
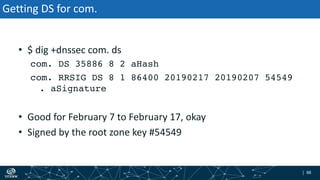
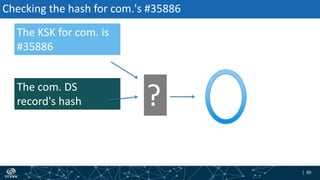
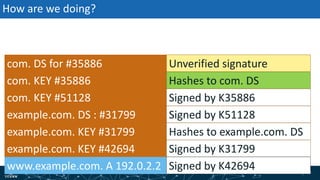
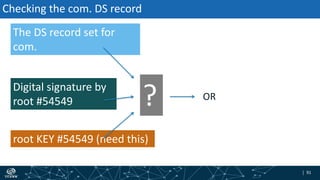
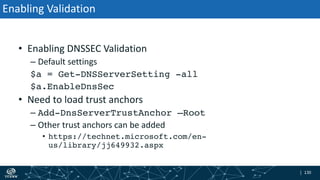
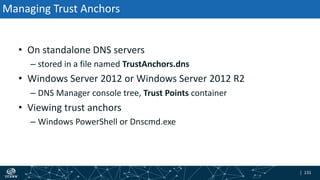
The document provides an overview of DNSSEC validation including:
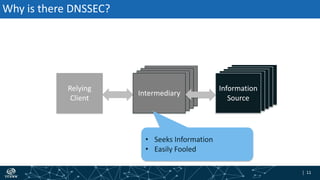
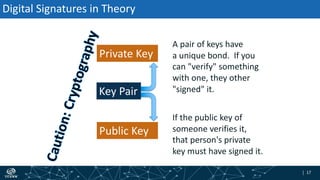
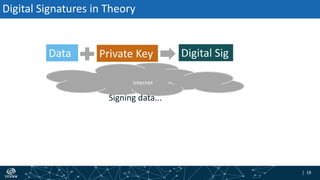
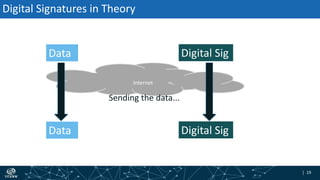
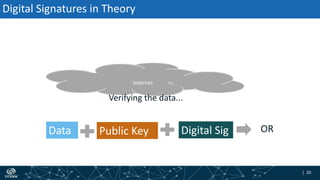
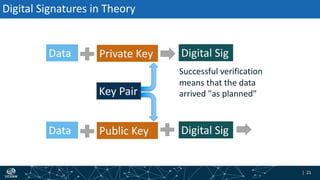
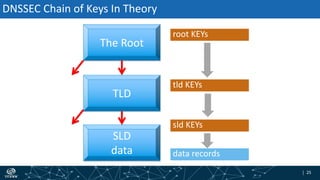
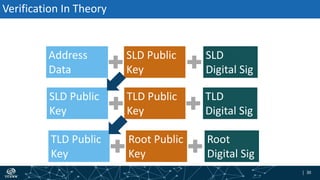
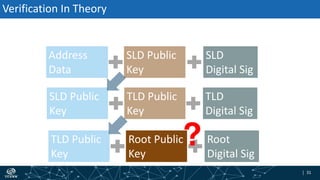
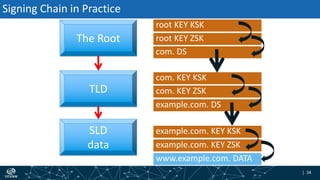
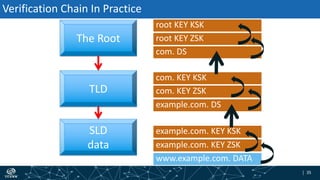
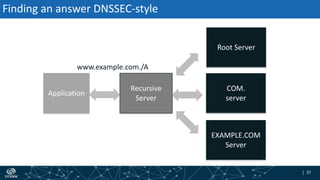
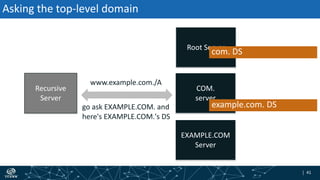
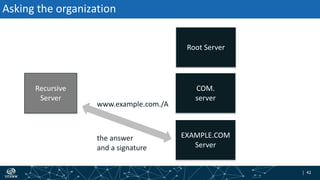
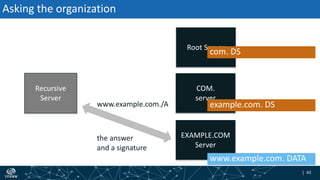
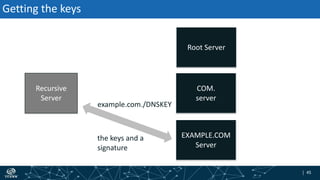
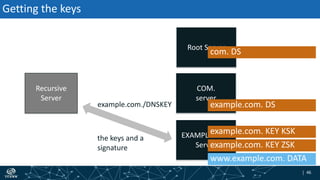
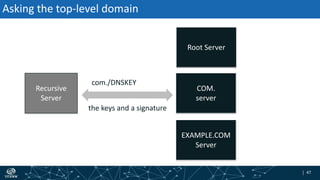
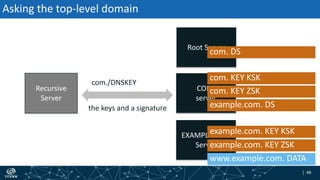
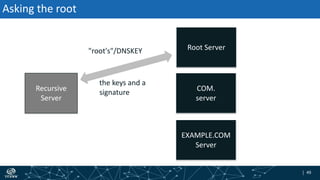
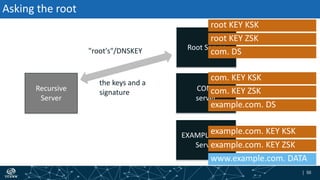
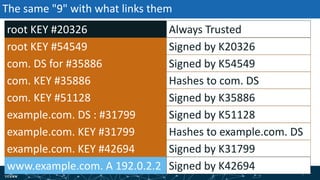
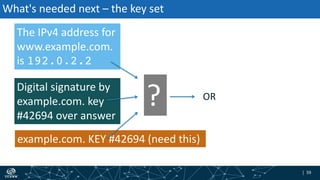
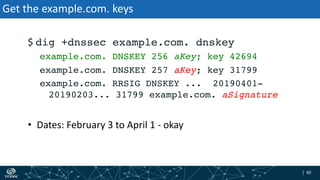
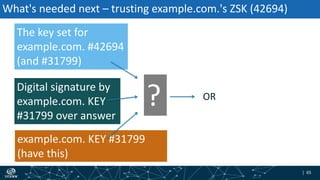
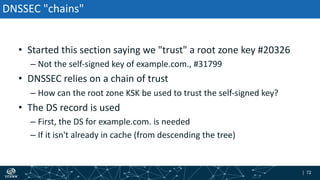
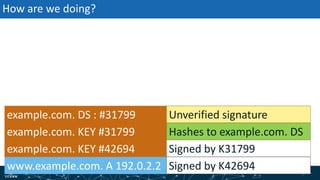
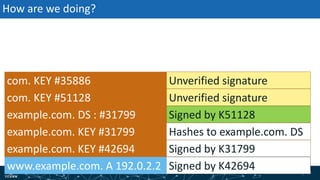
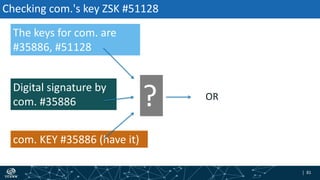
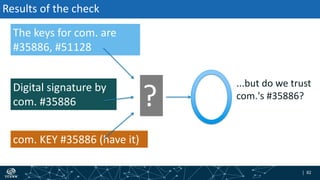
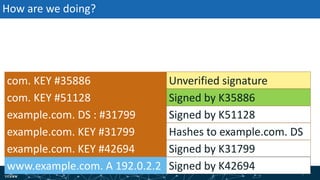
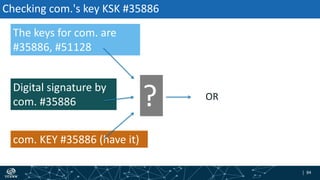
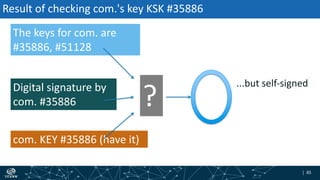
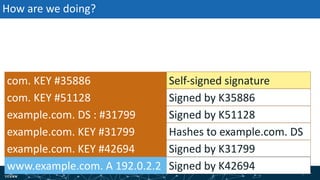
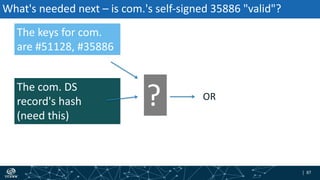
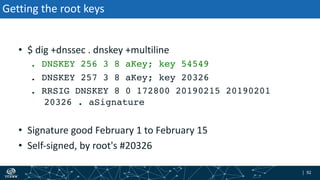
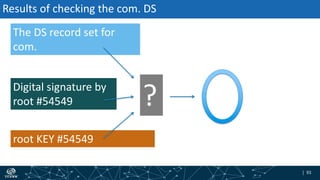
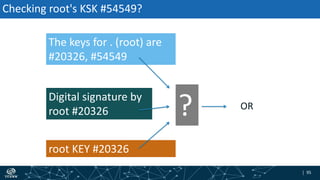
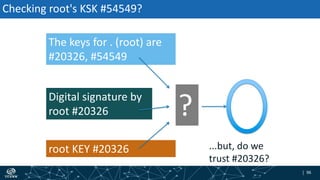
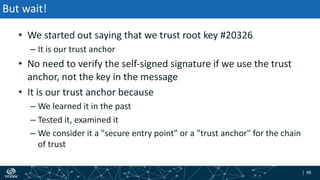
- How DNSSEC uses digital signatures and a chain of trust to validate DNS records and ensure they have not been tampered with.
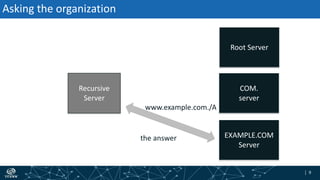
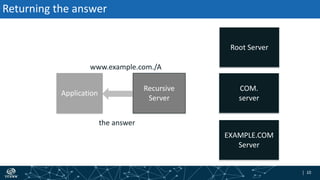
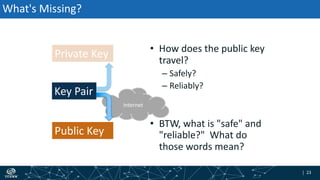
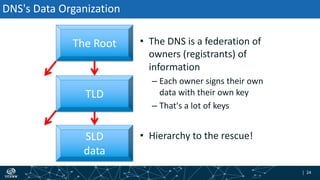
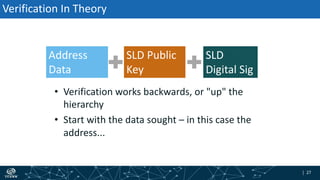
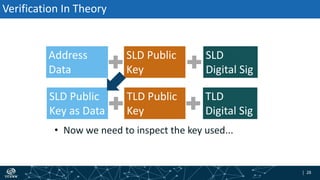
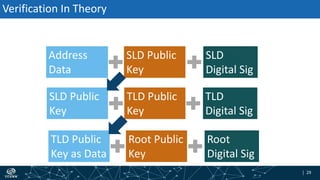
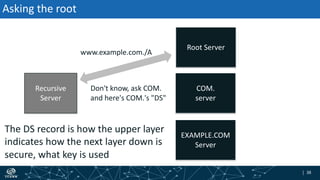
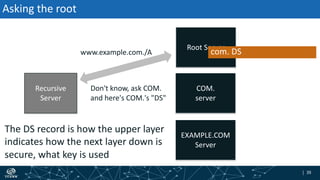
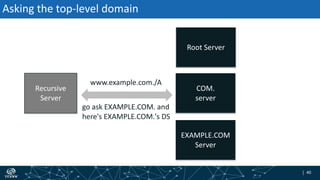
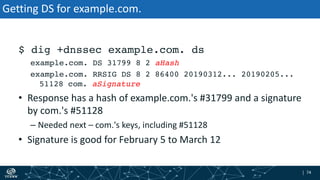
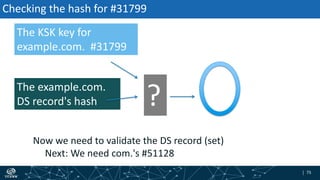
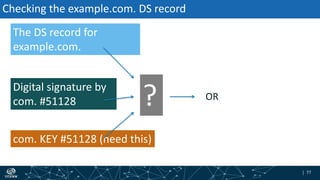
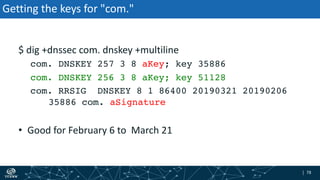
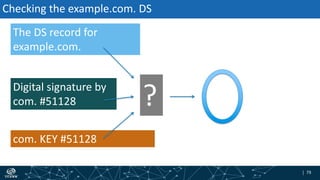
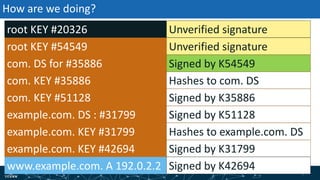
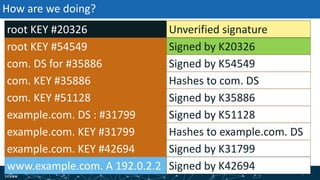
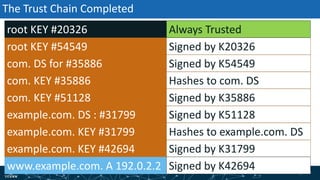
- The process of validation works by verifying signatures up the DNS hierarchy from the data record to the root zone using public/private key pairs.
- The roles of different record types like DNSKEY, DS, and their use in establishing the chain of trust during validation.