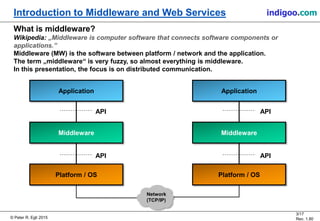
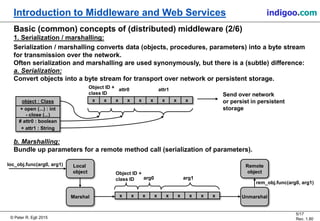
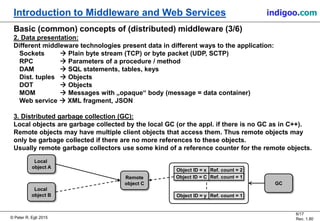
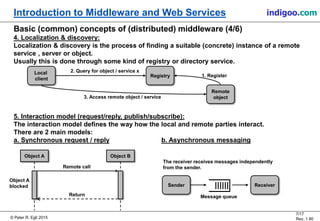
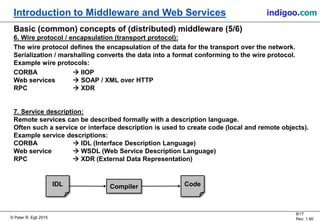
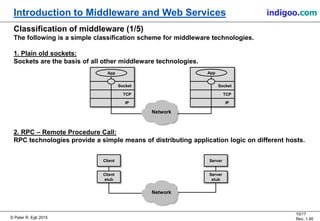
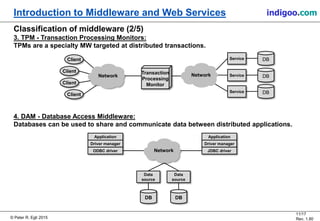
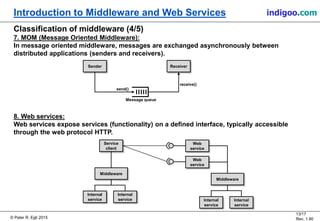
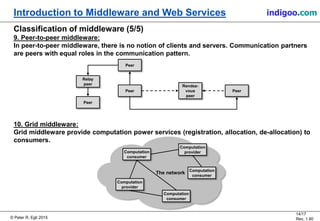
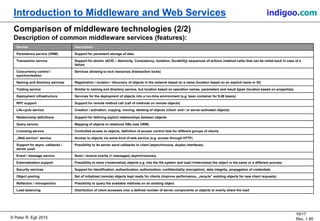
This document provides an introduction to middleware and web service concepts. It defines middleware as software that connects software components across platforms and networks. The document then discusses key concepts of distributed middleware including serialization, data presentation, distributed garbage collection, localization and discovery, interaction models, wire protocols, service descriptions, target domains, and platform dependence. It also provides a classification of various middleware technologies such as RPC, transaction processing monitors, database access middleware, distributed tuples, distributed object technology, message-oriented middleware, web services, peer-to-peer middleware, and grid middleware. Finally, it compares some concepts across different middleware technologies.