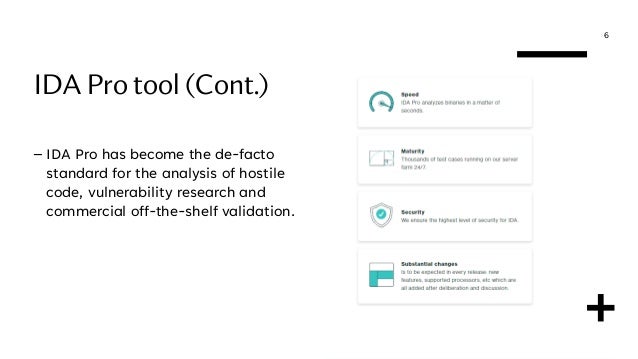
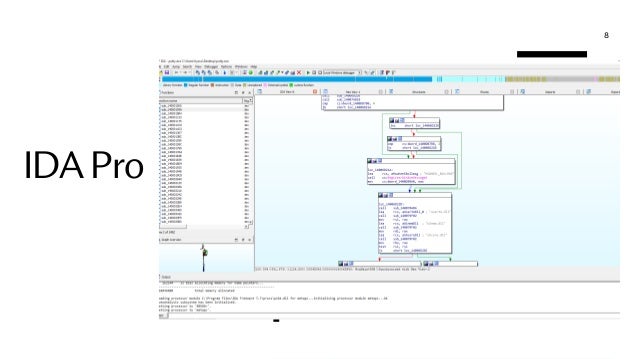
This document defines and compares disassemblers, debuggers, and decompilers. It then discusses the IDA Pro tool in more detail. A disassembler translates machine code back to assembly code, enabling static code analysis. A debugger also disassembles code but allows controlled execution and dynamic analysis. A decompiler translates machine code into high-level code. The document recommends IDA Pro as a powerful disassembler and debugger that has become a standard for reverse engineering. It also briefly mentions the open-source x64dbg debugger as an alternative.