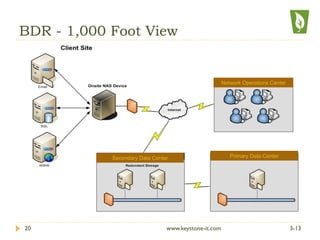
This document discusses IT disaster recovery plans for medical practices. It covers business continuity and data backup, HIPAA regulatory concerns regarding protected health information, scenarios involving data loss, and the importance of having a disaster recovery plan. It recommends a backup and disaster recovery (BDR) server solution that provides on-site and off-site backups with encryption to protect data and allow restoration in the event of a disaster. Key factors to consider with any disaster recovery solution include recovery timelines, backup frequency, data security, and support availability.