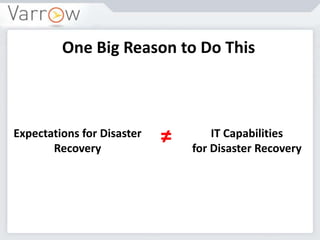
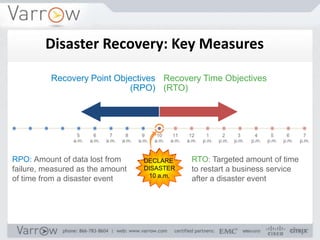
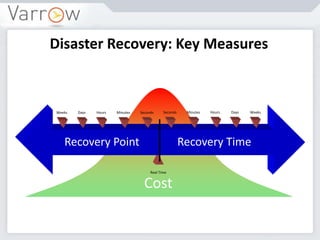
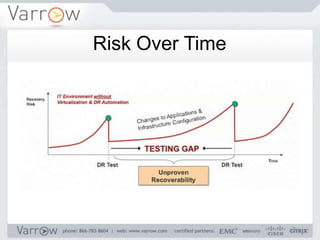
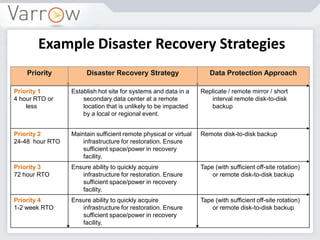
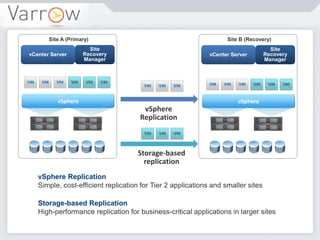
This document discusses disaster recovery strategies and approaches. It begins by defining what constitutes a disaster and differentiating between disaster recovery and operational recovery. It then examines common disaster risks and threats. The document outlines a disaster recovery approach that includes business impact analysis, identifying risks and gaps, establishing recovery strategies and objectives, implementing capabilities, and developing documentation and test procedures. Key measures for disaster recovery like recovery point objectives and recovery time objectives are explained. Various disaster recovery strategies are presented based on priority tiers. Finally, the document discusses technologies that can be used to enable disaster recovery capabilities like replication, remote sites, and recovery management tools.