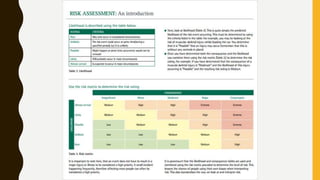
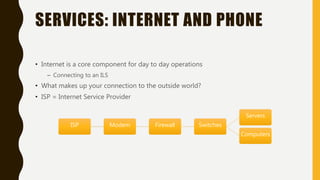
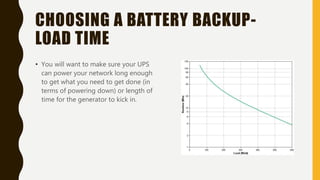
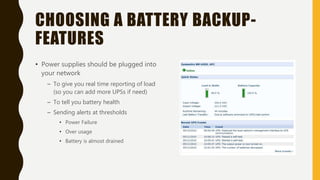
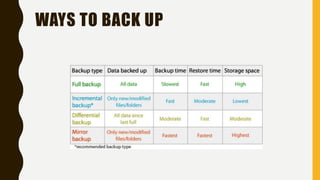
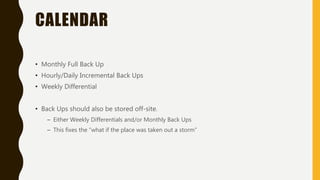
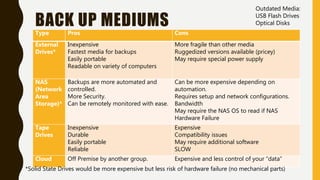
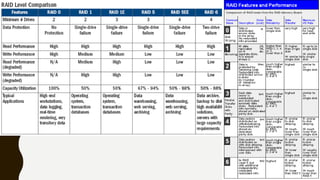
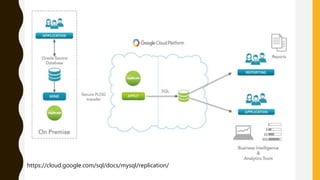
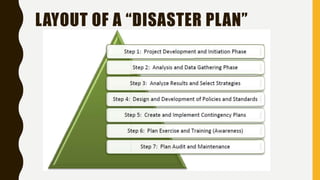
The document outlines essential components of disaster recovery plans for libraries, identifying various threats such as natural disasters, cyber incidents, and human errors, alongside strategies for mitigating risks. Key elements emphasized include active monitoring, robust backup systems, redundancy, and regular testing to ensure systems can withstand incidents effectively. Moreover, the document highlights the significant financial impact of data loss and the critical nature of planning for business continuity.