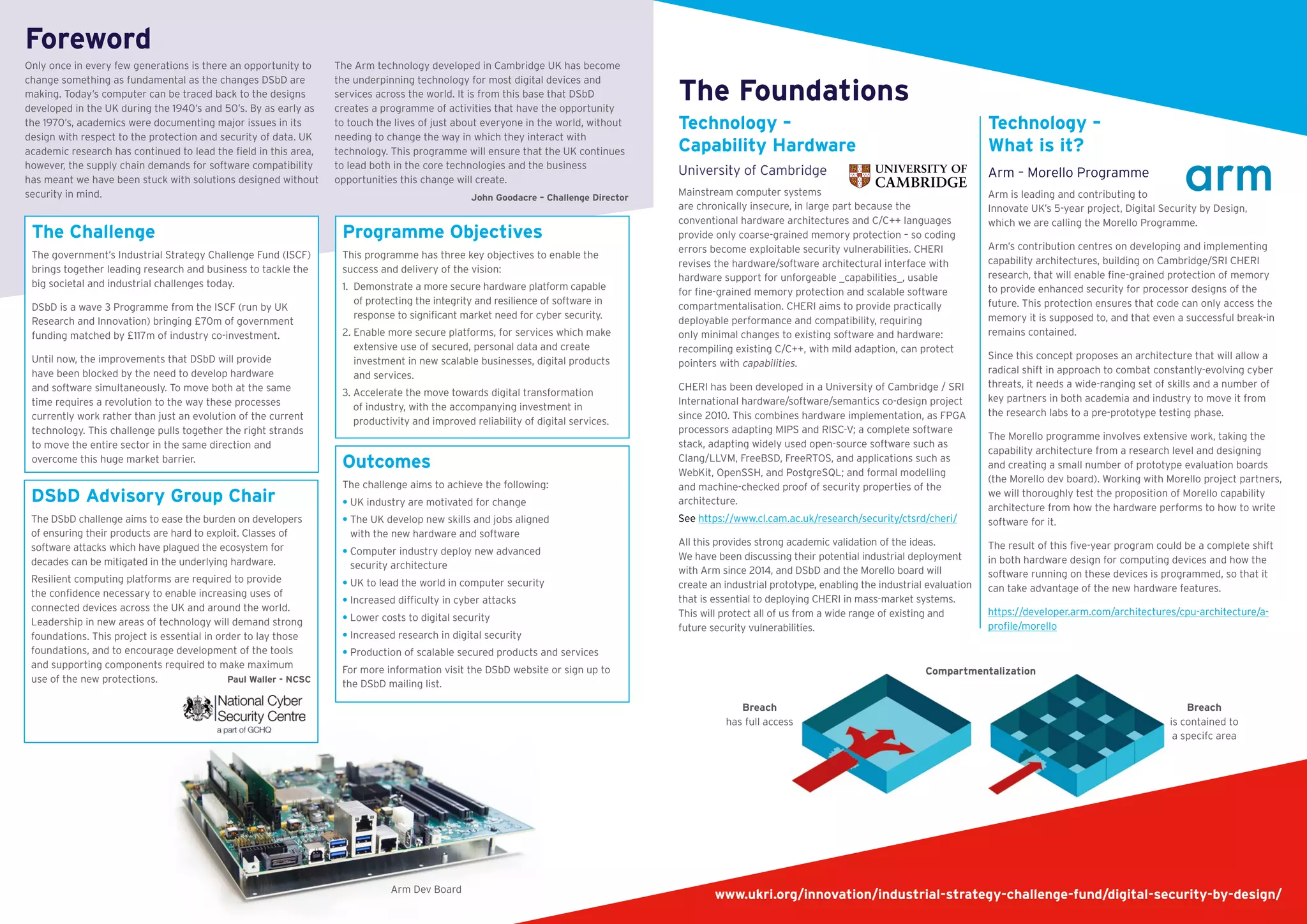
The Digital Security by Design (DSBD) initiative aims to transform the digital computing landscape by creating a secure hardware and software ecosystem supported by £70 million in government funding, complemented by £117 million from industry. The program seeks to address cybersecurity challenges by developing a more secure hardware platform and enabling the deployment of advanced security architectures, fostering innovation in digital products and services while ensuring the UK maintains a leadership role in cybersecurity. Key objectives include reducing the exploitation of software vulnerabilities, enhancing the resilience of connected devices, and advancing digital transformation across industries.