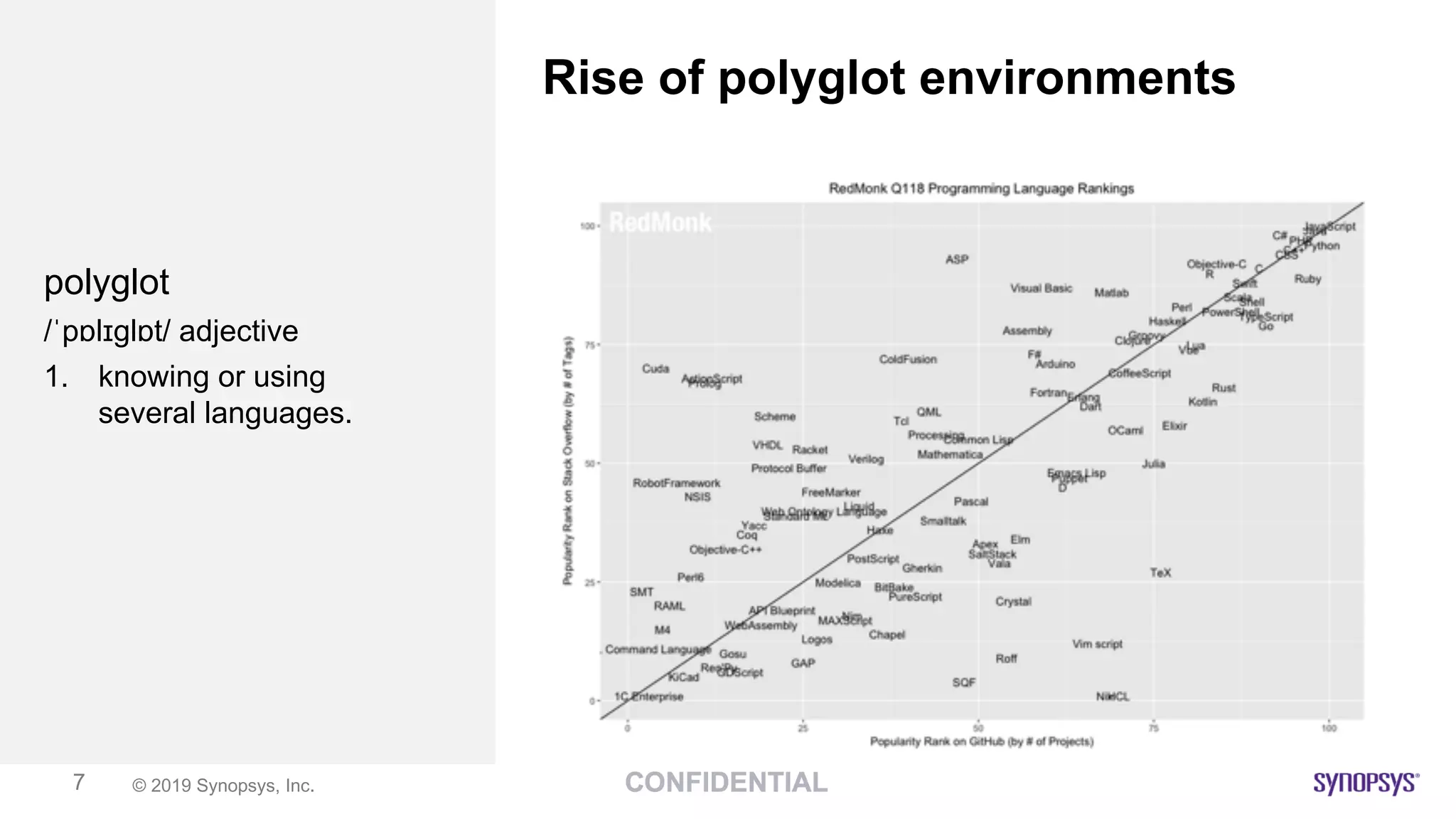
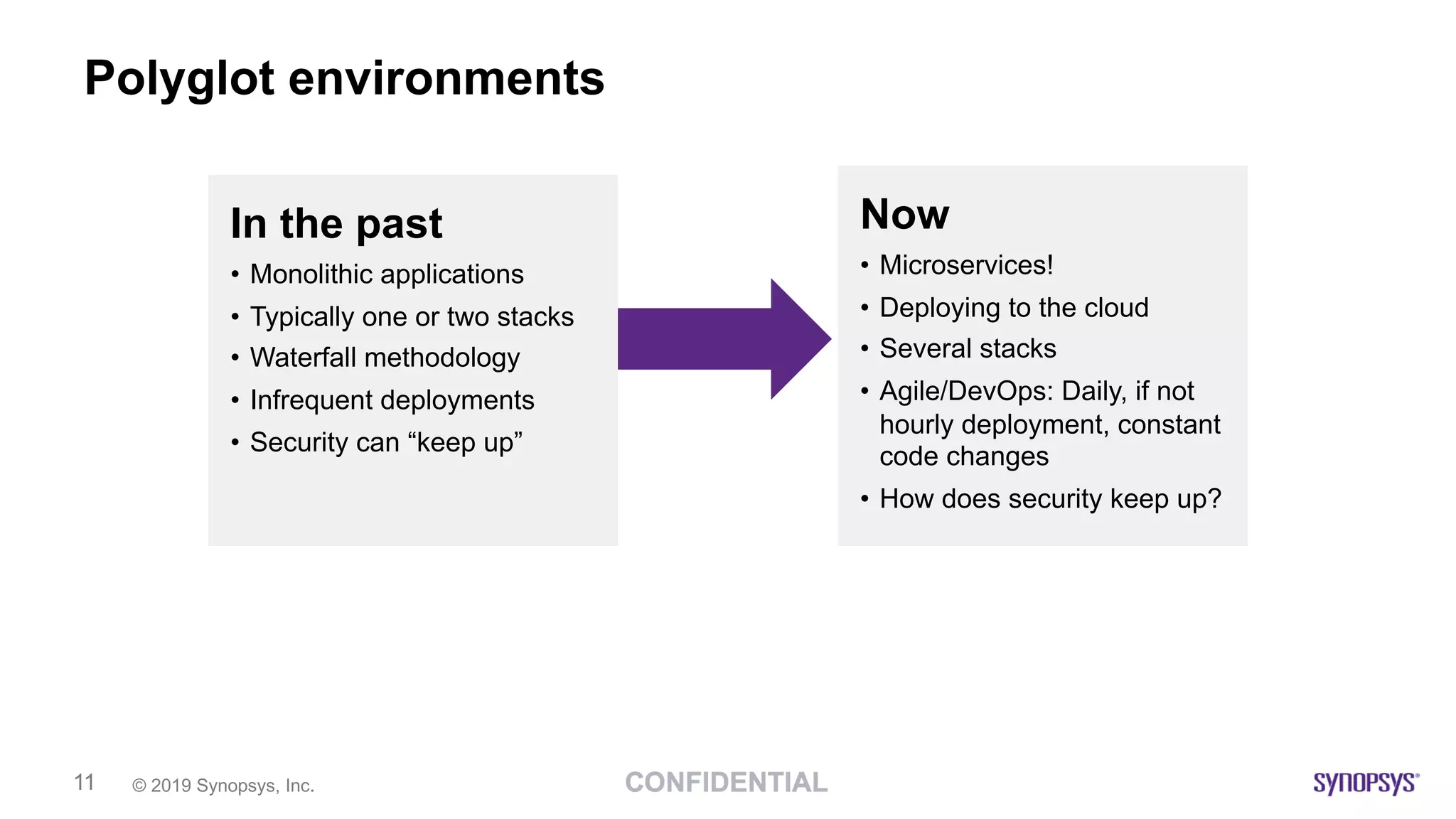
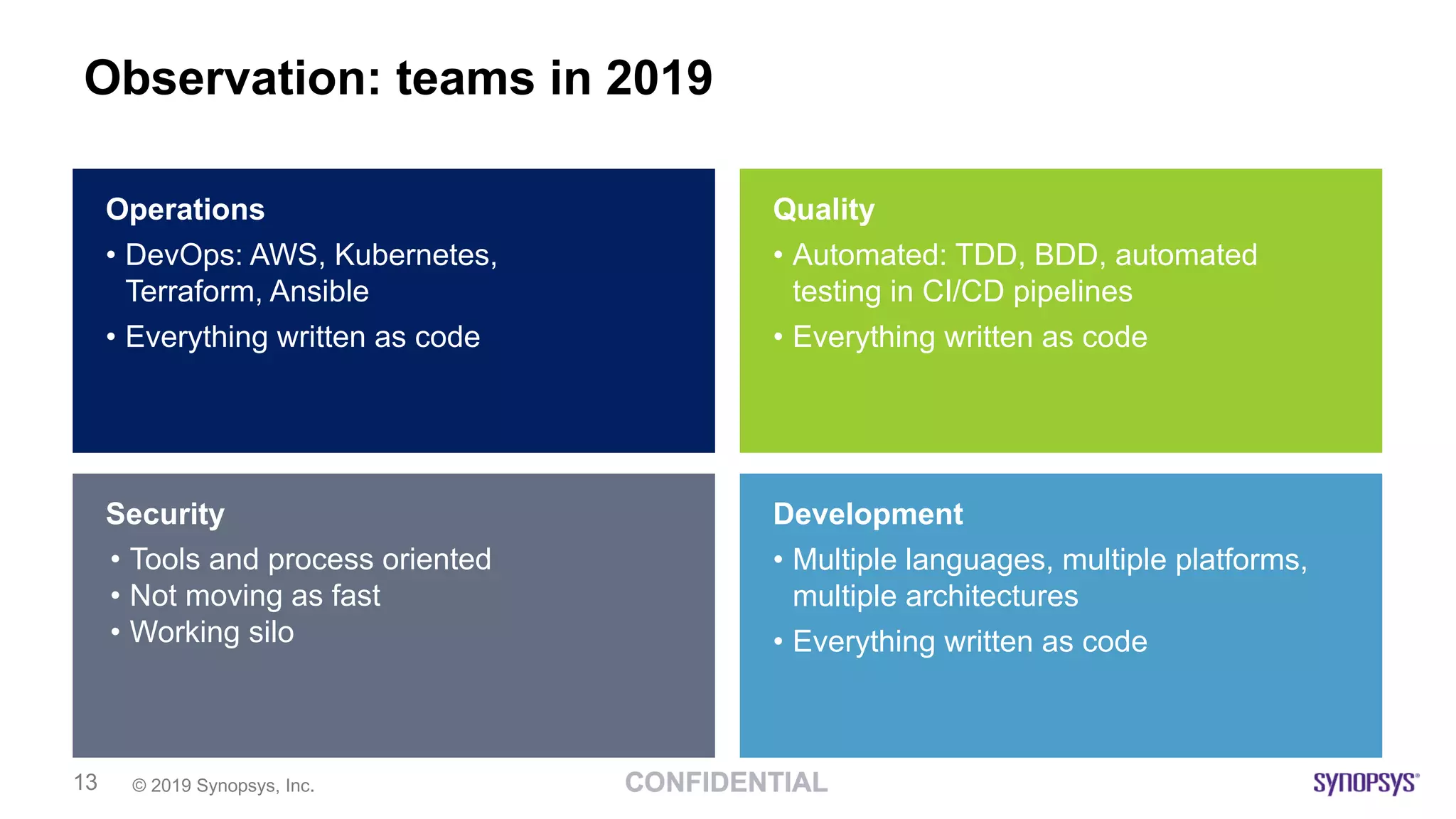
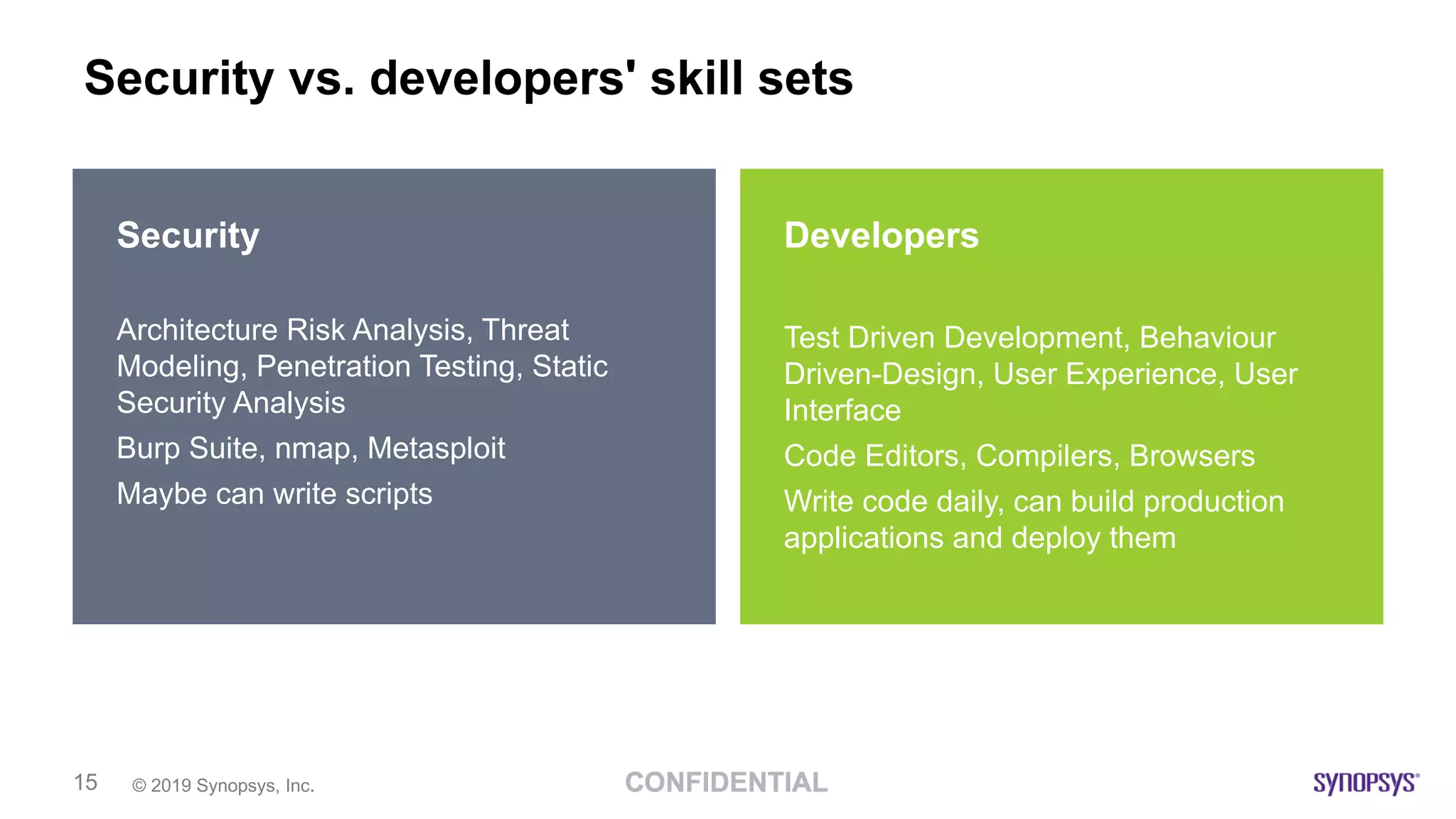
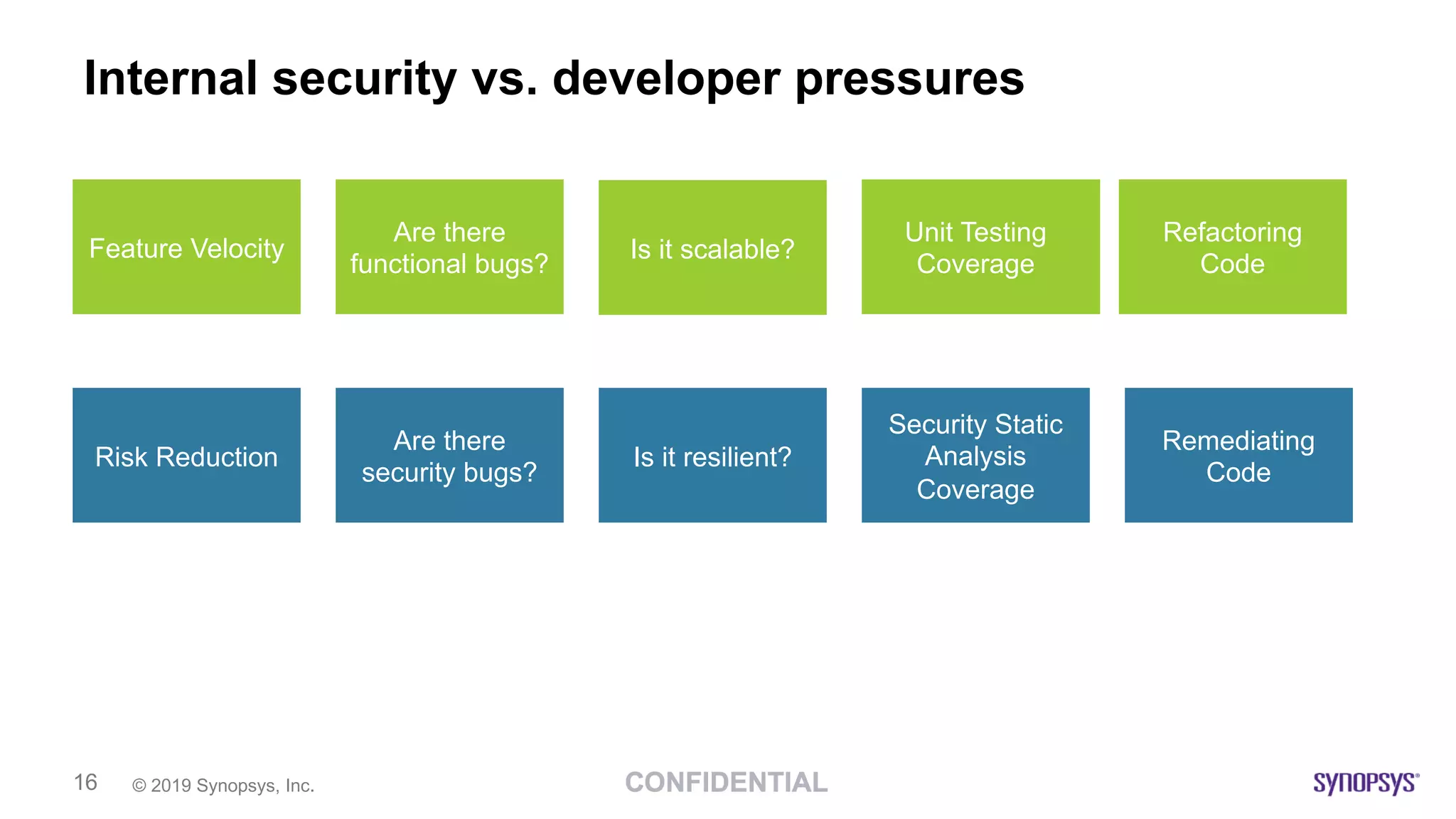
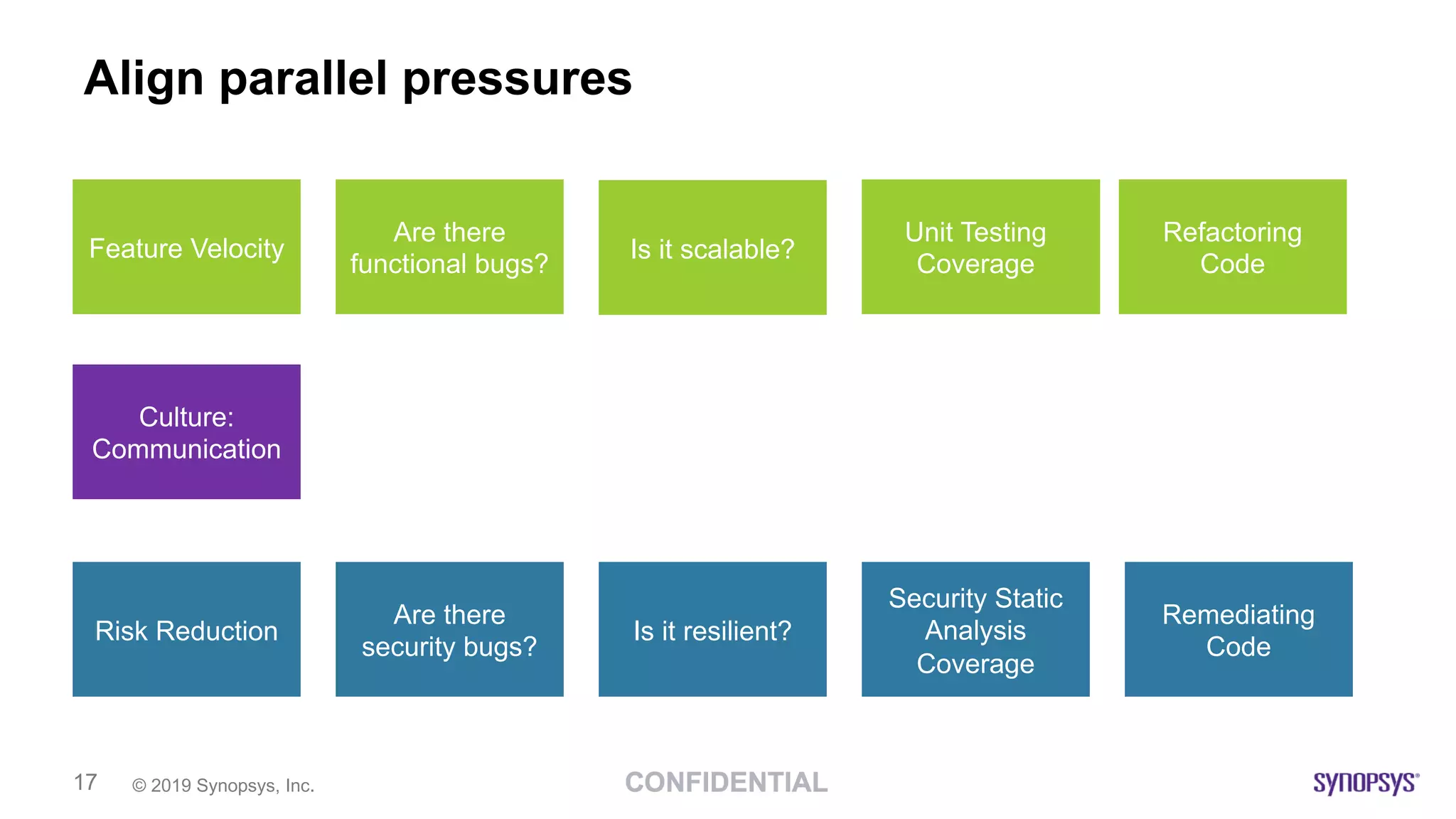
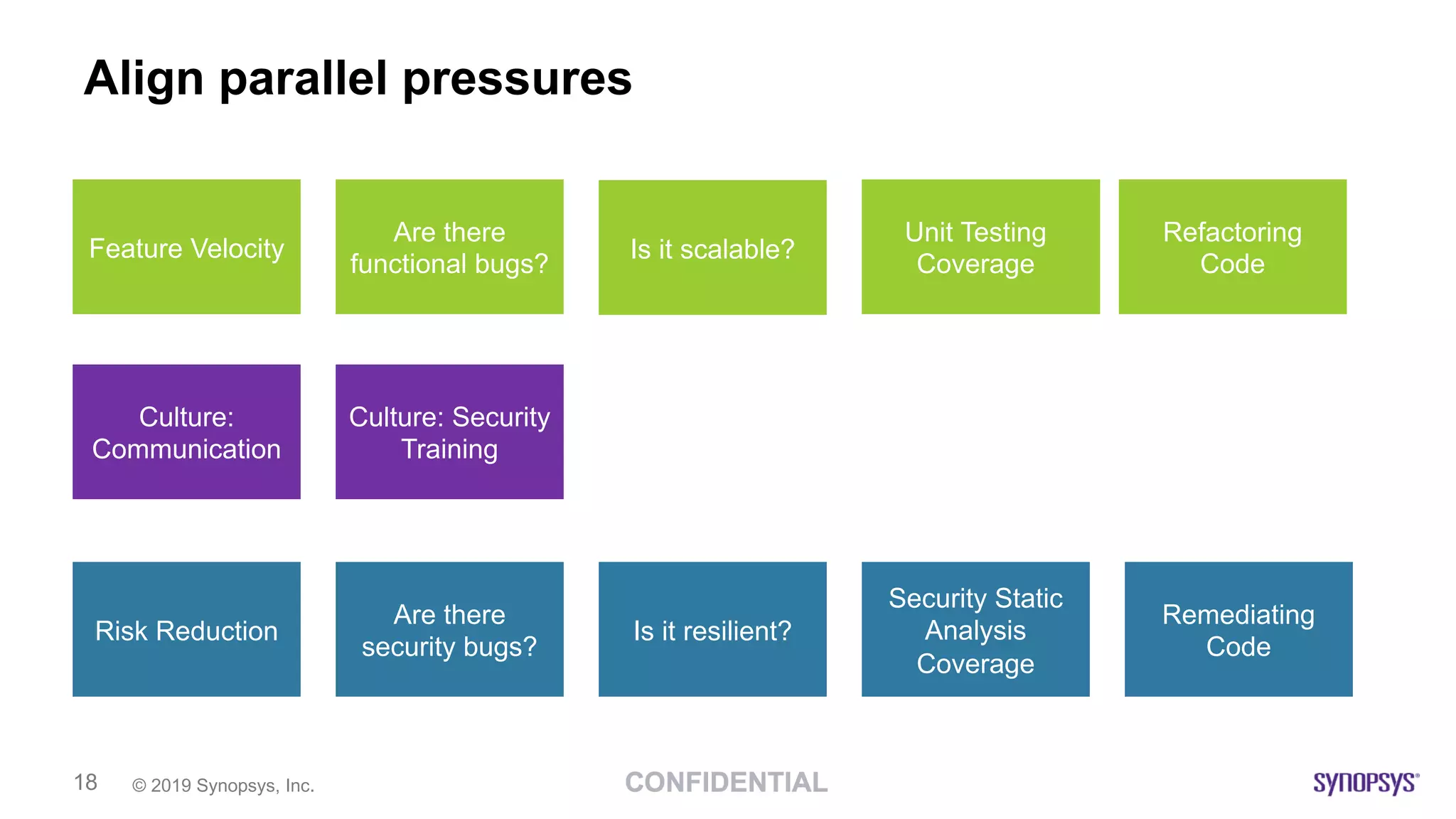
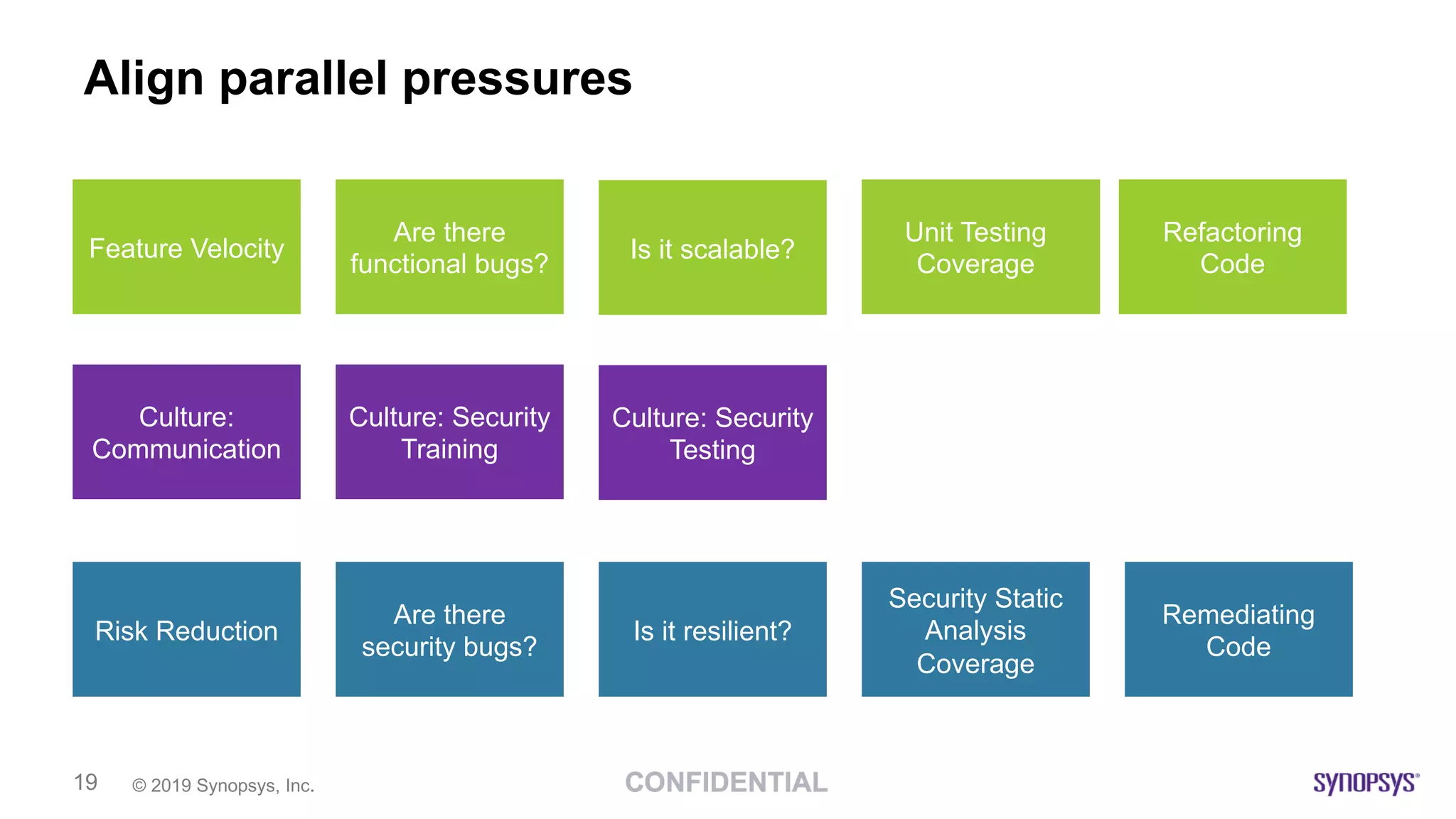
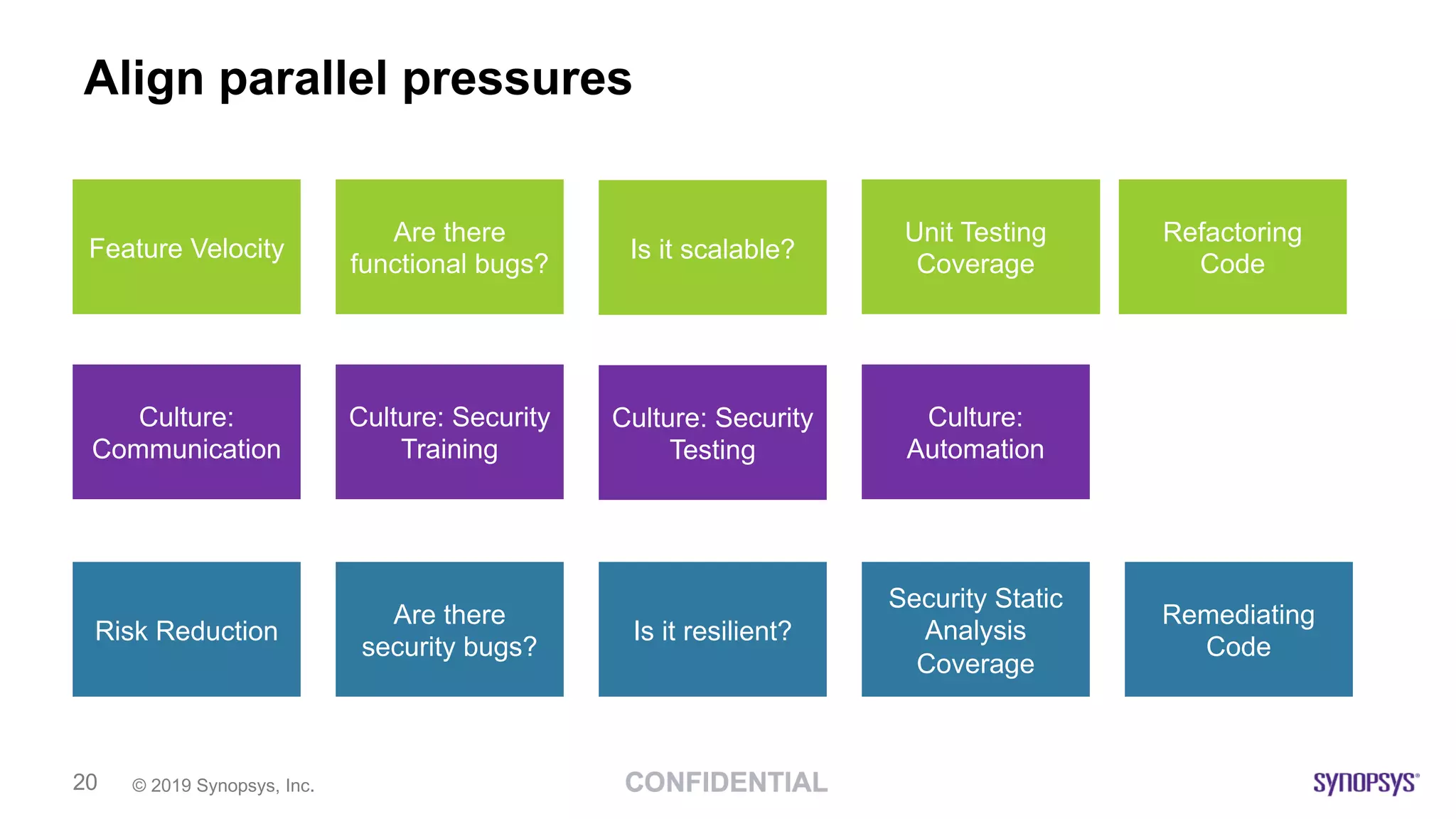
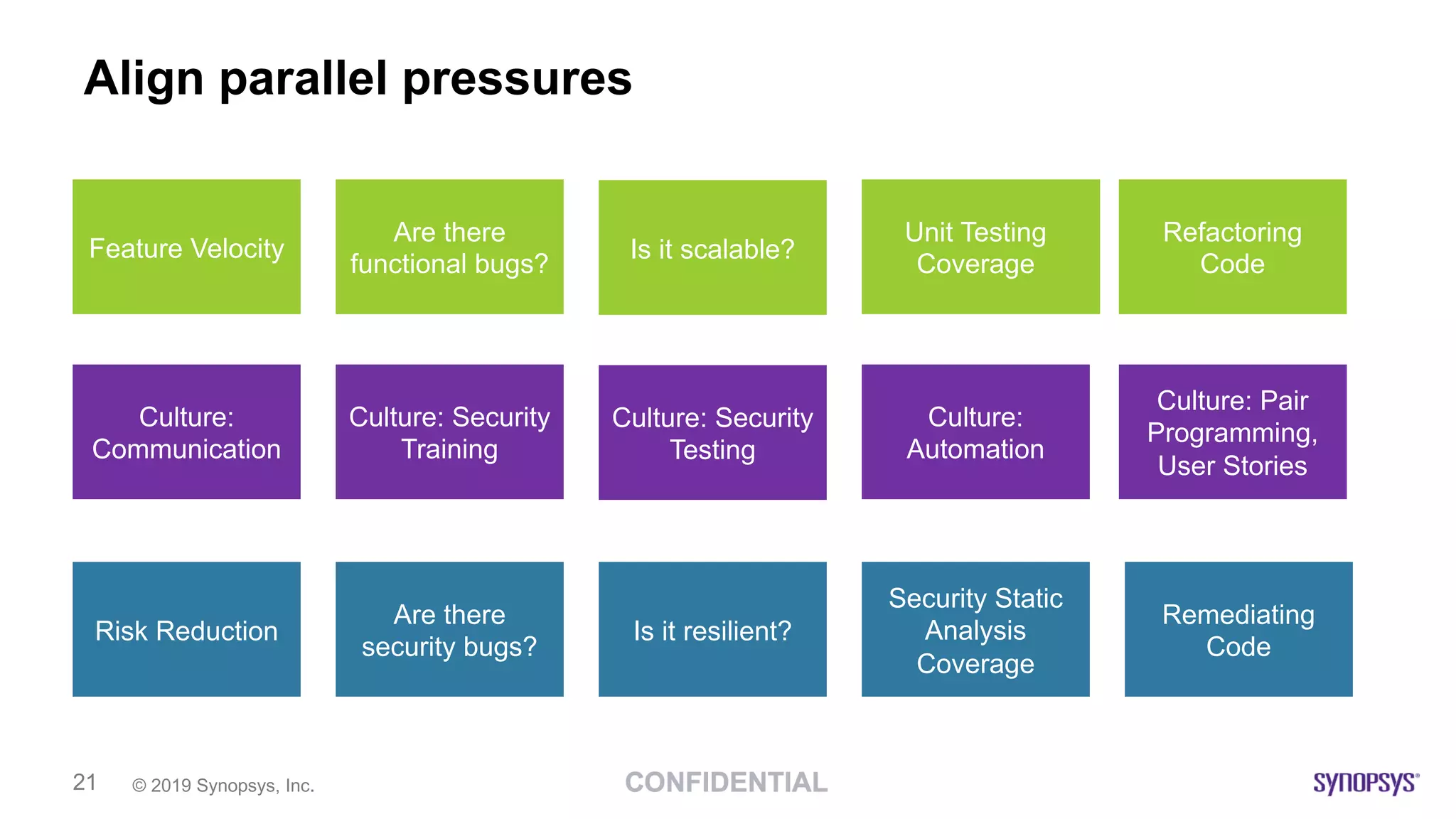
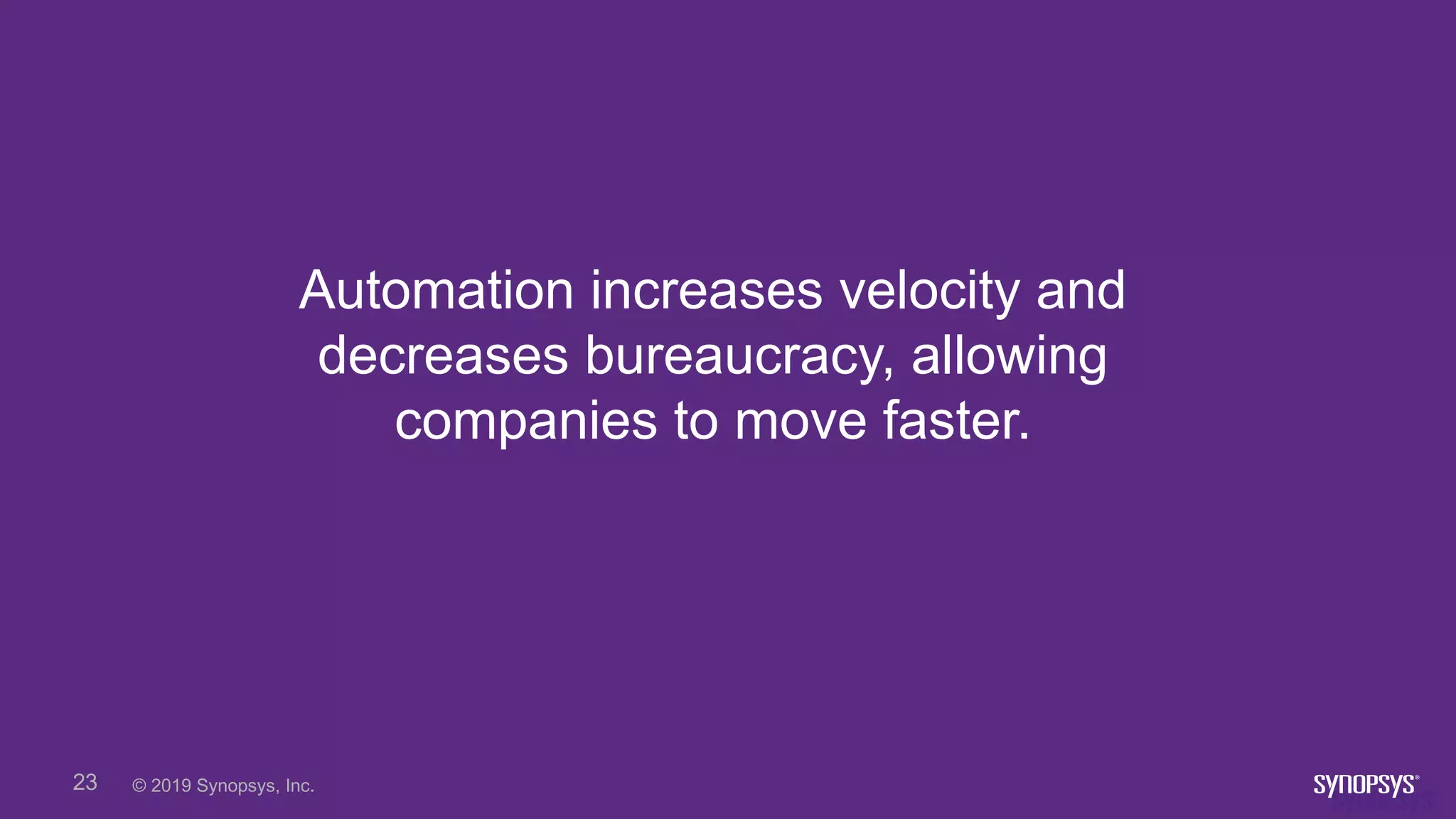
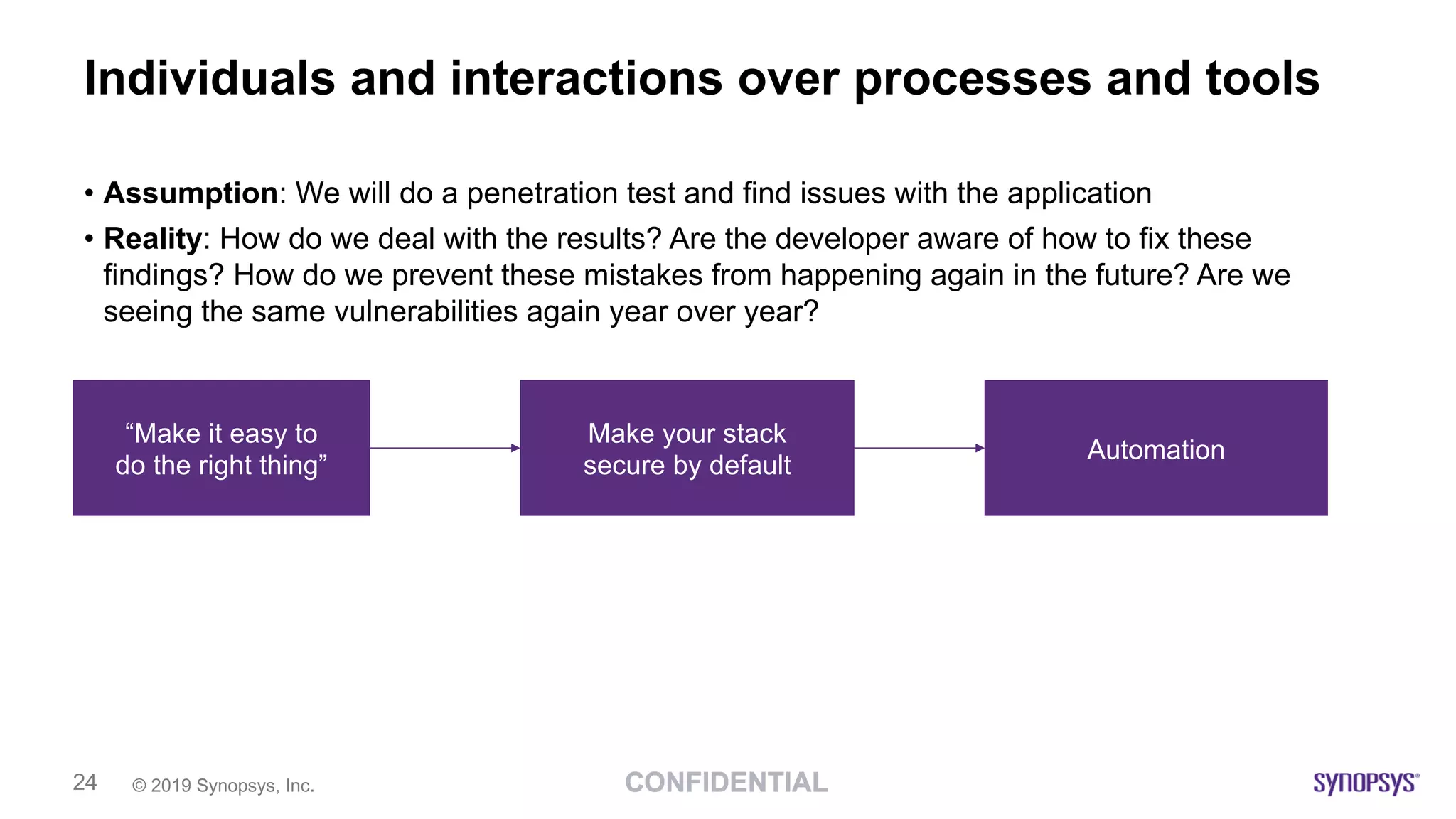
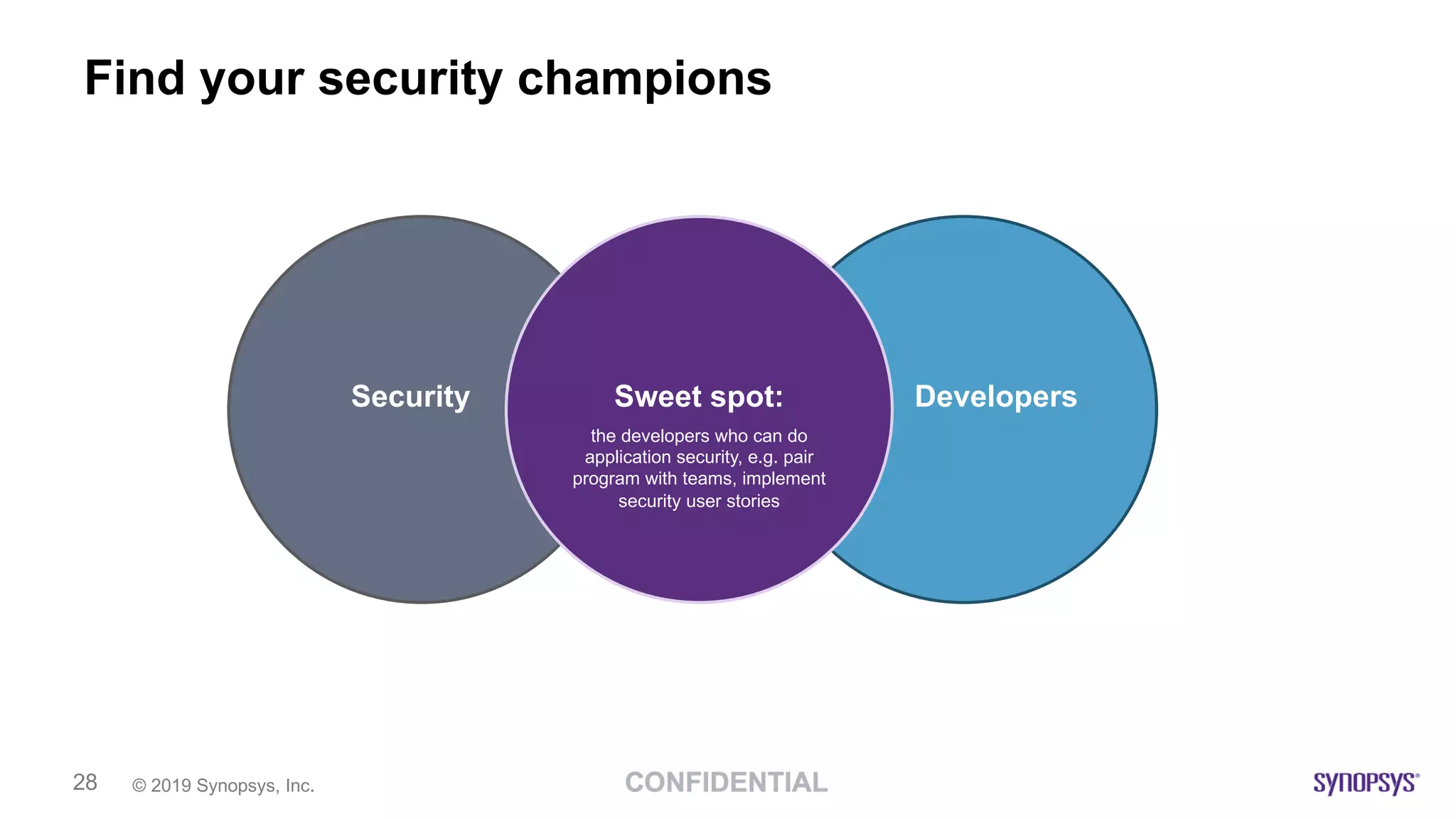
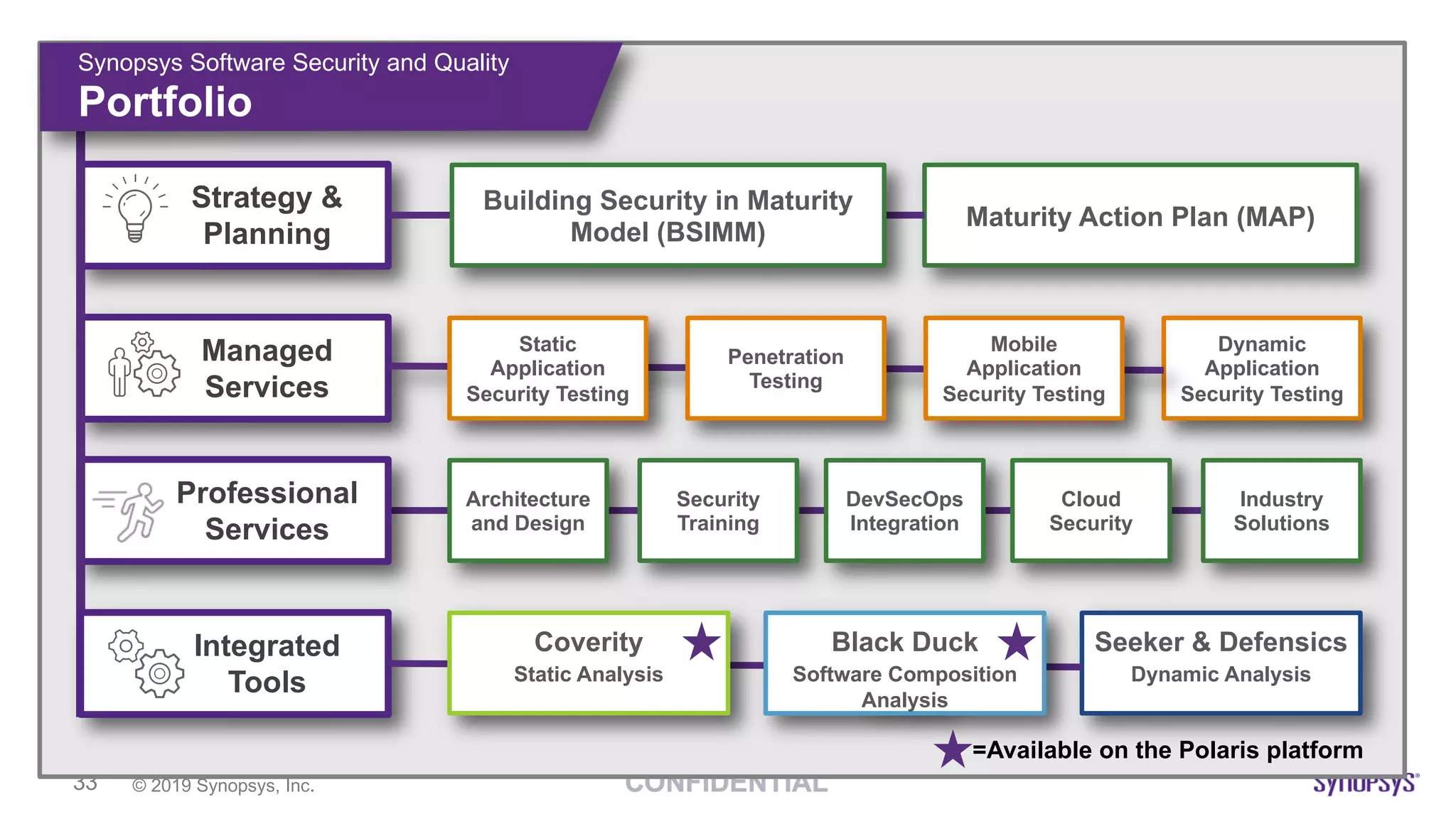
This document discusses building a culture of secure programming within an organization. It notes that culture can account for 20-30% of differences in corporate performance. It discusses challenges of modern software development like polyglot environments and faster development cycles. It argues security must understand developer technologies and processes. It promotes solutions like security champions who work with developers, security training, automation, and early involvement to align security and development pressures. The goal is open communication, security as enablers rather than blockers, and nurturing a proactive security culture.