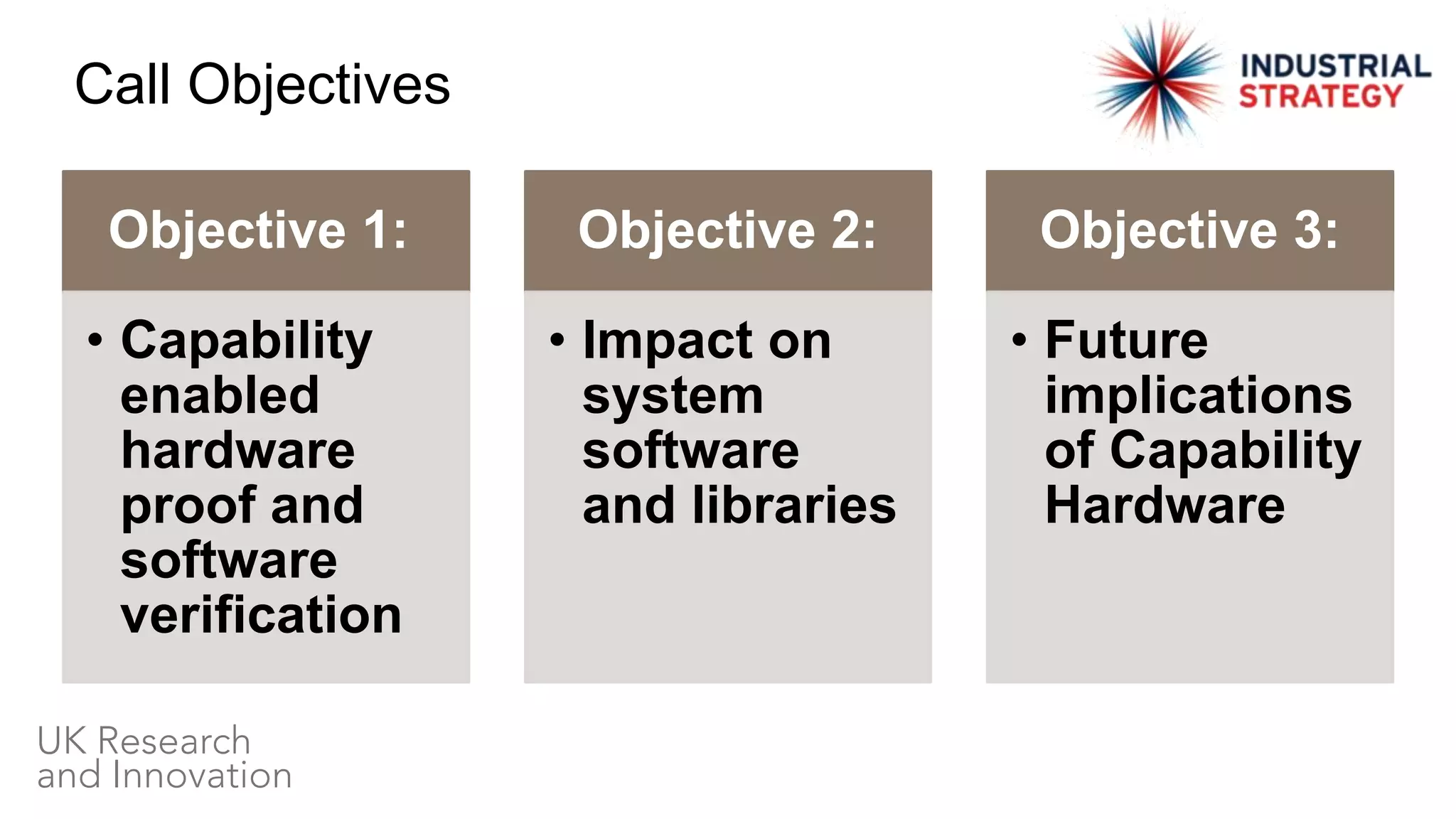
The EPSRC Call for Proposals for Digital Security by Design invites research projects focused on capability hardware and its impact on software verification and security, with up to £8 million available for funding. The call includes objectives centered on hardware/software verification, system software impact, and future implications of capability hardware, and aims to investigate new opportunities and threats introduced by fine-grain data protection. The proposals are due by January 7, 2020, and a workshop will be held in November 2019 for potential applicants.