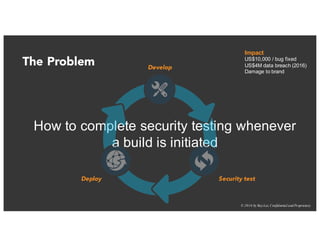
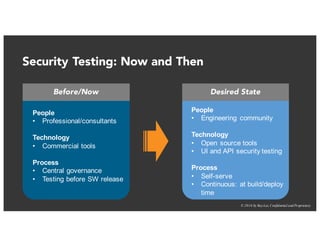
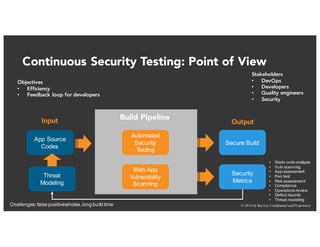
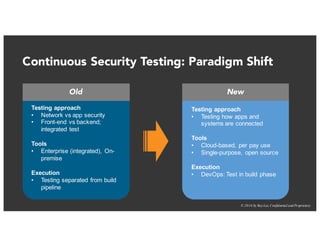
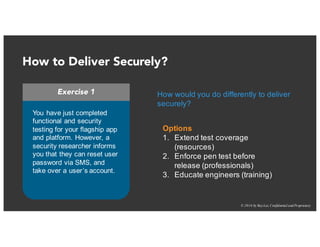
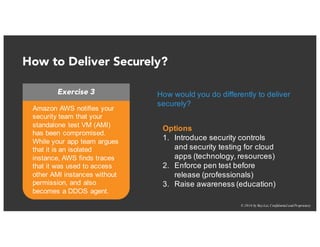
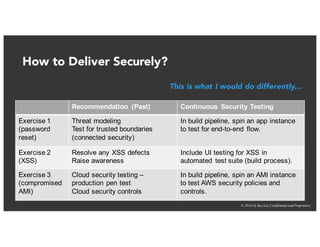
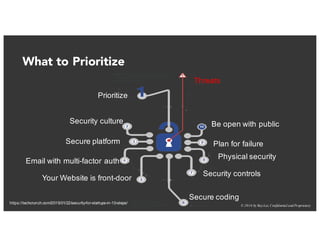
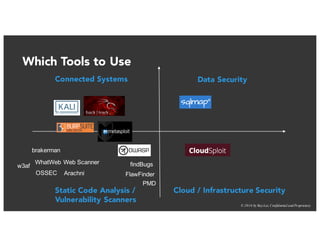
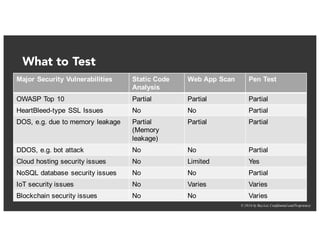
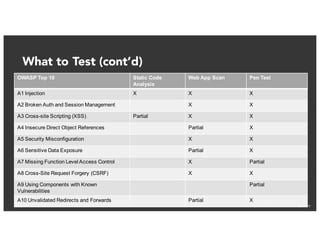
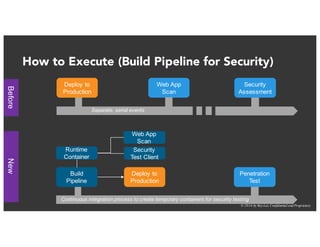
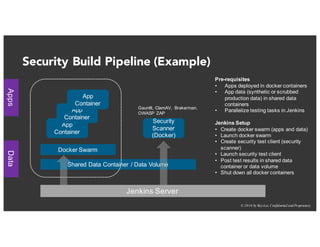
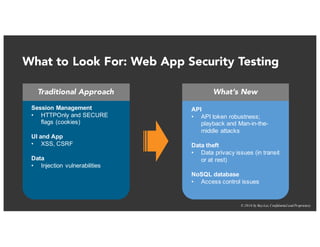
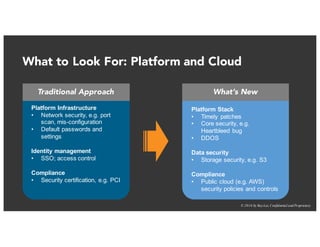
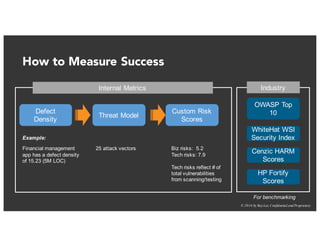
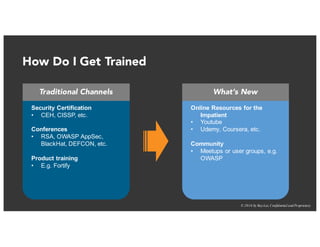
The document discusses the challenges and best practices of continuous security testing in both enterprise and startup environments. It highlights the need for effective security measures throughout the software development lifecycle and offers recommendations for improving security testing processes. Various tools and methodologies are explored, along with case studies and exercises to enhance understanding and implementation of security protocols.