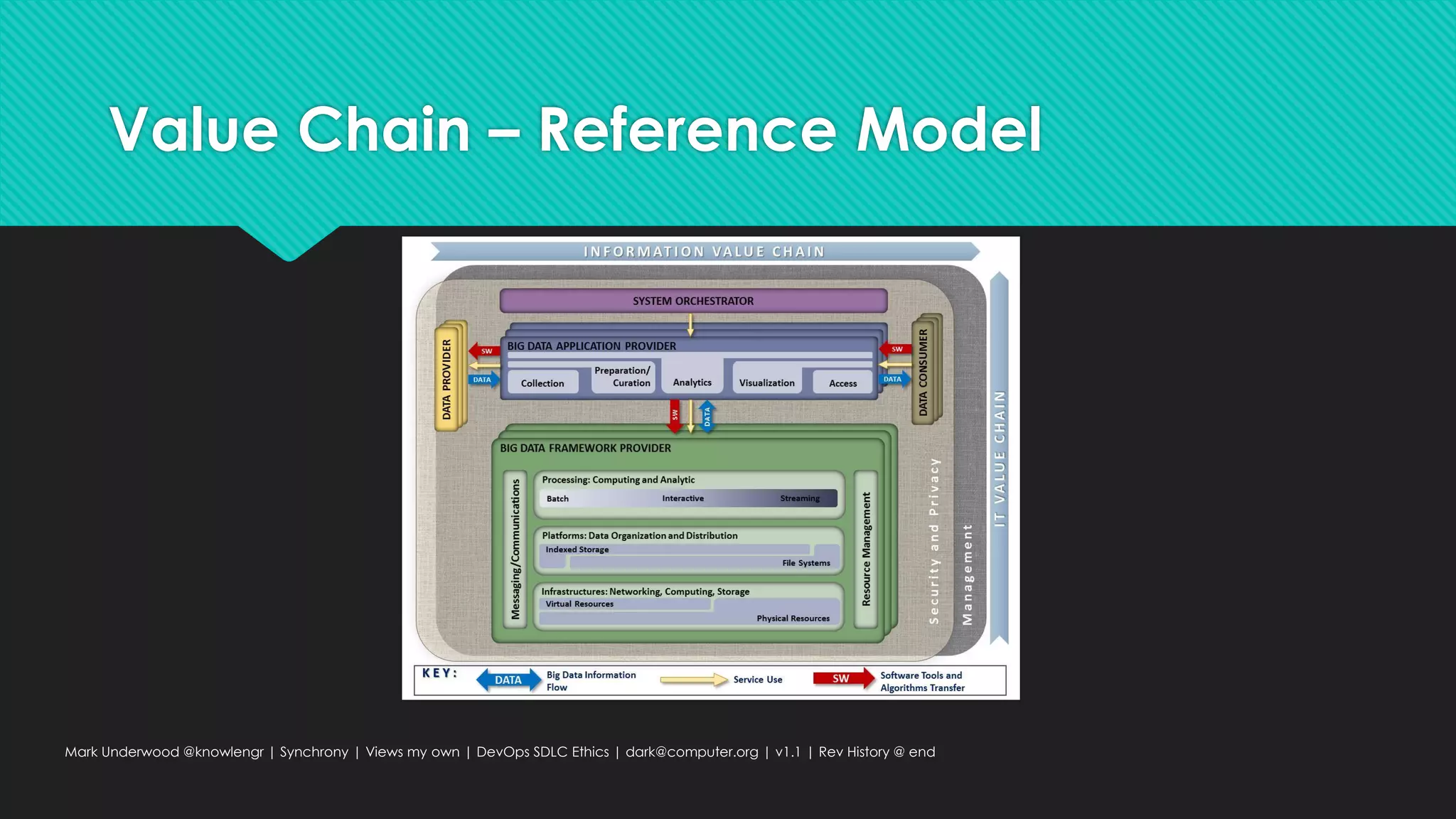
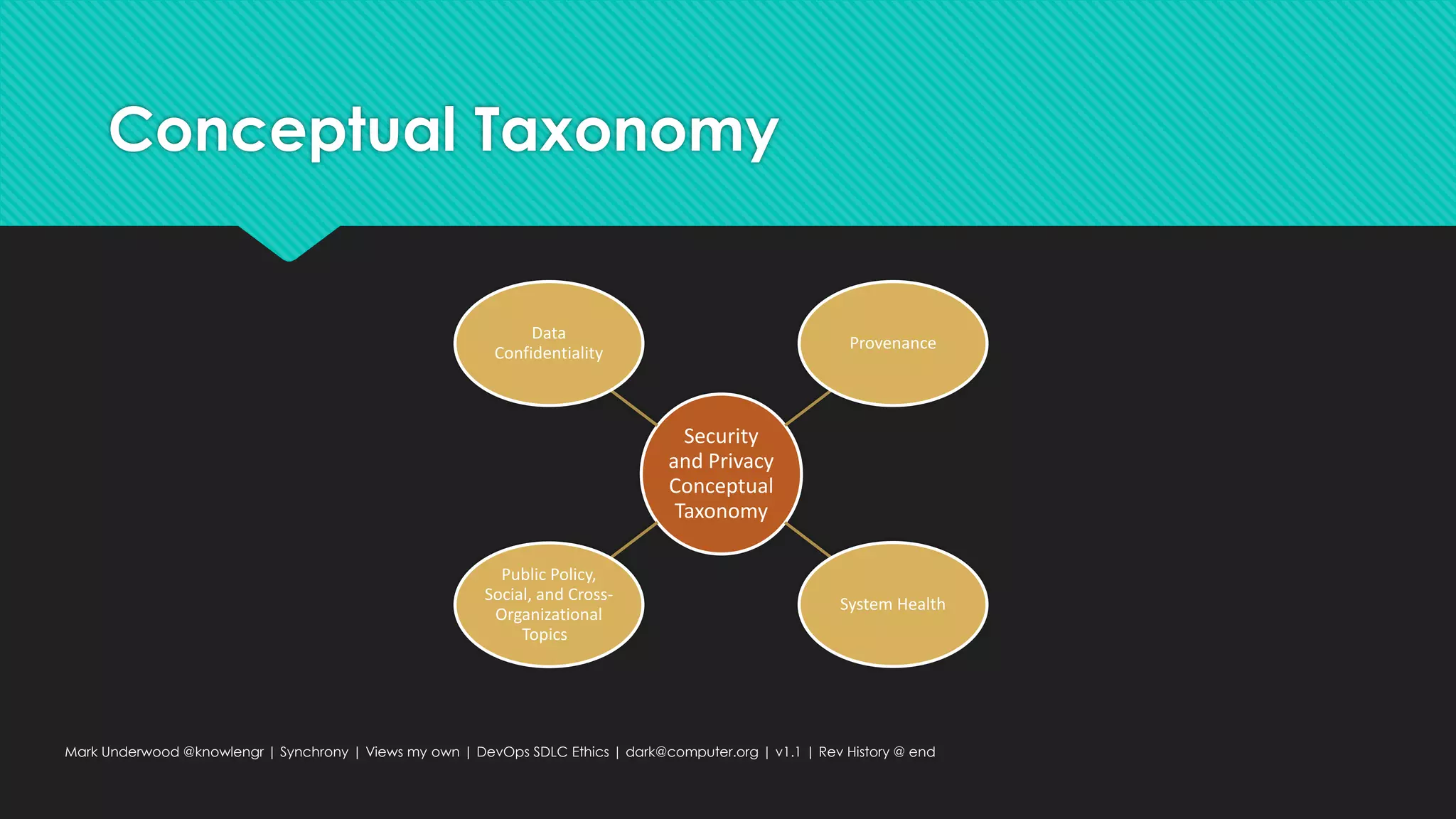
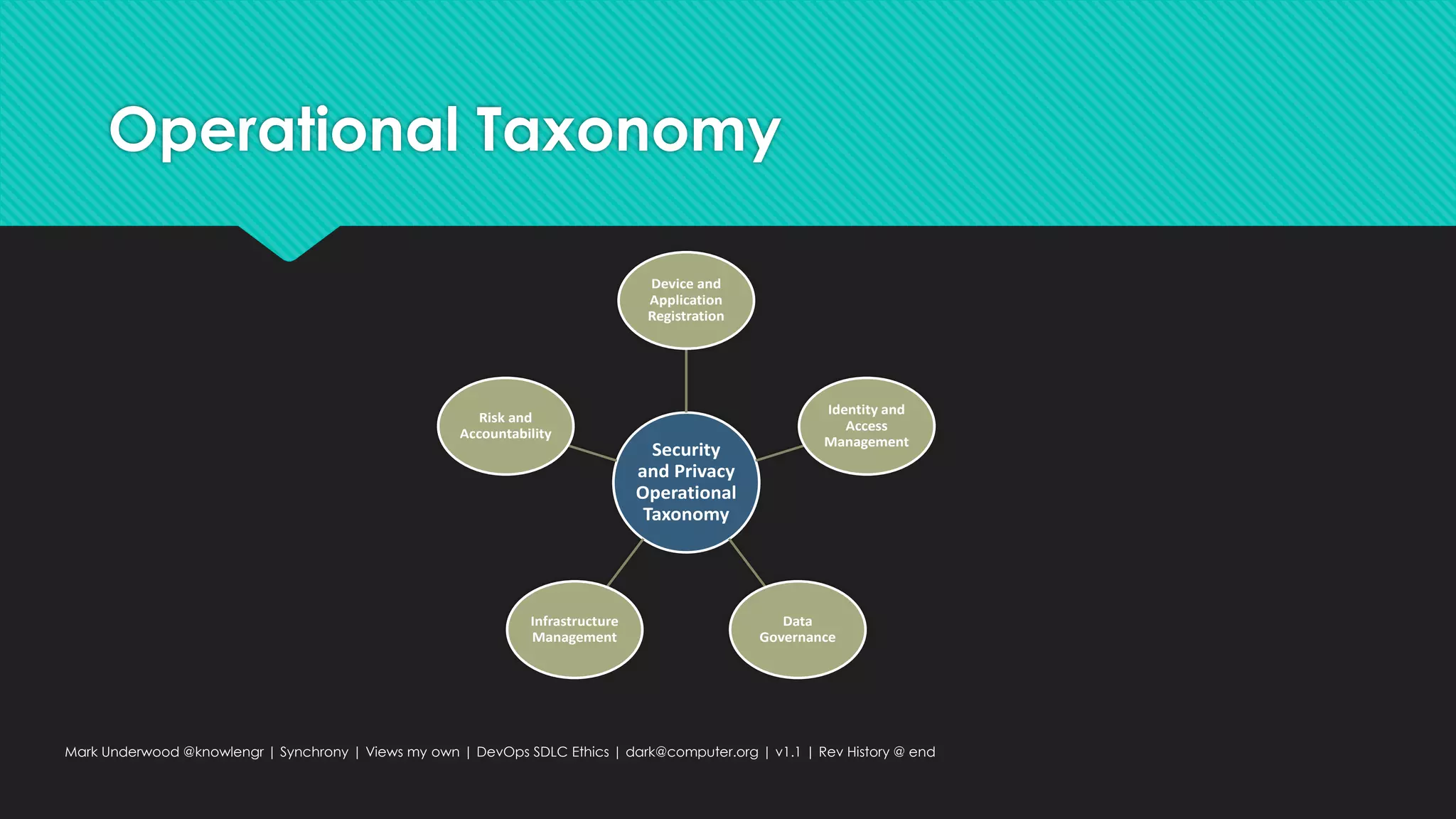
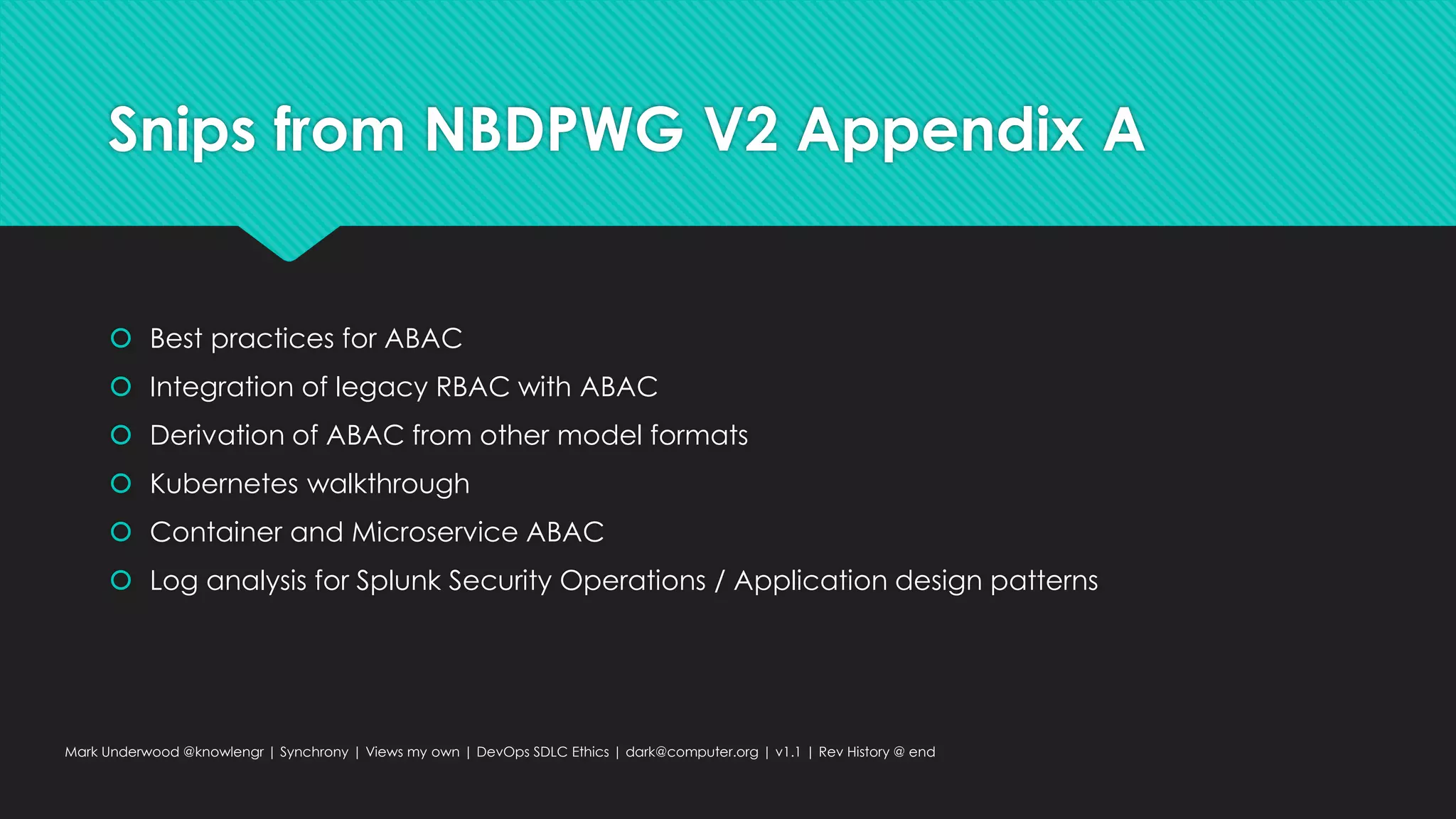
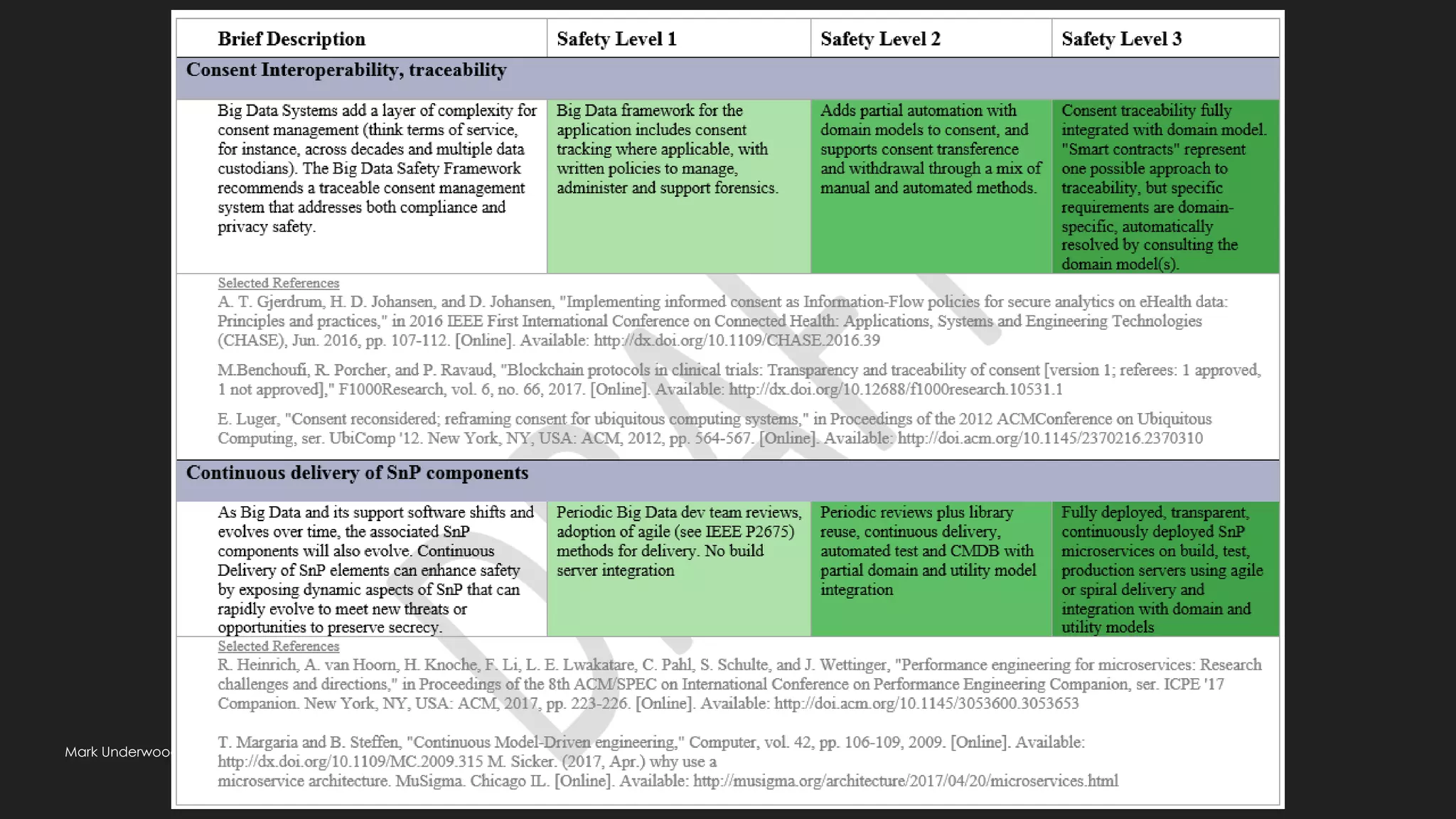
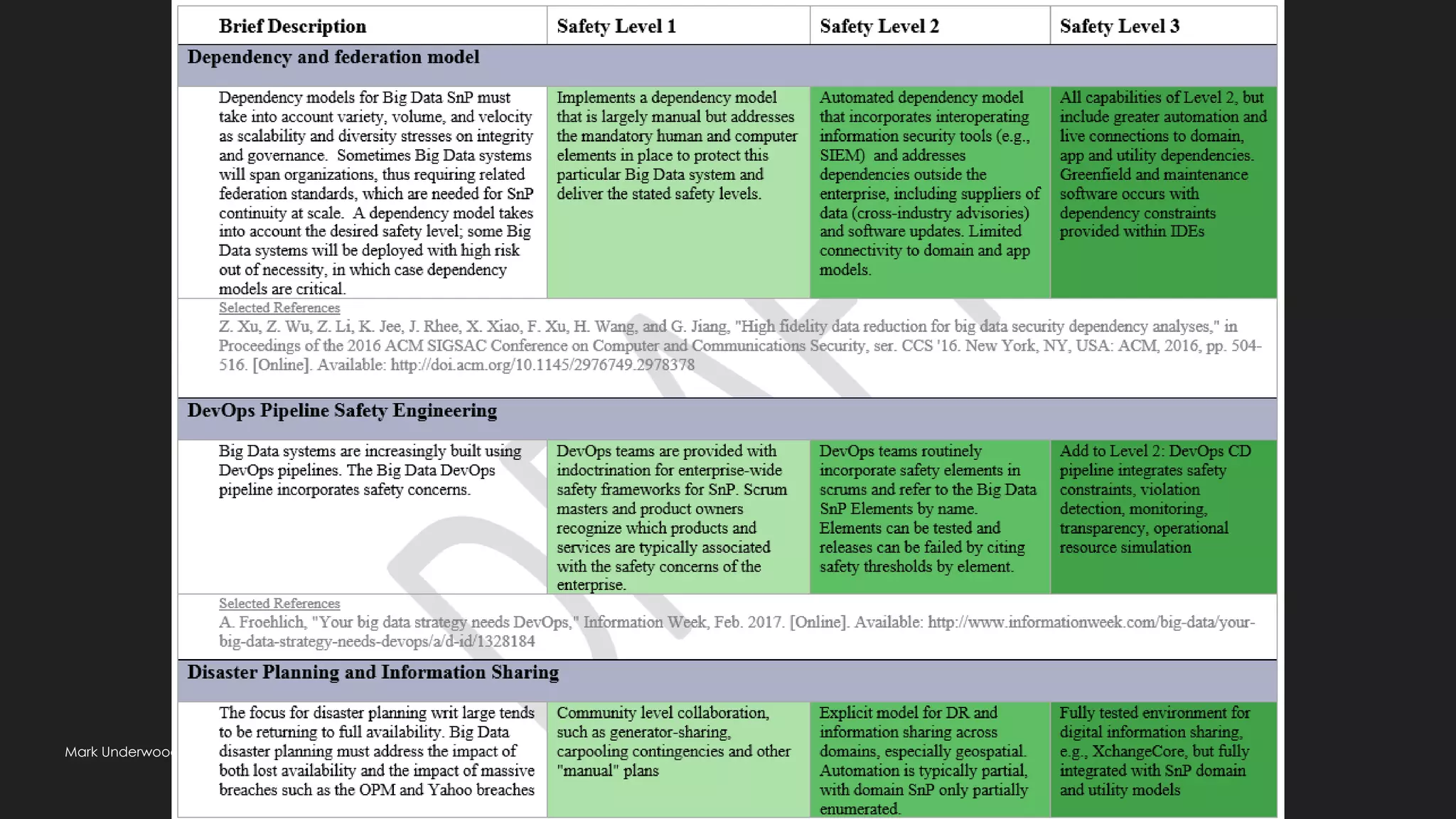
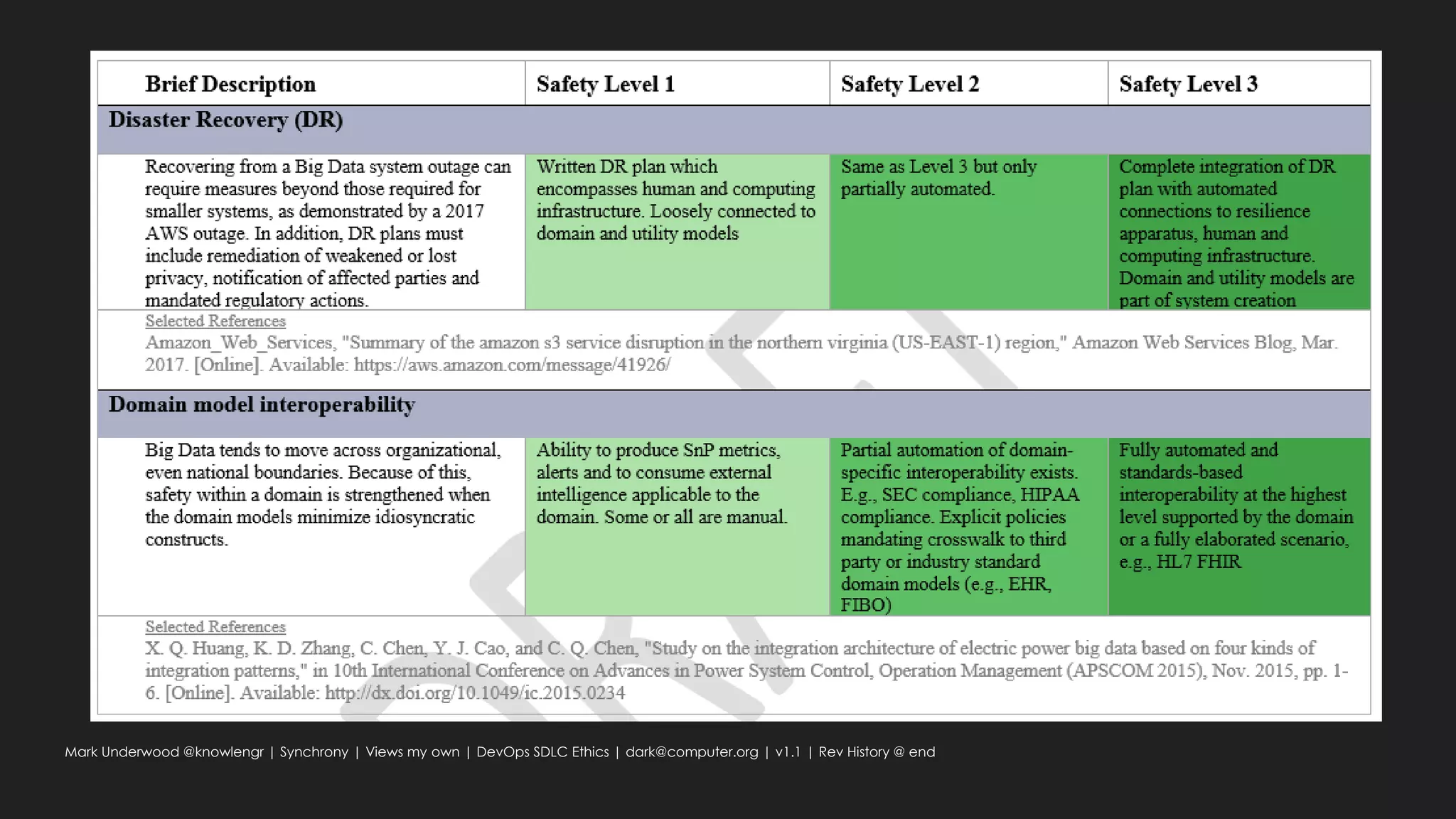
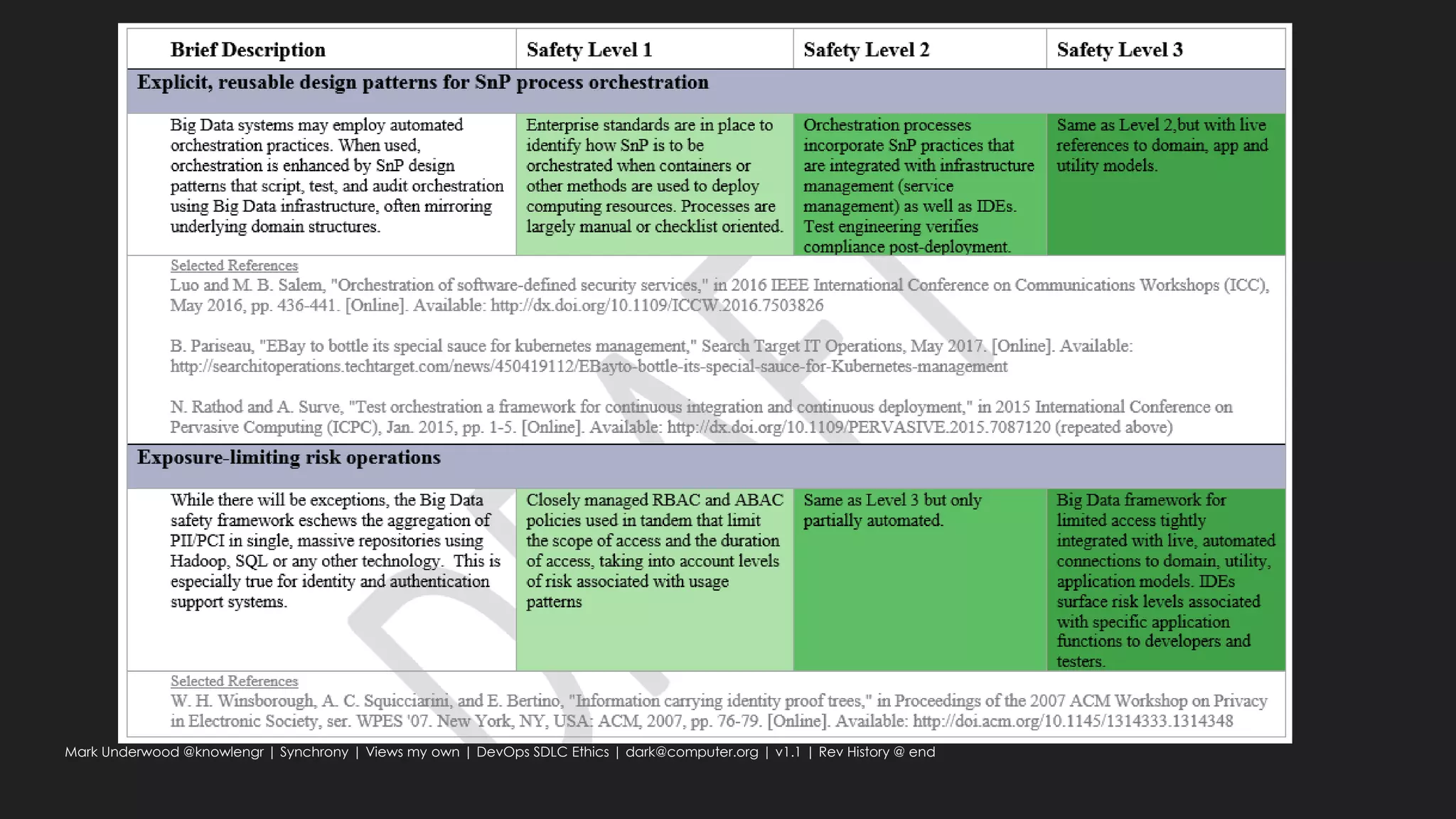
This document provides an overview of ethical considerations in the software development life cycle (SDLC) as guided by IEEE standards, emphasizing the importance of ethical practices in IT product development. It discusses various case studies highlighting ethical dilemmas in technology, particularly in areas like artificial intelligence and data privacy. The document also examines the role of transparency and accountability in ethical decision-making and the need for inclusive practices that consider underrepresented populations.












![Traceability & Requirements Engineering
Define what is an ethical requirement
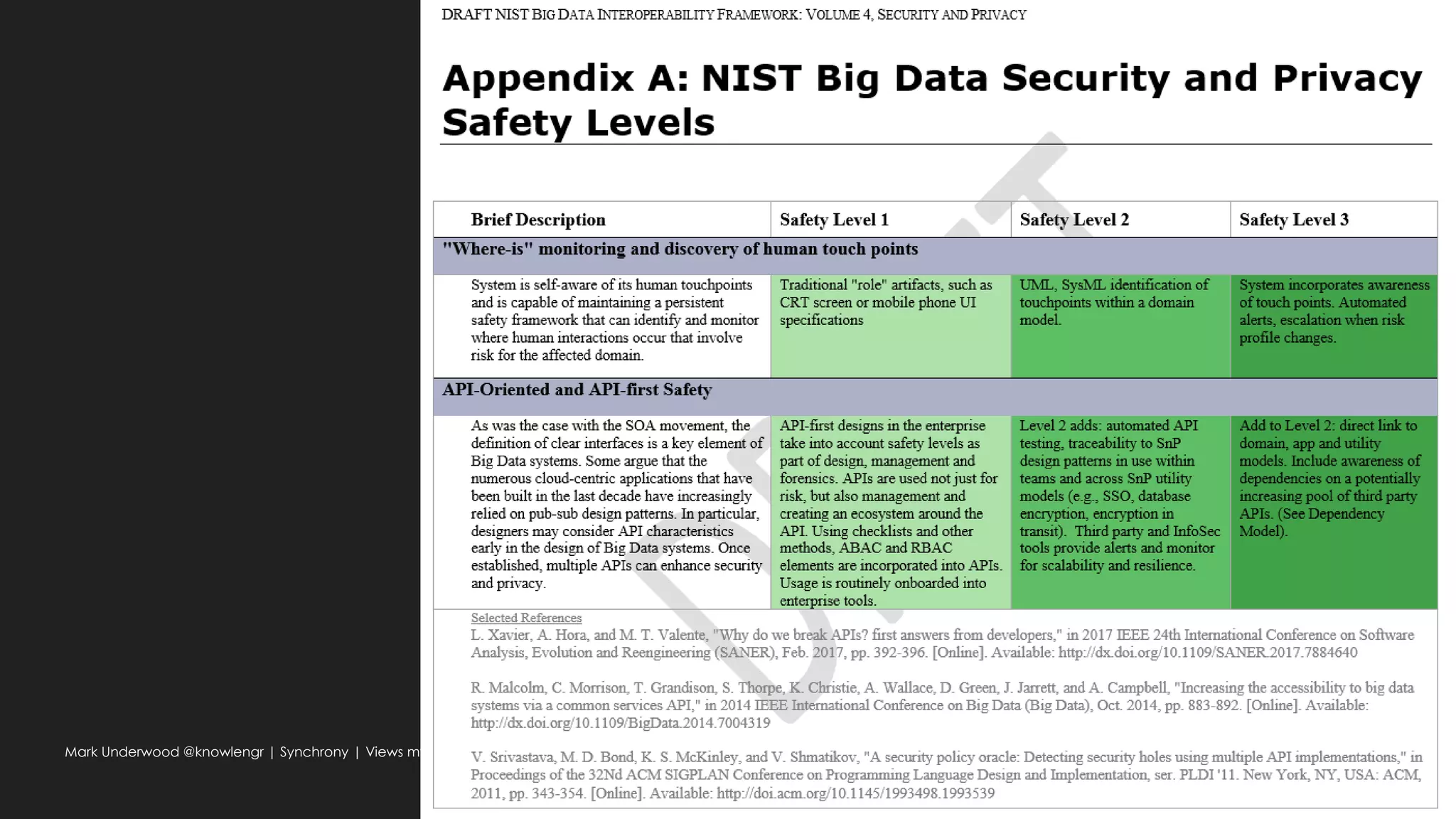
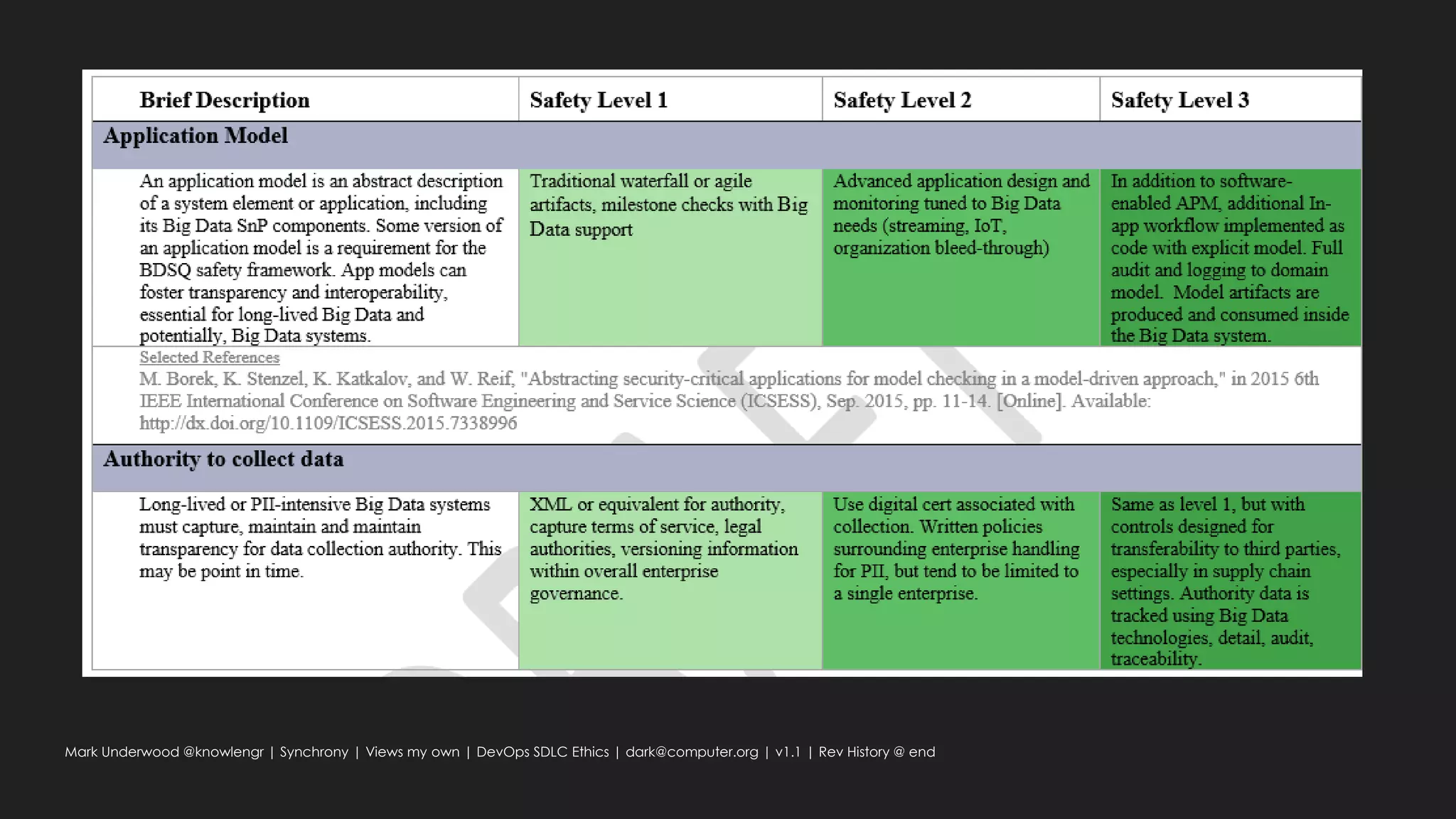
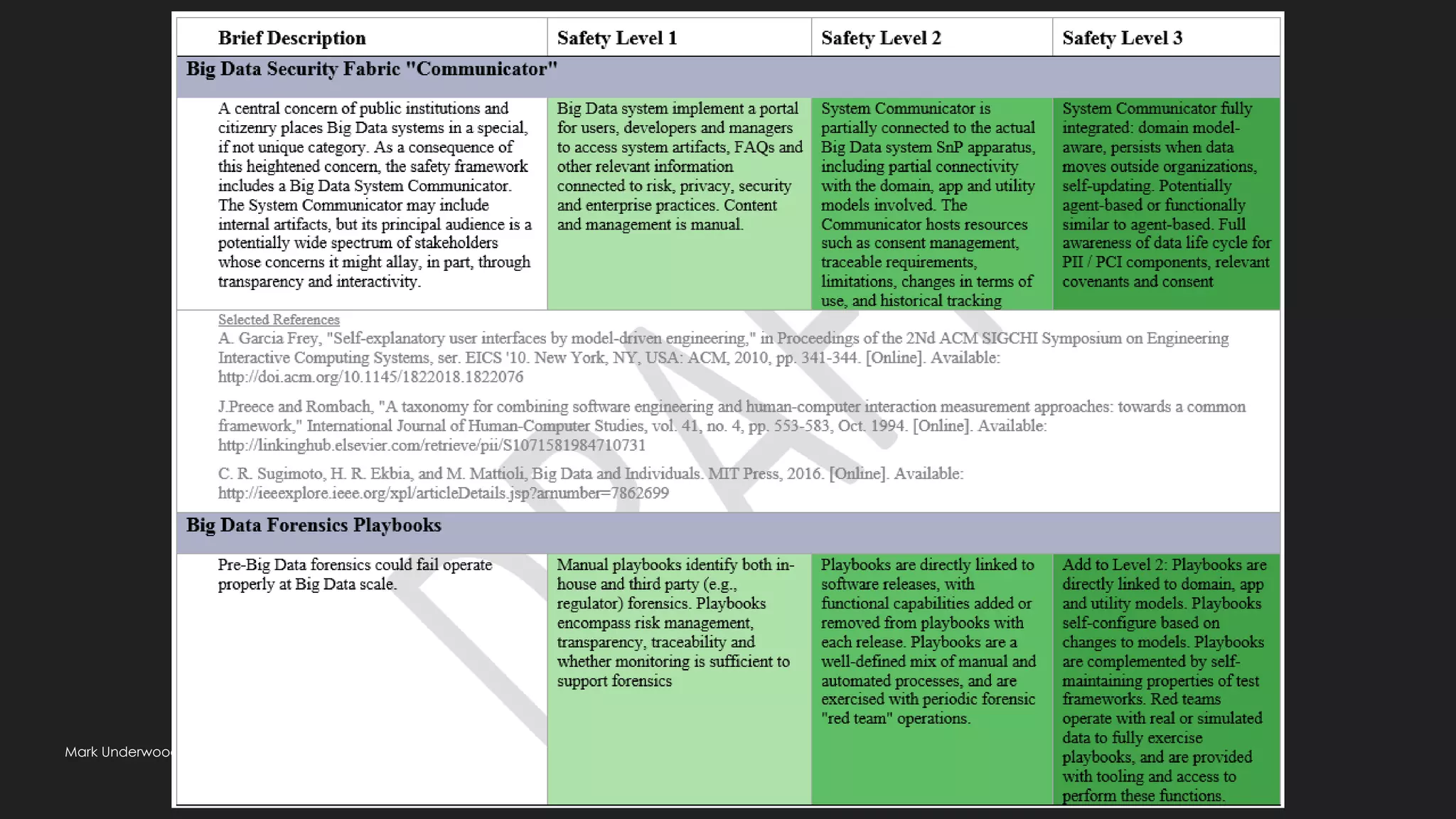
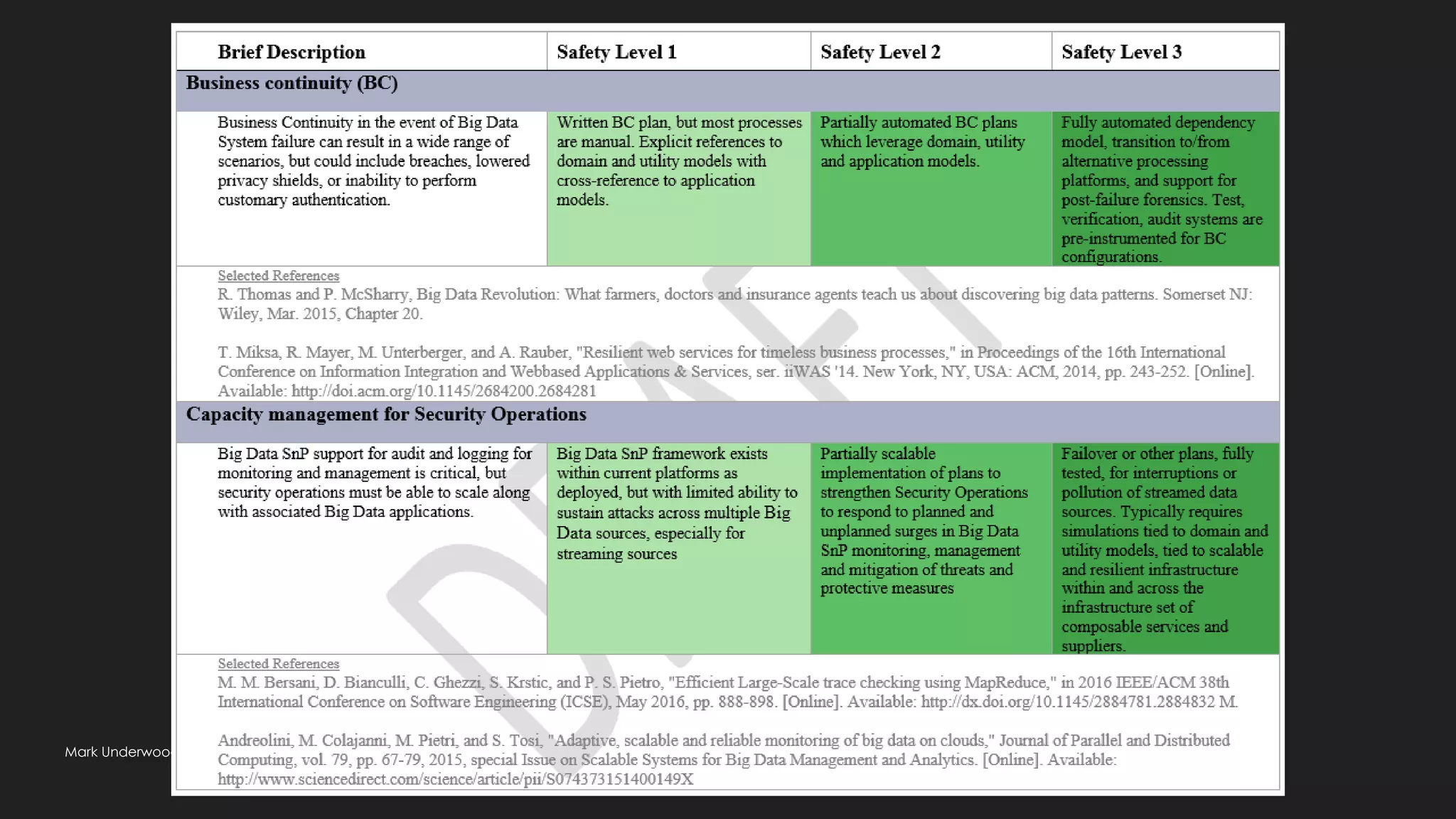
Possible: big data ethical fabric (transparency, usage)
Audit
Traceability requirements
Can an ethical responsibility be inherited like Personal Data-tagged data elements?
What about synthetic, algorithm-defined elements?
Note: See EU notion for “Personal Data” vs. PII in the US: P. Schwartz and D. Solove, "Reconciling
Personal Information in the United States and European Union," California Law Review, vol. 102,
no. 4, Aug. 2014. [Online]. Available:
https://scholarship.law.berkeley.edu/californialawreview/vol102/iss4/7
Mark Underwood @knowlengr | Synchrony | Views my own | DevOps SDLC Ethics | dark@computer.org | v1.1 | Rev History @ end](https://image.slidesharecdn.com/devops-support-for-ethical-systems-development-180530013548/75/DevOps-Support-for-an-Ethical-Software-Development-Life-Cycle-SDLC-26-2048.jpg)