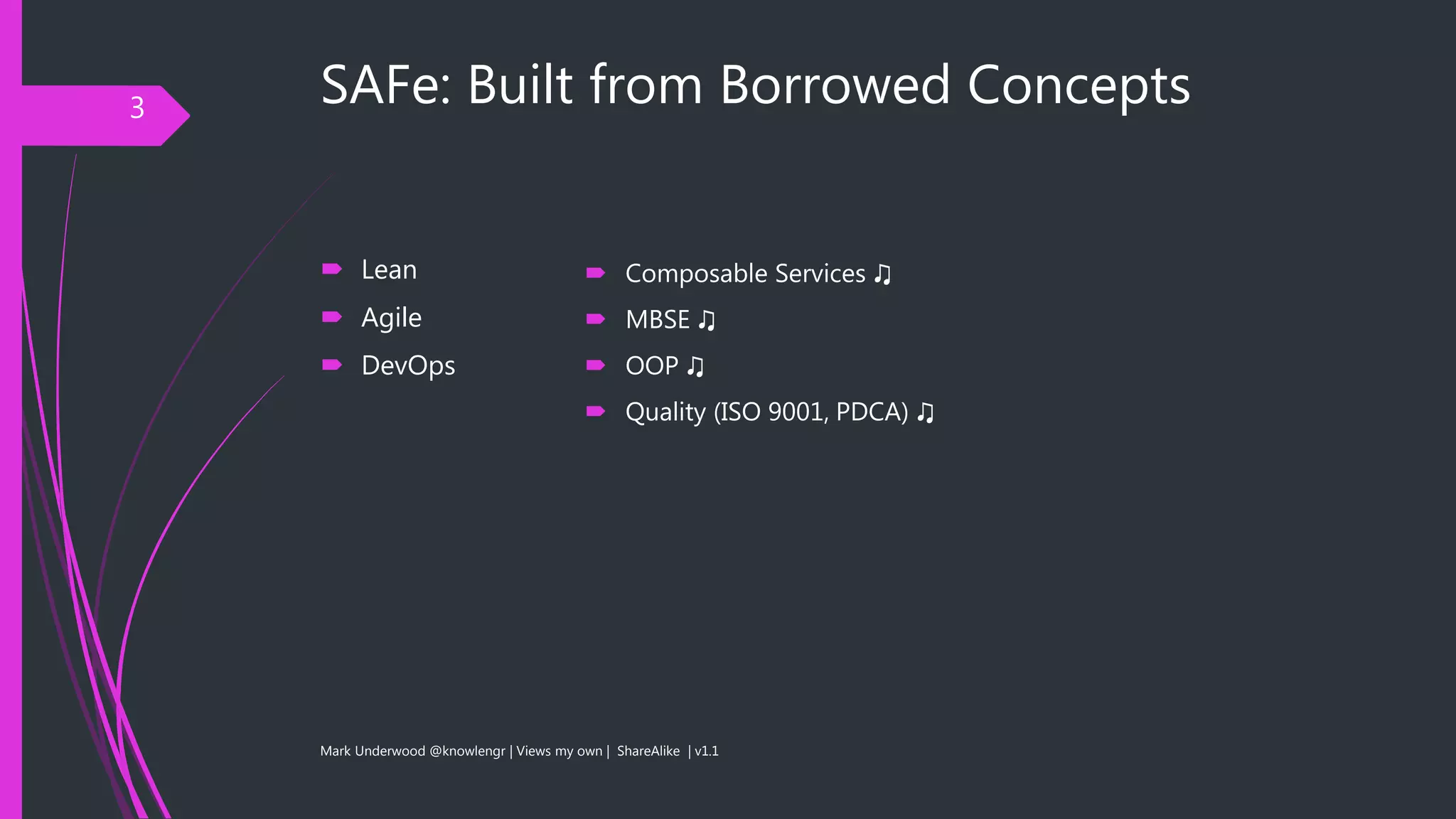
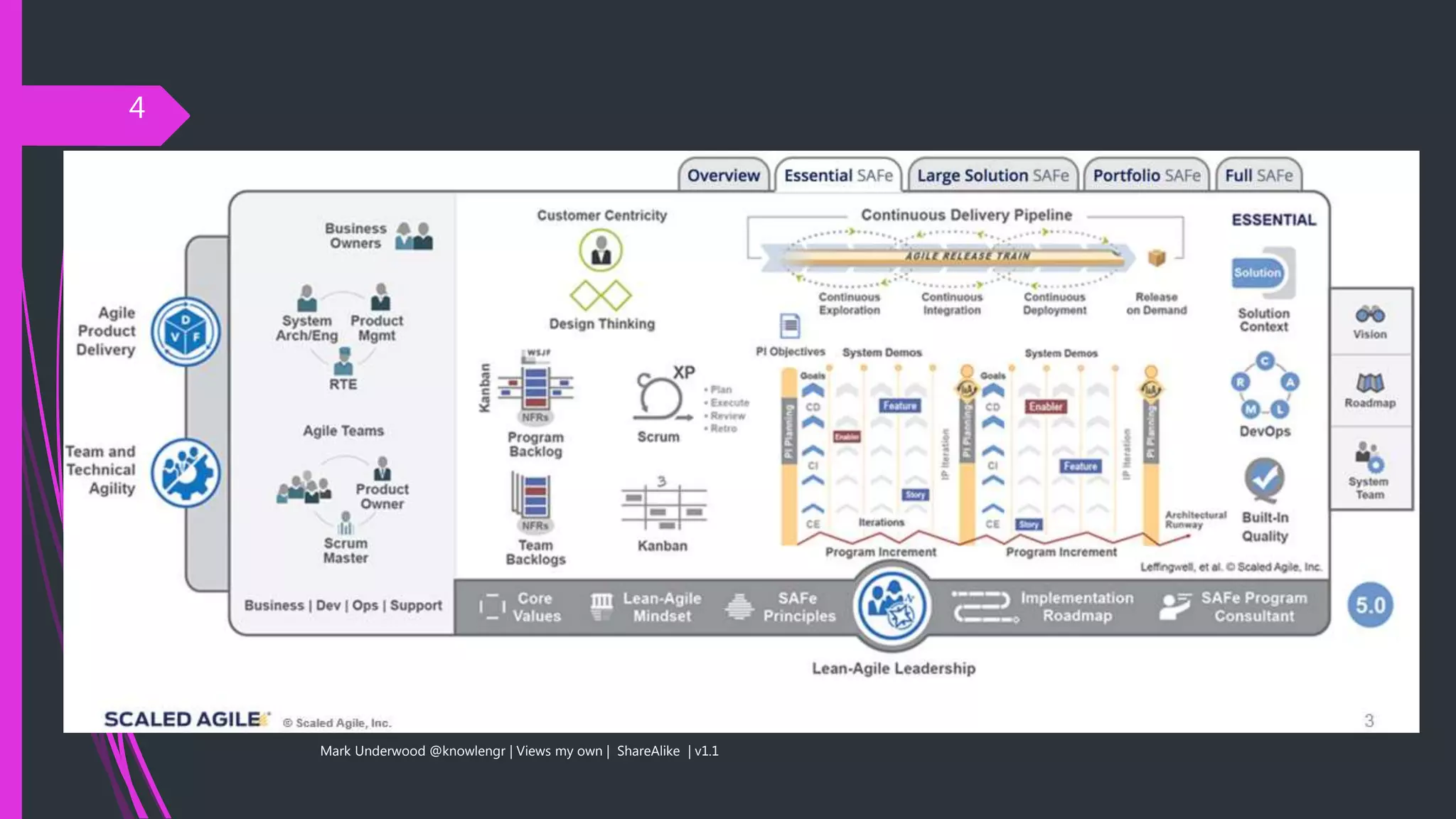
The document provides an overview of the Scaled Agile Framework (SAFe) from the perspective of security and privacy specialists. It discusses how SAFe borrows concepts from lean, agile, and DevOps principles. While SAFe incorporates security as a quality attribute, the document notes it may not provide an in-depth treatment and hybrid models could also be considered.

![Disclaimers
Not an in-depth briefing
SAFe treats security as one among many quality attributes
Also consider hybrid models and/or Site [Service] Reliability Engineering
Credit: Some content adapted from Scaled Agile materials
♫ = Personal “Professional” Opinion
Mark Underwood @knowlengr | Views my own | ShareAlike | v1.1
2](https://image.slidesharecdn.com/scaled-agile-for-cncf-sig-security-200420200103/75/Security-within-Scaled-Agile-2-2048.jpg)