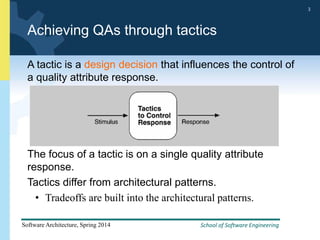
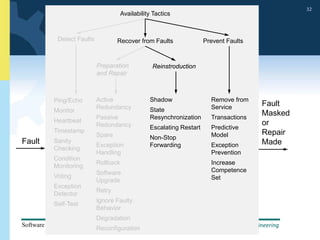
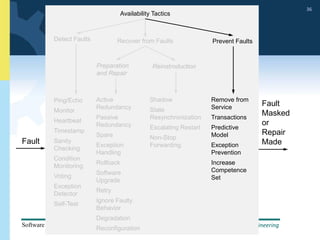
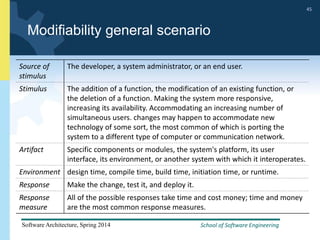
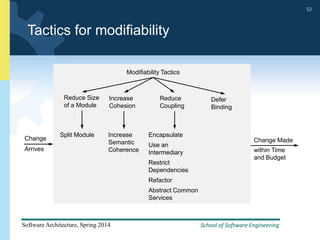
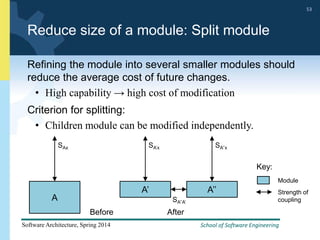
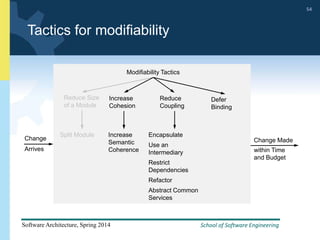
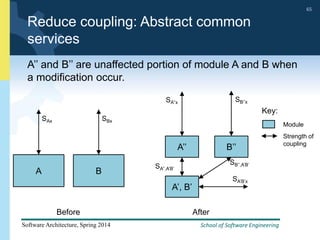
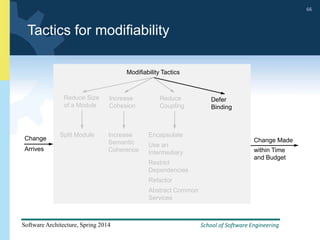
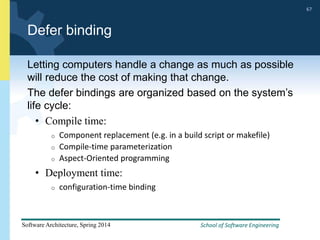
1) The document discusses various tactics that can be used to achieve software qualities like availability and modifiability. It focuses on tactics for availability, describing ways to detect faults, recover from faults, and prevent faults.
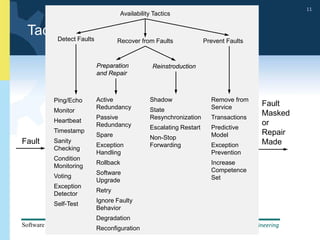
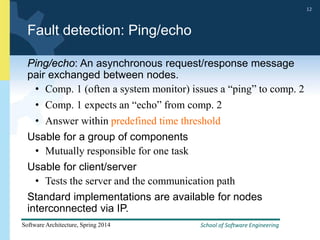
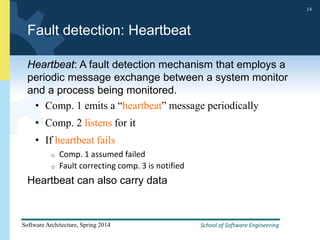
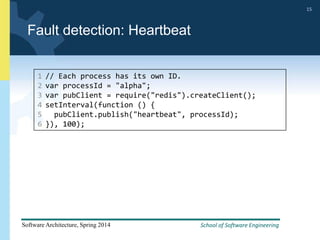
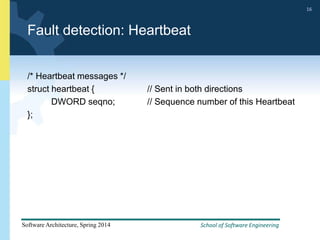
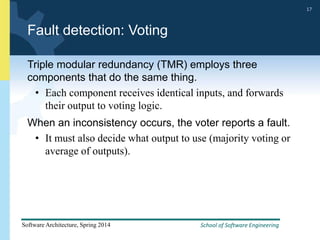
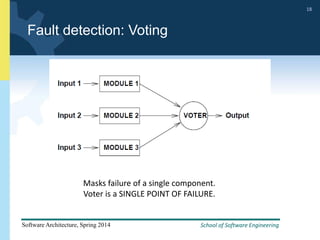
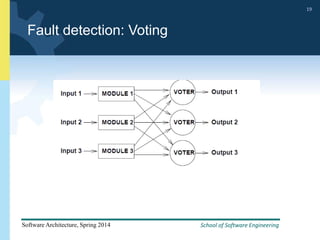
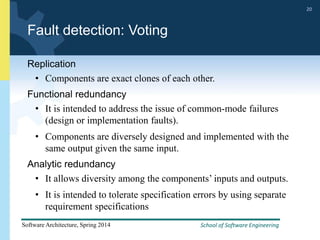
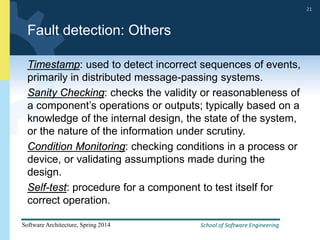
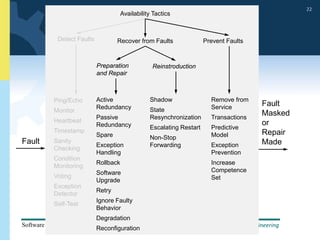
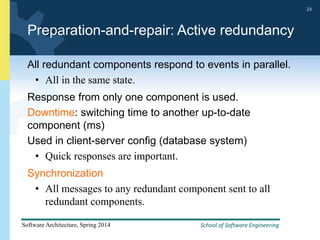
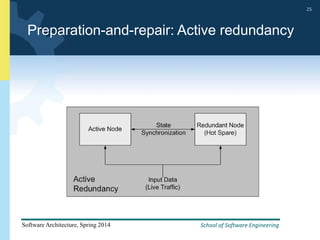
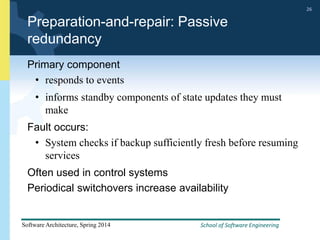
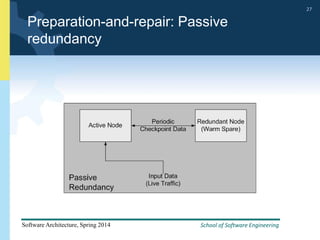
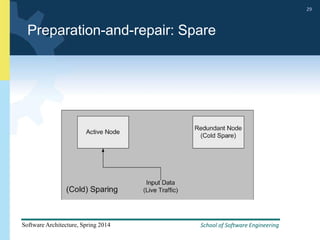
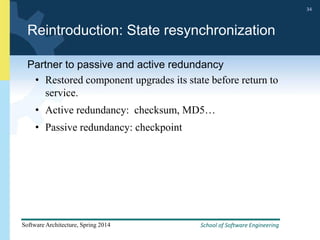
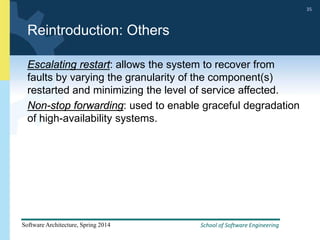
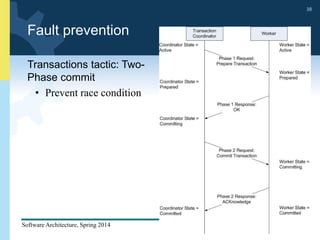
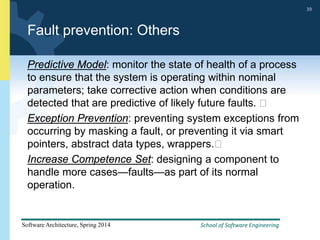
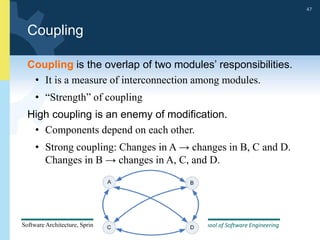
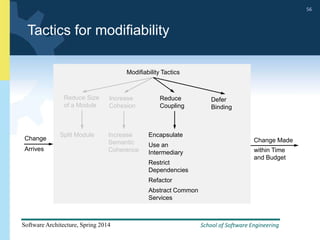
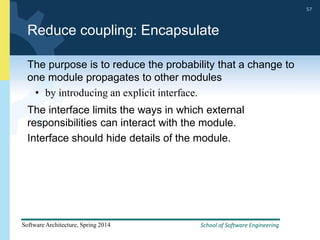
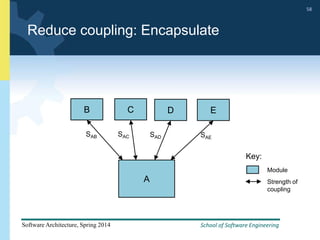
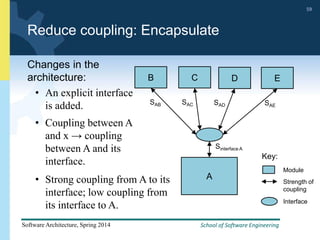
2) Tactics for availability include adding redundancy through techniques like active and passive redundancy, detecting faults through heartbeat monitoring and voting, and preventing faults using transactions and removal from service.
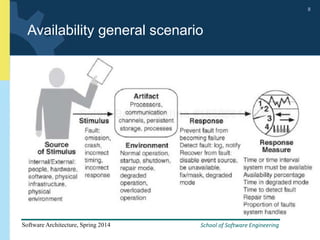
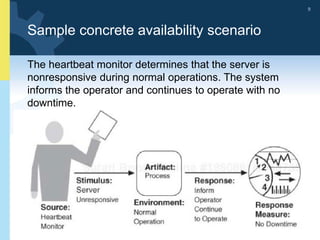
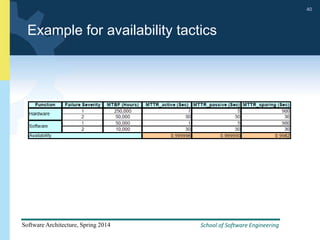
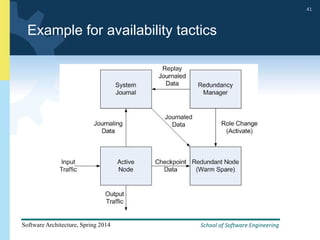
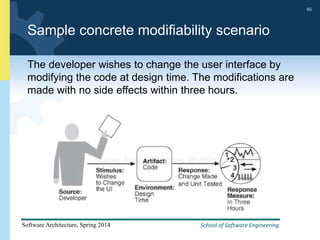
3) The document provides examples and discussion of specific availability tactics like heartbeat monitoring, active redundancy, and two-phase commit transactions. It also includes sample availability scenarios.