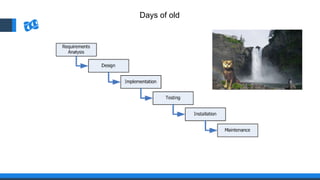
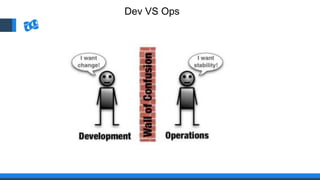
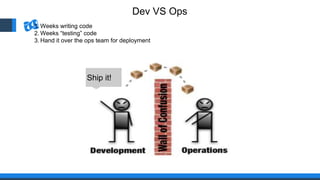
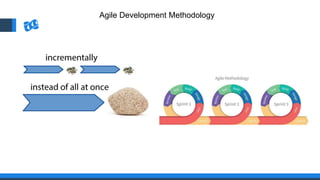
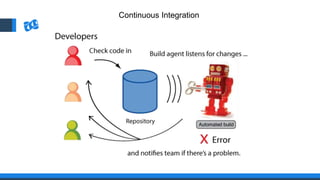
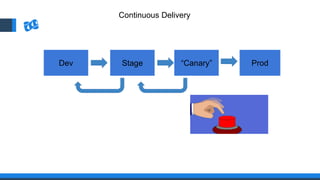
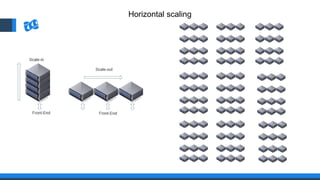
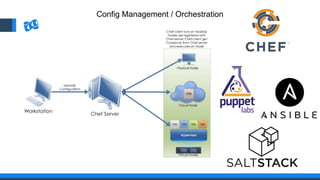
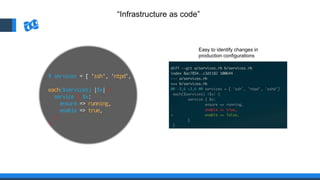
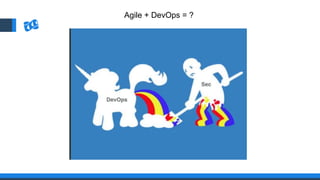
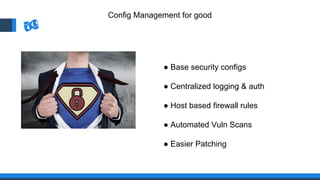
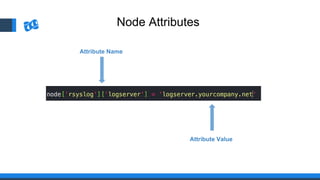
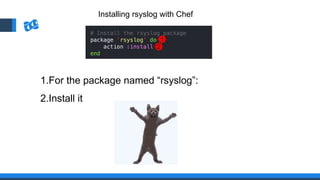
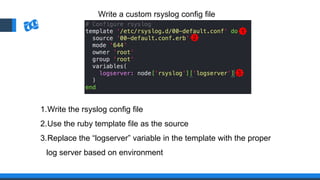
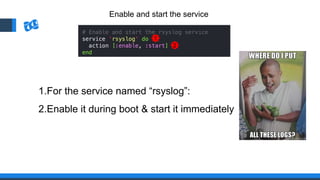
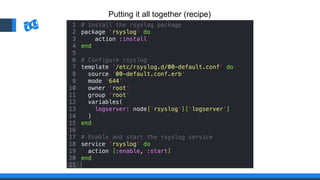
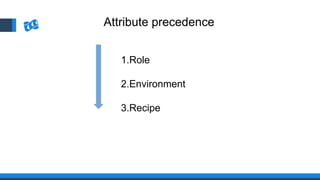
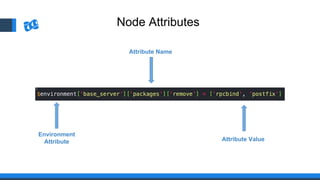
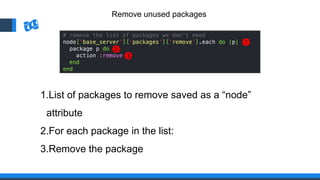
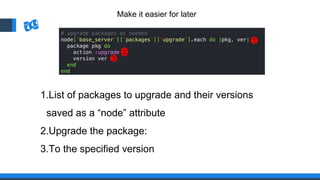
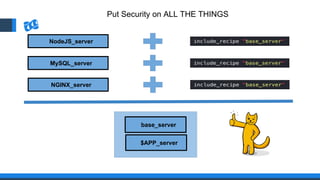
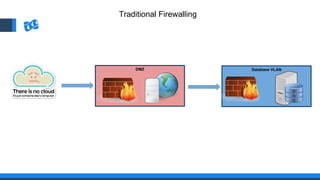
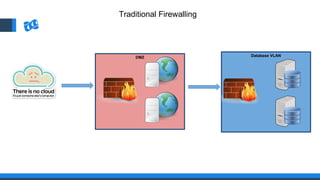
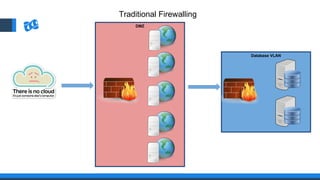
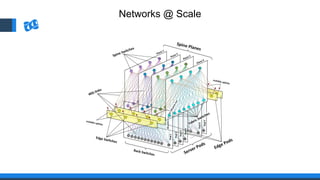
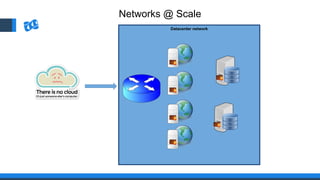
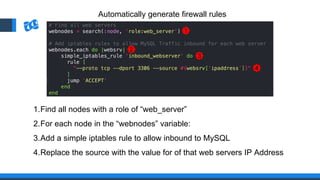
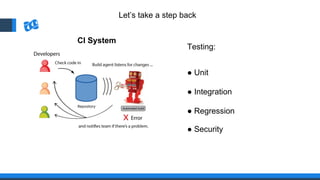
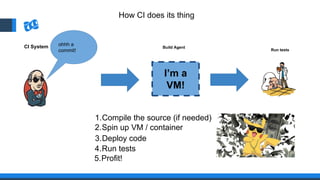
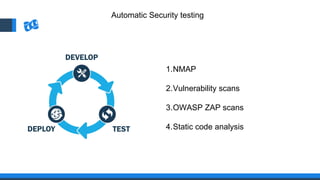
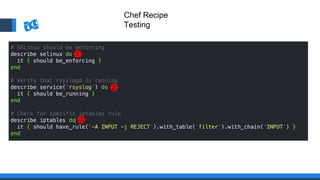
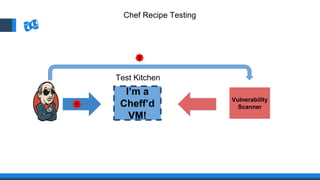
The document discusses the integration of DevOps and Agile methodologies in software development, highlighting the challenges they pose to security practices. It emphasizes the importance of using configuration management and automated security tools to enhance security throughout the software lifecycle. Furthermore, it provides practical examples and techniques for implementing robust security measures in DevOps environments.