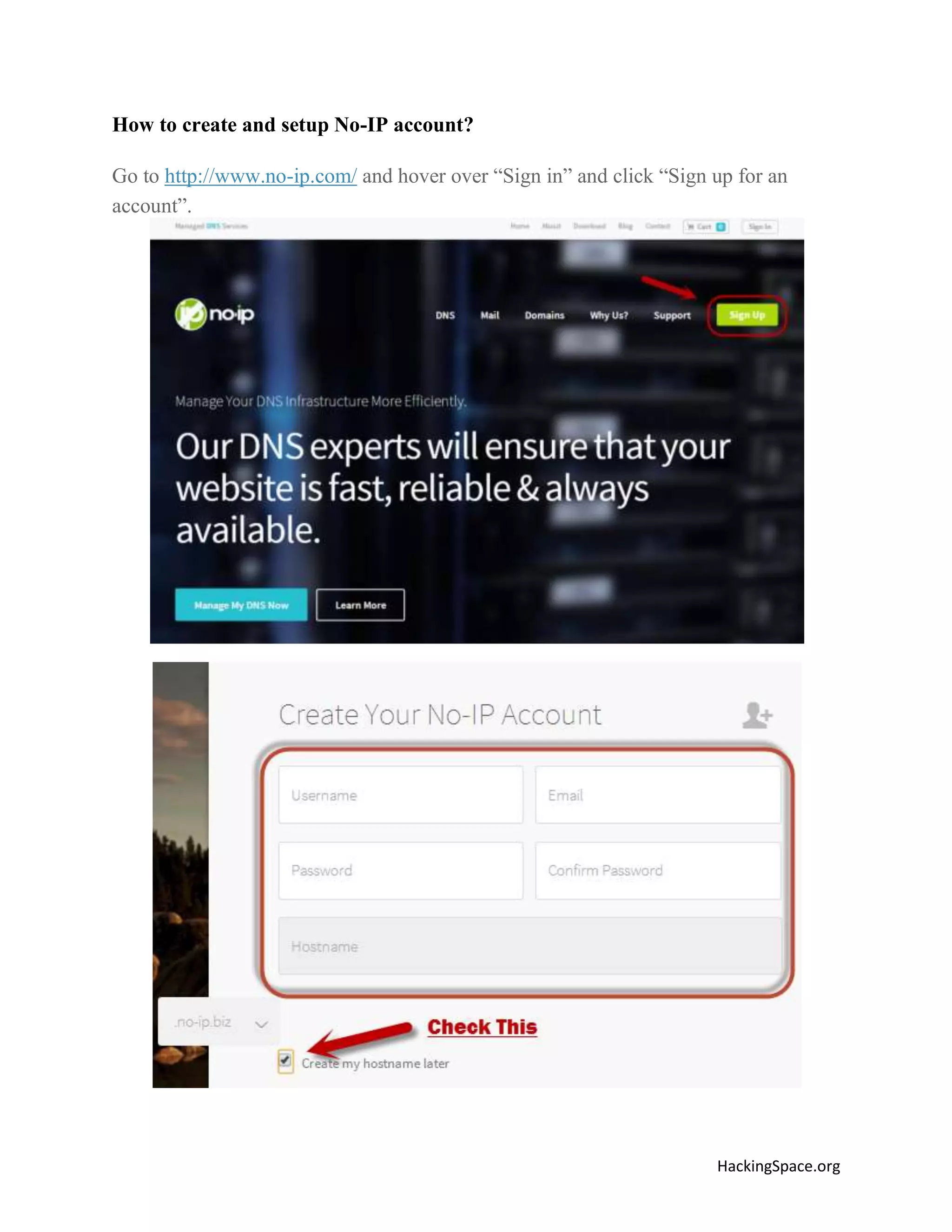
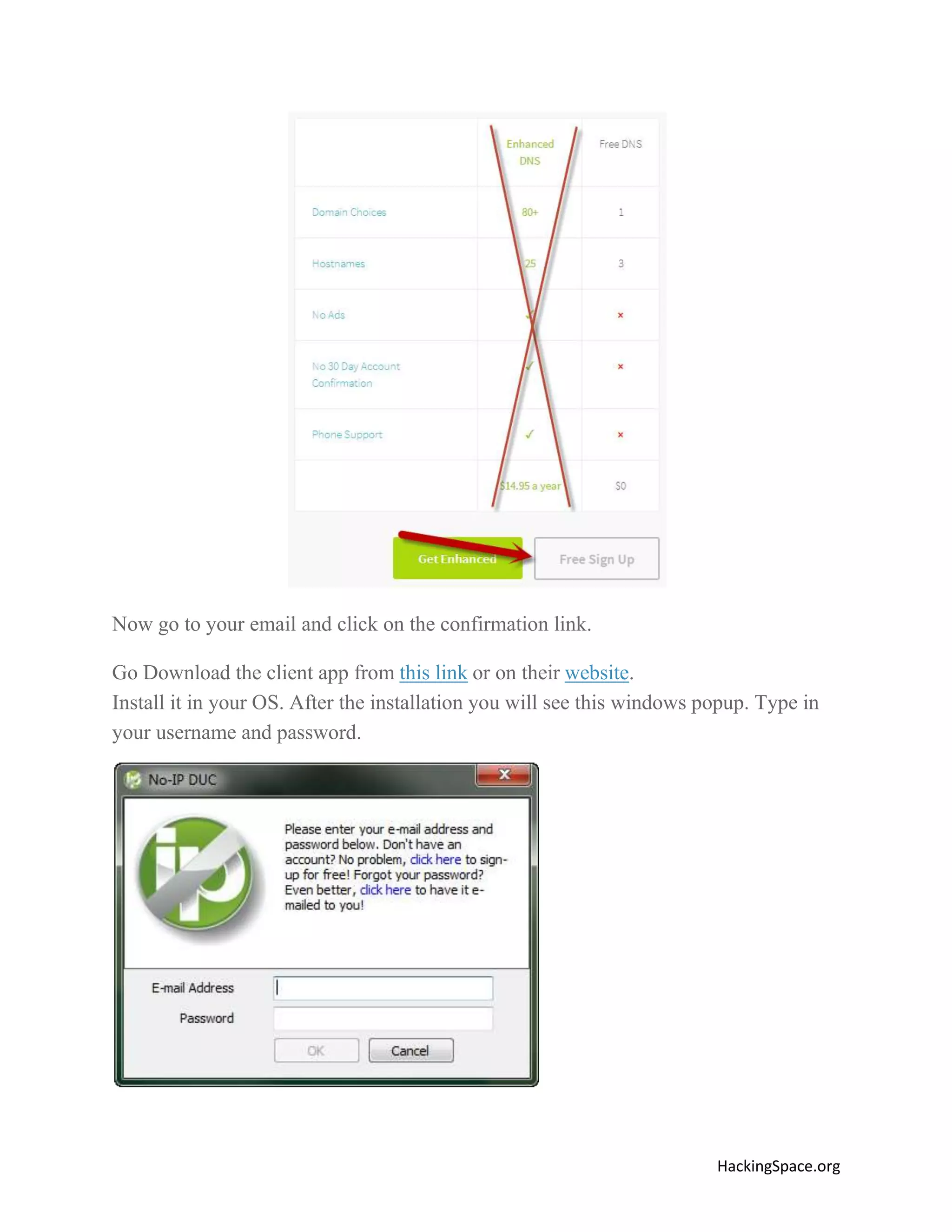
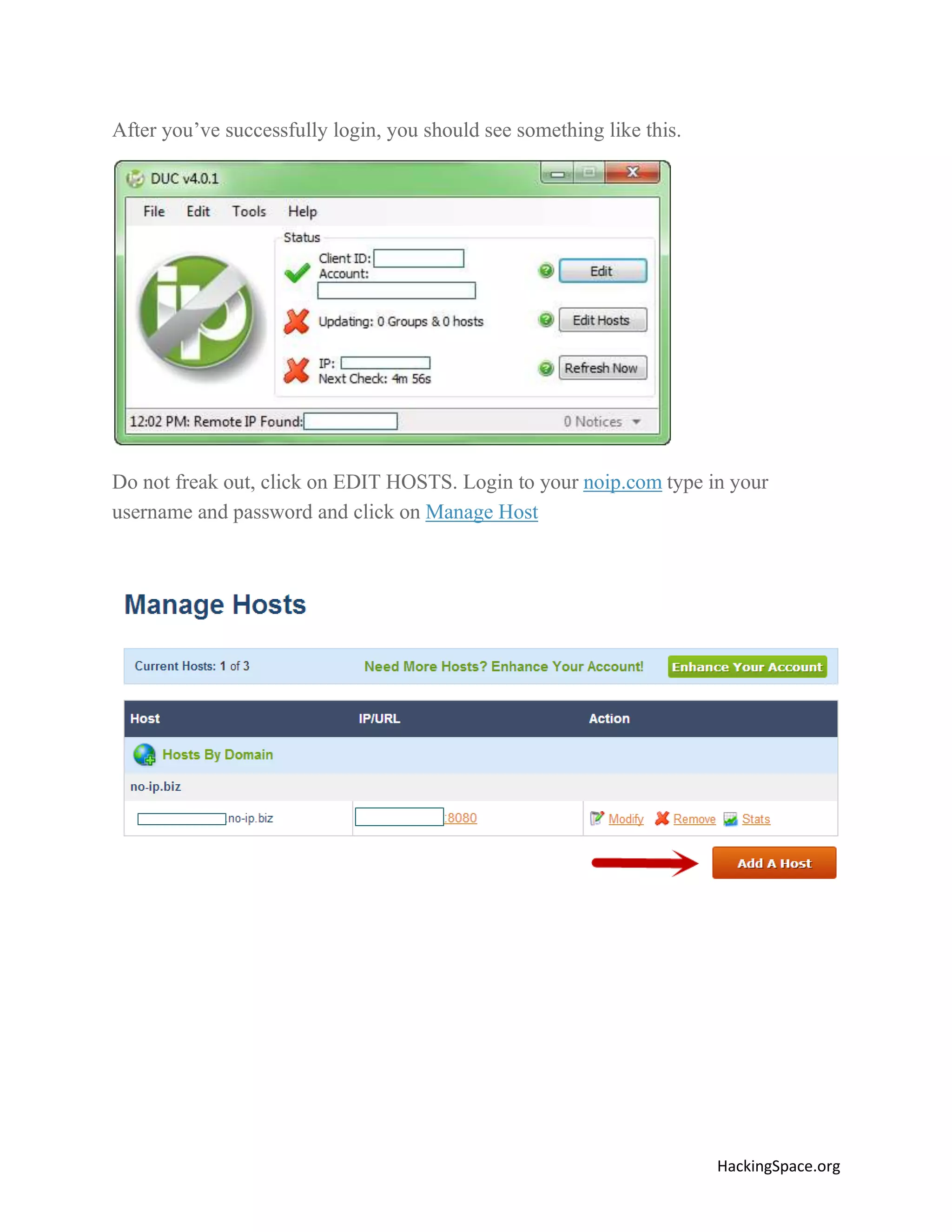
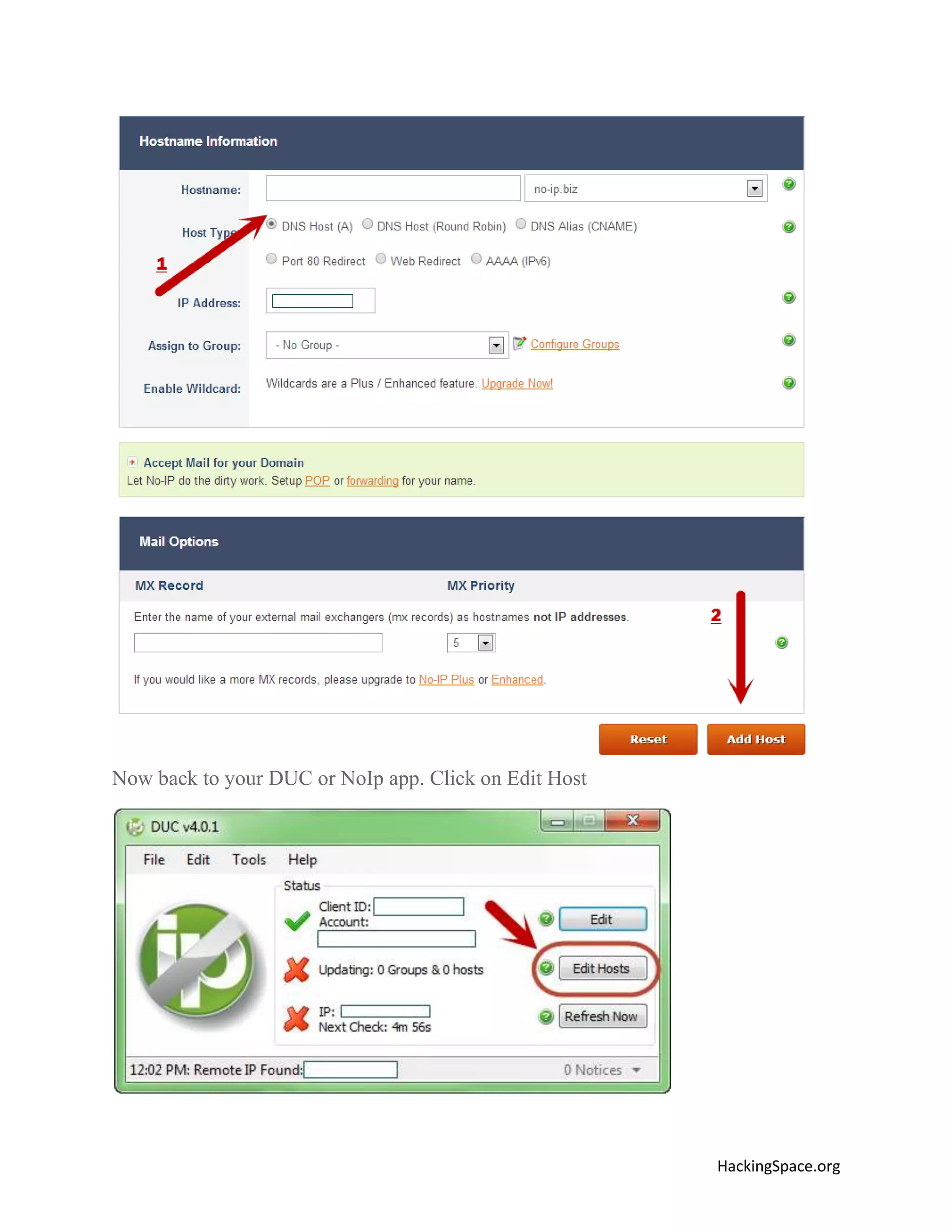
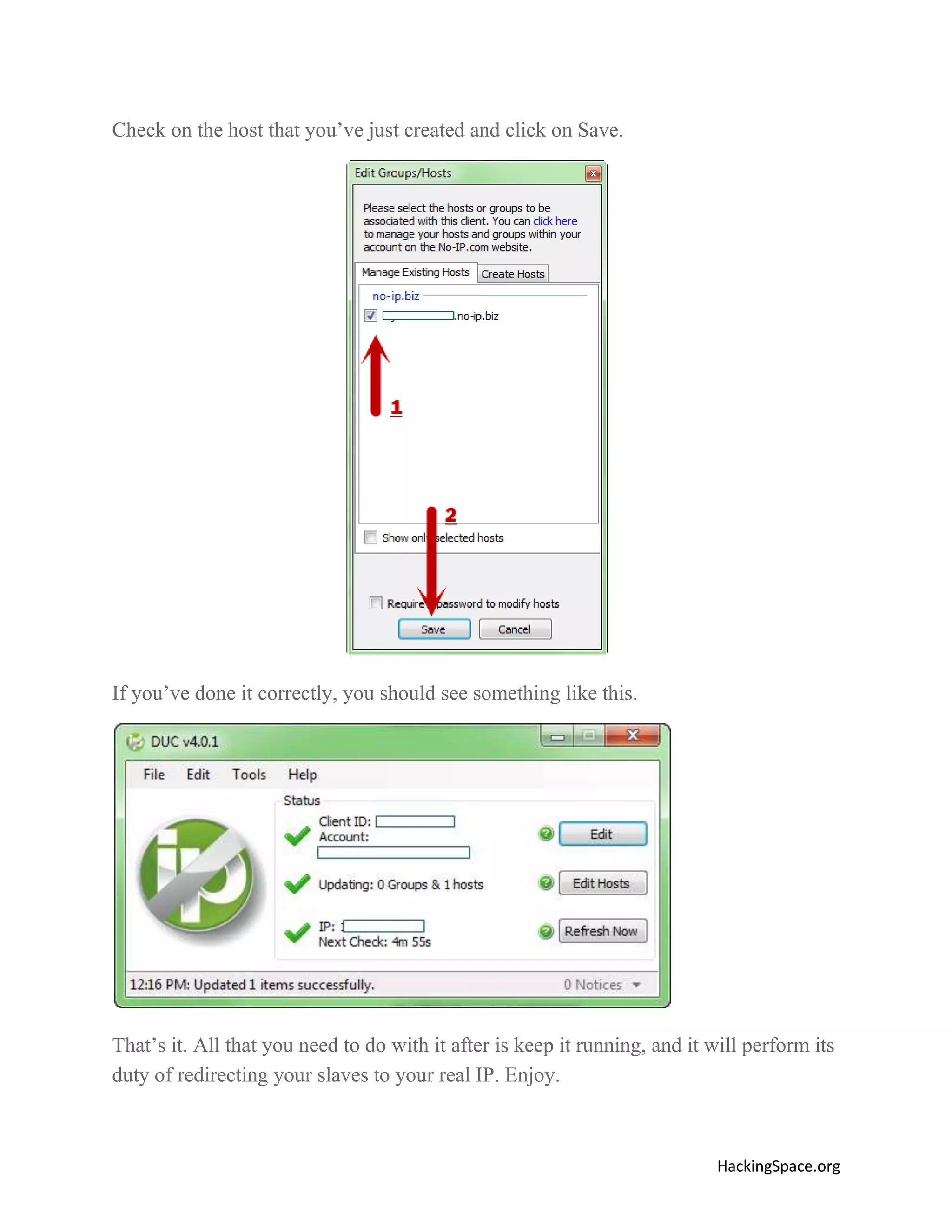
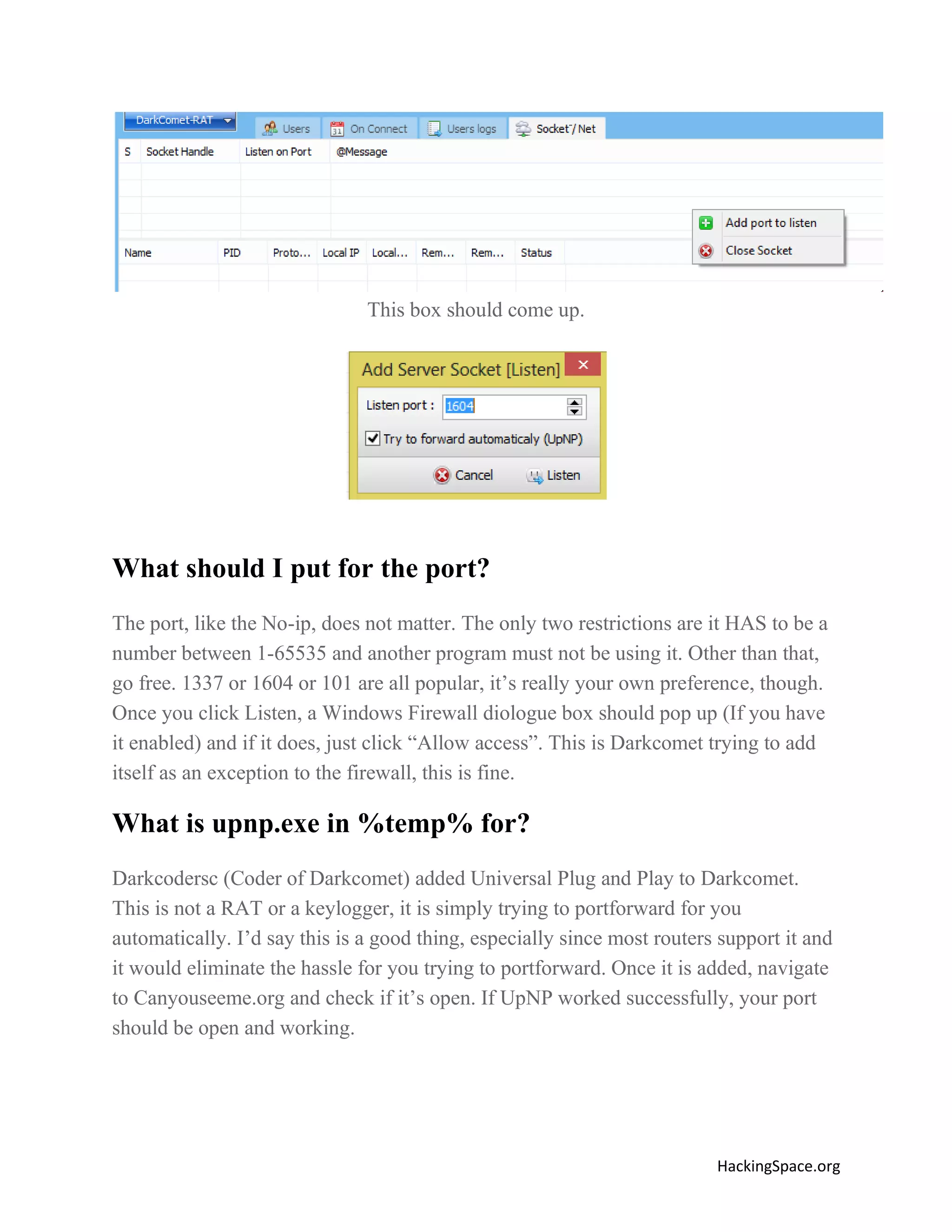
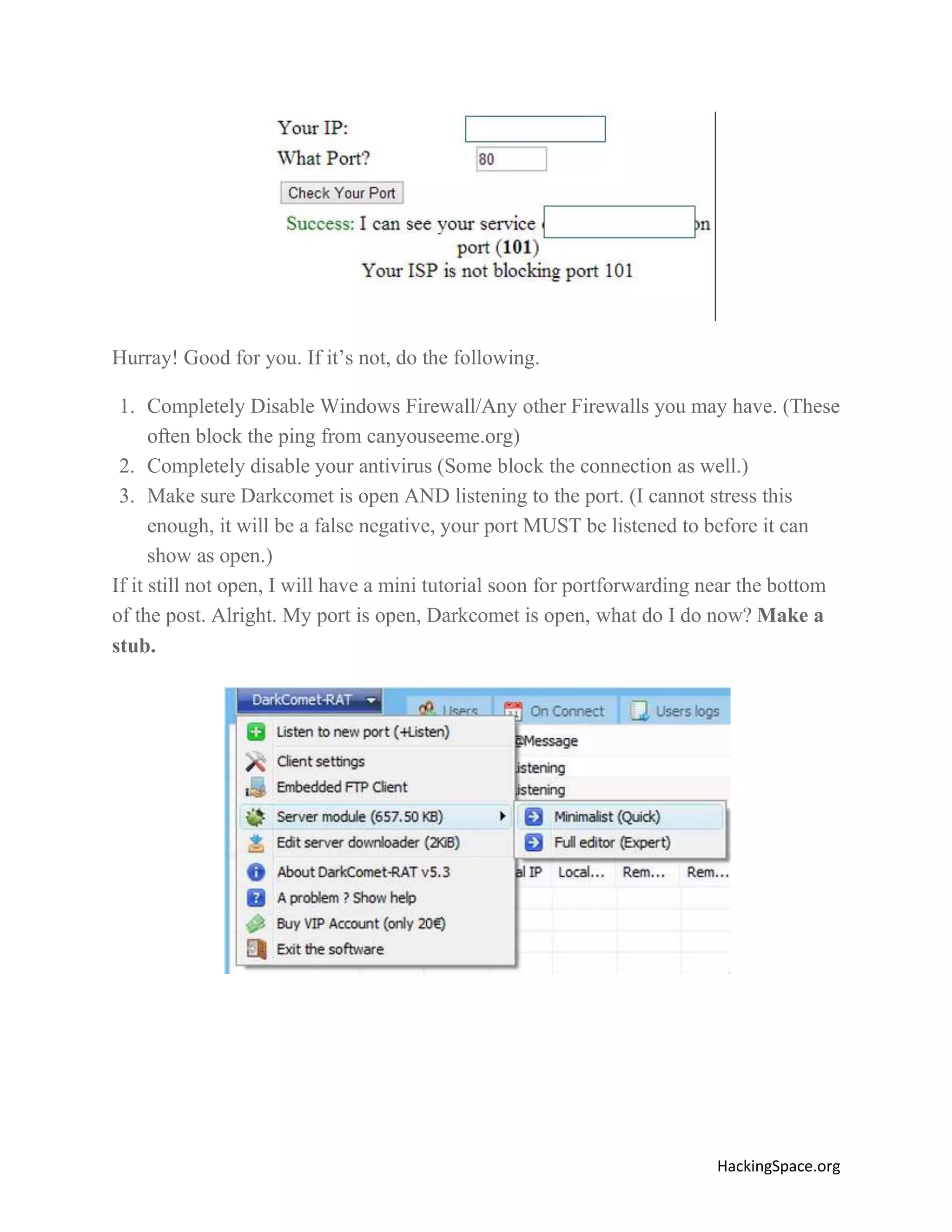
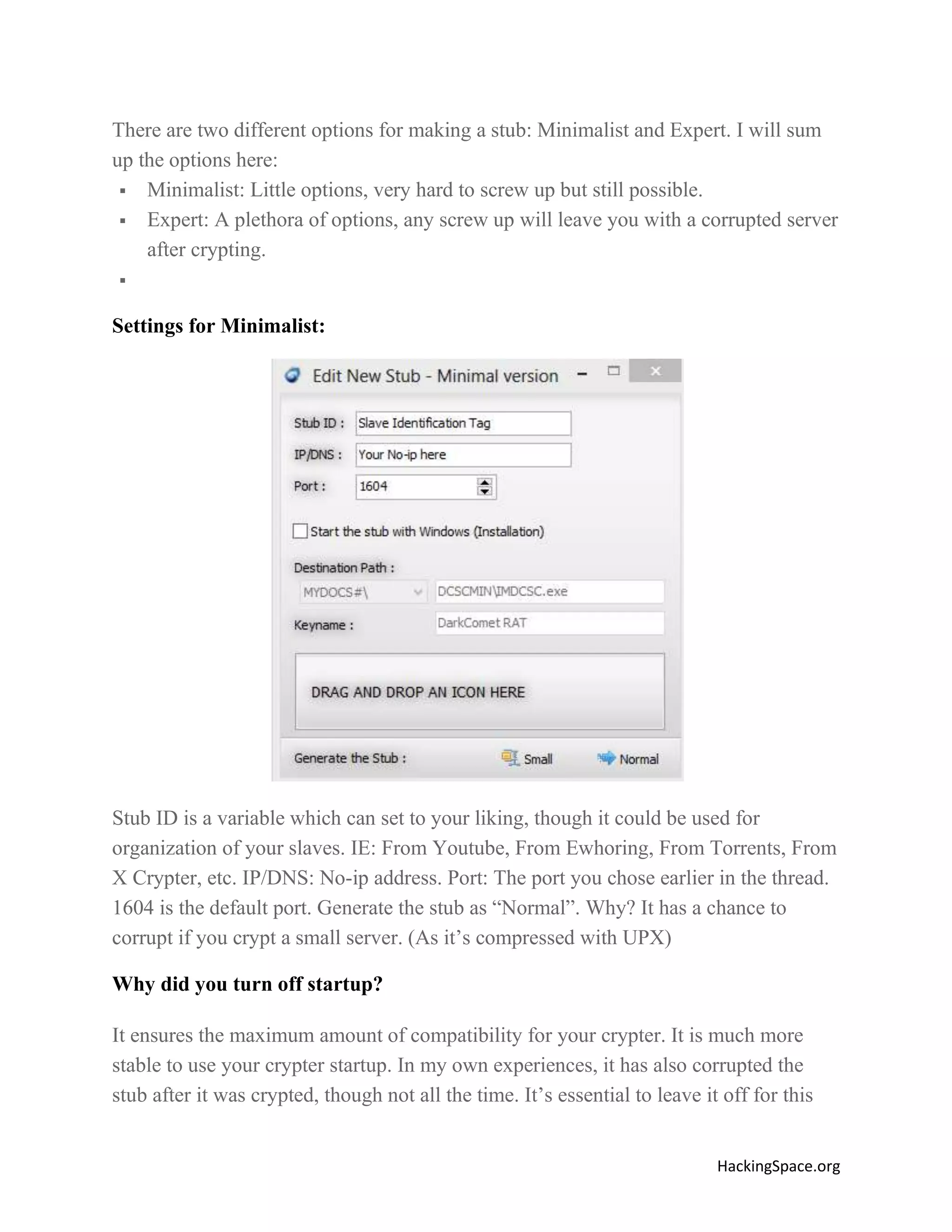
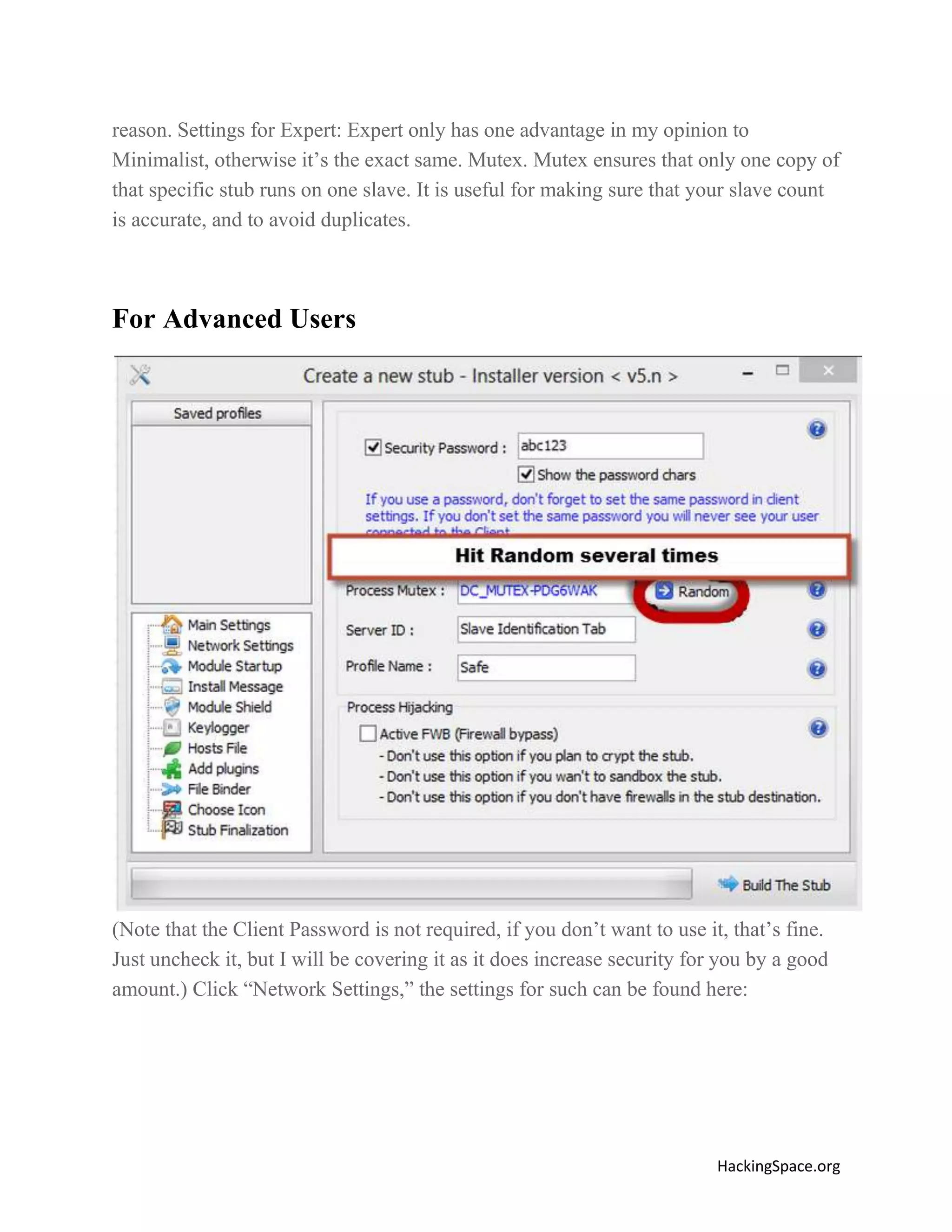
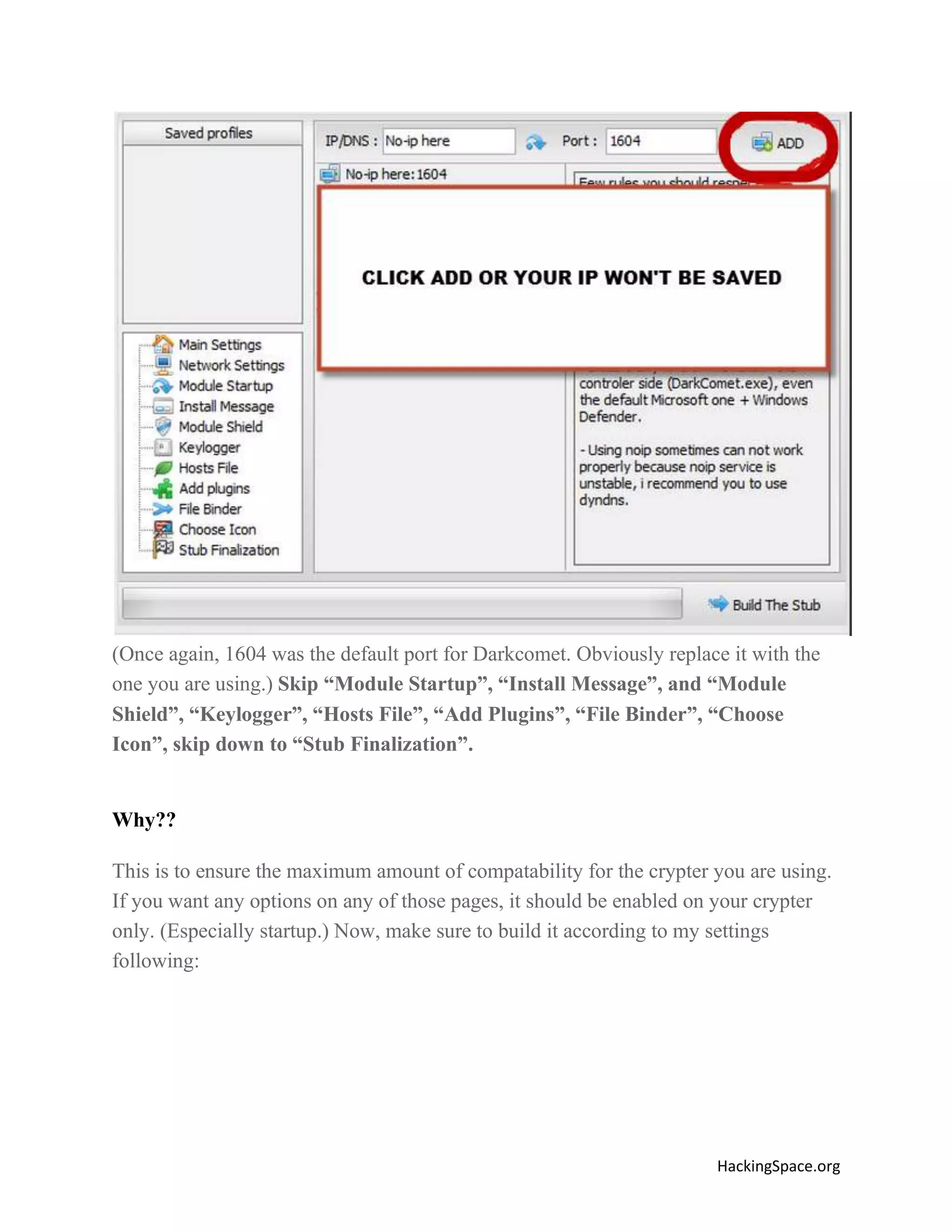
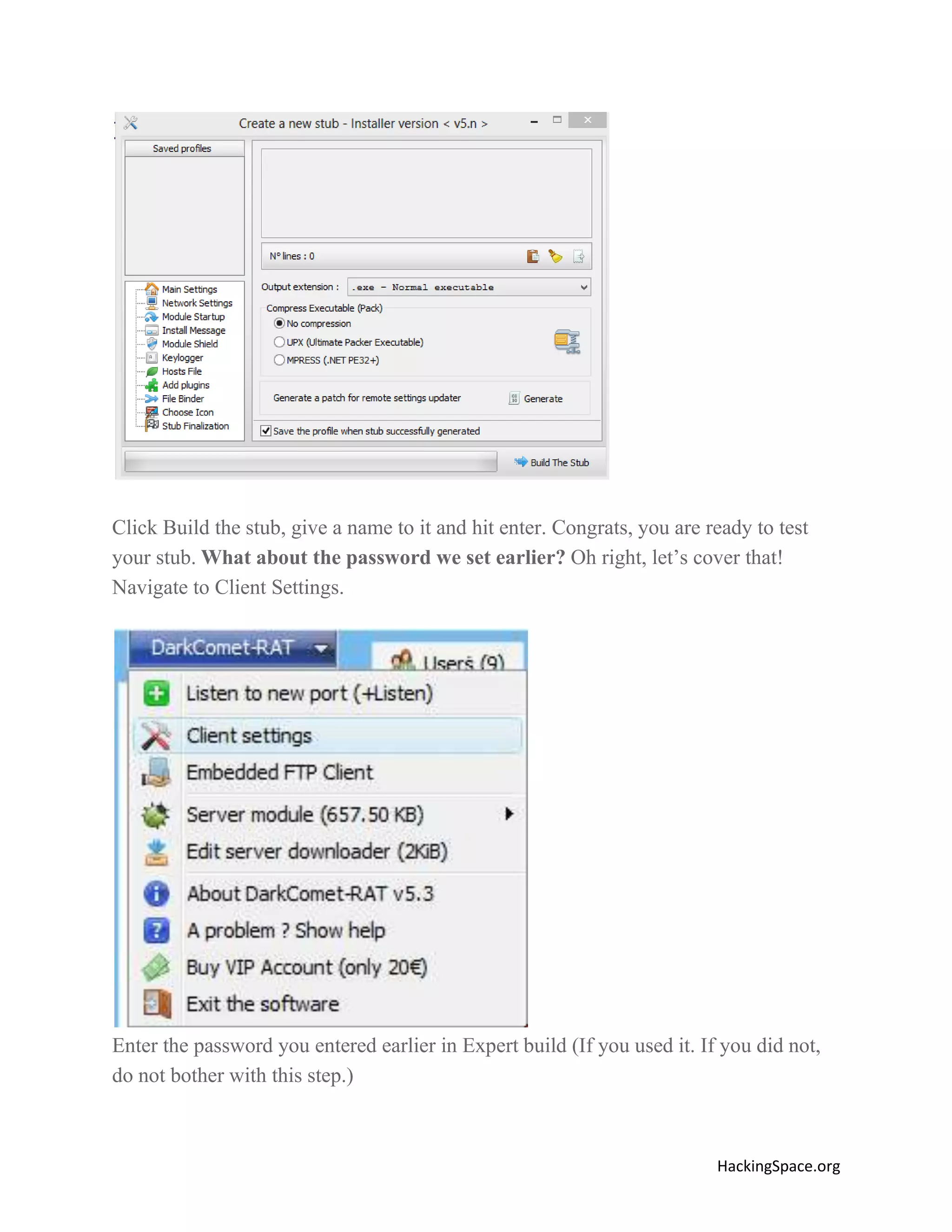
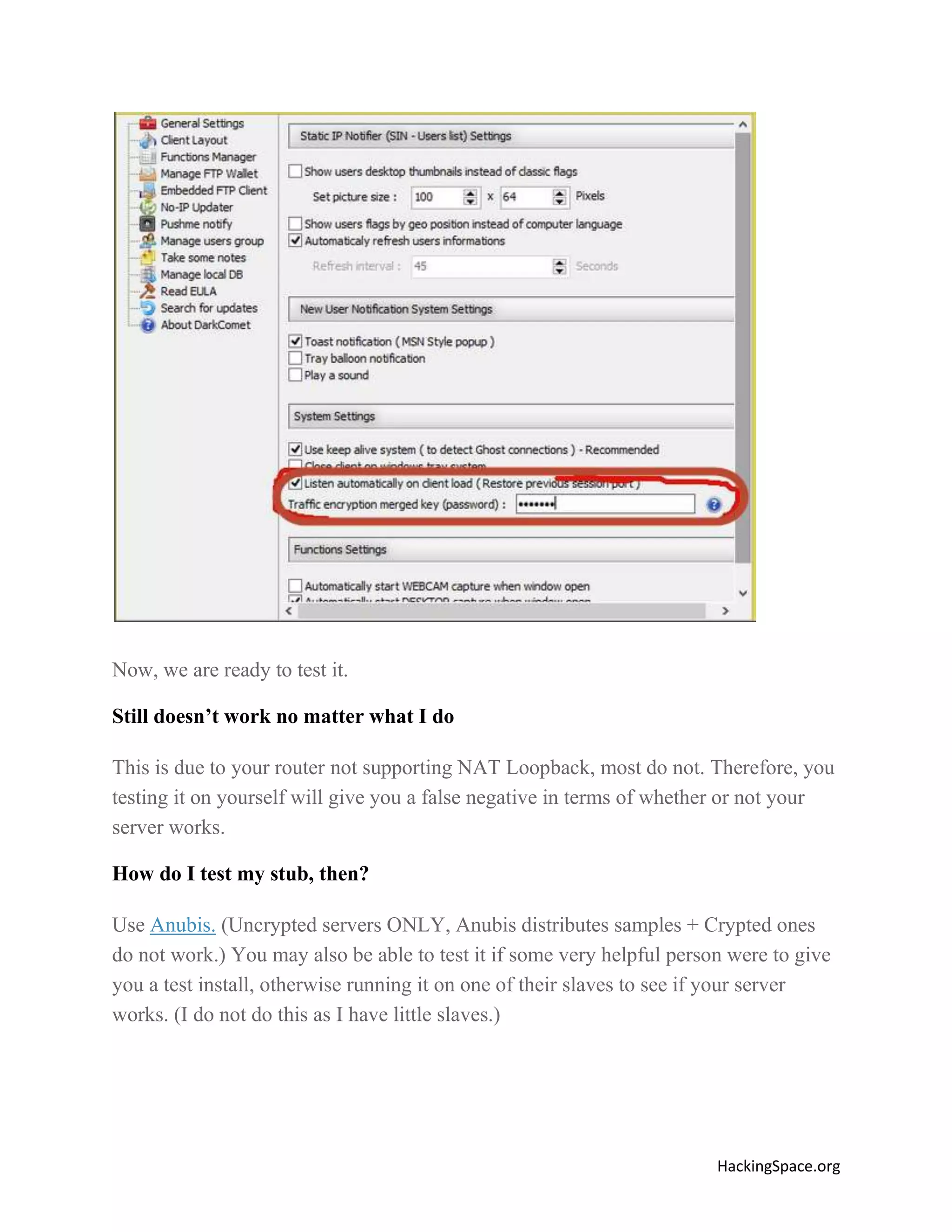
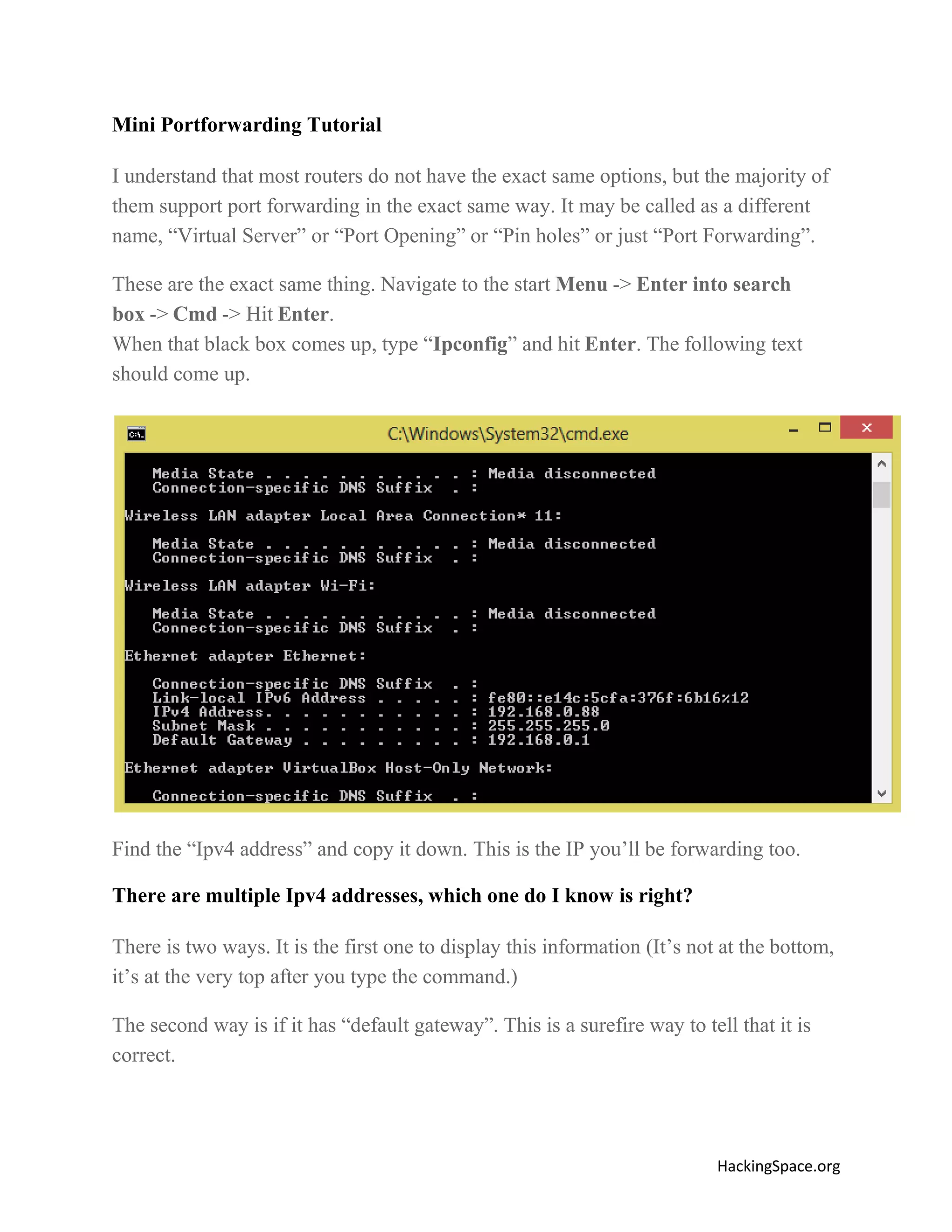
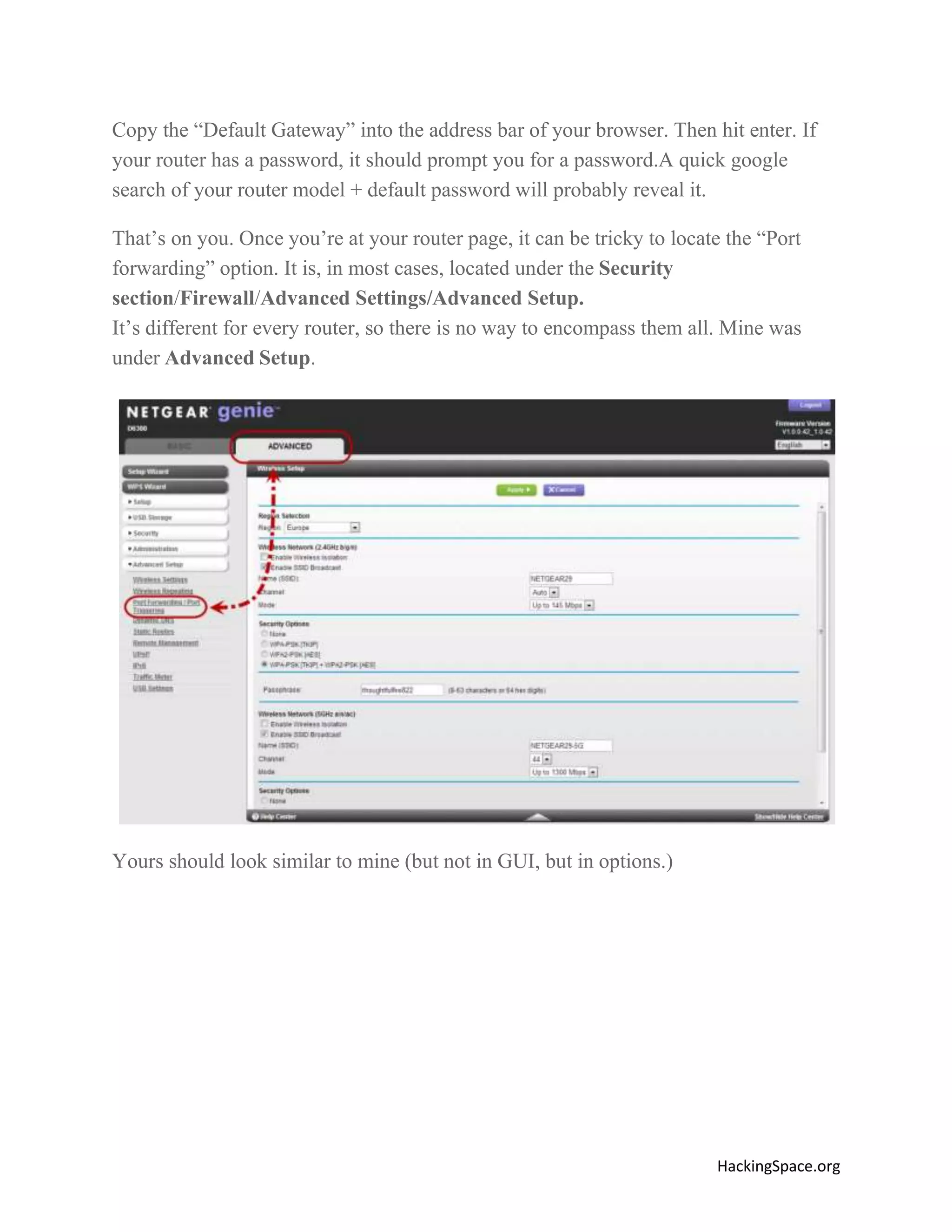
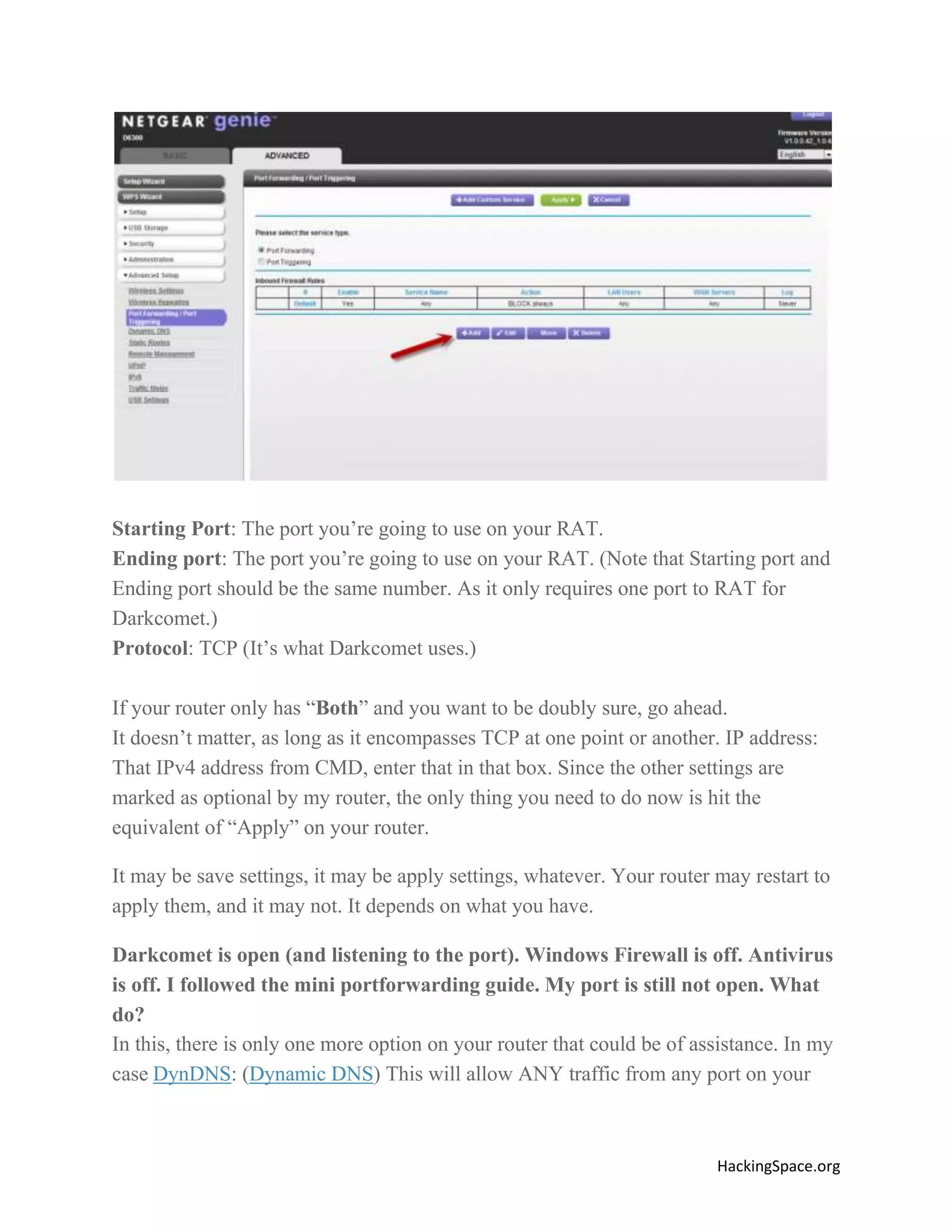
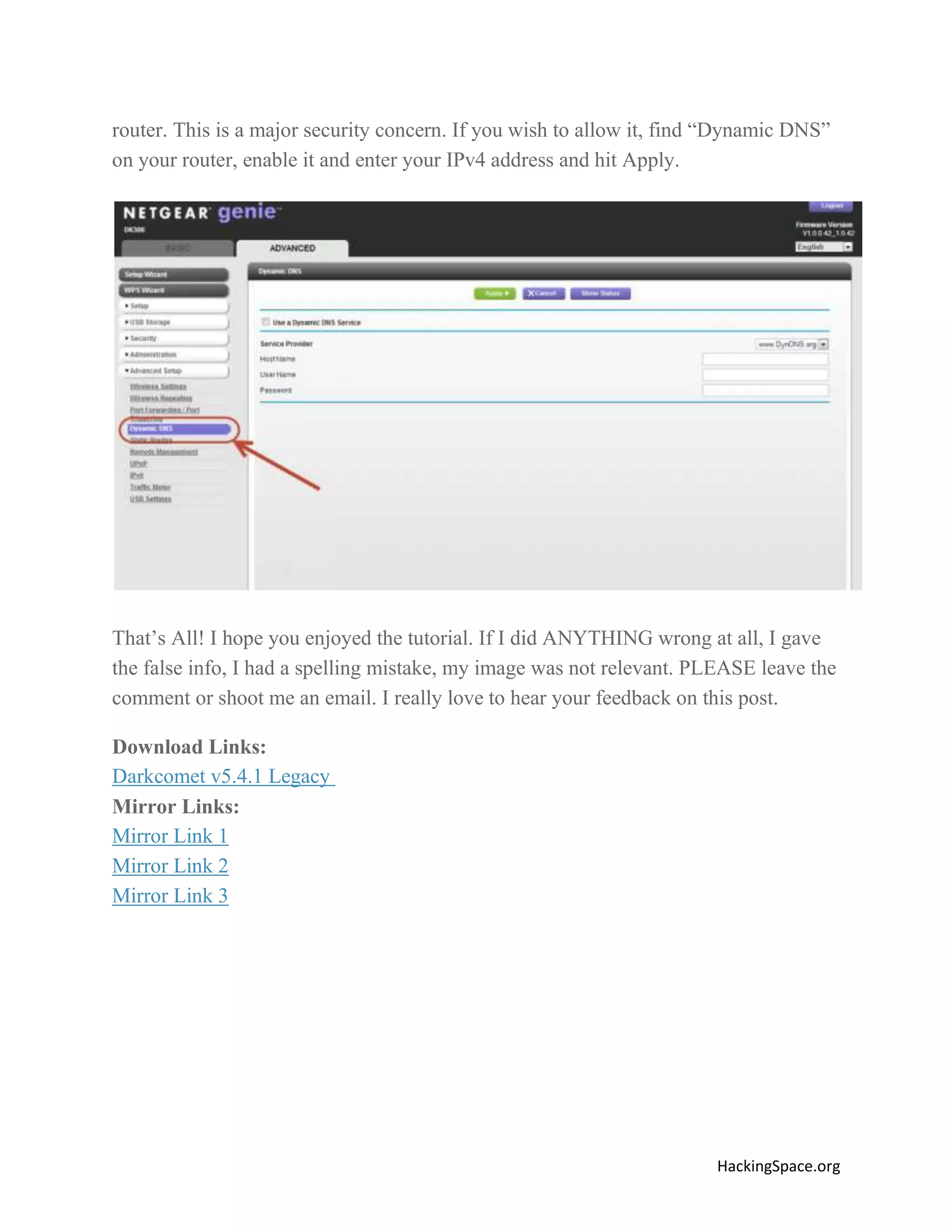
The document provides a comprehensive guide on setting up DarkComet RAT, a remote administration tool for Windows, emphasizing its functionality and reputation in remote control and monitoring. It outlines the requirement of a no-ip account for maintaining IP address consistency and details the steps for installation and configuration of both DarkComet and no-ip. Additionally, it offers troubleshooting advice for common issues related to antivirus and router configurations to ensure successful operation.