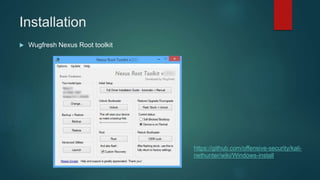
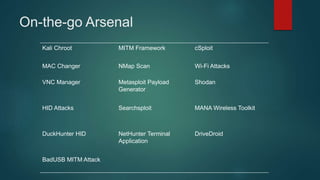
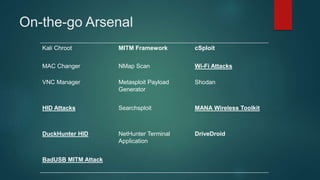
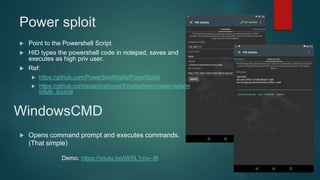
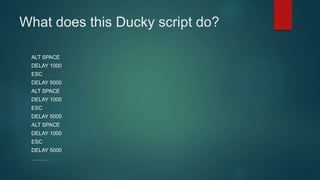
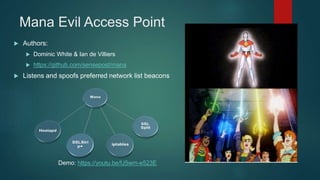
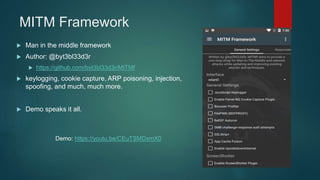
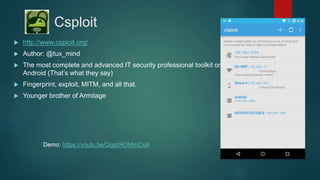
The document provides an overview of Kali Nethunter, an Android ROM overlay with features for information security, including wireless injection and USB HID attacks. It lists compatible devices and tools such as Metasploit, VNC manager, and the Duckhunter script generator, while also mentioning advantages and disadvantages of various tools. The author invites questions and provides contact information at the end.