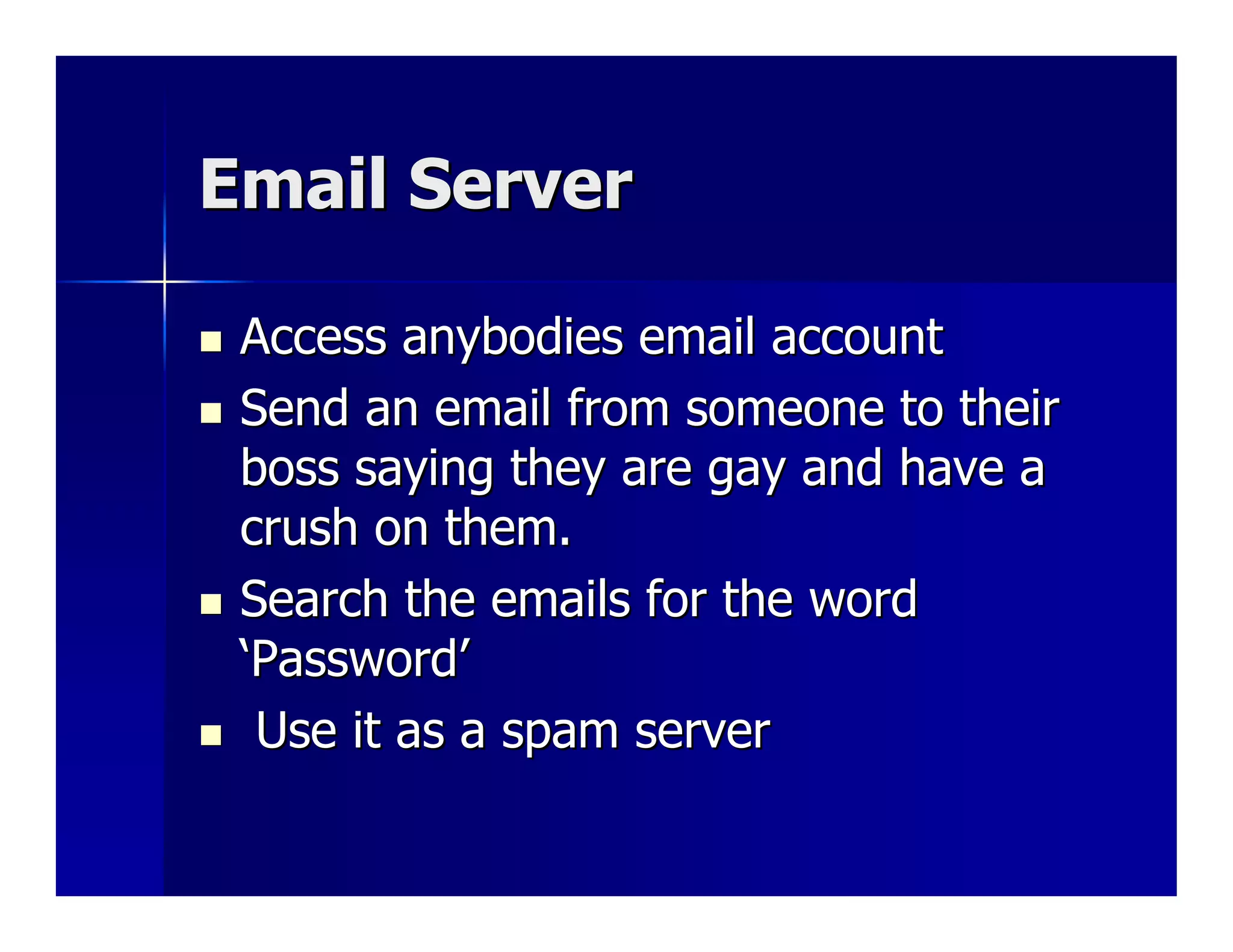
The talk by Wicked Clown at BSides London discusses significant security vulnerabilities in Remote Desktop Protocol (RDP) sessions, highlighting how users can execute unauthorized commands despite group policy restrictions. The session includes demos on exploiting weak passwords and escalating privileges to gain full access to systems. The speaker emphasizes the risks of overlooked security settings and their potential impact on organizations.