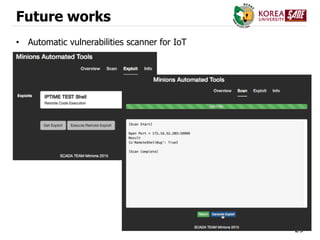
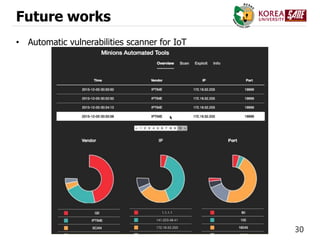
The document discusses a case study of a DDoS attack on SK Broadband in 2014, which utilized infected IoT devices to generate 15 million packets per second, causing significant internet disruption. It analyzes the vulnerabilities of various IoT devices, such as home routers, network switches, and CCTV systems, revealing how they can be exploited for attacks. The conclusion emphasizes the need for improved defenses and automated vulnerability scanners to combat the growing threats posed by IoT devices.

![3
Internet down after cyberattack
29 November, 2014
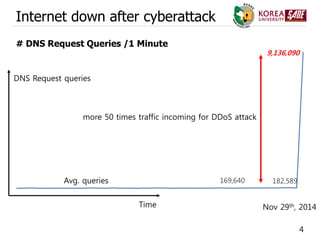
15,000,000 packets per second
SK Broadband, one of the largest providers of broadband Internet access in
Korea, was attacked by the Distributed Denial-of-Service (DDoS) over the
weekend, disconnecting its Internet services for about an hour.
DDoS is a kind of cyberattack in which multiple compromised systems are
used to target a single network or a machine and make it unavailable to
users.
On Saturday at 10:55 a.m., the traffic on SK Broadband’s DNS server soared
up to 15 million packets per second (PPS), from its usual average of about 1
million PPS. PPS refers to the number of database transactions performed
per second.
SK Broadband users near Seocho and Dongjak distrcts in southern Seoul
were without Internet from 10:55 a.m. until 12:05 p.m. on Saturday.
[1] Internet down after cyberattack (JOONGANG DAILY, Dec 2014)](https://image.slidesharecdn.com/ddosattackstodnsusinginfectediotdevices-151215052328/85/DDoS-Attack-on-DNS-using-infected-IoT-Devices-3-320.jpg)
![6
How to detect DDoS attack
• Our own <Near-Real Time DNS Query Analyzing System for Detecting
DDoS Attacks>
[2] Study on the near-real time DNS query analyzing system for DNS amplification attacks, KIISC (2015)](https://image.slidesharecdn.com/ddosattackstodnsusinginfectediotdevices-151215052328/85/DDoS-Attack-on-DNS-using-infected-IoT-Devices-6-320.jpg)

![8
Benefits of IoT device for DDoS
Why do attacker want to use IoT device for DDoS attack?
Any TIME
communication
Any THING
communication
Any PLACE
communication
• on the move
• night
• daytime
• outdoor
• indoor (away from the computer)
• at the computer
• between computers
• human to human, not using a computer
• human to thing, using generic equipment
• thing to thing
[3] The new dimension introduced in the Internet of things - Recommendation ITU-T Y.2060 (06/2012)](https://image.slidesharecdn.com/ddosattackstodnsusinginfectediotdevices-151215052328/85/DDoS-Attack-on-DNS-using-infected-IoT-Devices-8-320.jpg)
![9
Top 10 IoT Vulnerabilities (2014)
A list of the top 10 internet of things vulnerabilities
[4] OWASP Internet of Things Project (https://www.owasp.org/index.php/OWASP_Internet_of_Things_Project)
Rank Title
I1 Insecure Web Interface
I2 Insufficient Authentication/Authorization
I3 Insecure Network Services
I4 Lack of Transport Encryption
I5 Privacy Concerns
I6 Insecure Cloud Interface
I7 Insecure Mobile Interface
I8 Insufficient Security Configurability
I9 Insecure Software/Firmware
I10 Poor Physical Security](https://image.slidesharecdn.com/ddosattackstodnsusinginfectediotdevices-151215052328/85/DDoS-Attack-on-DNS-using-infected-IoT-Devices-9-320.jpg)


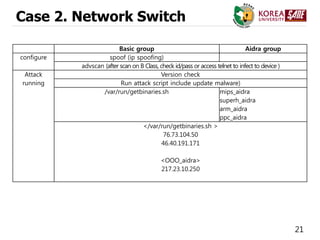
![19
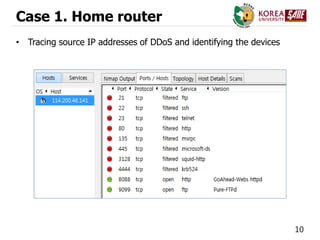
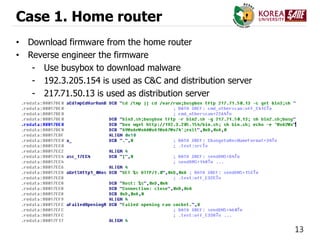
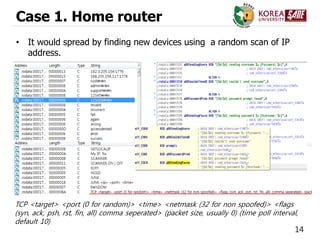
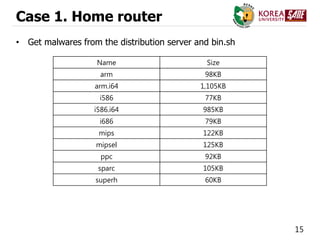
Case 2. Network Switch
• Source code
[5] Lightaidra, https://github.com/eurialo/lightaidra](https://image.slidesharecdn.com/ddosattackstodnsusinginfectediotdevices-151215052328/85/DDoS-Attack-on-DNS-using-infected-IoT-Devices-19-320.jpg)
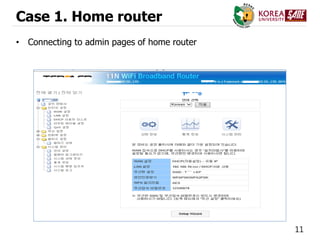
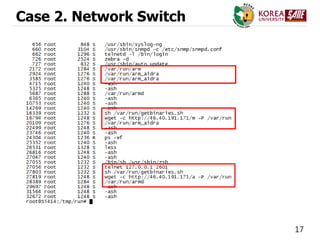
![20
Case 2. Network Switch
Basic group Aidra group
File list arm, mips, mipsel, ppc,s,sh
mips_aidra, superh_aidra, arm_aidra, mipsel
_aidra
C&C or
distribution
Server IP
automation.whatismyip.com
(72.233.89.199)
IRC connect
76.73.104.50:6667
76.73.103.60:6667
76.73.104.243:6667
205.188.14.92:6667
Command list
Access Commands (login/logout)
Miscs Commands (run/check)
Scan Commands (scan)
DDoS Commands
.spoof <IP> : ip spoofing attack
.synflood , .nssynflood
.ackflood, .nsackflood
Attack Command
.synflood
.*flood->[m,a,p,s,x]
<example>
.nssynflood->s <host> <port> <secs>
* : syn, nssyn, ack, nsack
a=arm / p=ppc /
s=superh / x=x86](https://image.slidesharecdn.com/ddosattackstodnsusinginfectediotdevices-151215052328/85/DDoS-Attack-on-DNS-using-infected-IoT-Devices-20-320.jpg)
![23
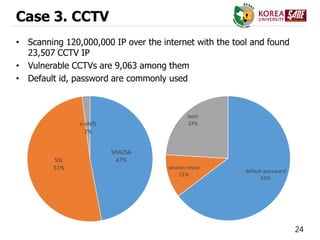
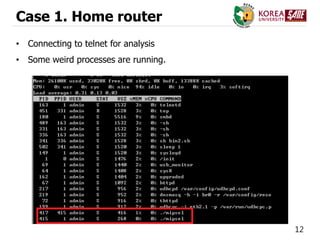
Case 3. CCTV
• Malwares on CCTV
- password is changed
- update with infected firmware (get root permission)
• rtsp://<CCTV IP>/trackID=1&basic_auth=base64([id:pw])
- root / (empty)
- root / root
- root / admin
- admin / admin
- admin / 1234
- admin / 12345
- admin / smcadmin
- admin / (empty)](https://image.slidesharecdn.com/ddosattackstodnsusinginfectediotdevices-151215052328/85/DDoS-Attack-on-DNS-using-infected-IoT-Devices-23-320.jpg)