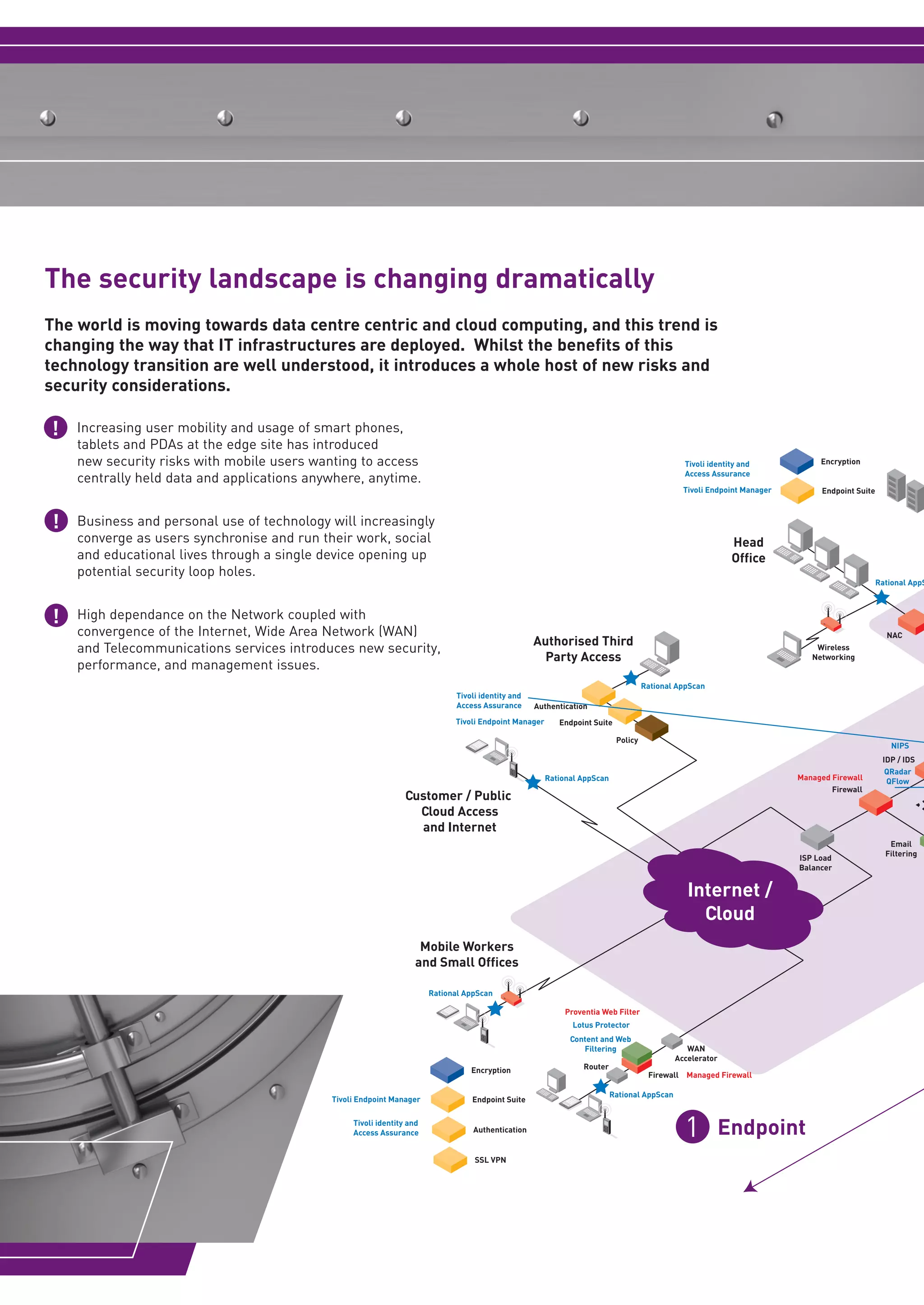
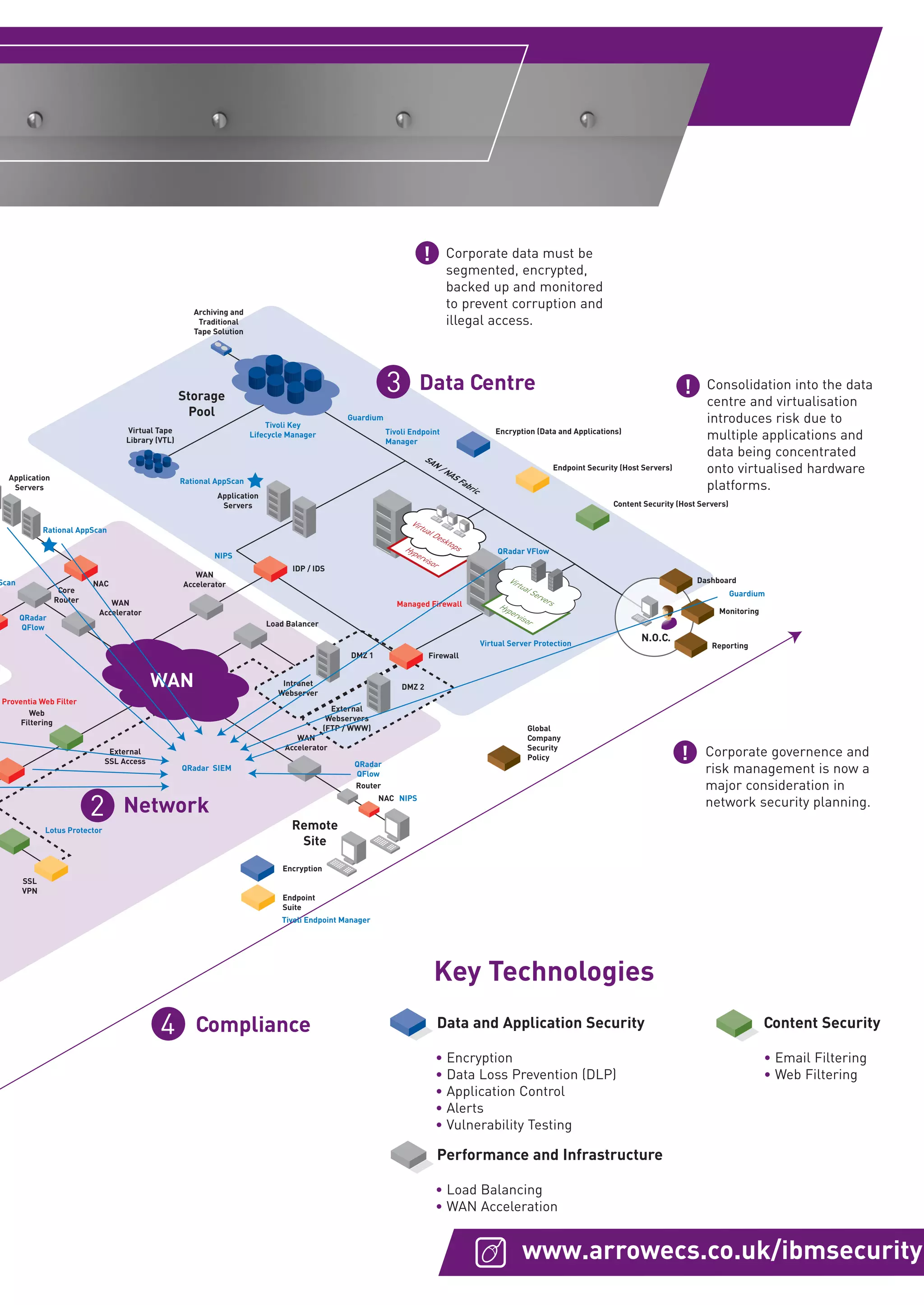
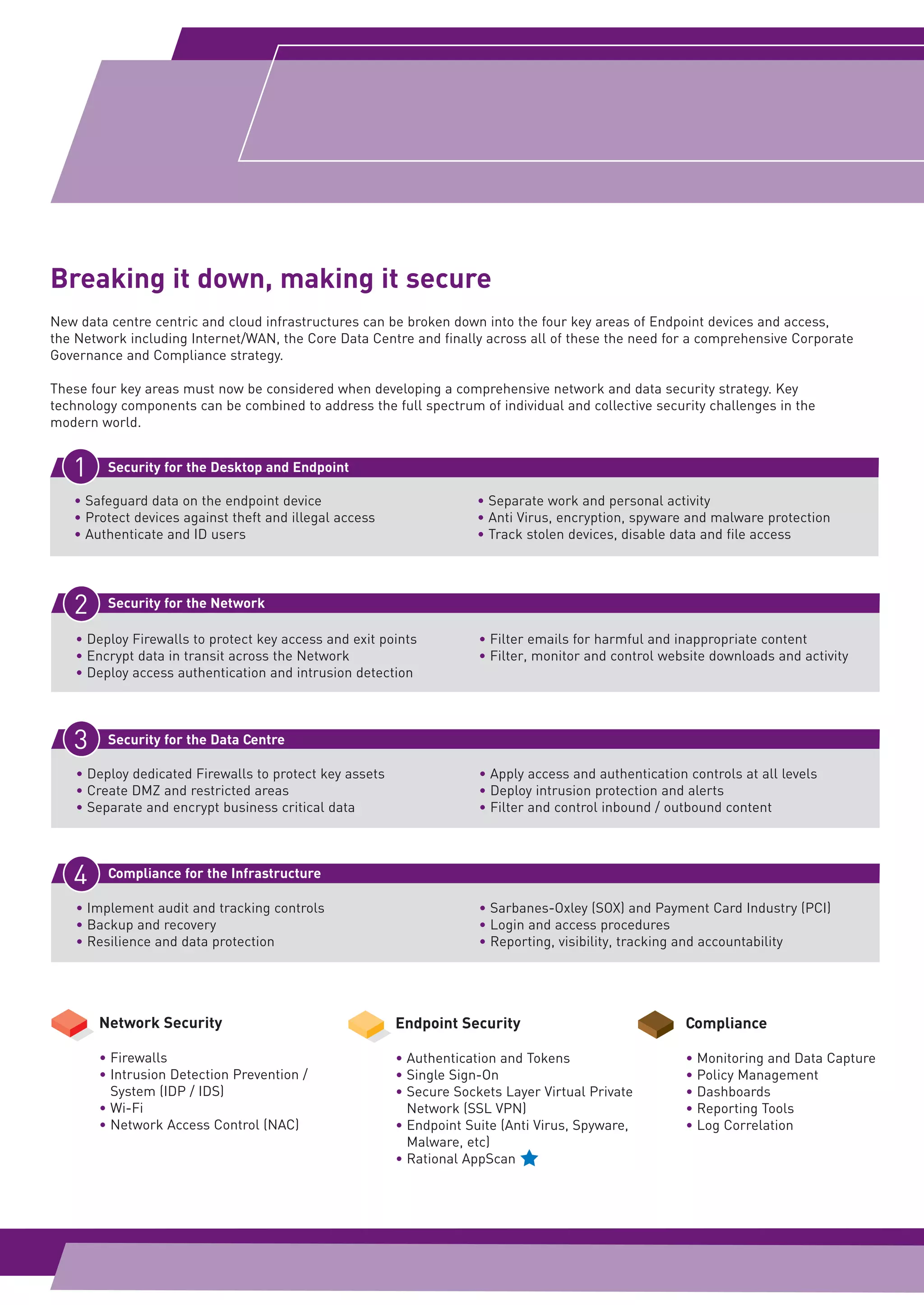
Arrow ECS is a leading UK security distributor that can offer customers solutions from its Security Center of Excellence and partnerships with top security vendors. It has expertise in translating industry knowledge into practical security solutions for issues like safeguarding data, securing the network and data center, and ensuring compliance. Arrow ECS works with IBM security products to help organizations address escalating security and compliance needs.