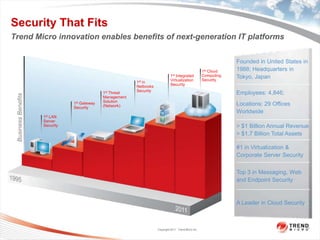
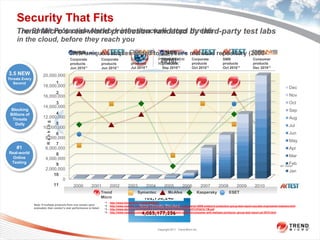
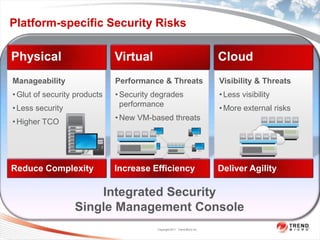
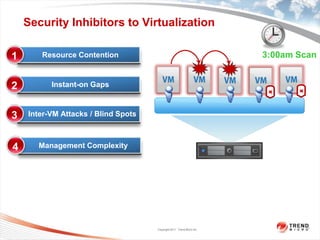
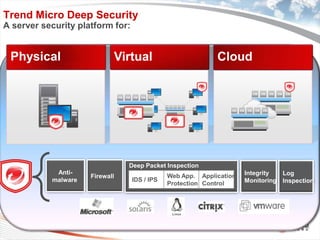
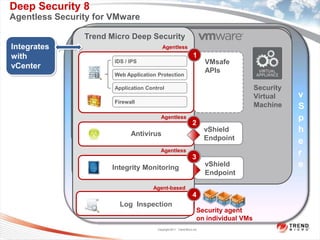
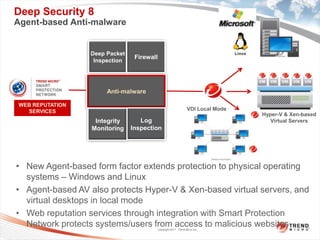
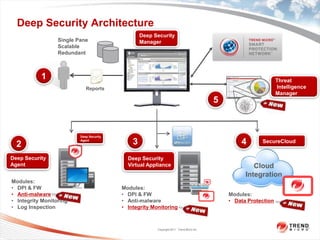
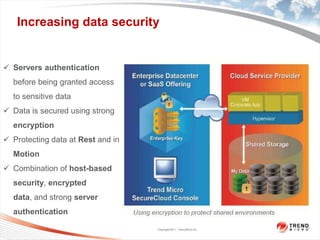
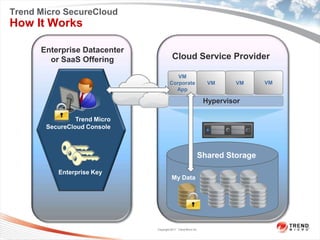
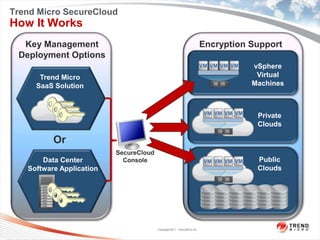
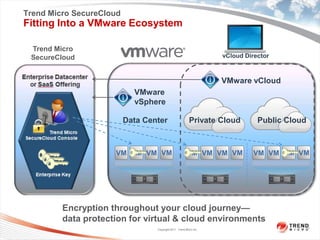
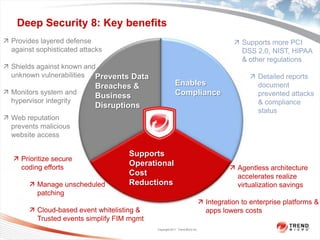
Trend Micro is a leader in virtualization and cloud security. It was the first to offer security solutions for virtualization, cloud computing, and netbooks. Trend Micro blocks billions of threats daily and detects over 3.5 million new threats every second. It ranked #1 in real-world online testing and is also a leader in messaging, web, and endpoint security. Deep Security is Trend Micro's platform that provides unified security across physical, virtual, and cloud environments.