This document discusses the data link layer and design issues related to protocols at the data link layer. It covers three main points:
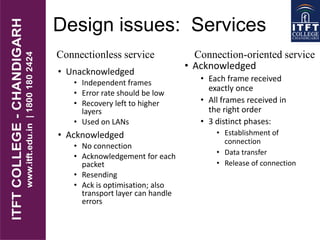
1. The data link layer provides services to the network layer like unacknowledged connectionless service, acknowledged connectionless service, and acknowledged connection-oriented service. It receives services from the physical layer like unreliable bit transport.
2. Important design issues for data link layer protocols include framing data, providing error control, and flow control. Common framing methods are using flags or character stuffing. Error control involves acknowledgements and resending packets. Flow control prevents senders from overwhelming receivers.
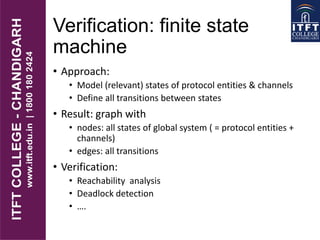
3. Formal verification techniques like finite state machines and Petri nets can be used