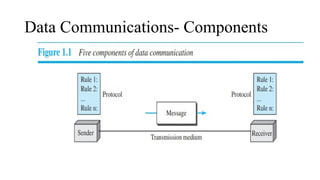
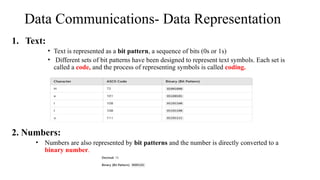
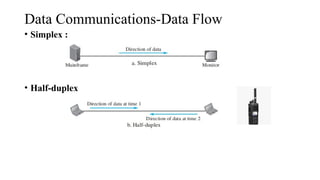
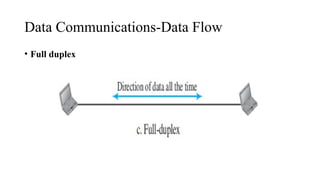
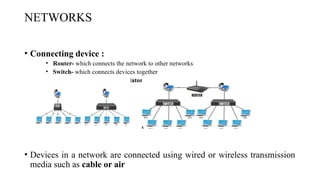
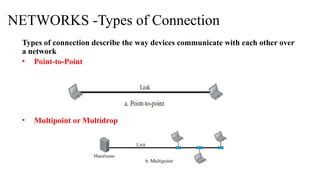
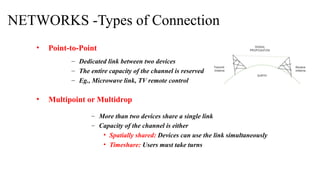
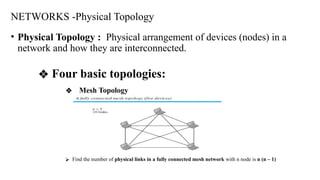
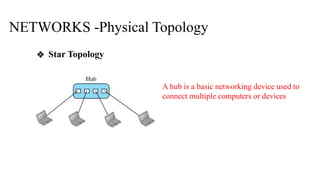
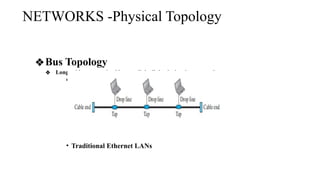
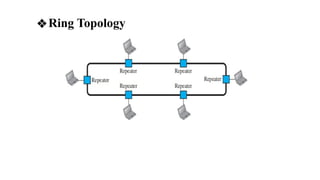
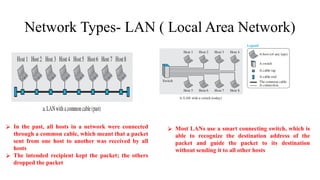
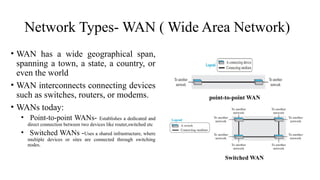
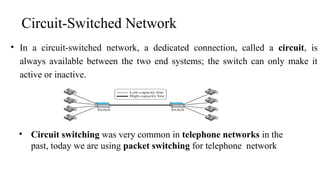
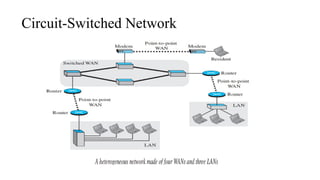
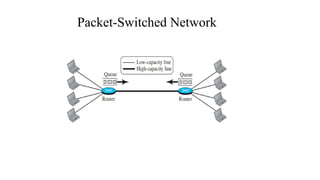
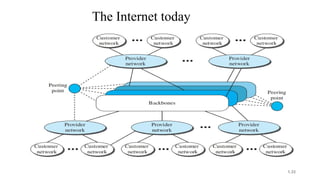
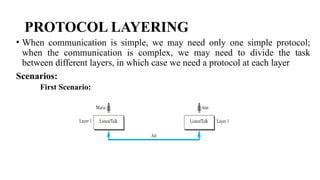
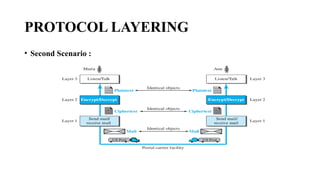
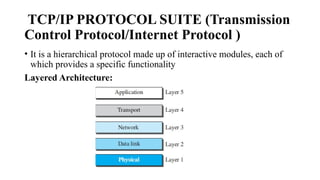
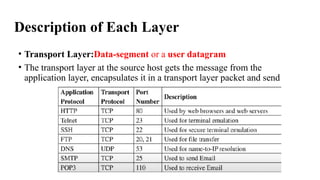
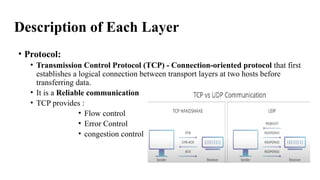
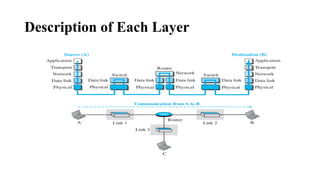
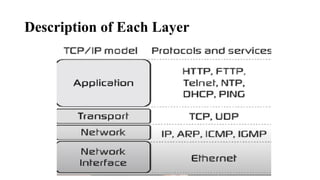
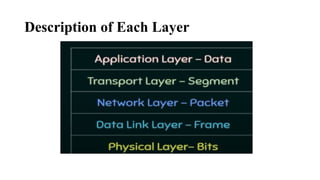
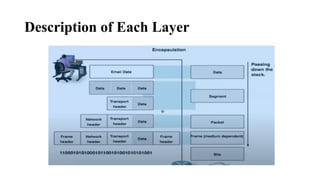
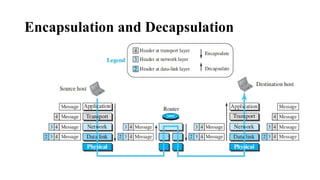
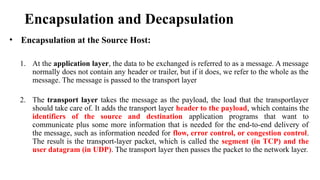
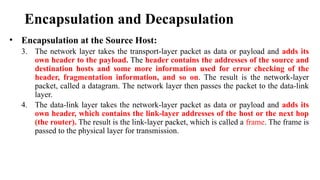
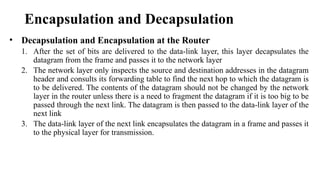
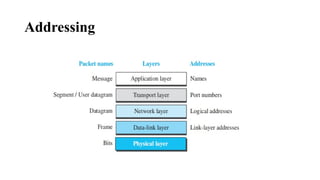
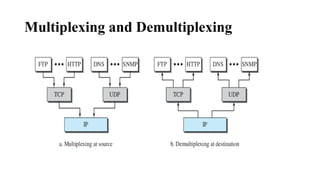
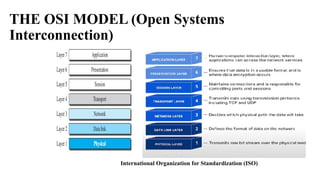
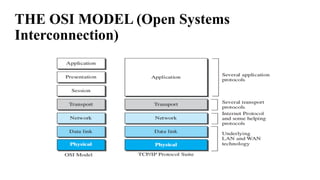
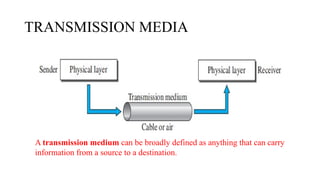
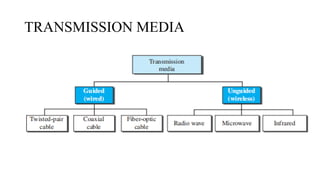
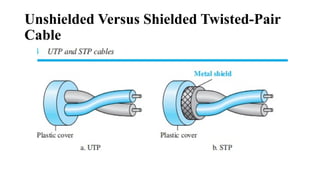
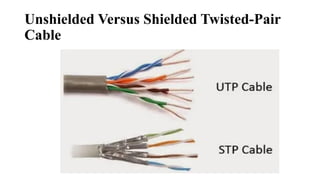
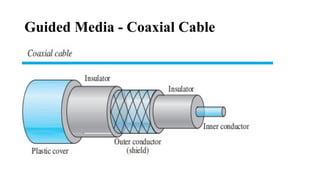
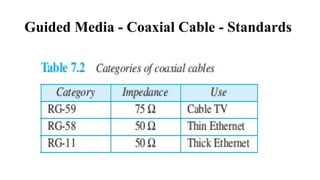
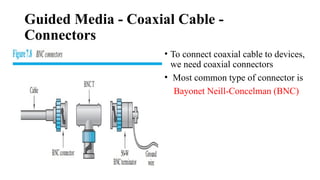
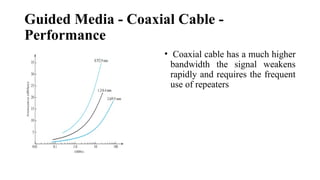
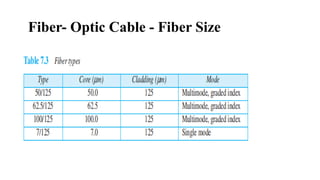
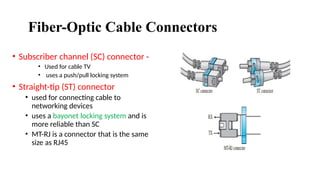
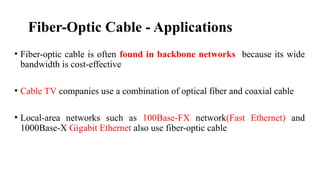
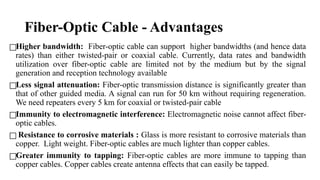
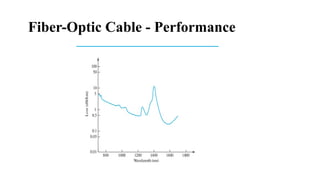
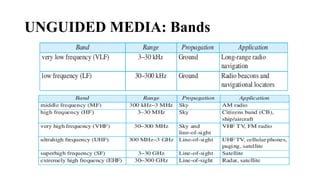
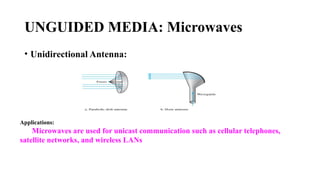
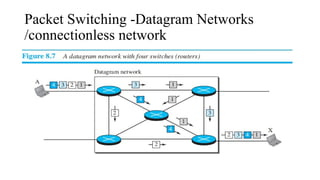
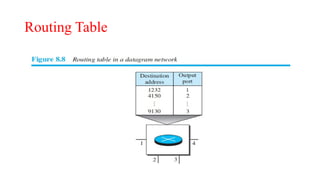
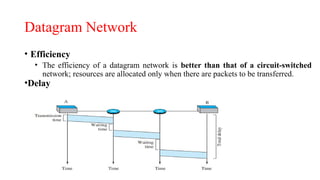
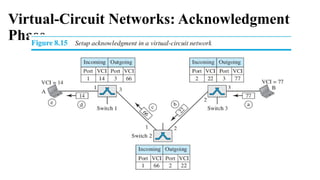
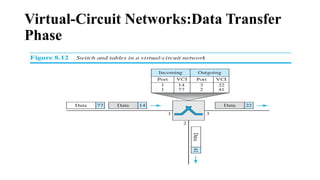
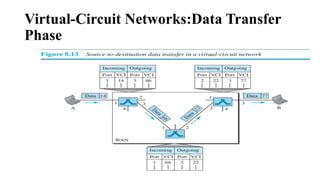
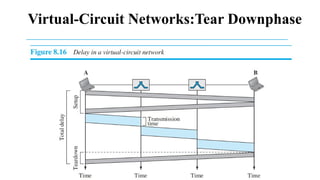
The document discusses computer networks, focusing on data communications and networking principles, components, representation, and various network types and topologies. Key aspects include the characteristics of data communication, such as delivery, accuracy, and timeliness, along with protocols governing data transmission. Additionally, it covers the structure of the TCP/IP protocol suite and the encapsulation process for data transmission between devices.