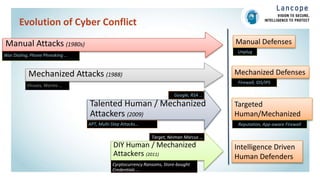
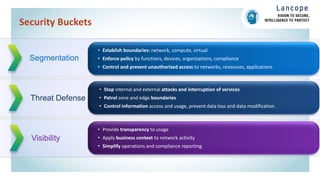
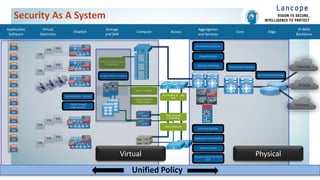
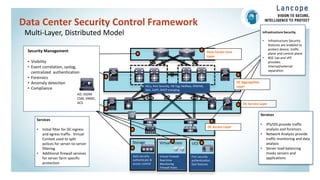
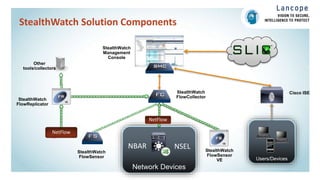
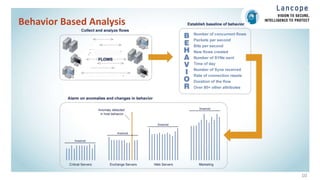
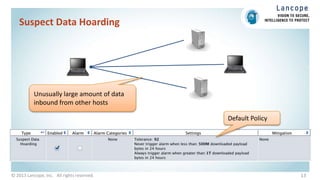
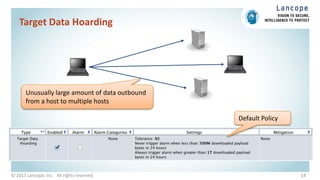
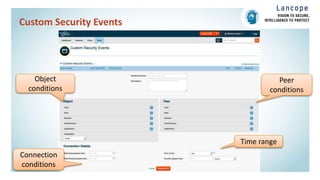
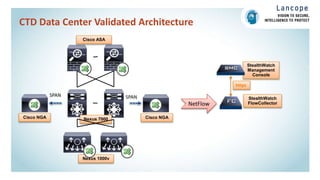
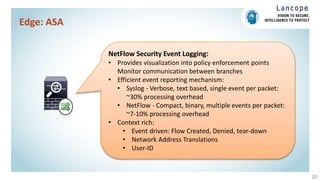
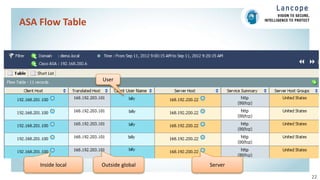
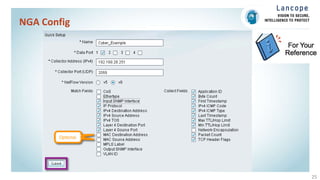
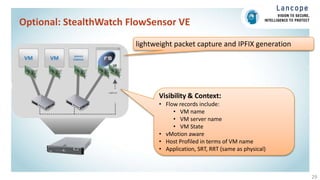
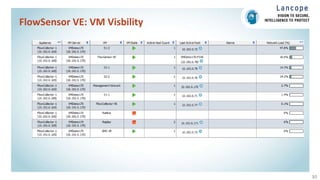
The document discusses securing data centers from cyber threats. It describes how attacks have evolved from manual to mechanized to sophisticated human-led attacks. It advocates employing segmentation, threat defense and visibility measures like firewalls, IDS/IPS, and NetFlow. The Cisco Cyber Threat Defense solution places these tools at the access, aggregation and core layers, including the ASA firewall, Nexus switches, and StealthWatch for network monitoring and analytics. This provides visibility into network traffic across physical and virtual infrastructure to detect threats and policy violations.