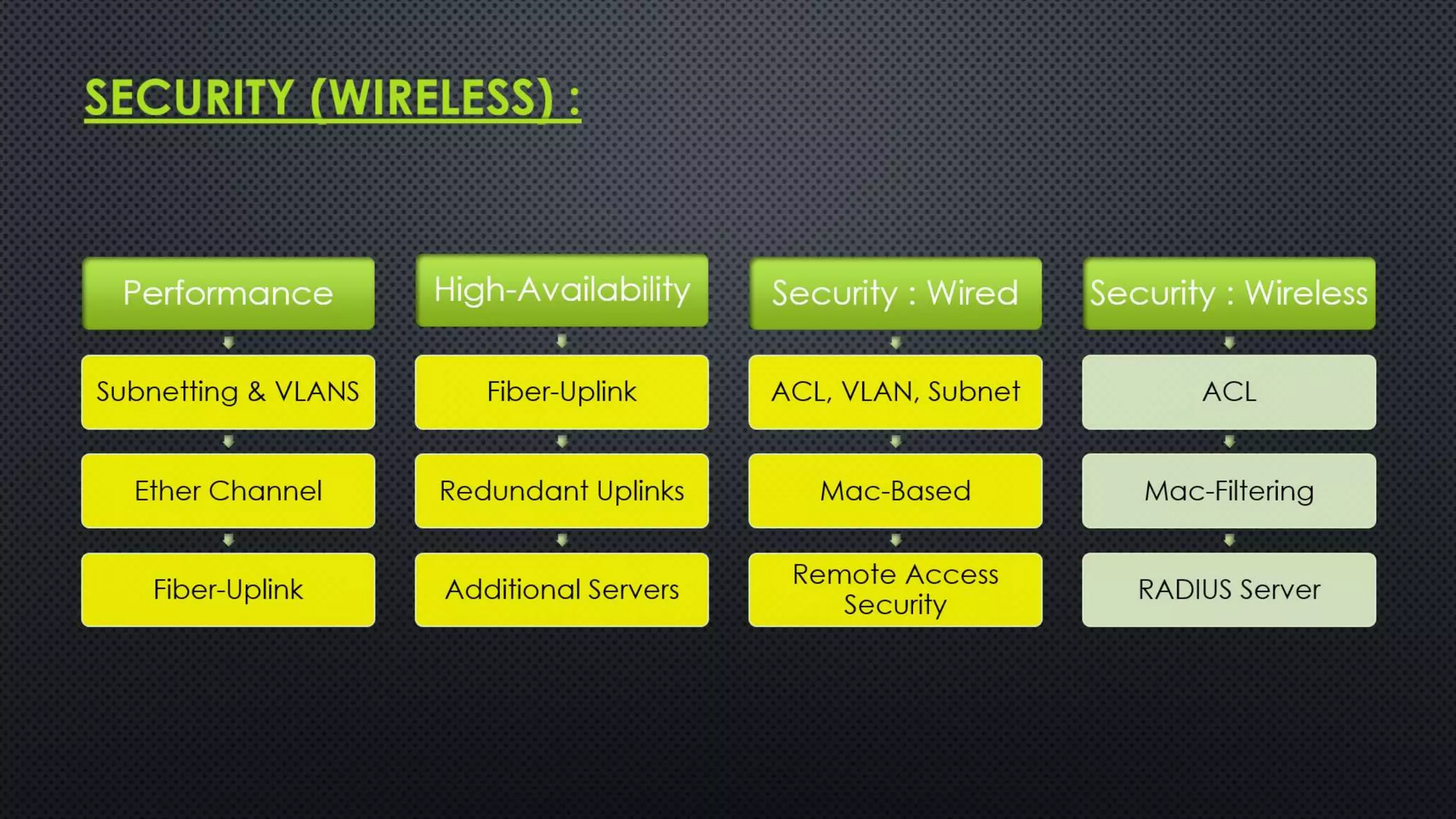
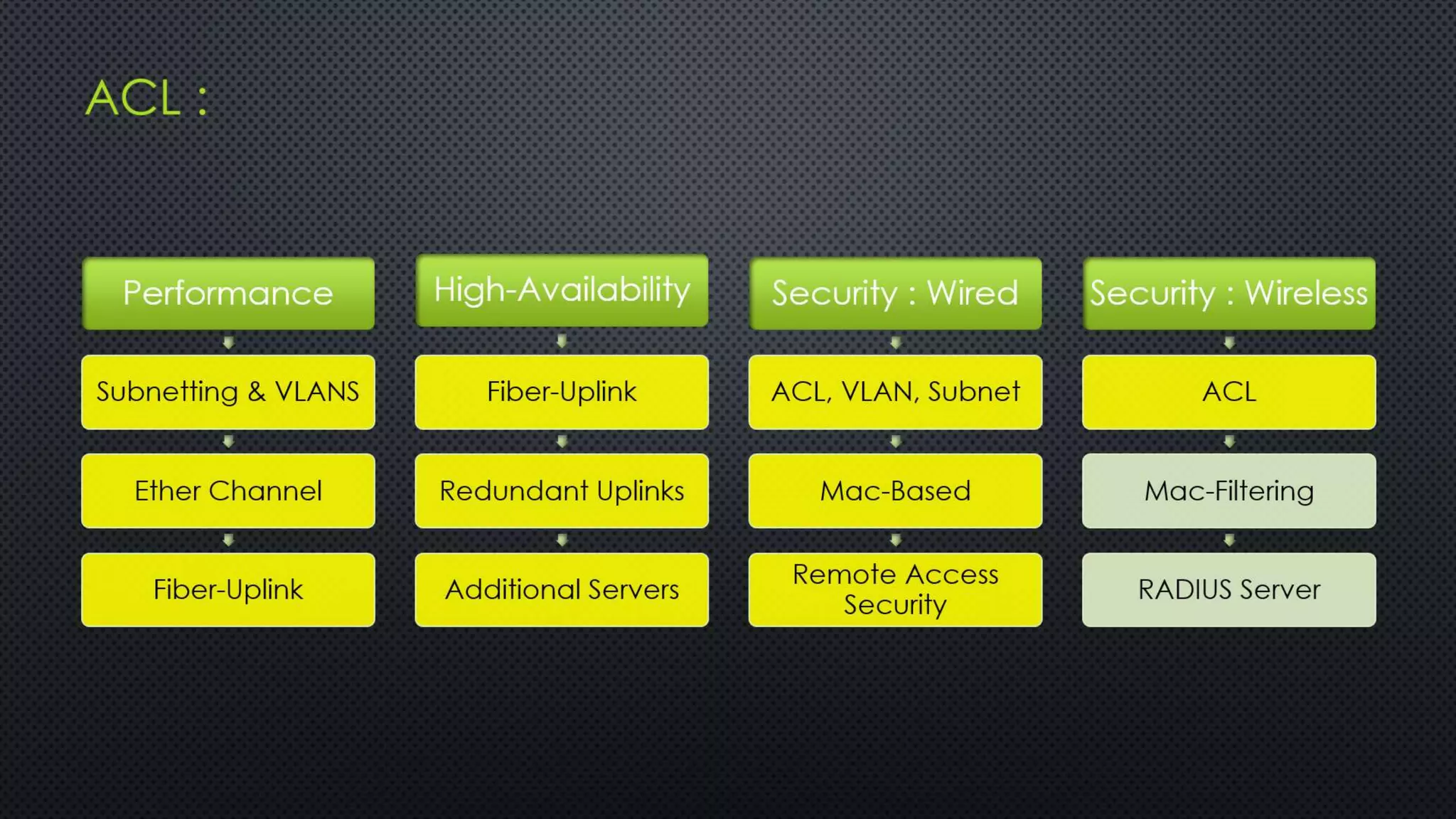
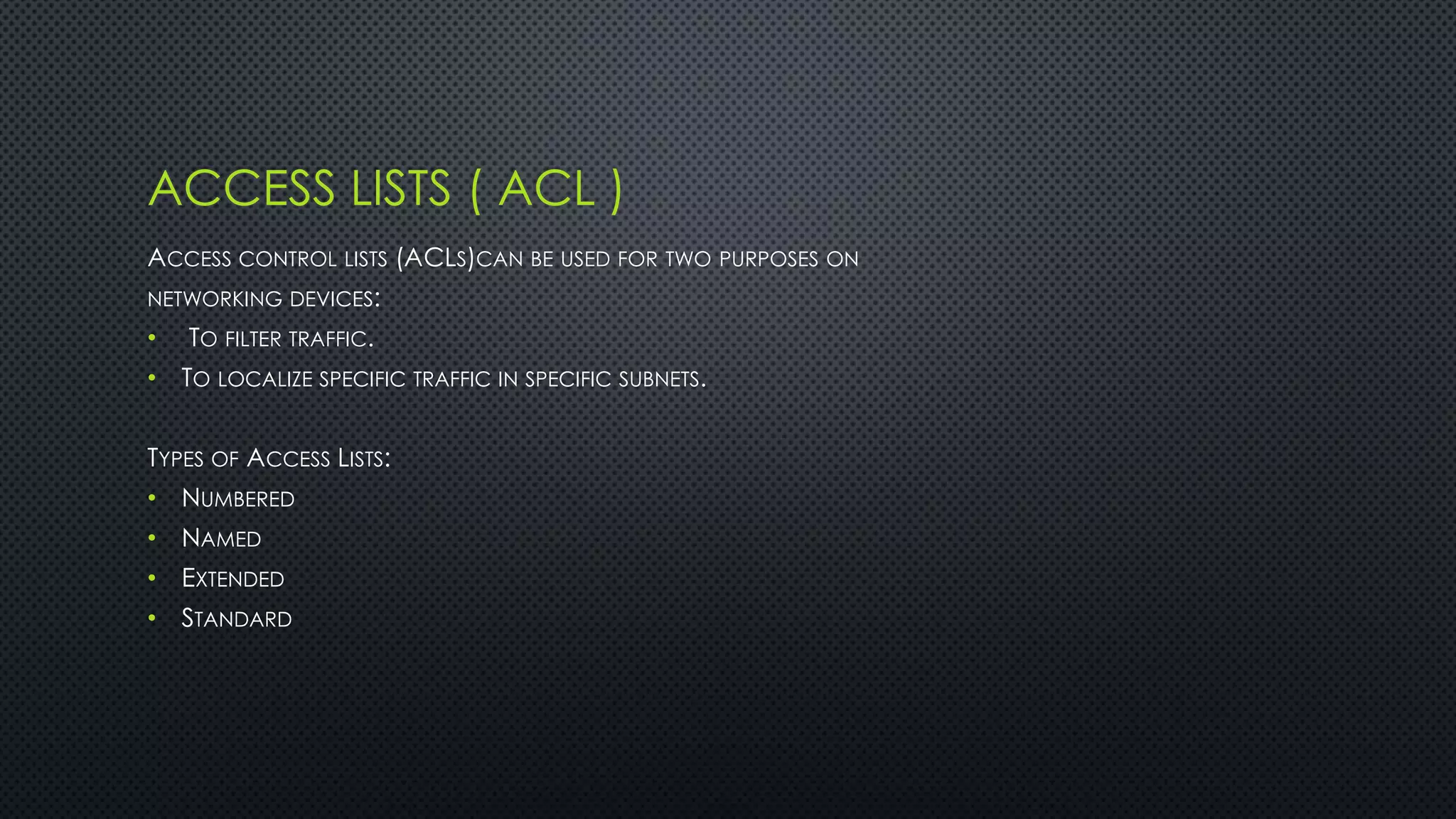
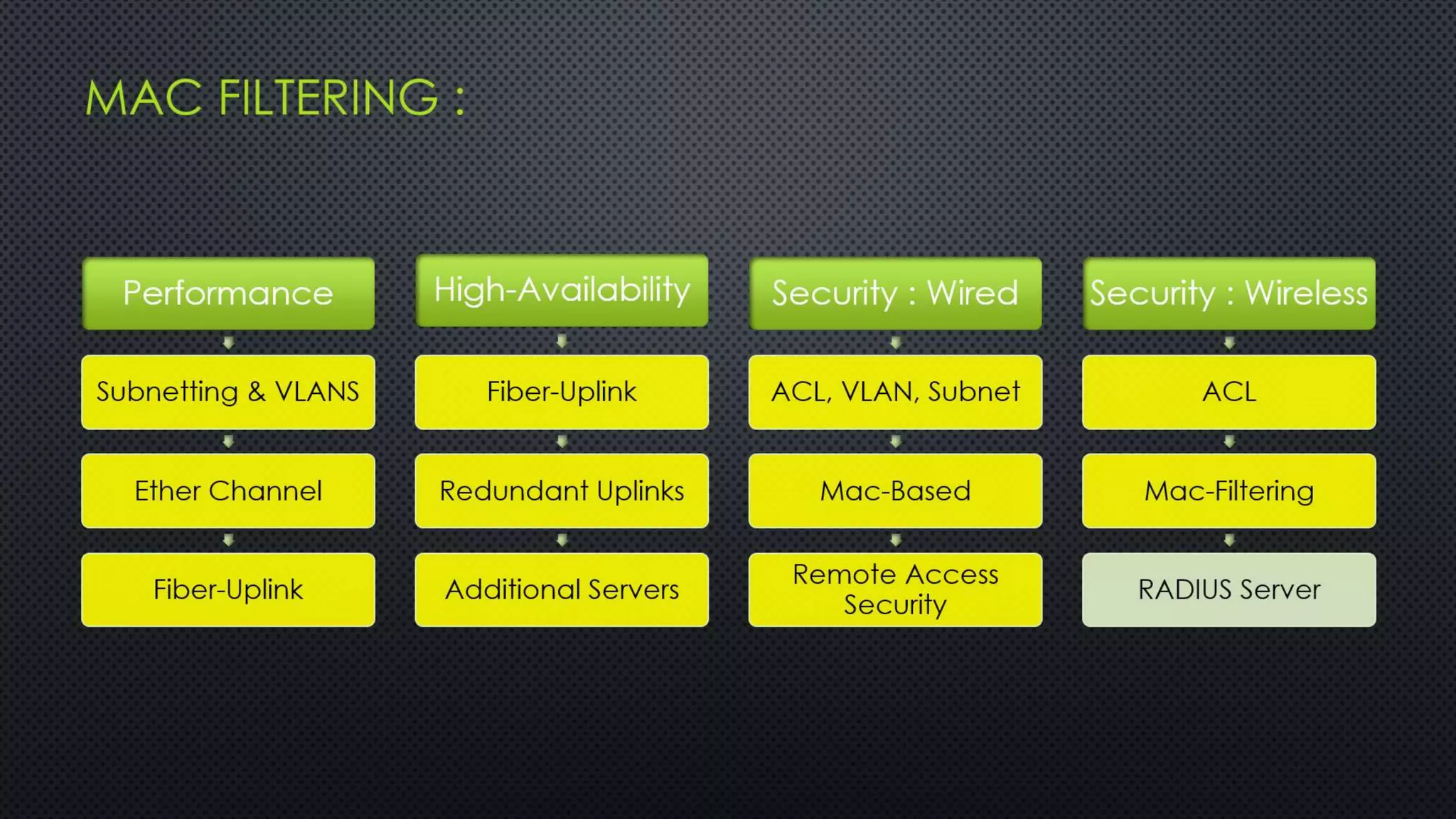
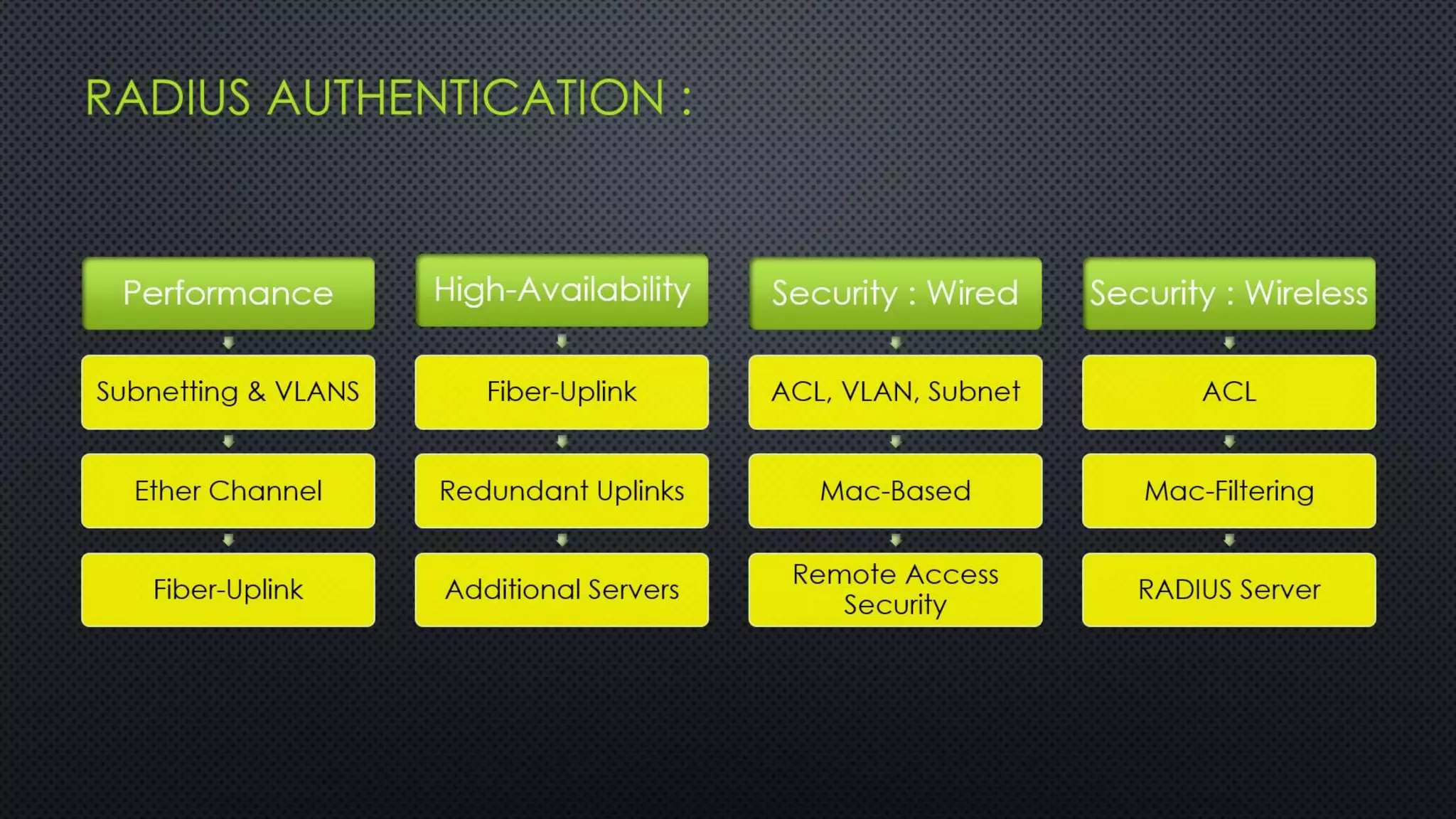
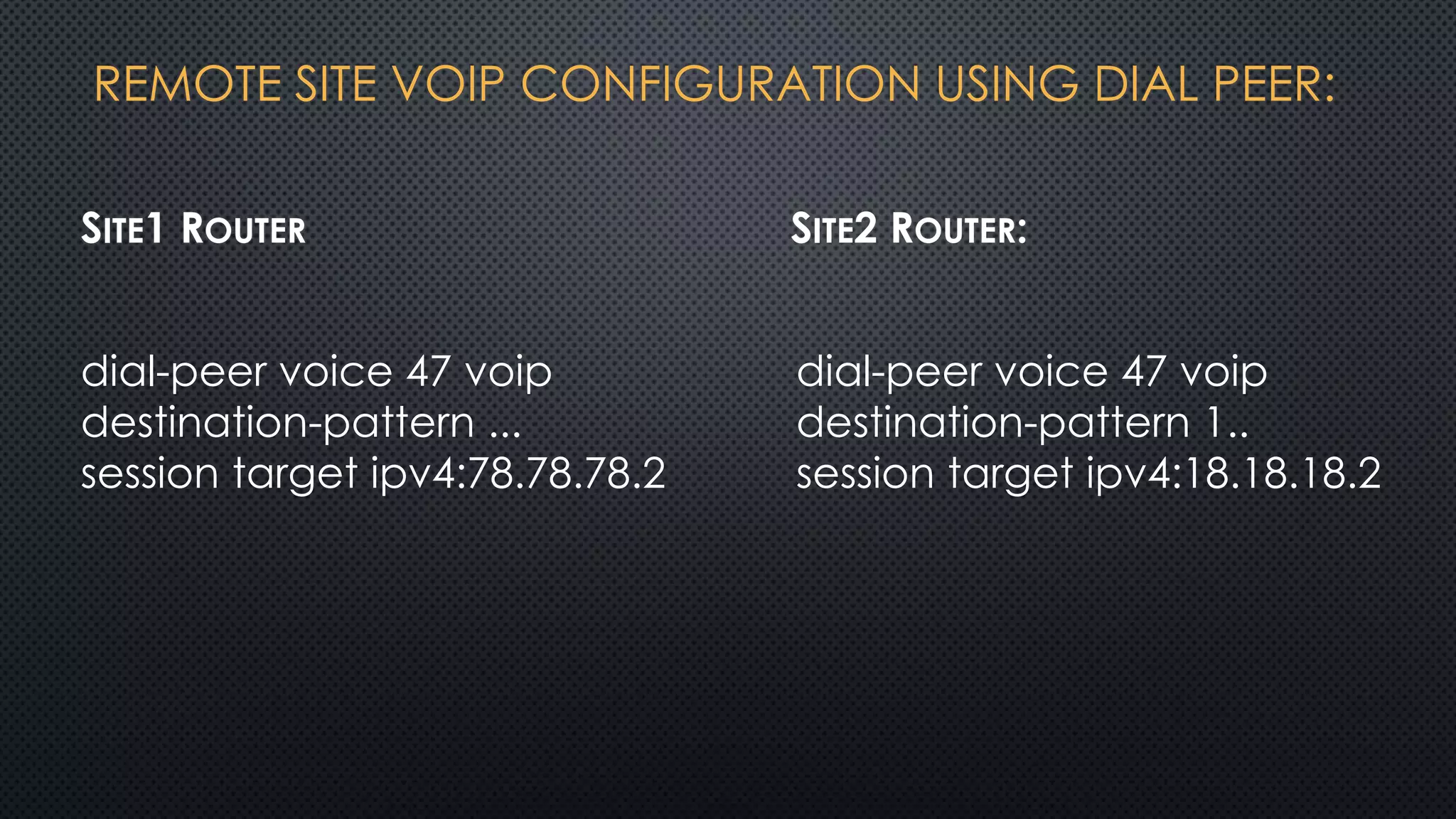
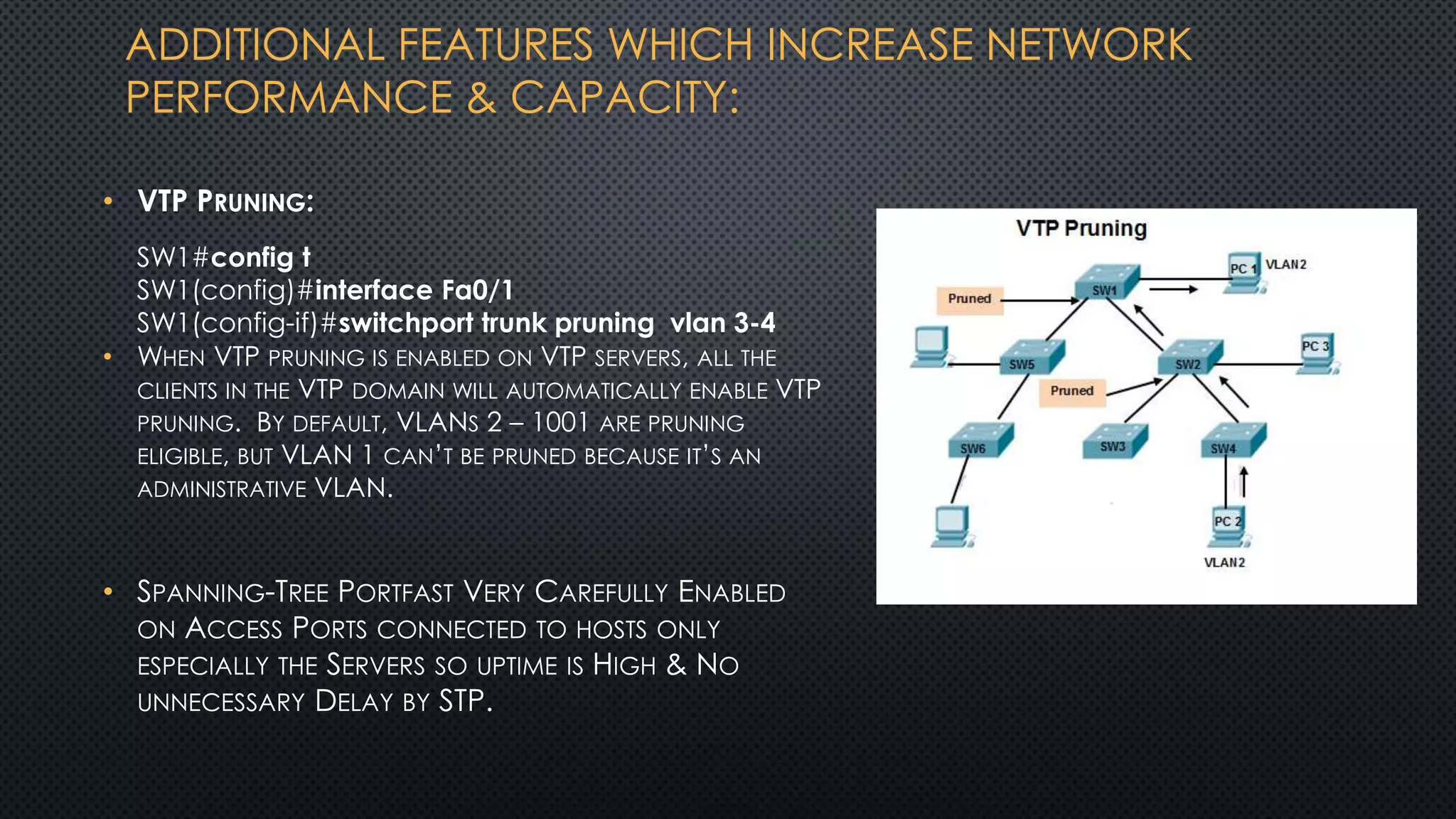
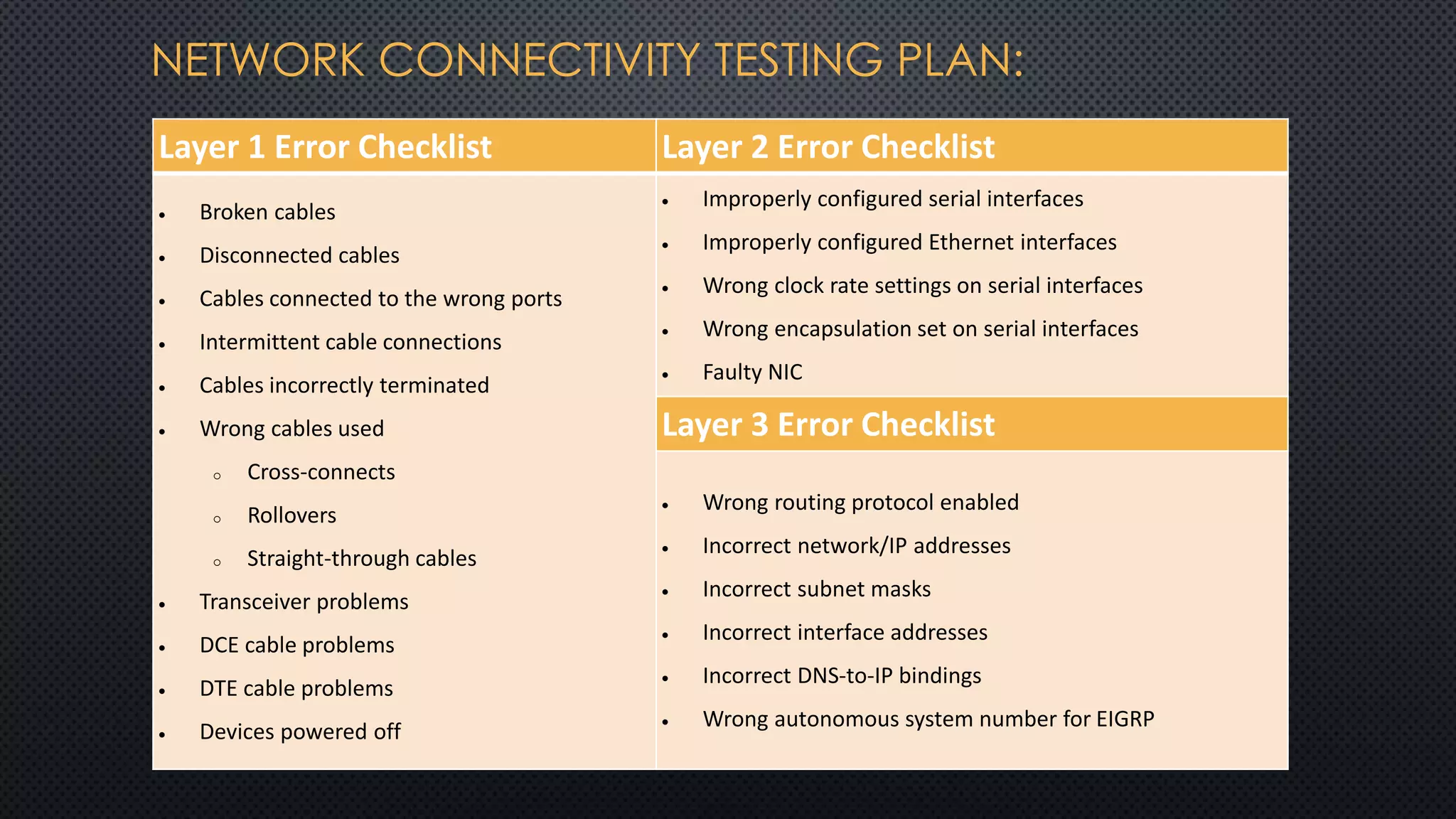
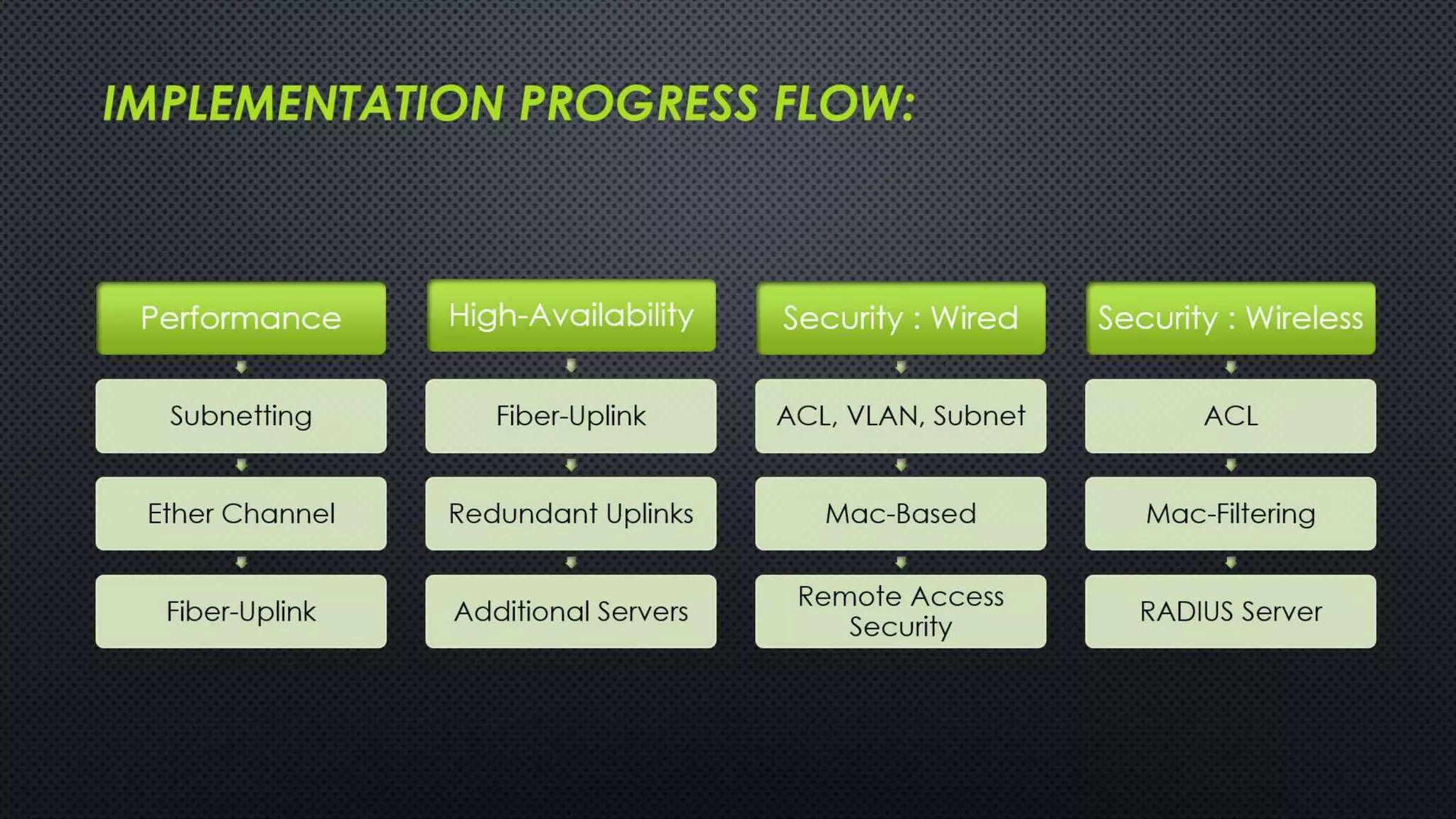
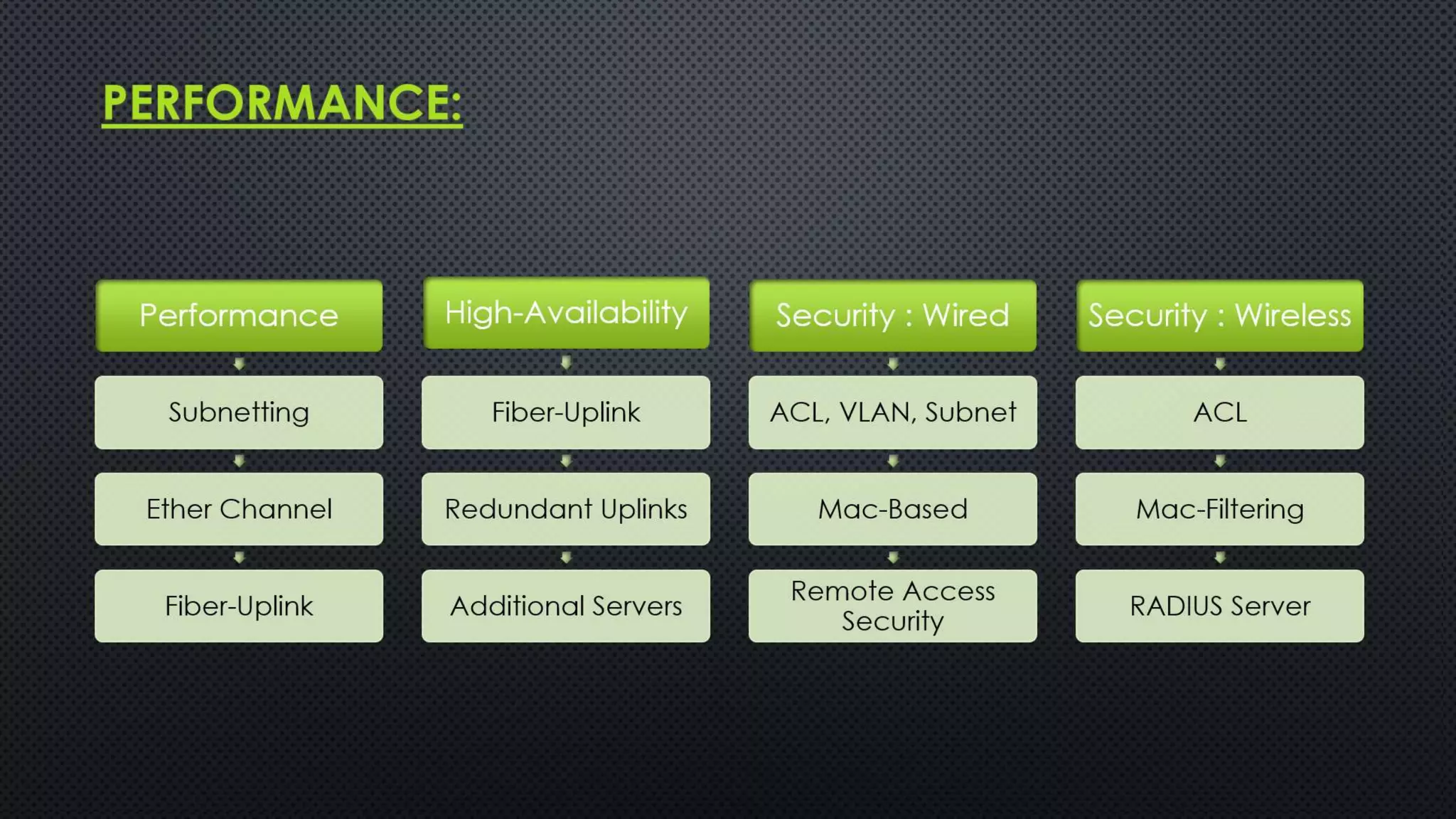
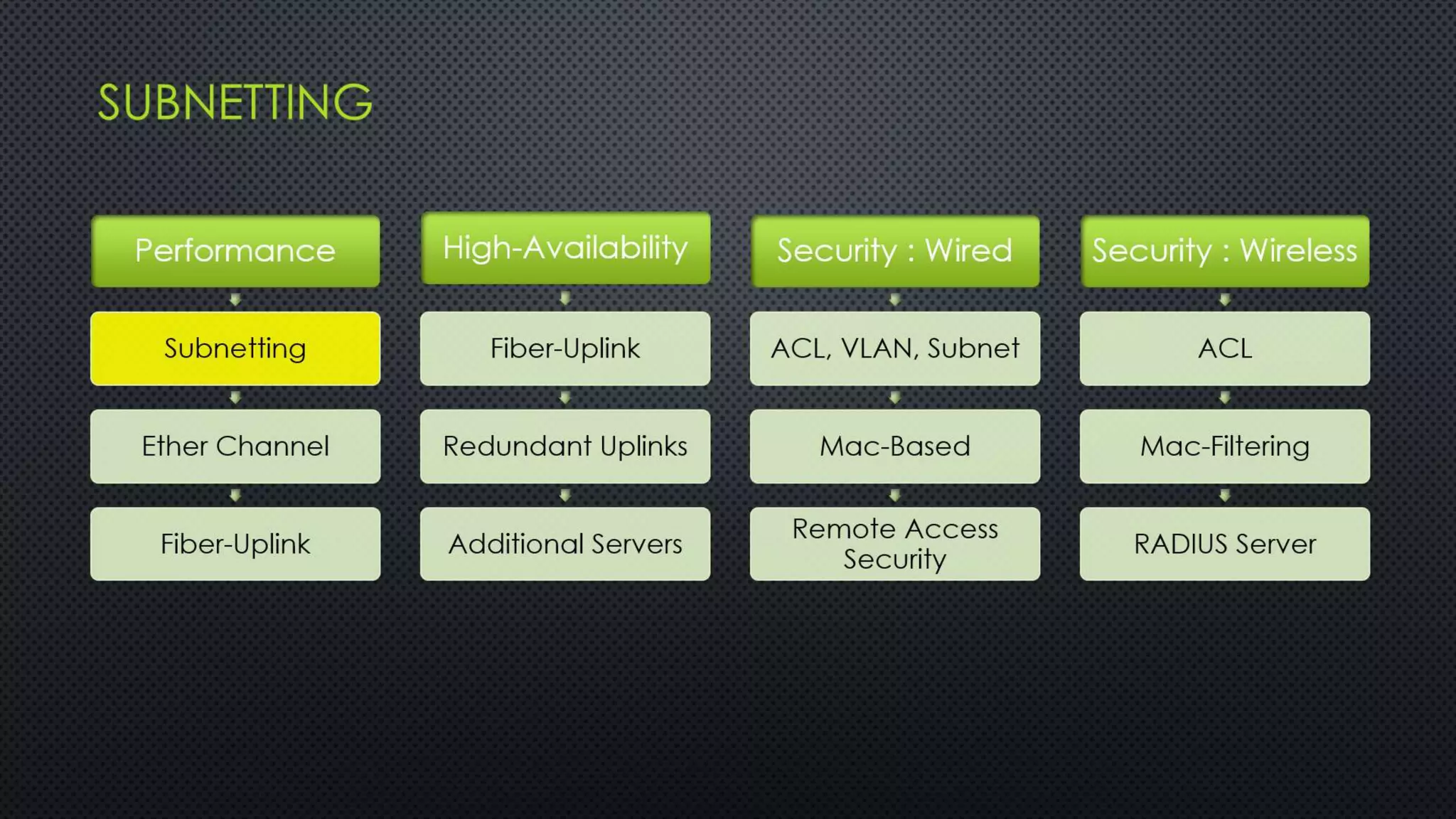
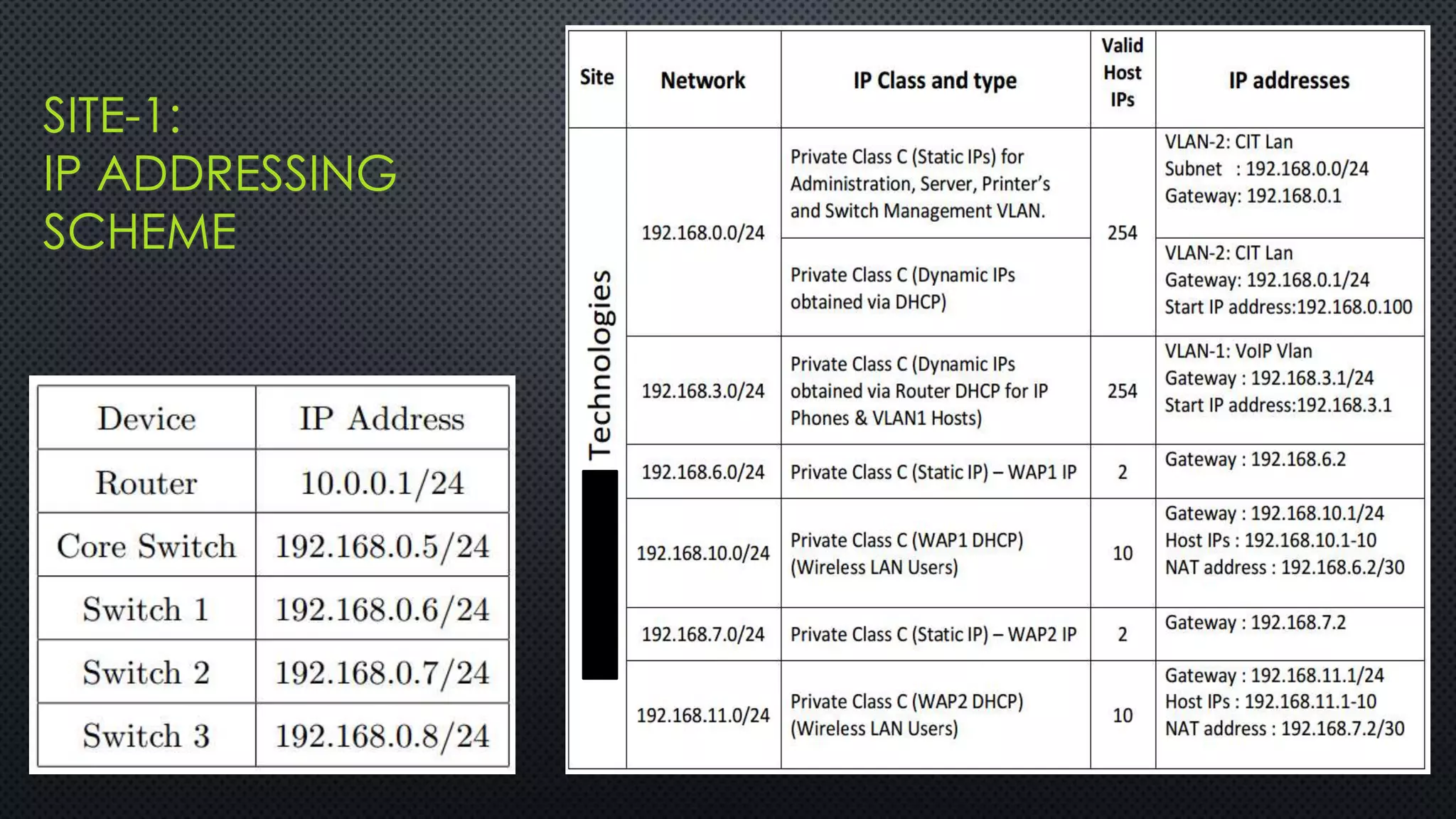
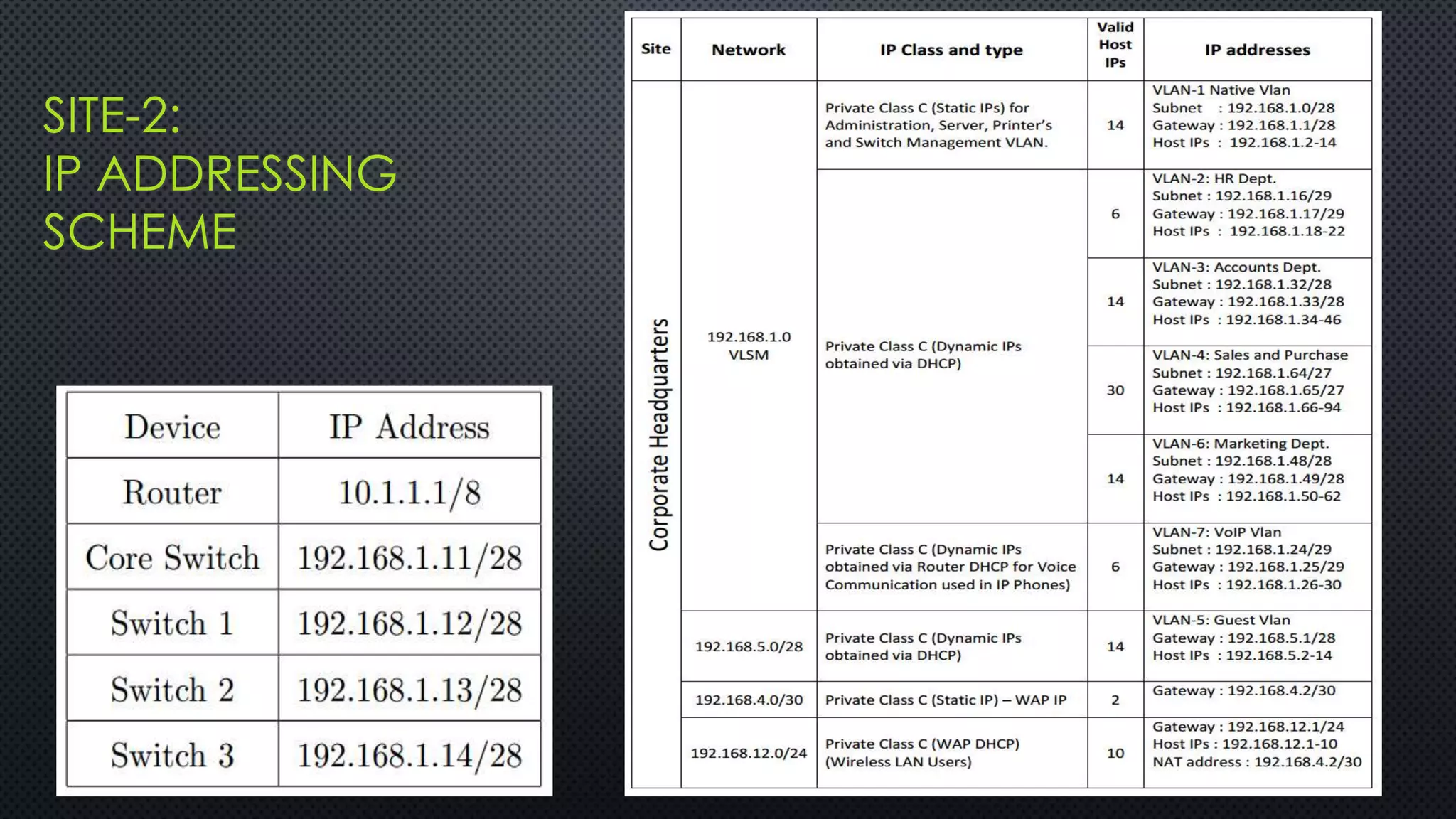
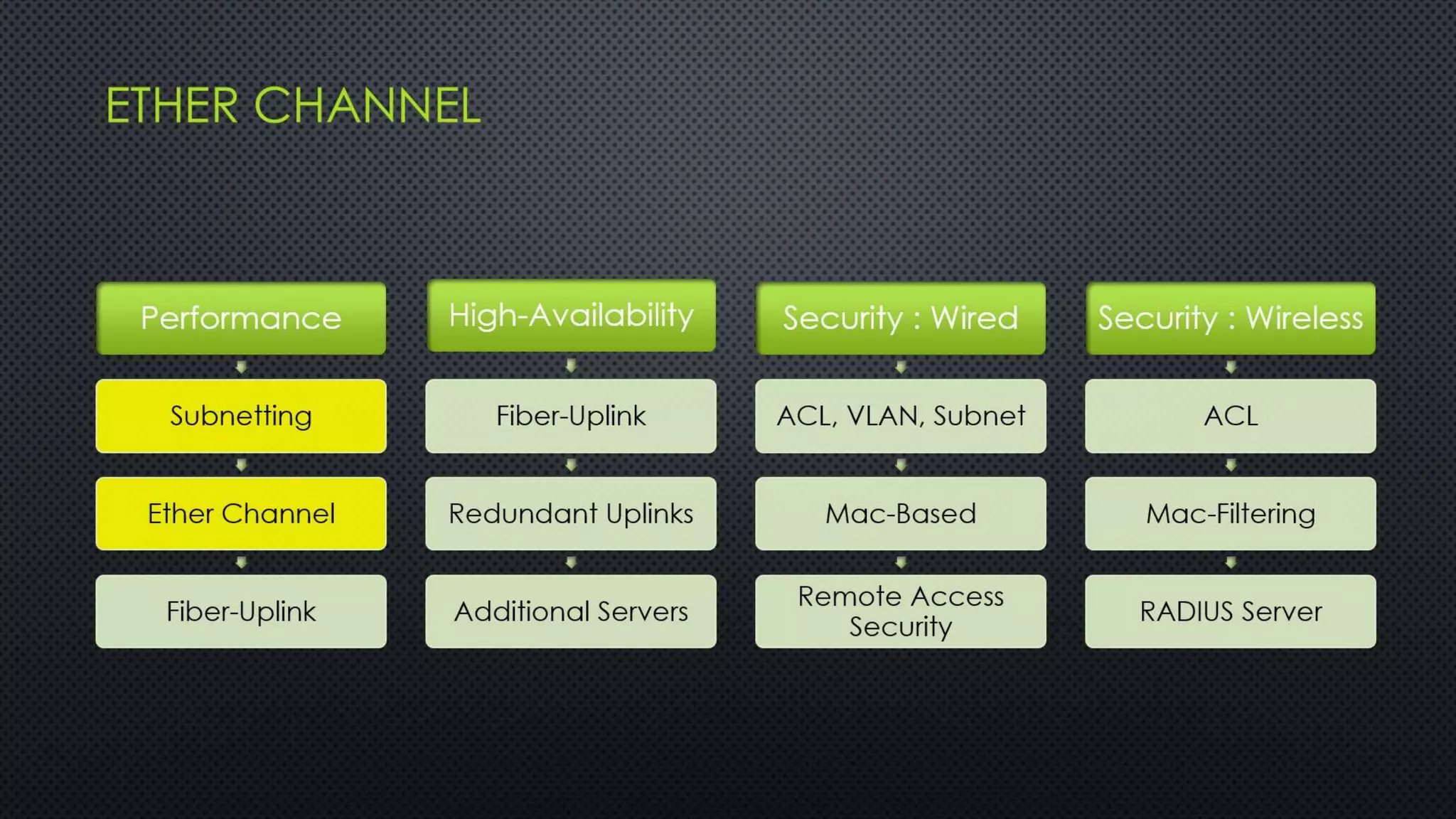
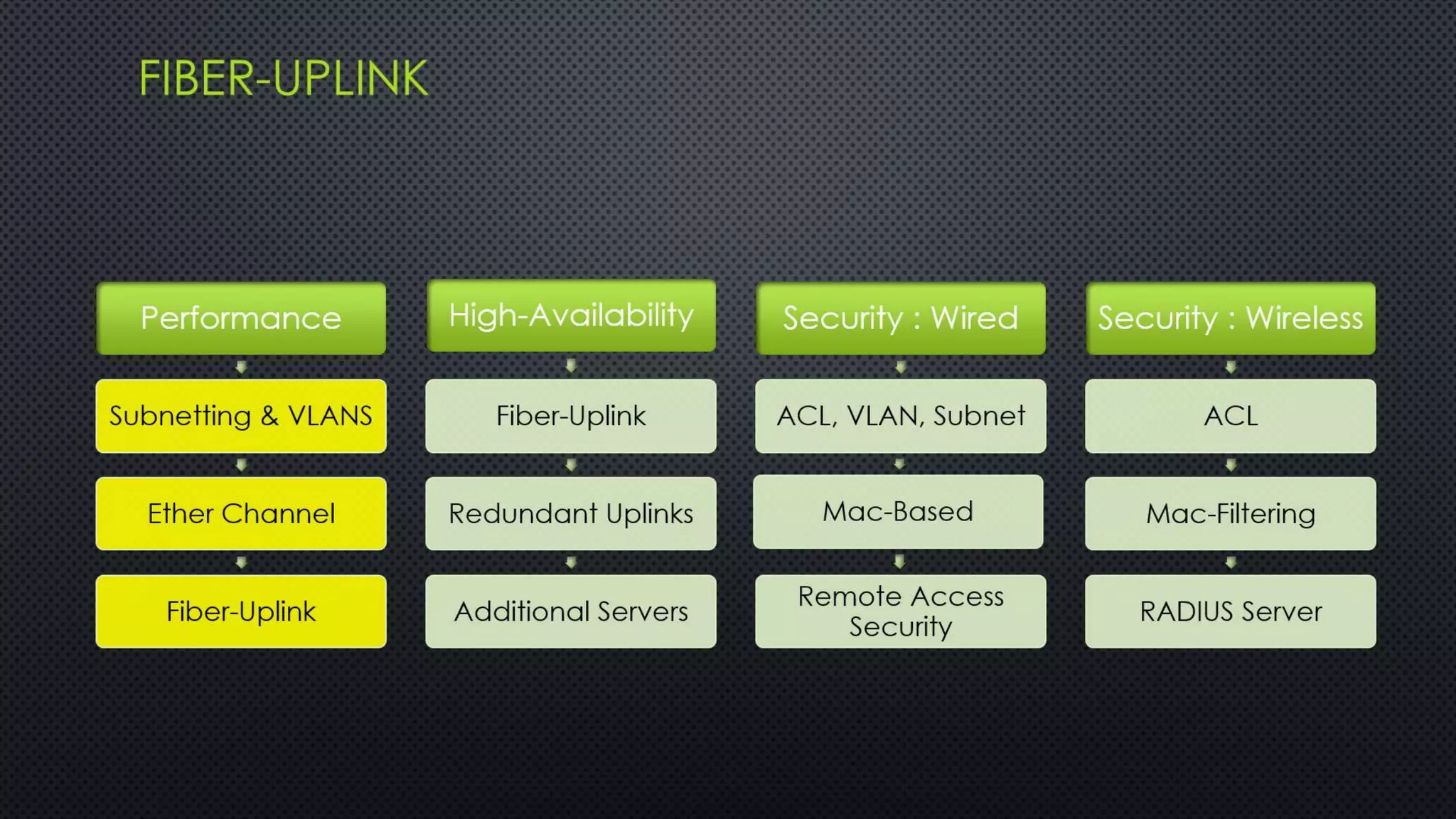
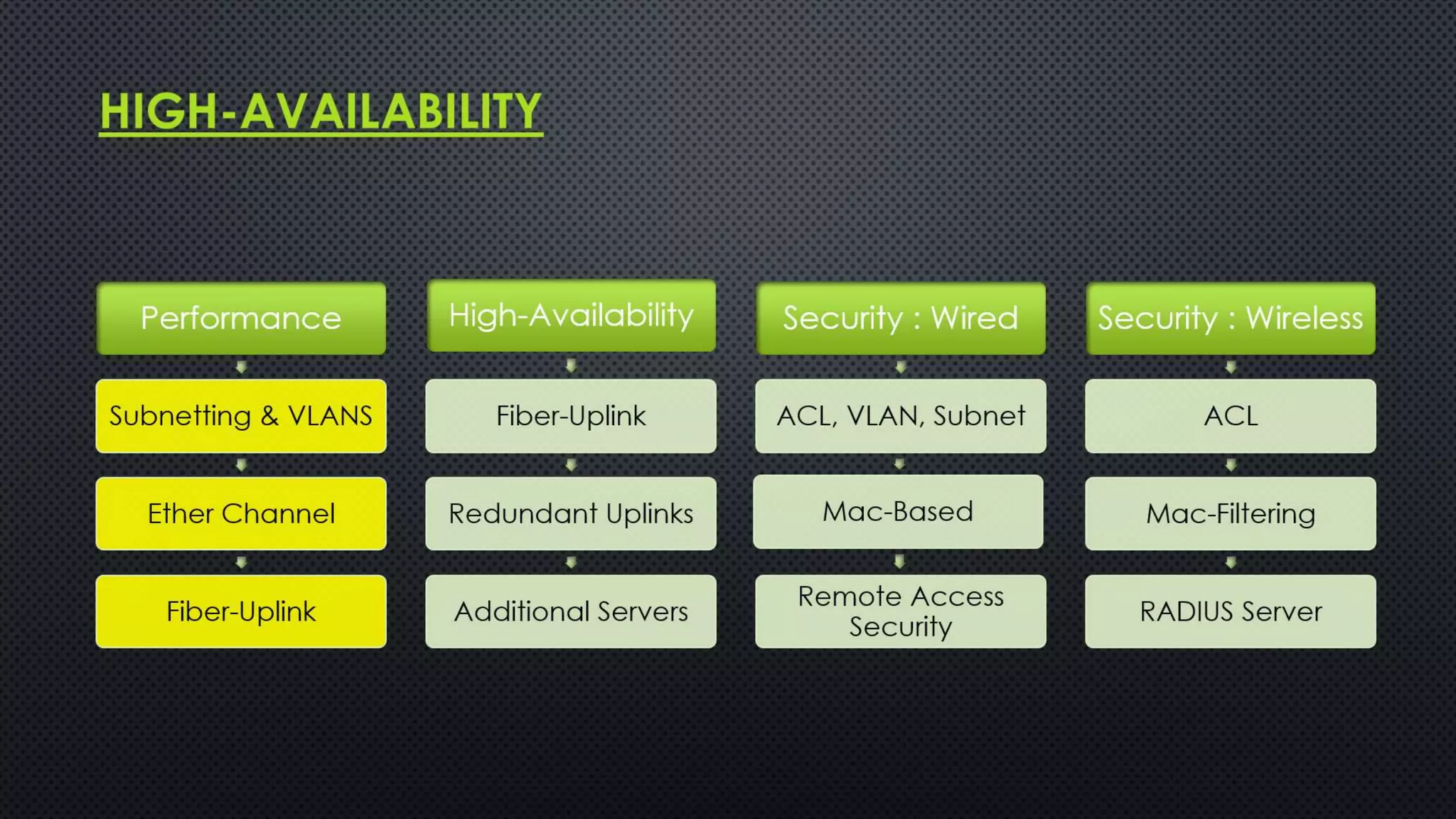
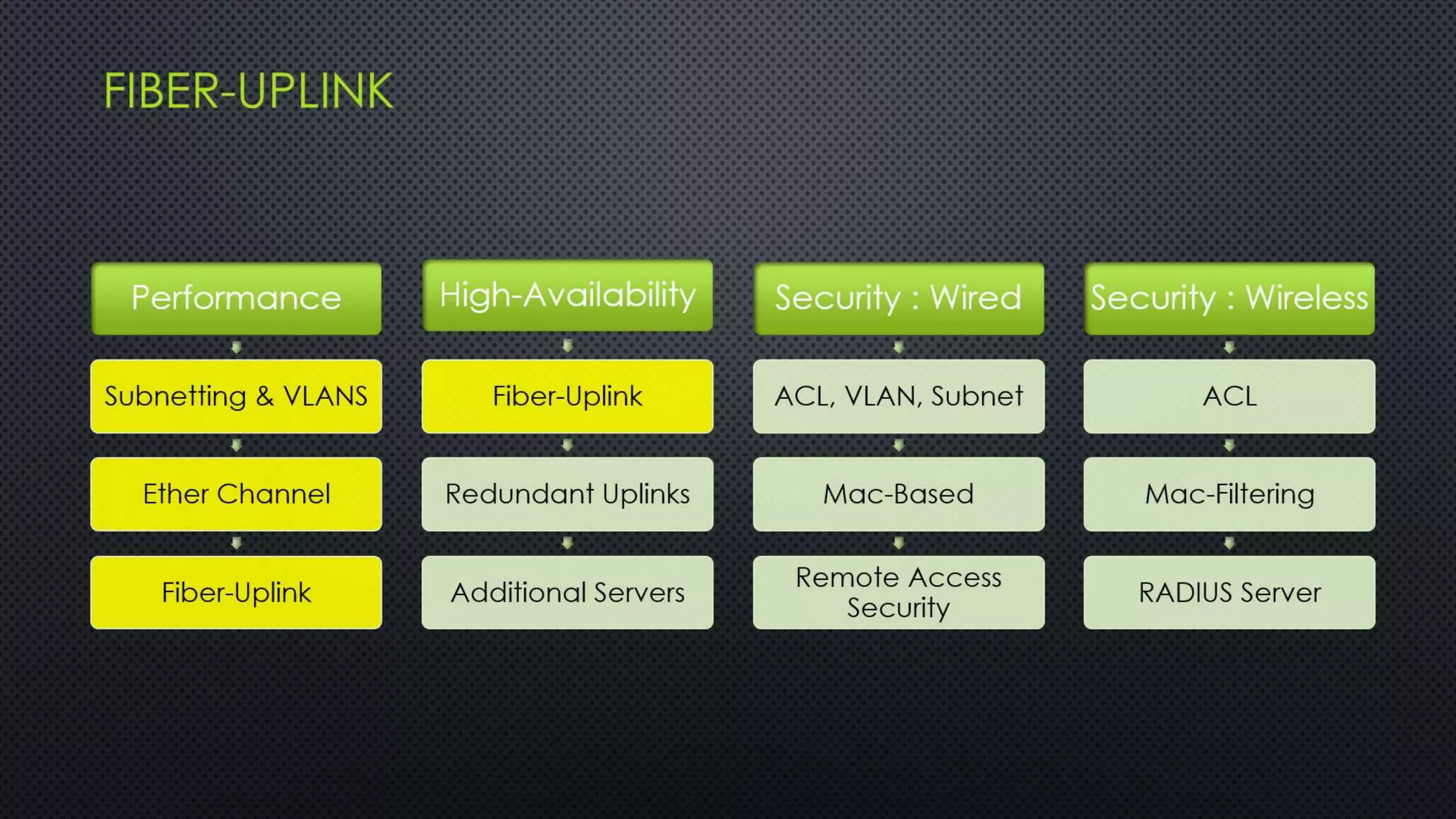
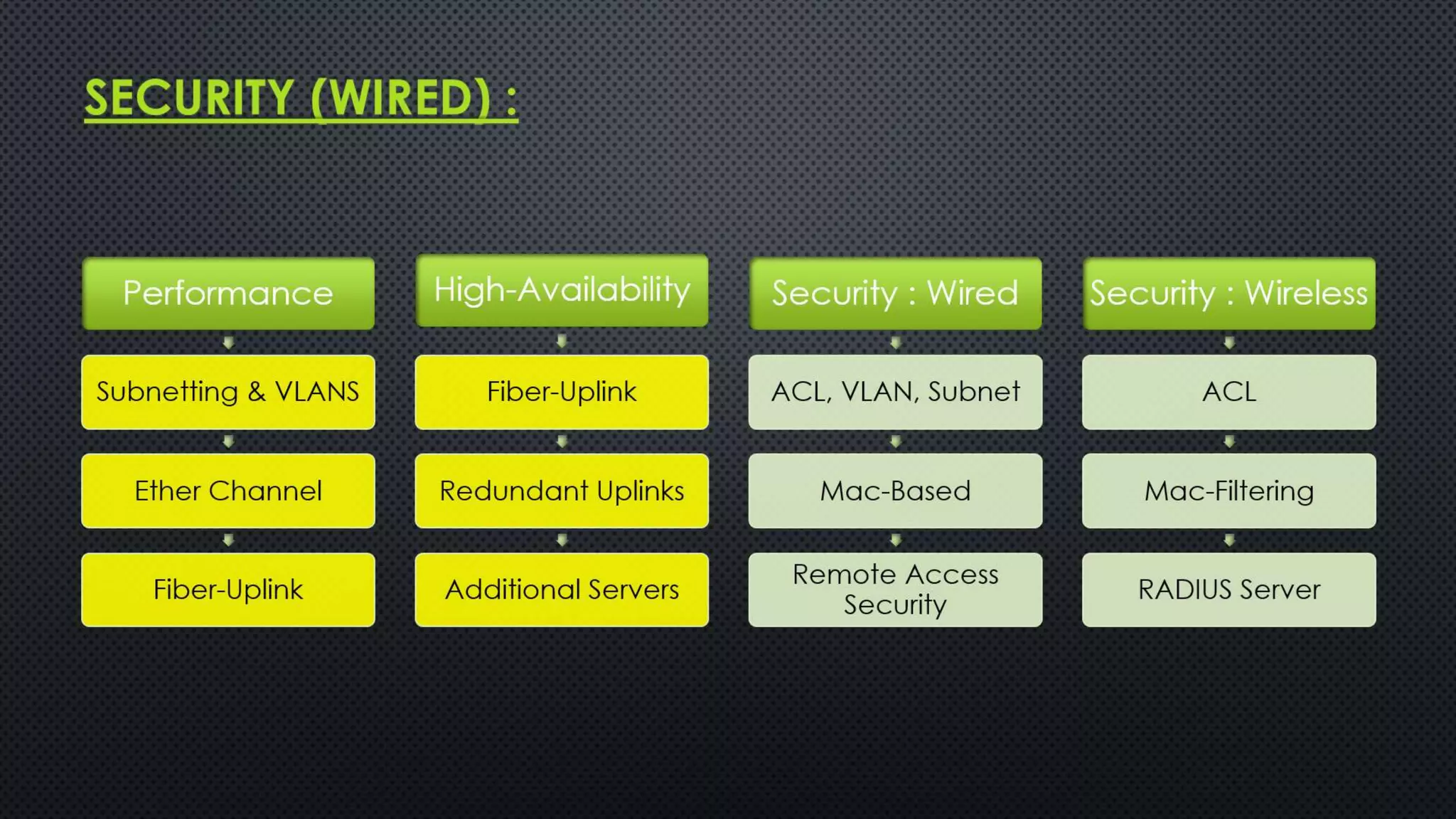
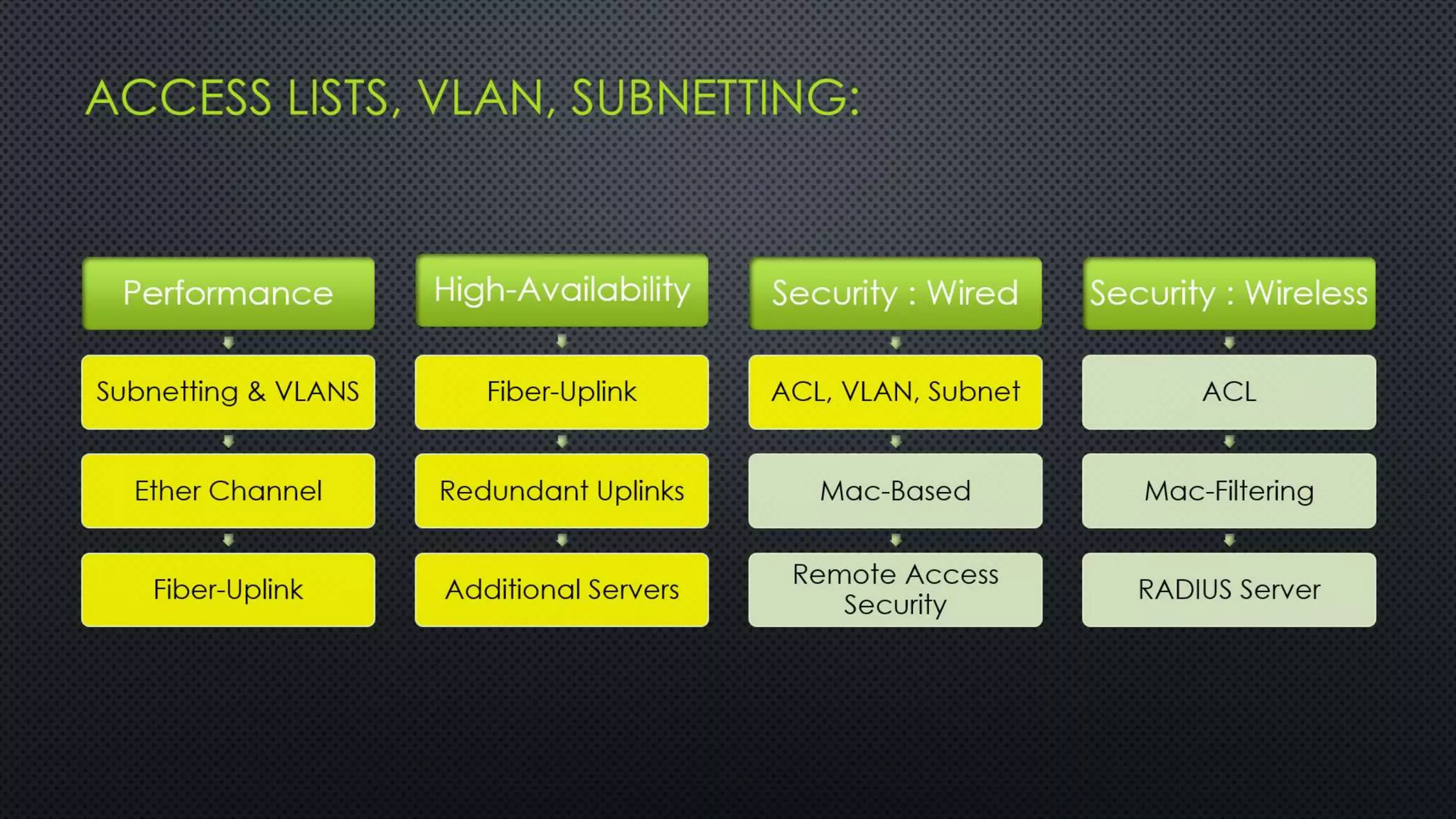
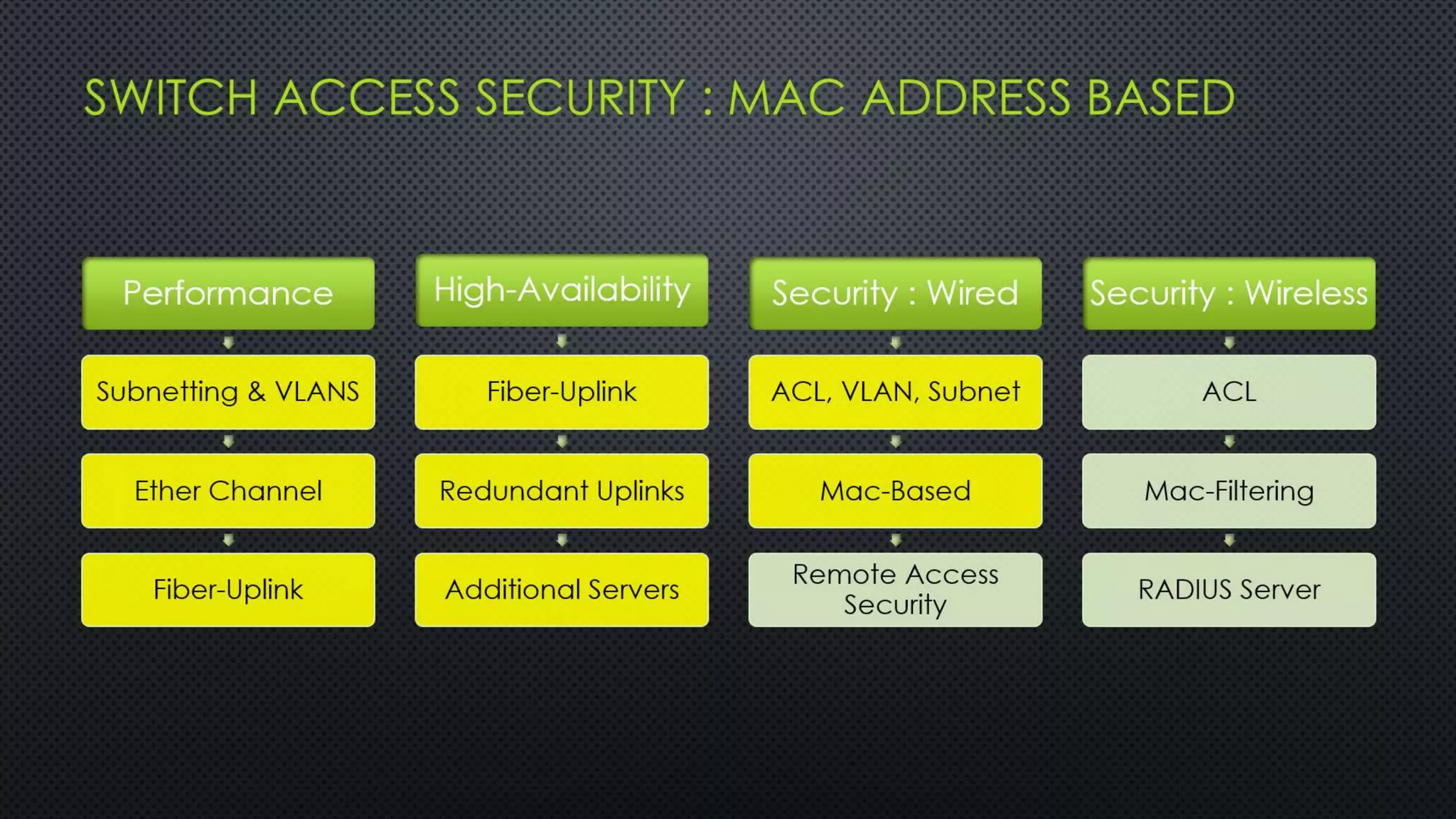
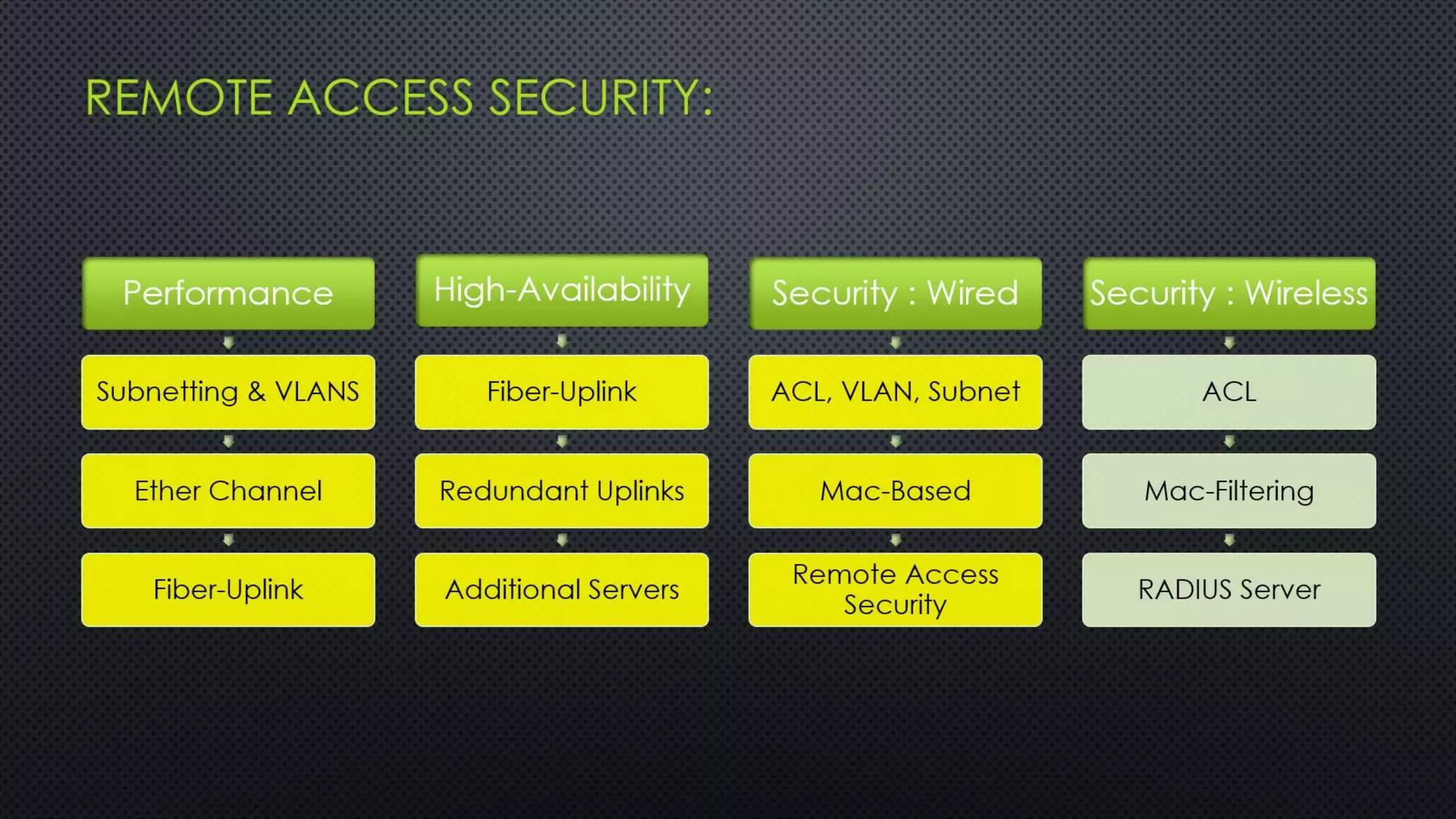
The project outlines the design of a secure and high-availability data and VoIP network for a small enterprise, focusing on improved performance, fault tolerance, and security enhancements. Key features include strict access controls, capability for future expansion, and implementation of VoIP using Cisco devices, with detailed configurations provided for network setup. Additionally, various network features, including access control lists, Ethernet channel configuration, and remote access security measures, are discussed to further enhance network efficiency and security.


















![REMOTE ACCESS &
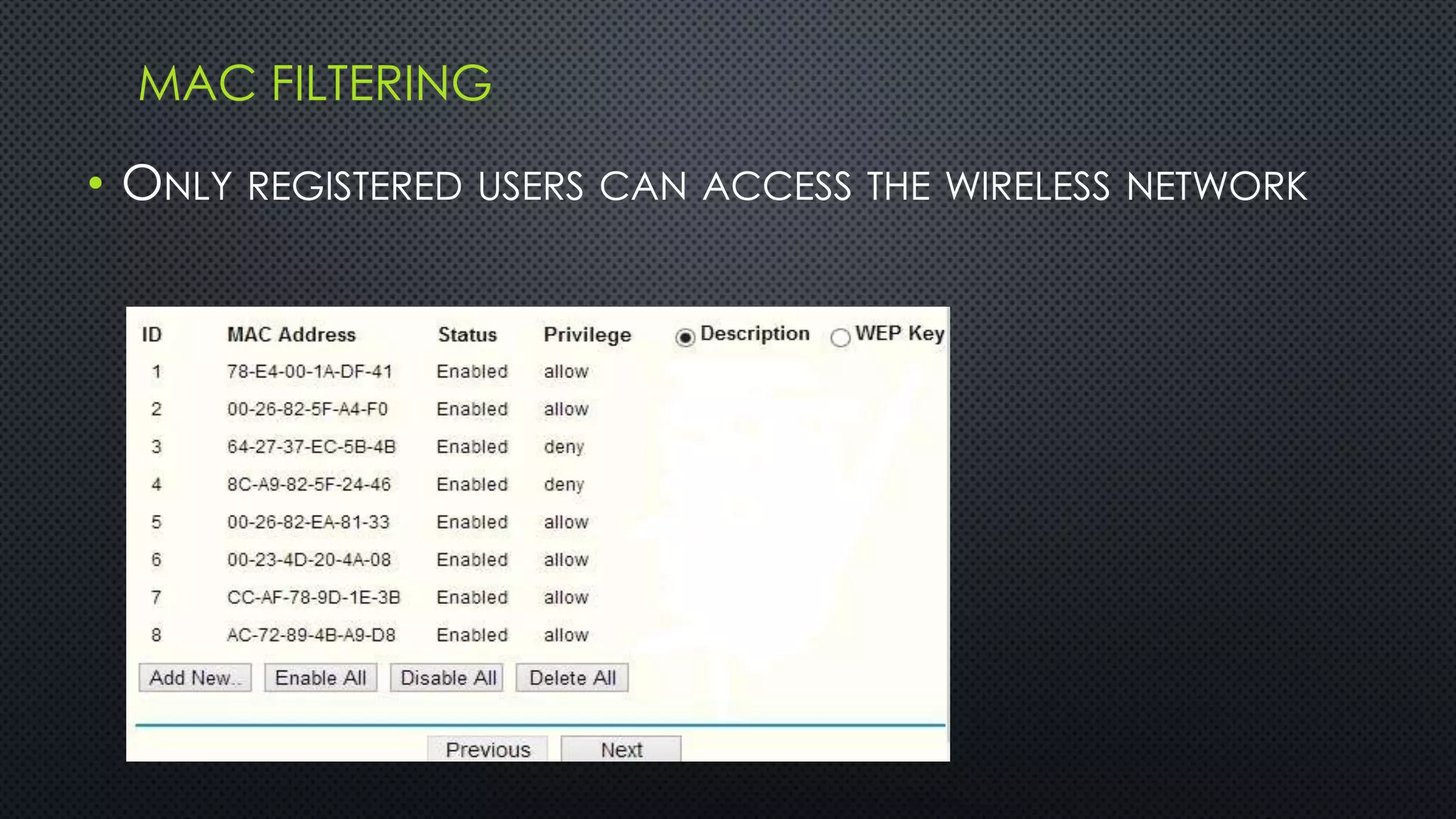
REMOTE ACCESS SECURITY:
• REMOTE ACCESS: TELNET (PORT 23)
• SECURE REMOTE ACCESS:
SSH VERSION 2 (PORT 22)
CONFIGURATION AS FOLLOWS:
Host identification (Using RSA-Keys)
Encryption (IDEA)
Authentication (RSA Challenge)
Router(config)# ip domain-name cisco.com
Router(config)# crypto key generate rsa
How many bits in the modulus [512]: 1024
% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]
Router(config)#exit
*Mar 1 0:4:8.988: %SSH-5-ENABLED: SSH 1.99 has been enabled
Router(config)#ip ssh version 2
Router(config)# username cisco password cisco
Router(config)# line vty 0 4
Router(config-line)# login local
Router(config-line)# transport input ssh
Router(config)#ip ssh time-out 90
Router(config)#ip ssh authentication-retries 2](https://image.slidesharecdn.com/securea-131008160454-phpapp02/75/Secure-Network-Design-with-High-Availability-VoIP-44-2048.jpg)