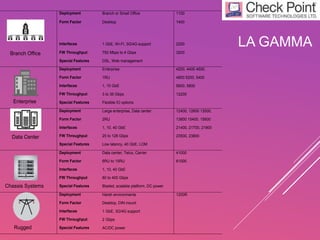
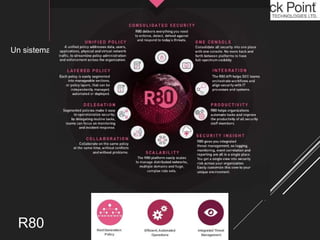
Check Point is a cyber security company founded in 1993 that has adapted to meet customers' needs over the years. It offers a comprehensive portfolio of security products including threat prevention appliances, endpoint security, mobile security, network protection, security management, and public/private cloud solutions. Check Point aims to provide holistic security services and sees security as an integral part of business processes.