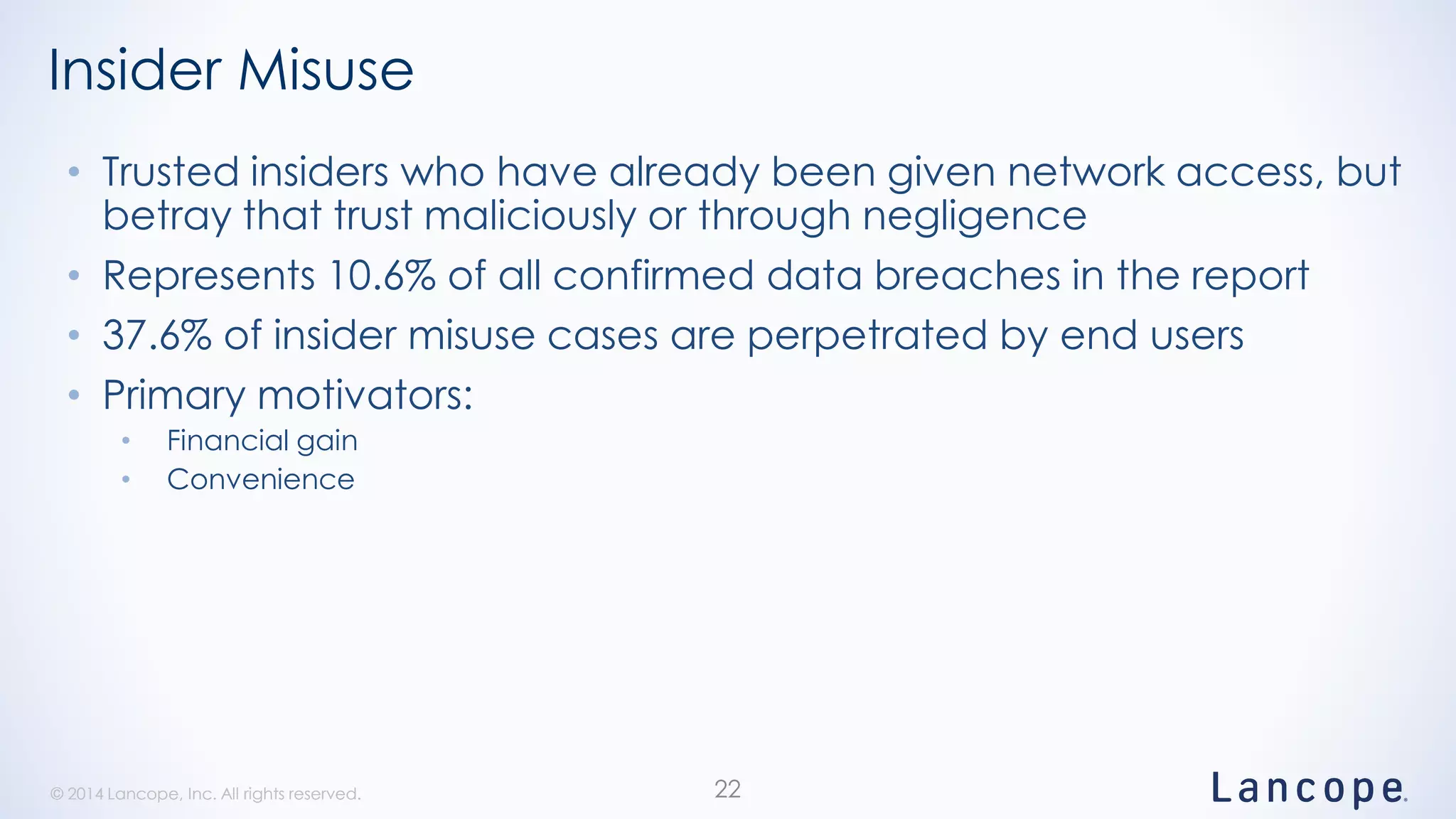
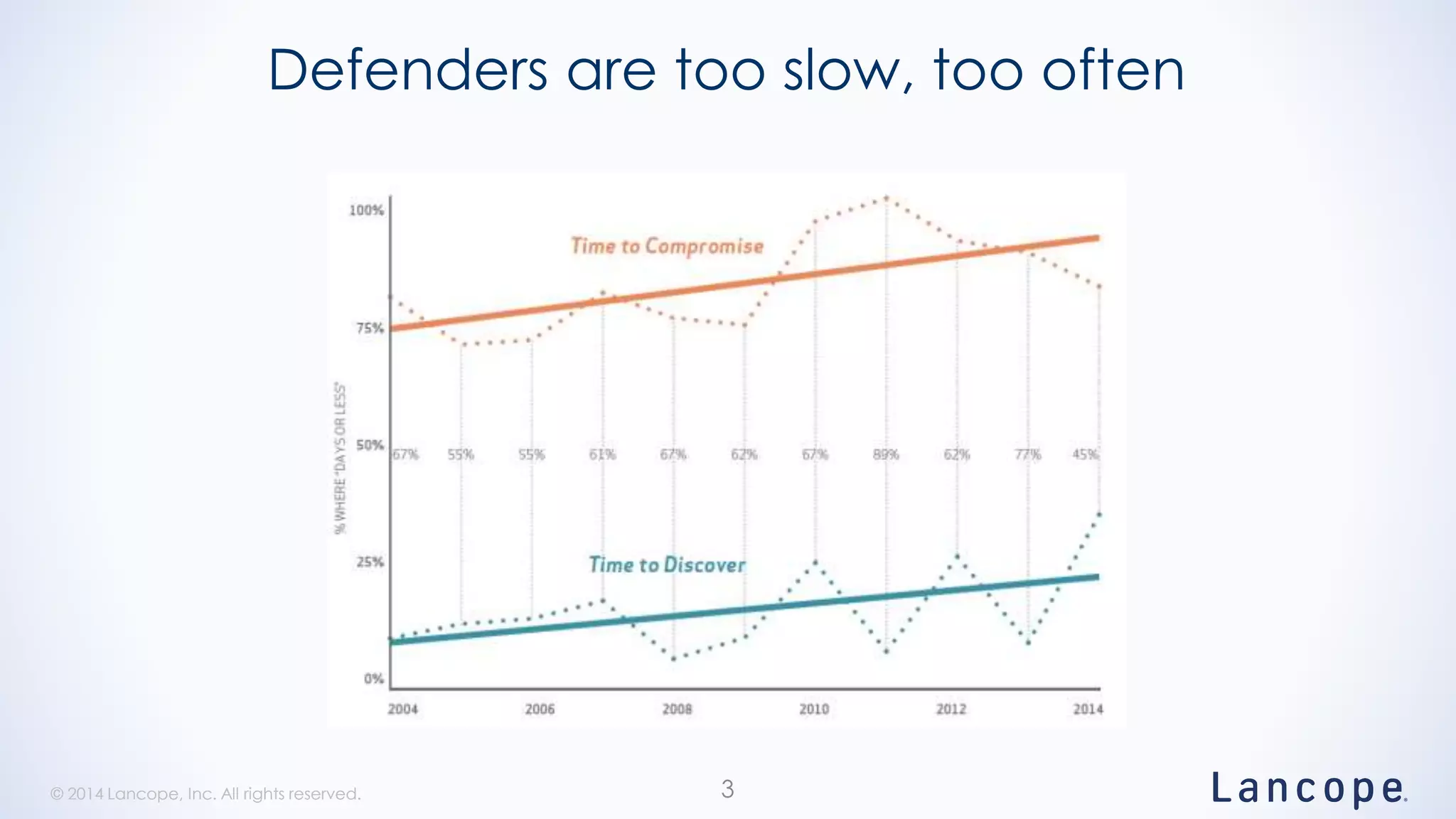
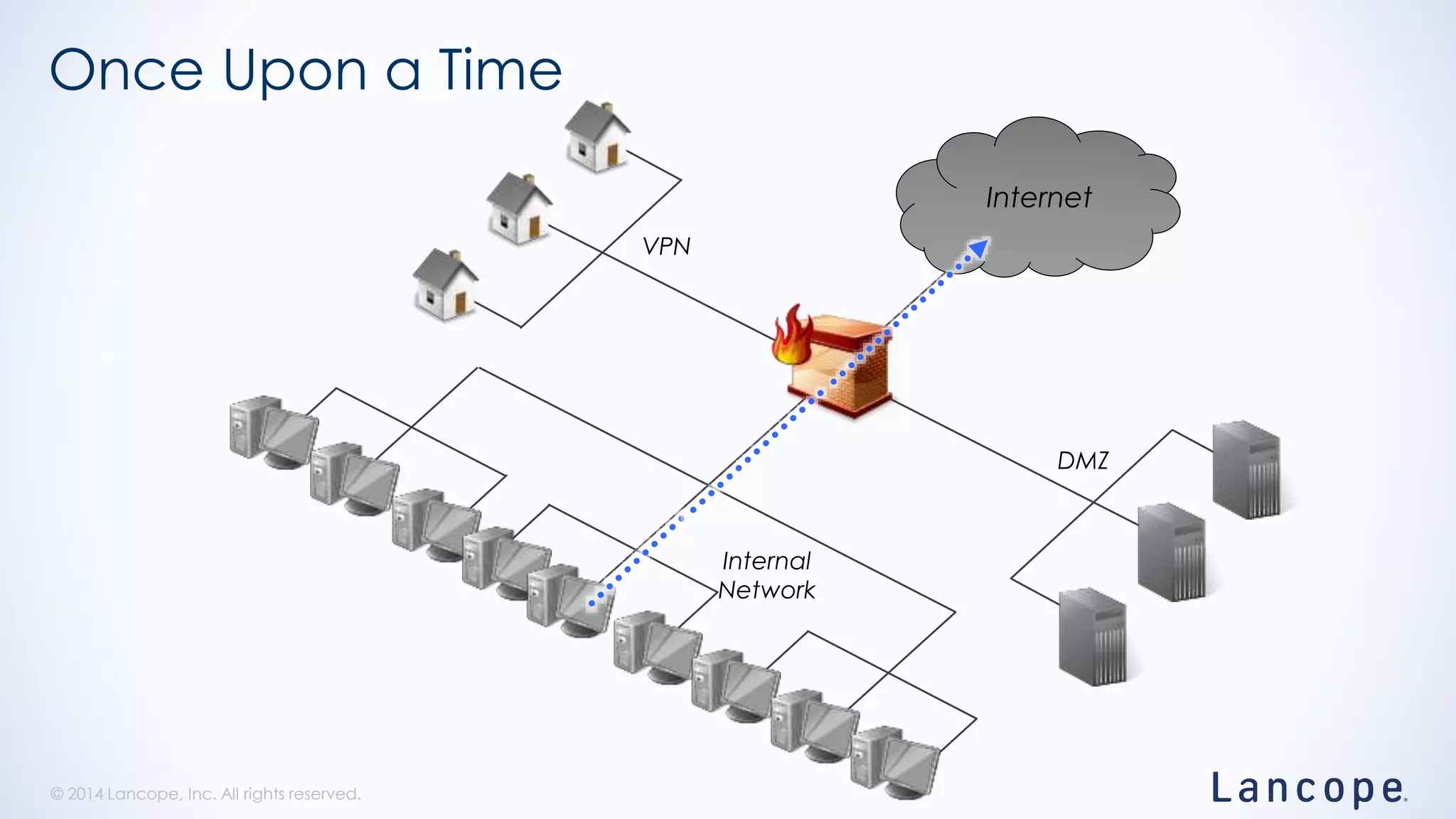
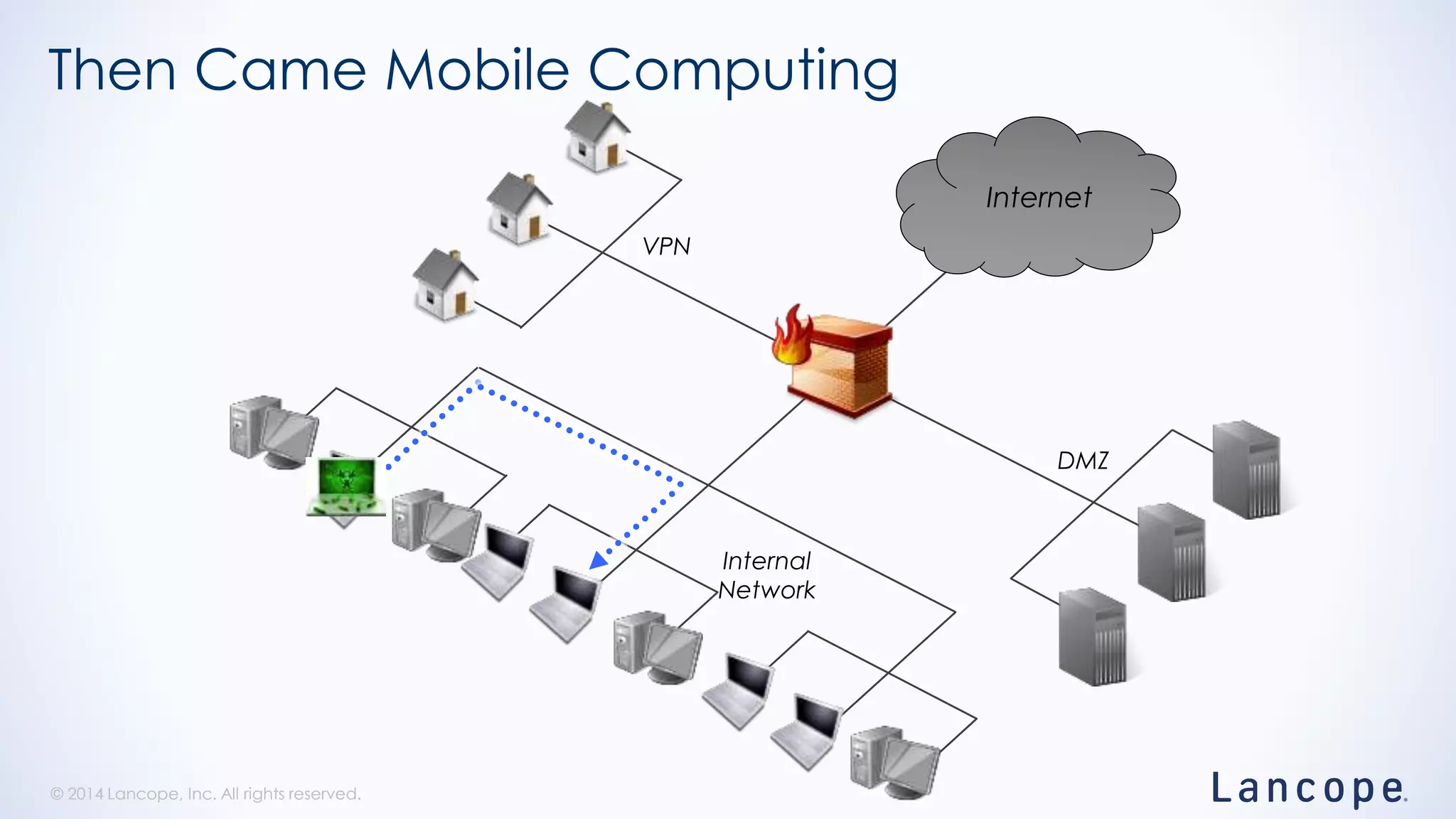
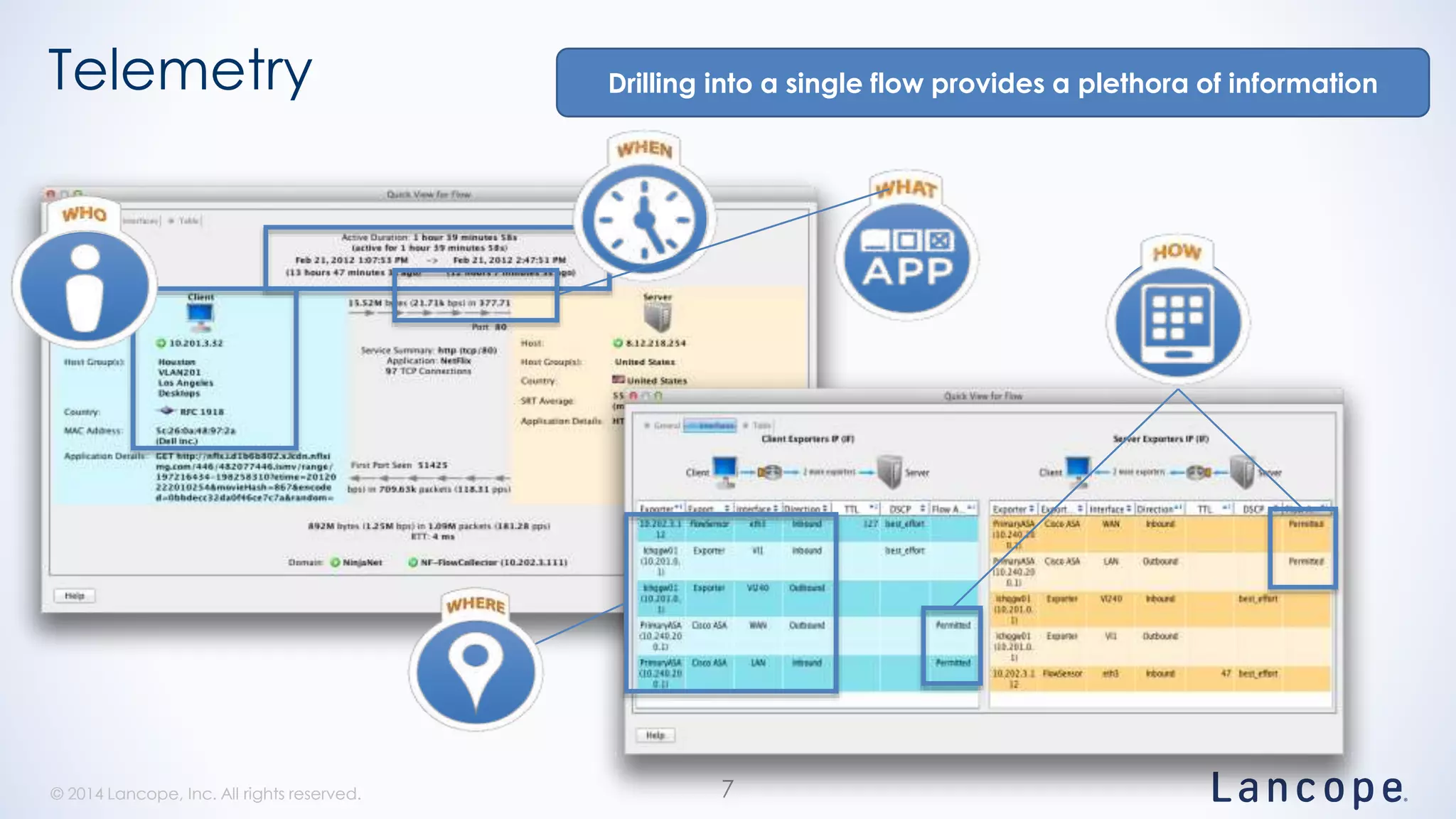
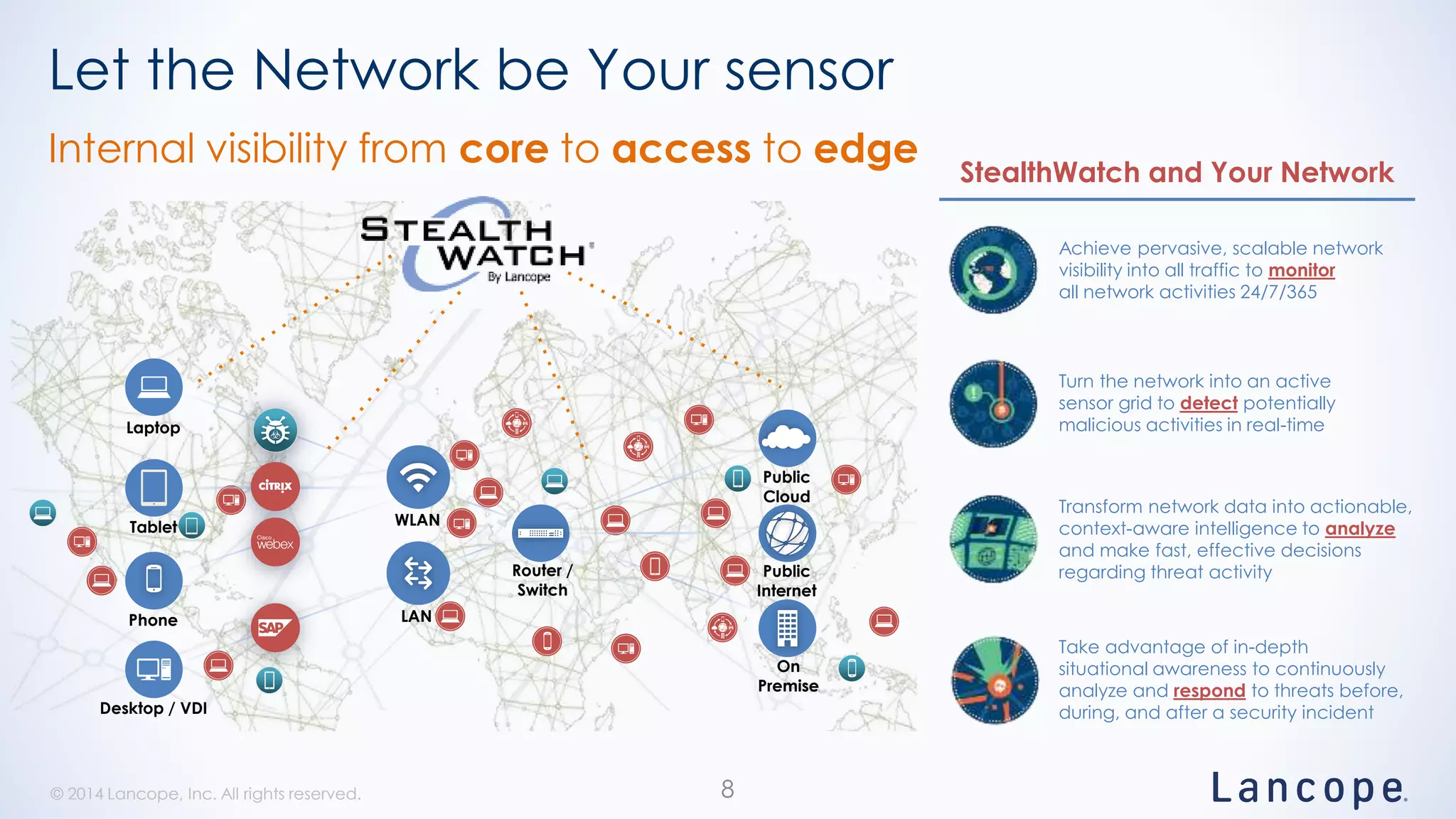
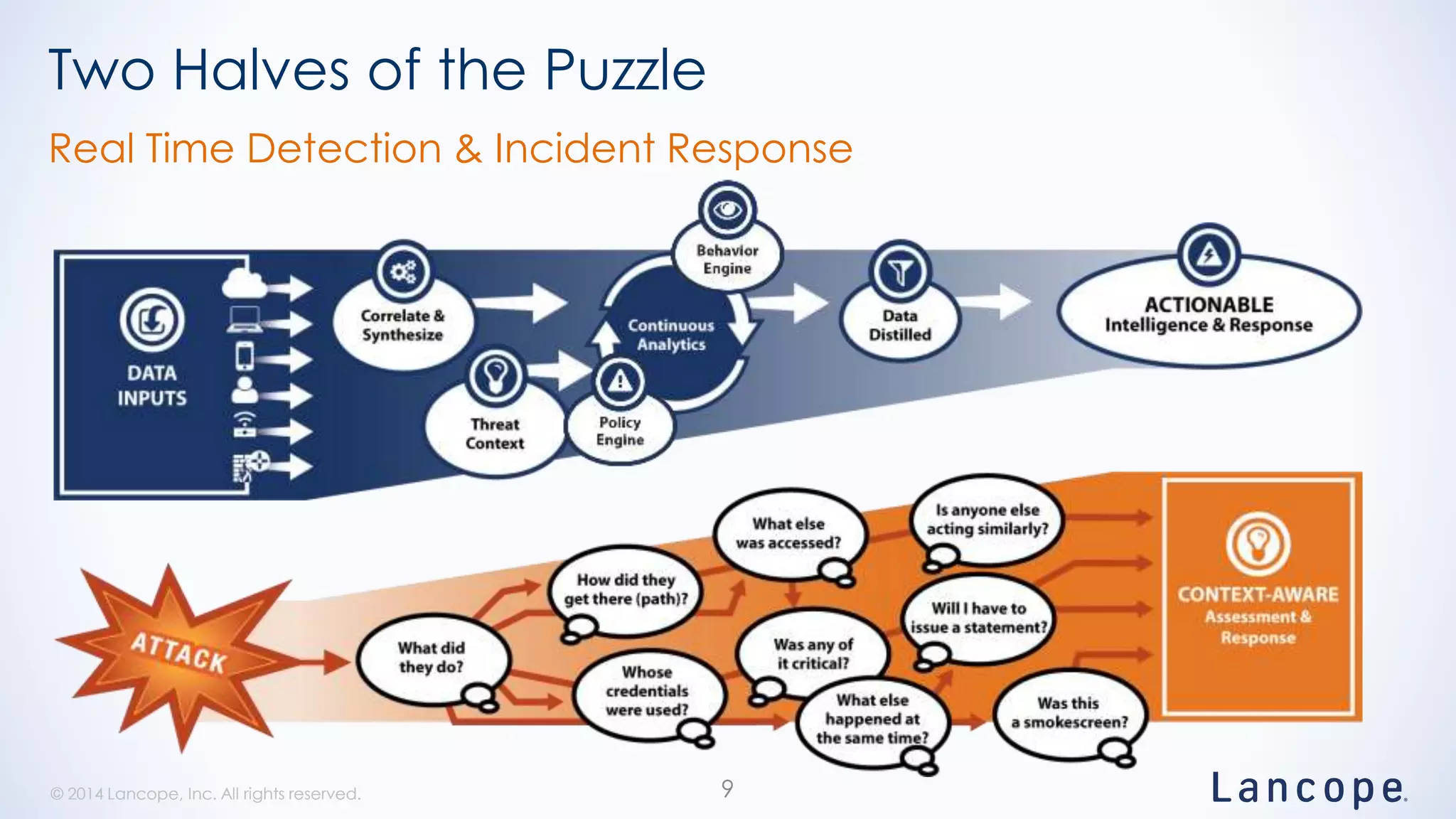
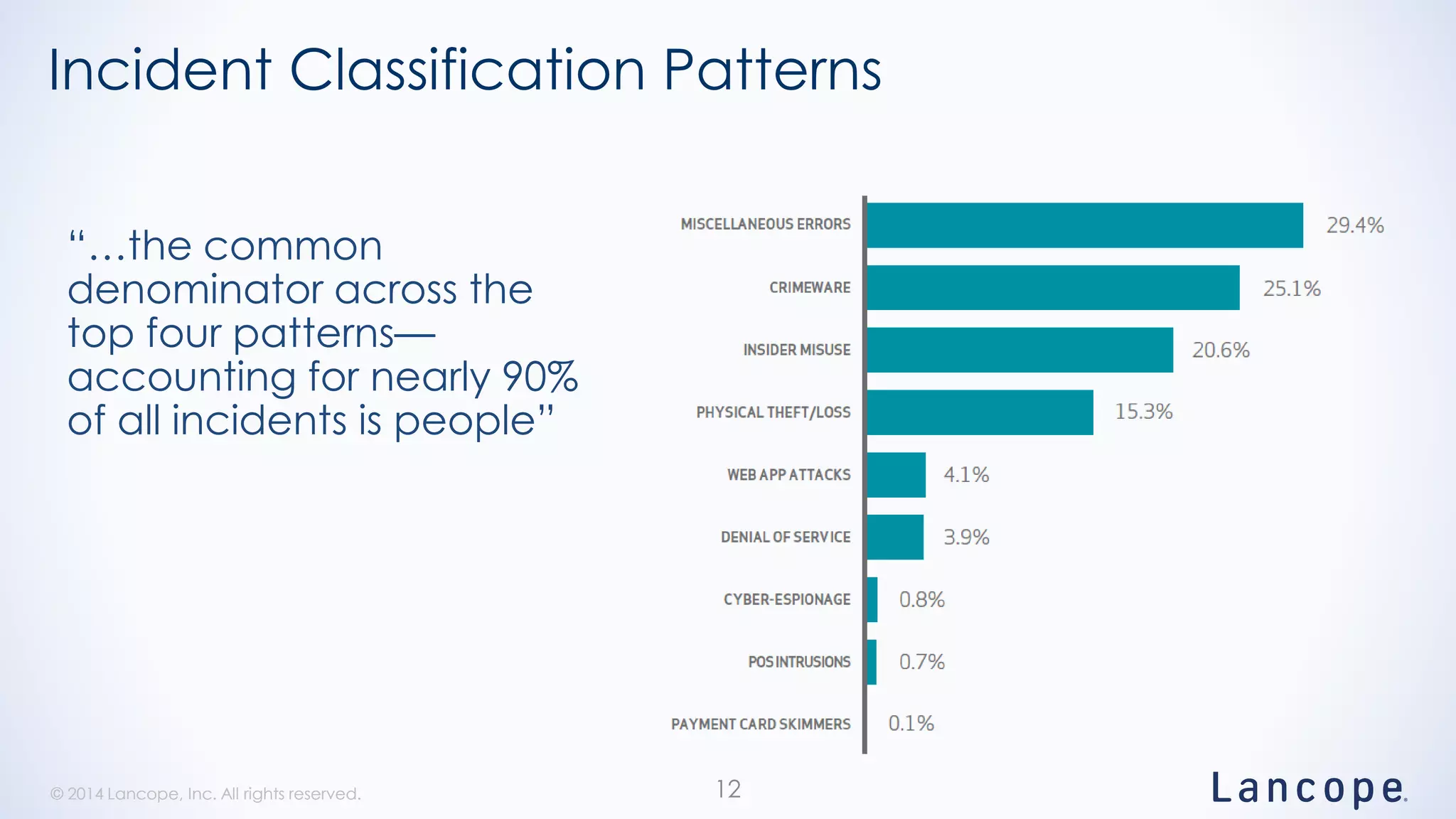
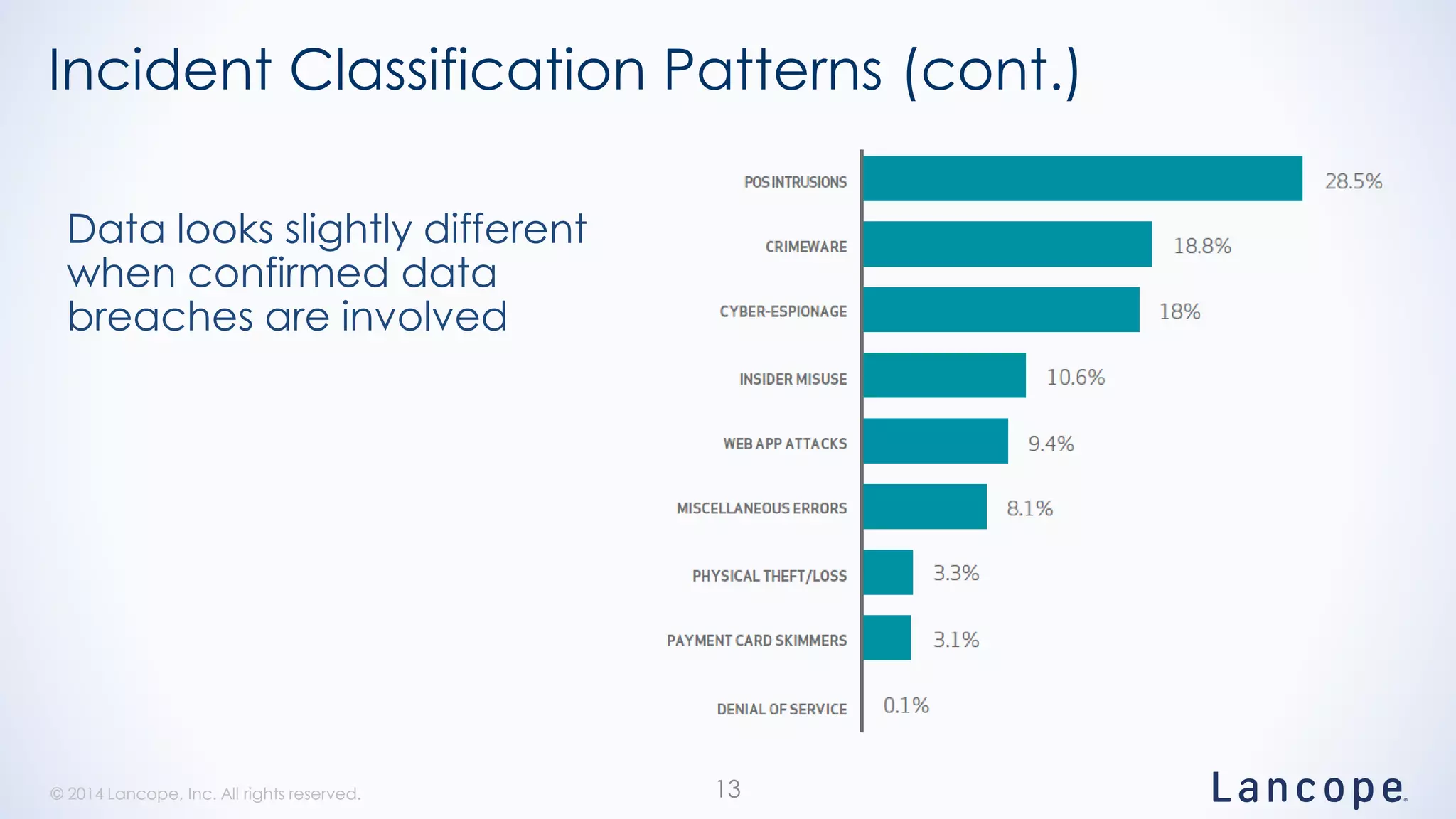
The document discusses threat detection through Lancope's Stealthwatch in relation to insights from the Verizon Data Breach Investigations Report (DBIR). It highlights the common types of data breaches, emphasizing that the majority of incidents involve human factors and includes breaches due to point-of-sale intrusions, cyber-espionage, and insider misuse. Additionally, it advocates for continuous monitoring of network traffic to enhance threat detection and response capabilities.








![© 2014 Lancope, Inc. All rights reserved.© 2014 Lancope, Inc. All rights reserved. 18
DDoS Source
---
[tcp|udp|icmp] Flood
Slow Connection Flood
Packet Flood
High Total Traffic
TCP Resets
Scanning / Brute Force
---
Address Scan [tcp|udp]
Stealth Scan [tcp|udp]
ICMP Port Unreachable
Talks to Phantoms (6.6)
Brute Force Login (6.6)
Mail
---
Spam Source
High Volume Email
Mail Reject](https://image.slidesharecdn.com/detectingthreats-alookattheverizondbirandstealthwatch-151030132009-lva1-app6892/75/Detecting-Threats-A-Look-at-the-Verizon-DBIR-and-StealthWatch-18-2048.jpg)


![© 2014 Lancope, Inc. All rights reserved.© 2014 Lancope, Inc. All rights reserved. 21
Detect and stop lateral
movement inside the network
Address Scan [tcp|udp]
Stealth Scan [tcp|udp]
ICMP Port Unreachable
Talks to Phantoms (6.6)
Brute Force Login (6.6)](https://image.slidesharecdn.com/detectingthreats-alookattheverizondbirandstealthwatch-151030132009-lva1-app6892/75/Detecting-Threats-A-Look-at-the-Verizon-DBIR-and-StealthWatch-21-2048.jpg)