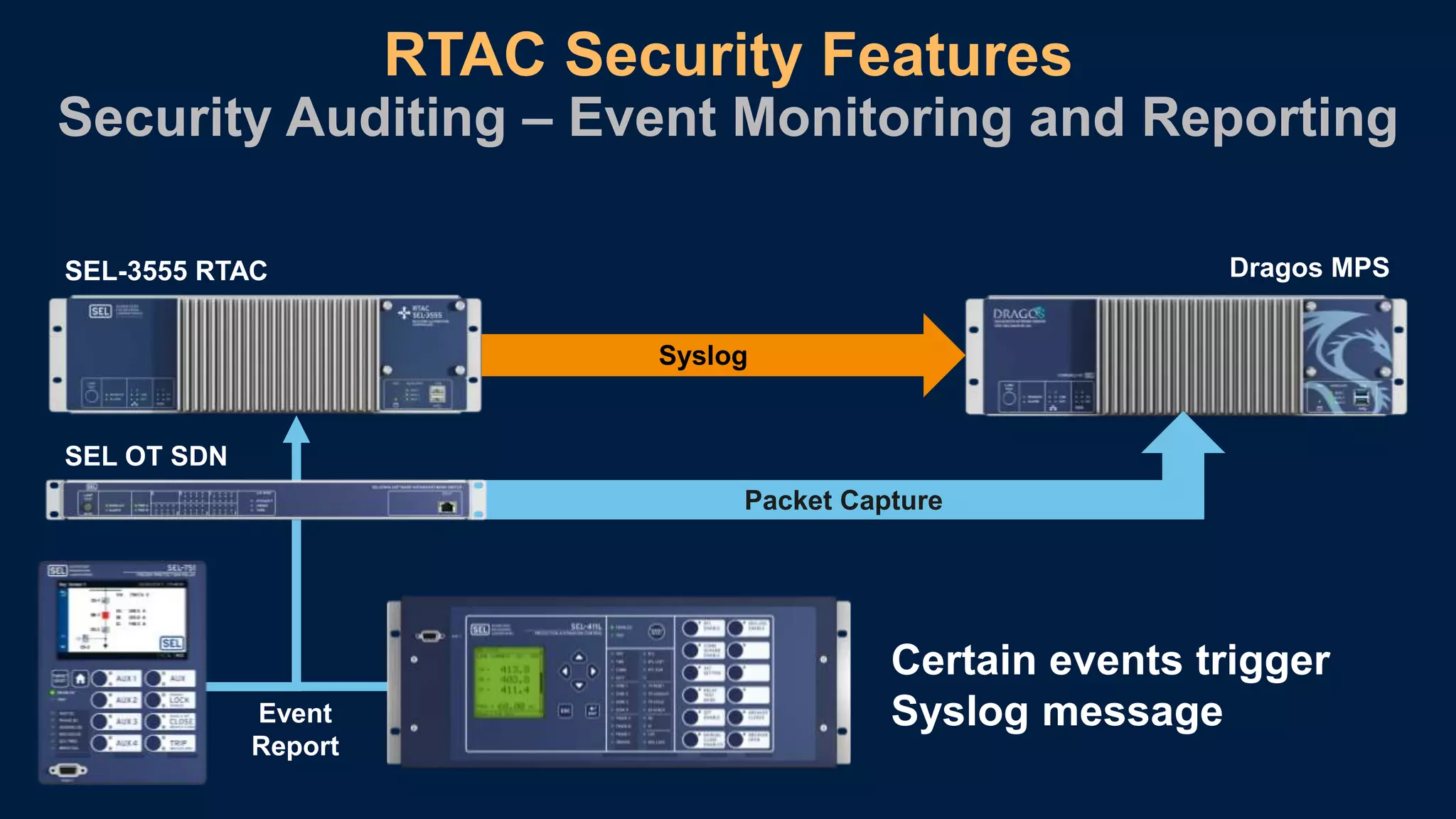
The document discusses a case study on enhancing cybersecurity for electric utility infrastructure through asset baselining, threat detection, and response strategies. It highlights challenges such as limited personnel, compliance issues, and the need for better threat awareness, along with proposed solutions including improved visibility and proactive threat hunting. The collaboration between Schweitzer Engineering Laboratories (SEL) and Dragos emphasizes the importance of integrating technology and personnel for effective defense against increasing cyber threats.