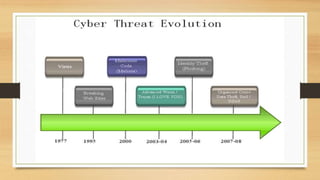
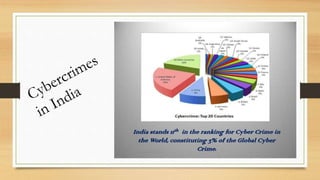
This document discusses cybercrime and security, including what cybercrime is, the history and categories of cybercrimes, common types like hacking and viruses, algorithms used in cybercrimes, and cyber security measures to protect against threats. Cybercrime involves any illegal activity using computers or networks, and can target computers directly or use them to enable real-world crimes, while cyber security aims to establish rules and protections against internet attacks.