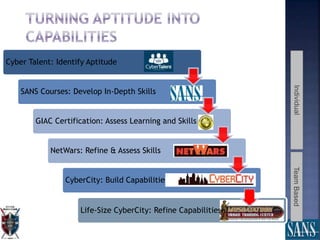
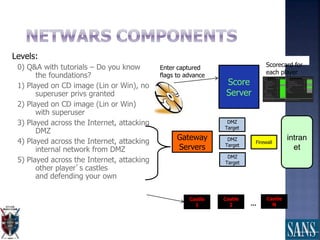
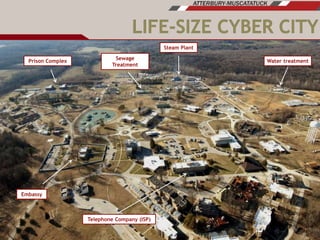
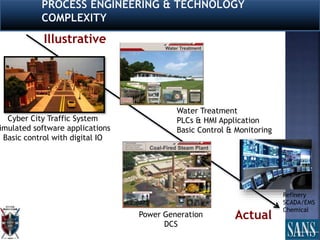
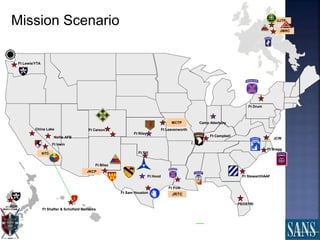
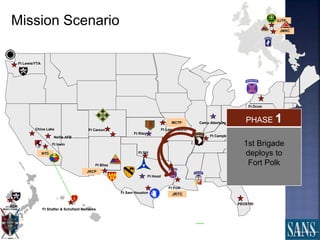
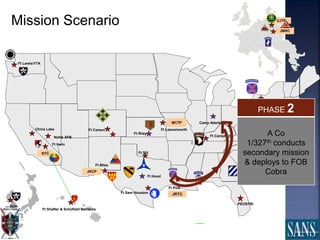
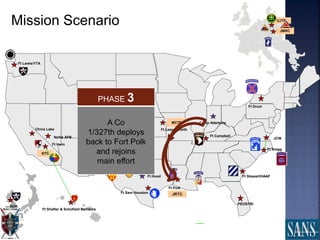
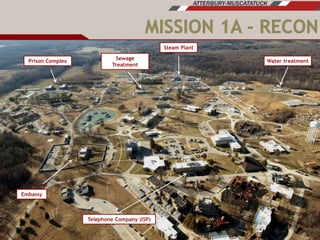
The document discusses plans for using a miniature city infrastructure called "CyberCity" to train cyber warriors. It describes CyberCity as a 1:87 scale physical model incorporating elements like a power grid, transportation systems and buildings that can be remotely controlled for offensive and defensive cyber missions. The goal is to demonstrate the kinetic impact of cyber attacks in a hands-on way and help trainees recognize real-world consequences. Initial missions discussed include disabling enemy weapons and manipulating traffic to support first responders. The document recommends starting with simpler missions and expanding complexity over time.














!["Leveraging inferior tactical or operational
strength against [the enemy’s] vulnerabilities
to achieve disproportionate effect with the
aim of undermining [their] will in order to
achieve the asymmetric actor's strategic
objectives.”
Kenneth McKenzie, NDU](https://image.slidesharecdn.com/sanstechnetaugustamegacitypresentation20150820-150903124131-lva1-app6892/85/Cyber-Operations-in-Smart-Megacities-TechNet-Augusta-2015-17-320.jpg)