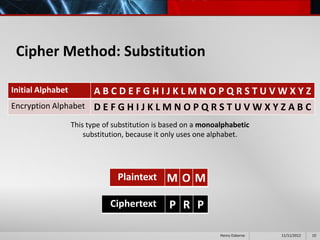
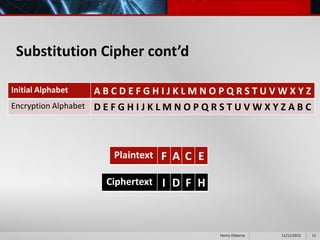
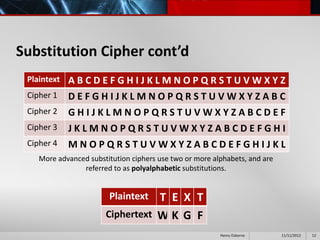
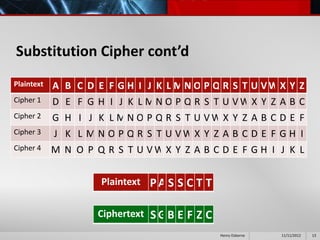
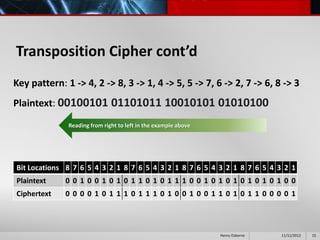
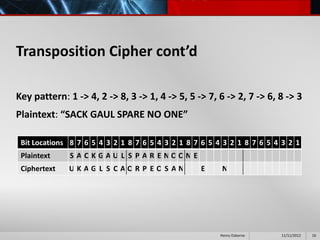
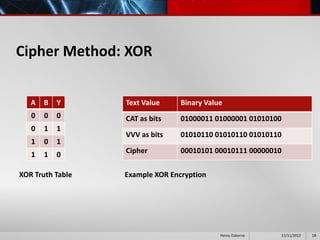
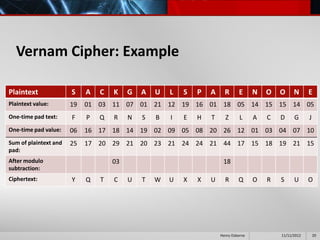
This document provides an overview of cryptography presented by Henry Osborne. It defines cryptography as the process of making and using codes to secure information transmission. It discusses key terms like ciphertext, plaintext, and key. It also summarizes several cipher methods: substitution cipher, transposition cipher (also known as permutation cipher), exclusive OR (XOR), and the Vernam cipher (also called the one-time pad). The presentation concludes by noting that while codes can secure information, human ingenuity will ultimately find a way to resolve any cipher.