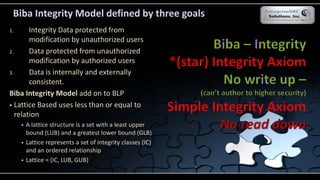
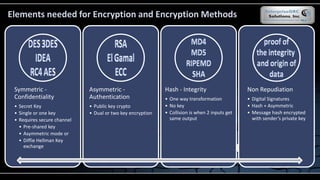
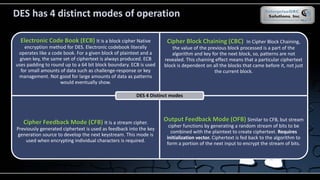
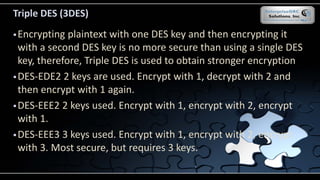
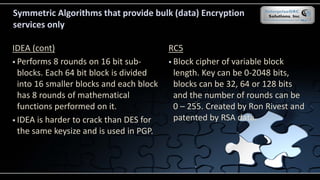
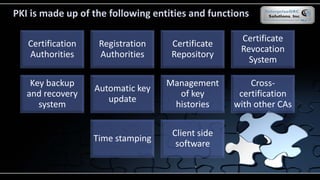
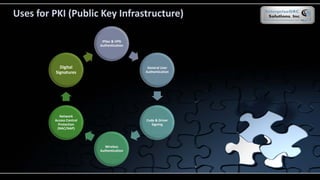
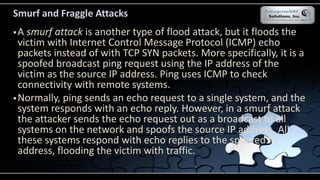
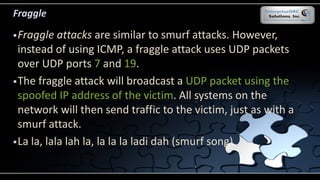
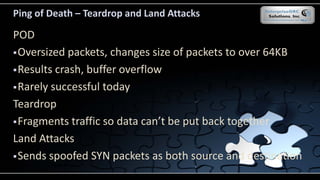
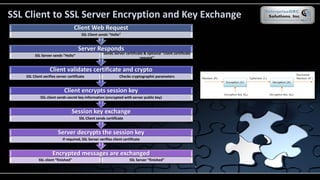
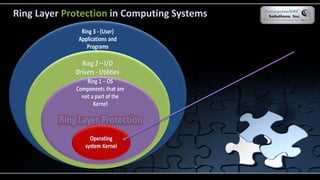
The document covers various security models and practices relevant to cryptography and information integrity in security engineering, including the Bell-LaPadula and Biba models, as well as the Clark-Wilson integrity model. It discusses cryptographic lifecycle management, including algorithm selection, key management, and the roles of symmetric and asymmetric encryption methods. Furthermore, it addresses denial-of-service attacks, botnets, and specific exploits, highlighting vulnerabilities in protocols like SSL and TLS.