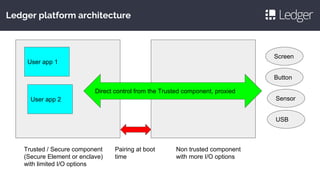
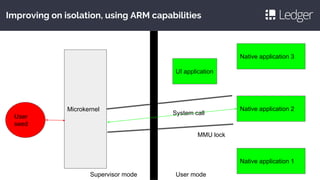
Cryptocurrency hardware wallets provide a secure way to store private keys by protecting them in a dedicated device. They address risks of online attacks, malware, and phishing by requiring confirmation on the hardware device. A new class of devices was needed that makes private key storage easy to use, recoverable, auditable, and adaptable while protecting against creative malware and side channel attacks through techniques like deterministic signing, constant time crypto, and isolation between trusted and non-trusted components. Popular implementations take different approaches by being fully open source versus using a secure element, but aim to balance security, auditability and ease of use.