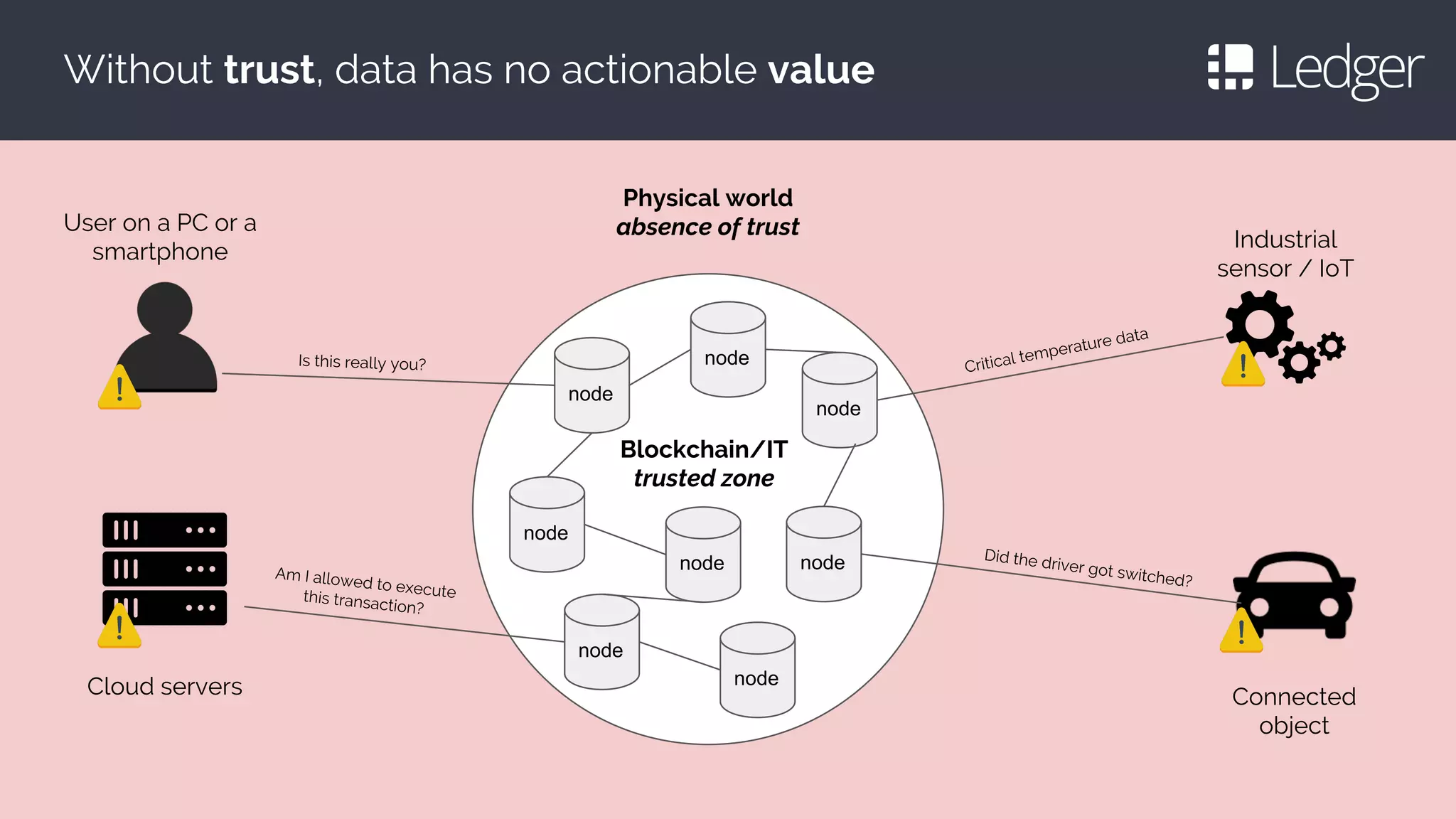
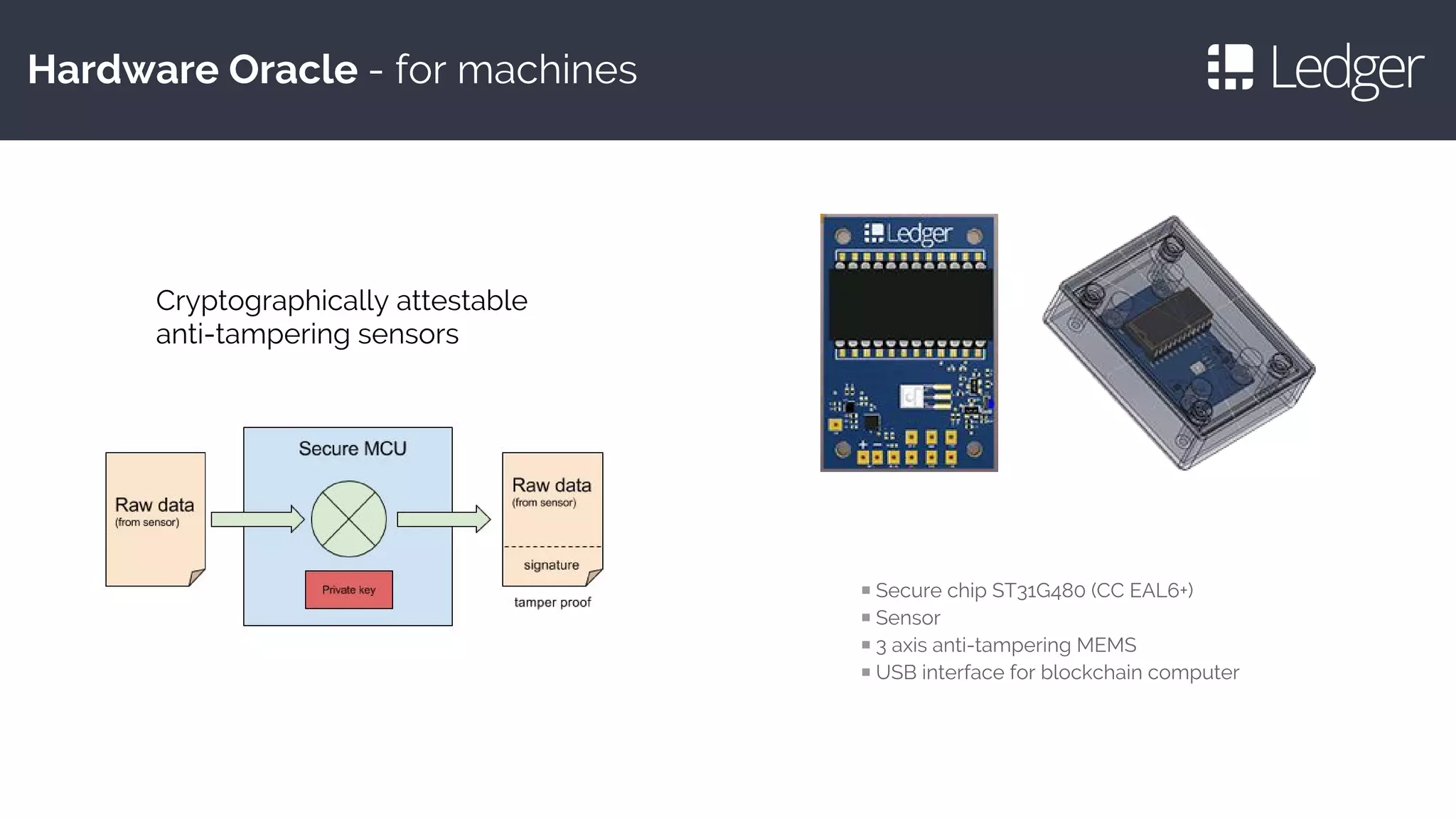
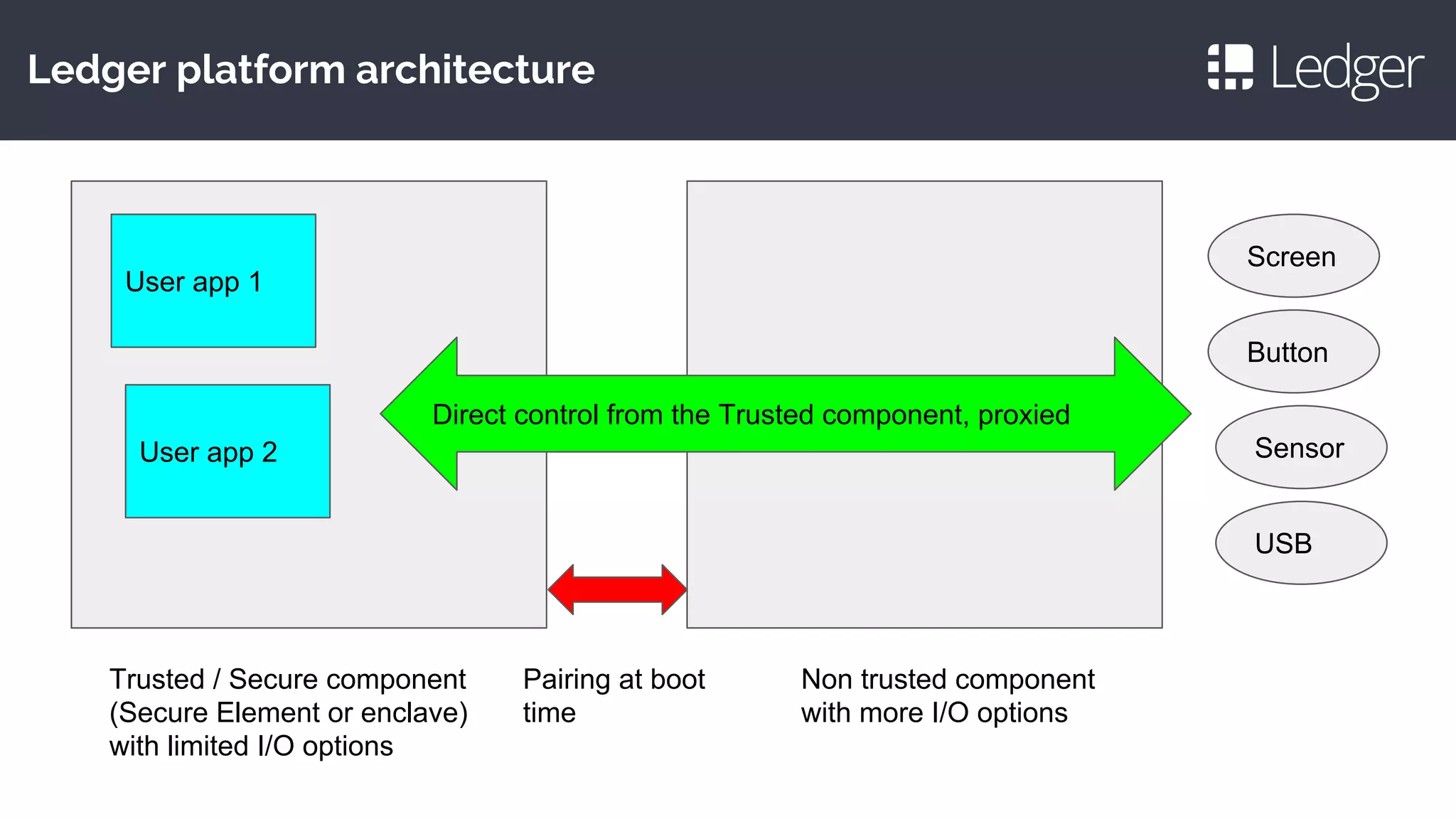
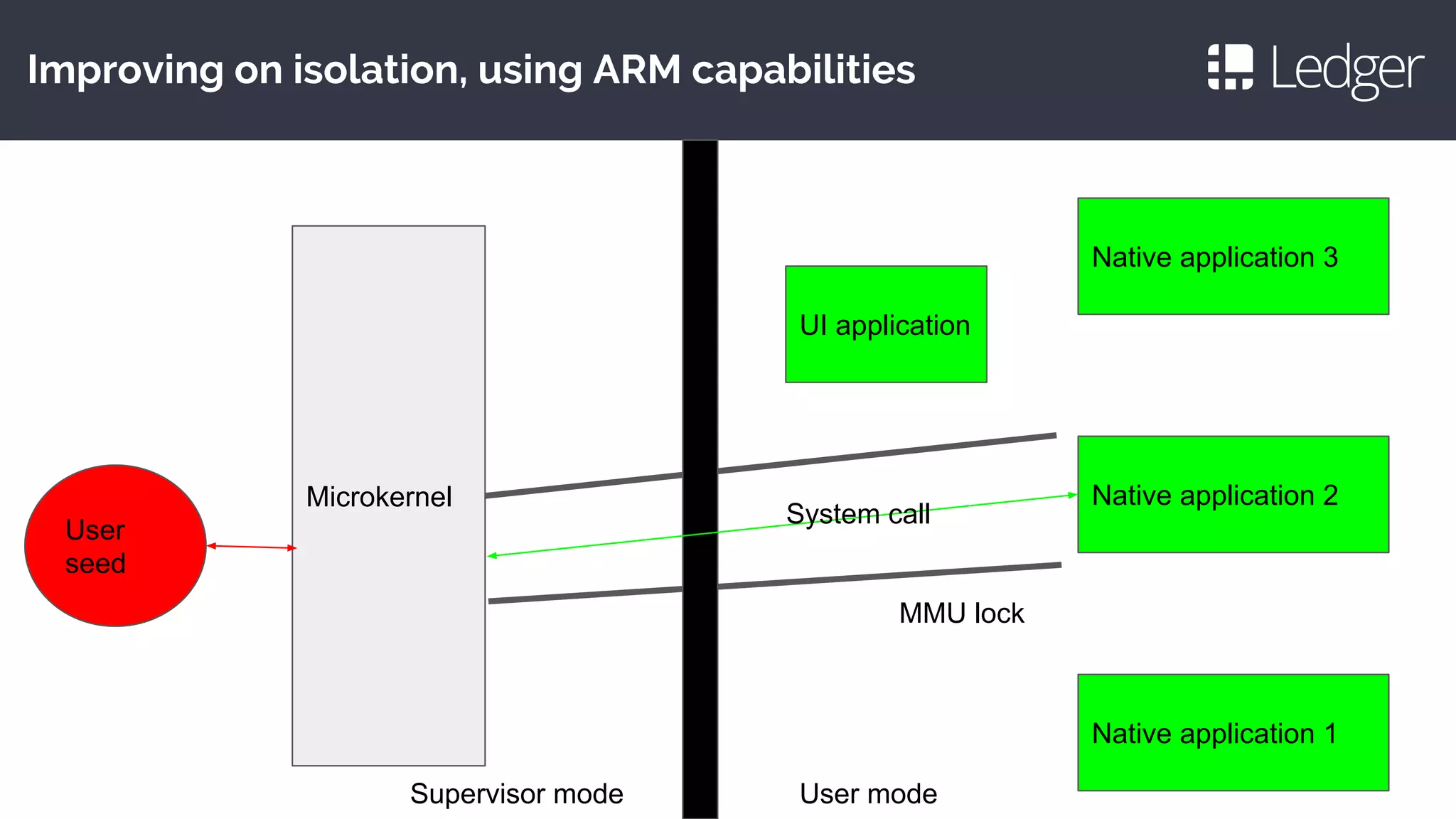
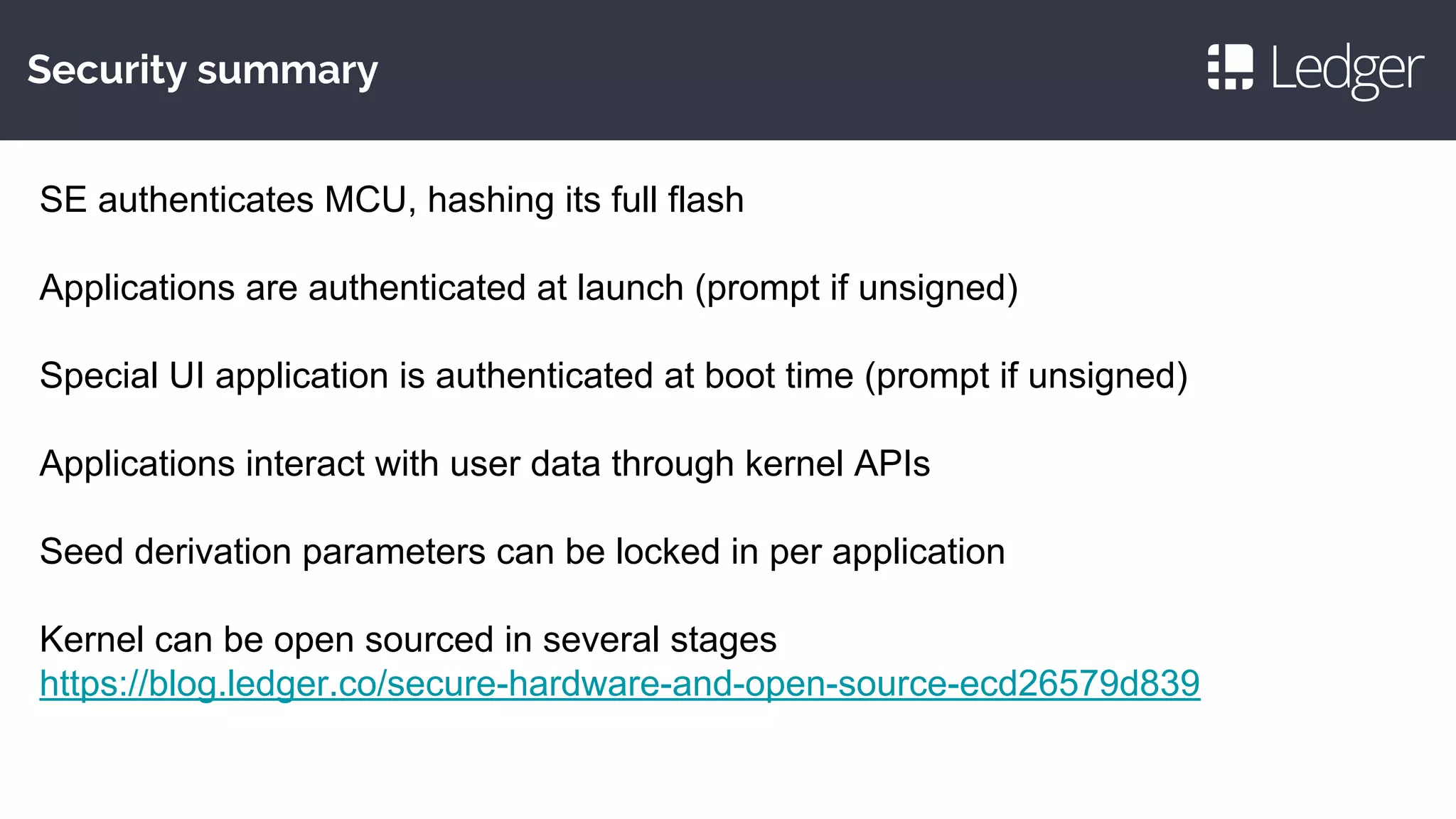
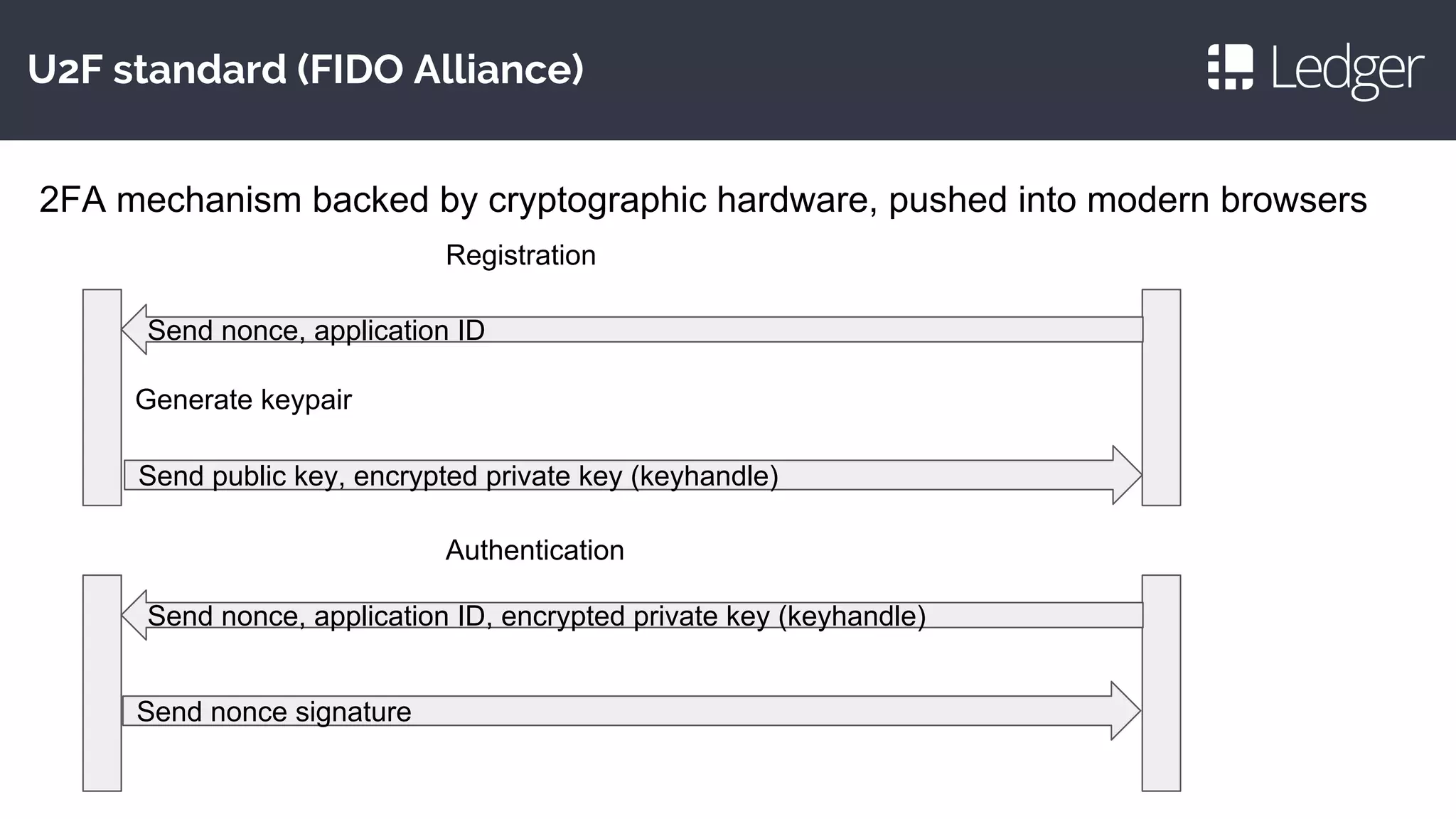
This document discusses making smartcards more useful for security applications by building a trust layer between blockchains and the physical world. It proposes using secure elements like smartcards combined with secure microcontrollers to create cryptographically authenticated hardware security tokens. These devices would allow installing applications securely, authenticating to blockchains, and improving on smartcard limitations regarding developers and auditing. Examples given include the Ledger Nano S hardware wallet and plans to implement bitcoin, ethereum, and other cryptocurrency applications as well as password management and OpenPGP.