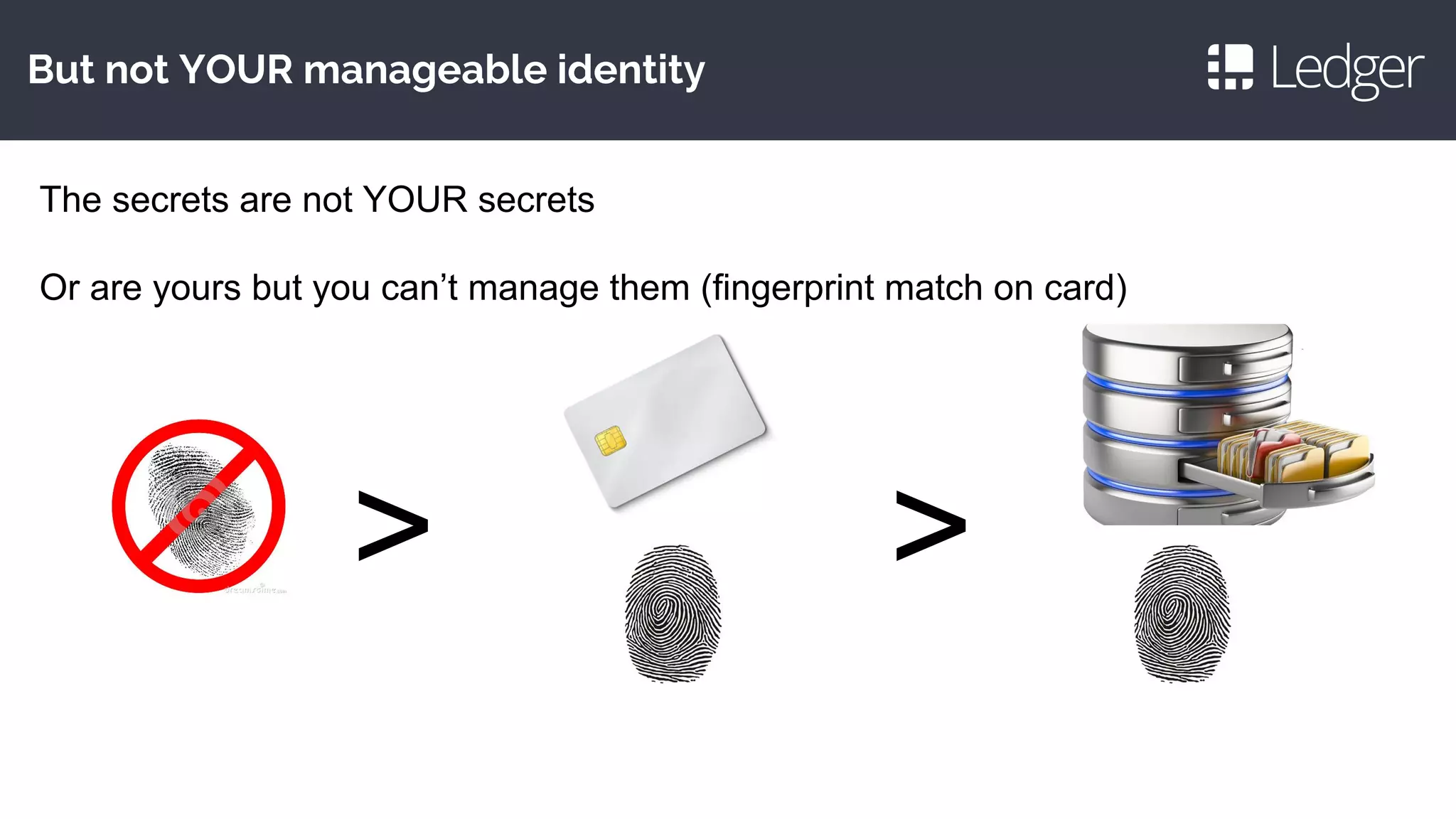
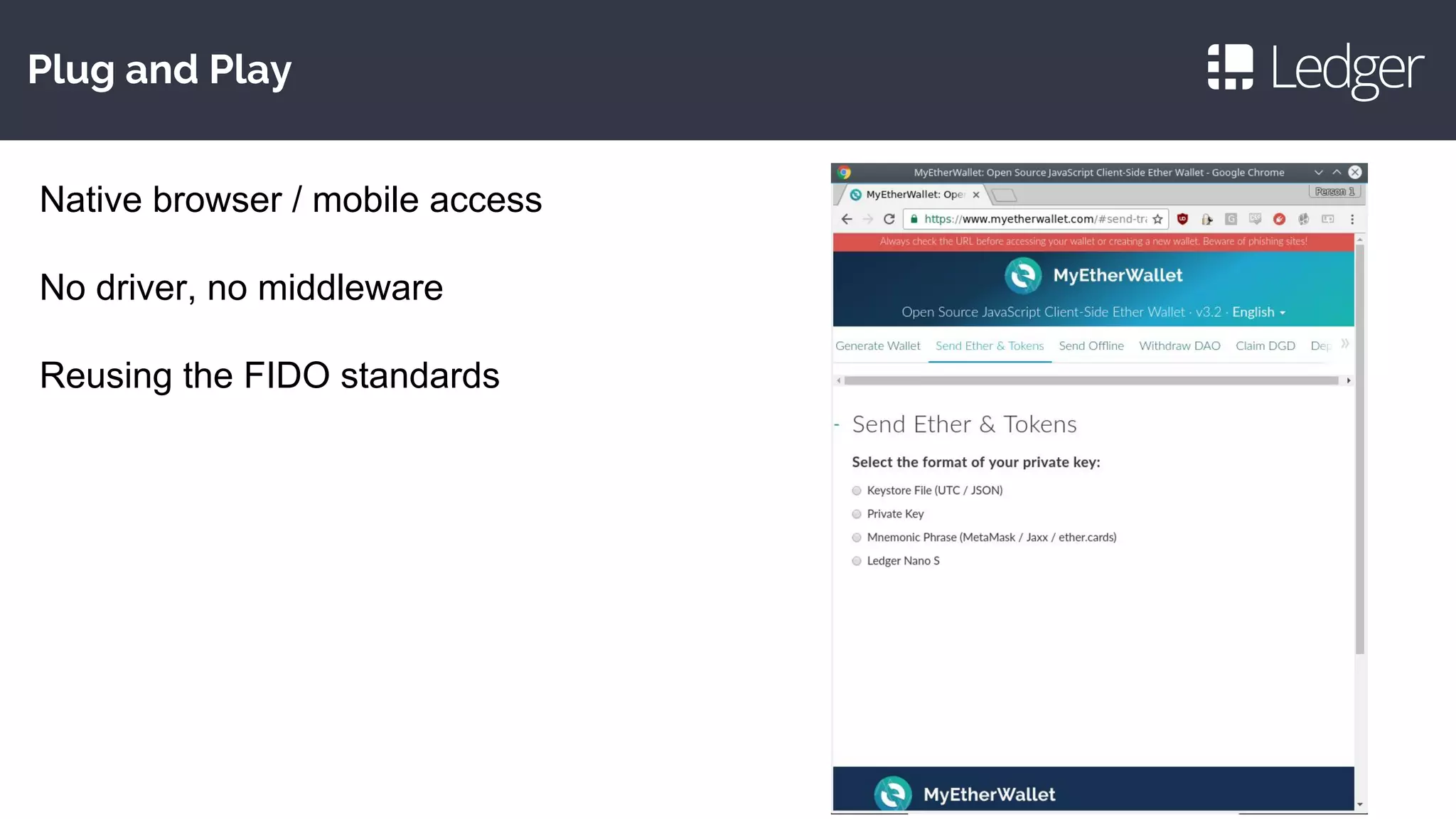
1. The document discusses rebooting the smartcard concept to make it more plug and play, developer friendly, and malware resistant.
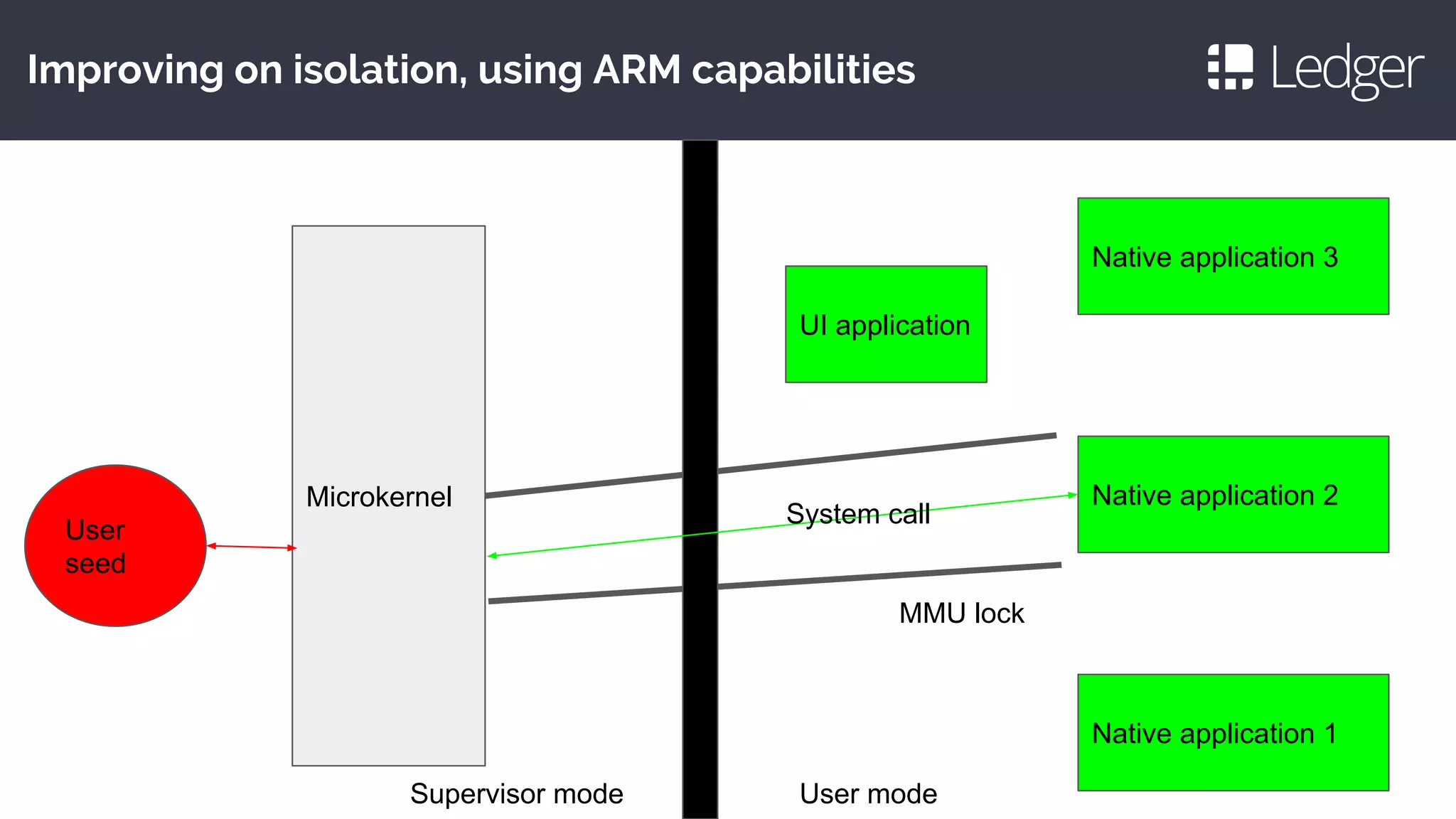
2. It proposes isolating secure and non-secure code using a microkernel architecture to improve auditability.
3. Details are provided on Ledger's latest consumer devices, the Ledger Nano S and Ledger Blue, and resources for developers including sample apps and documentation.