This document provides information about VMware, including:
- VMware is headquartered in Palo Alto with over 17,800 employees worldwide and over $25 billion in revenues.
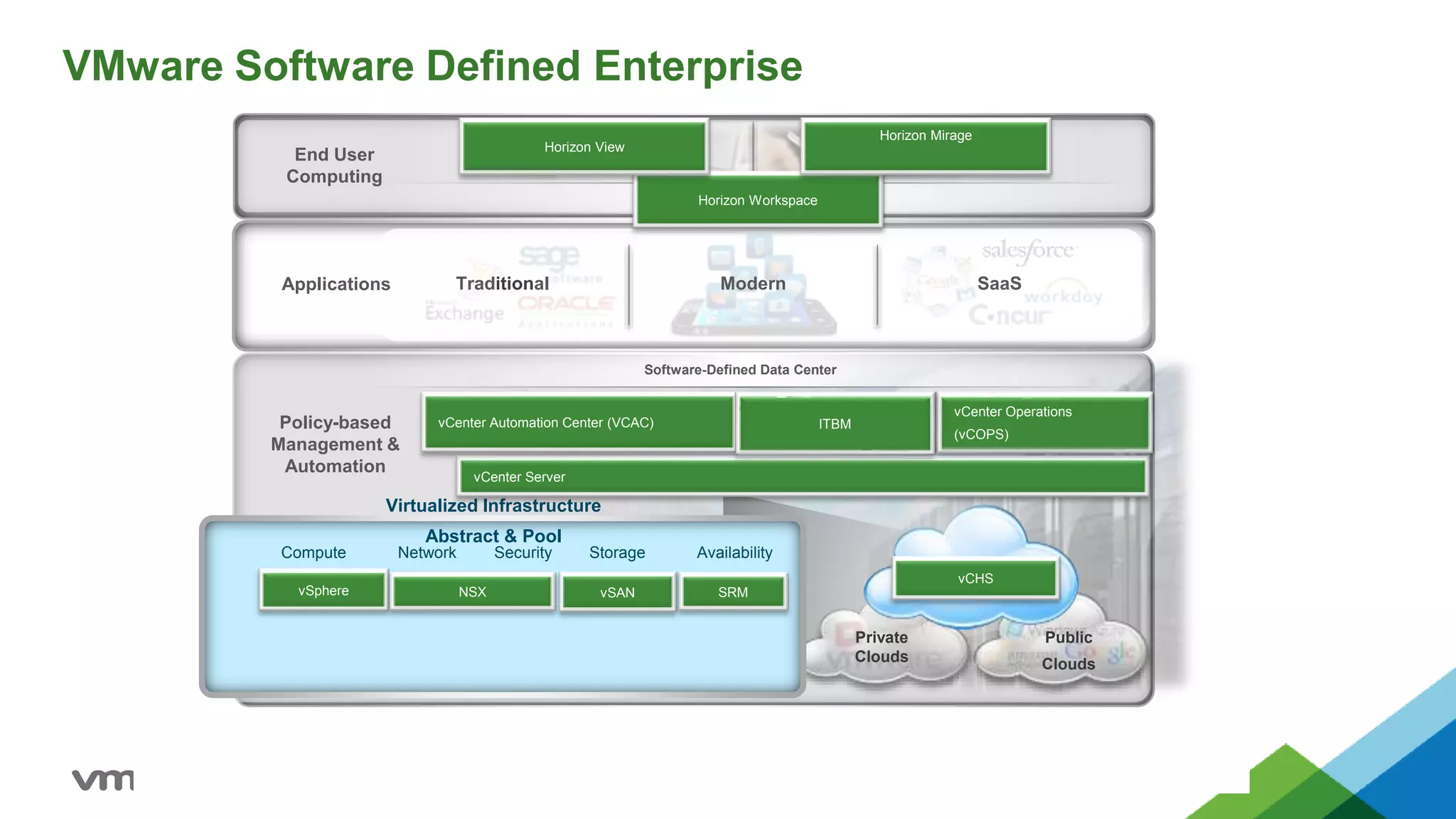
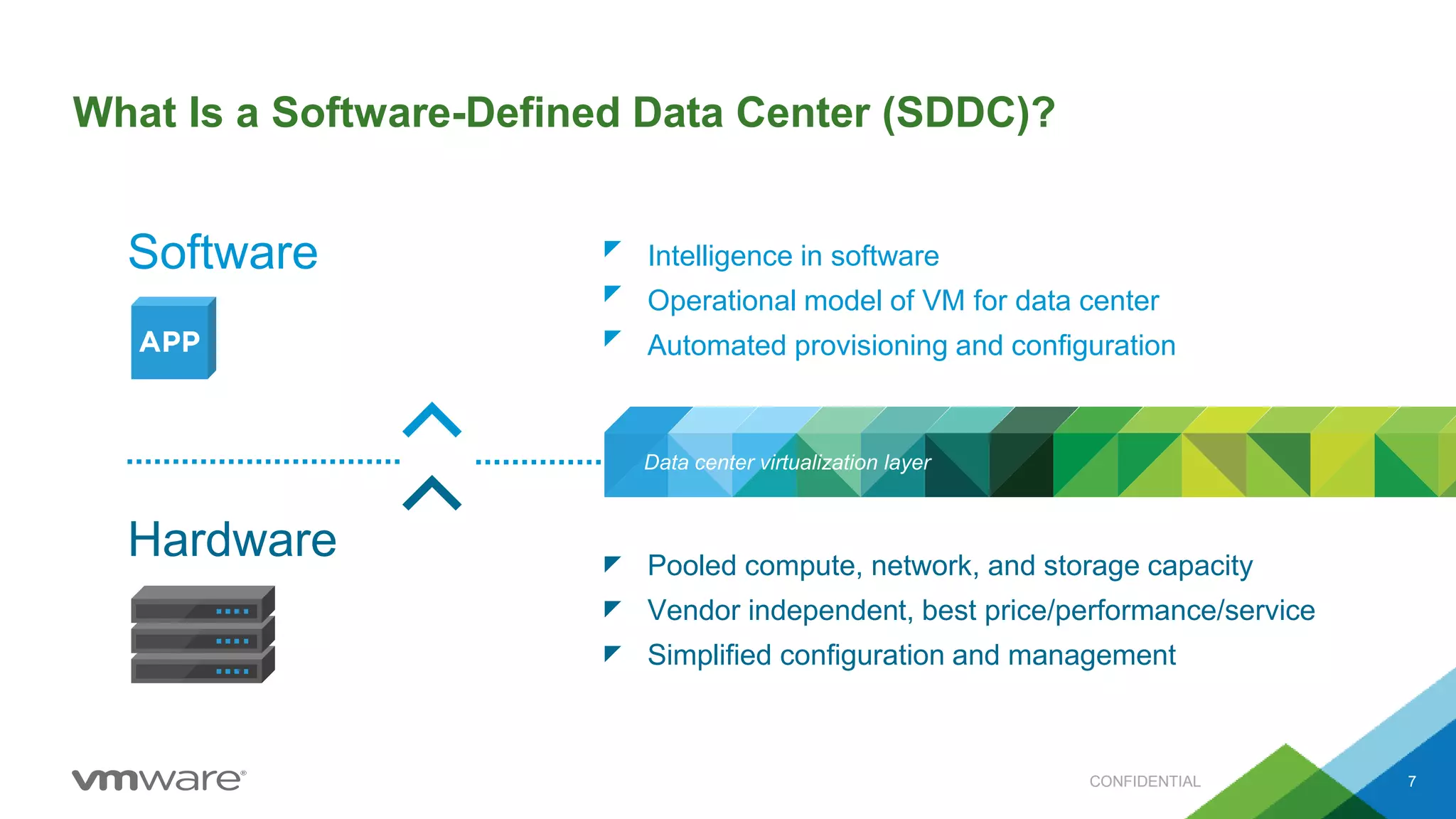
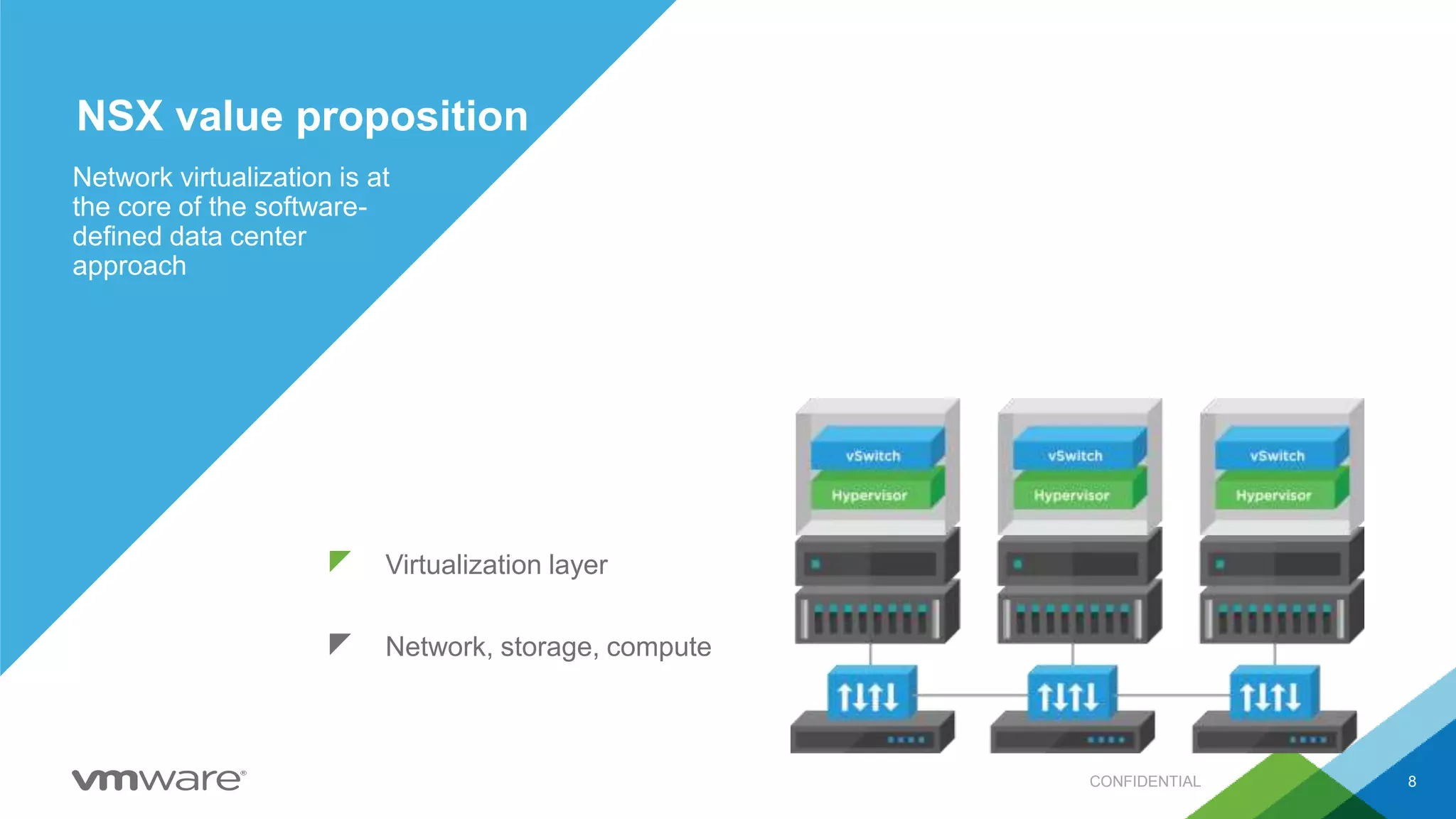
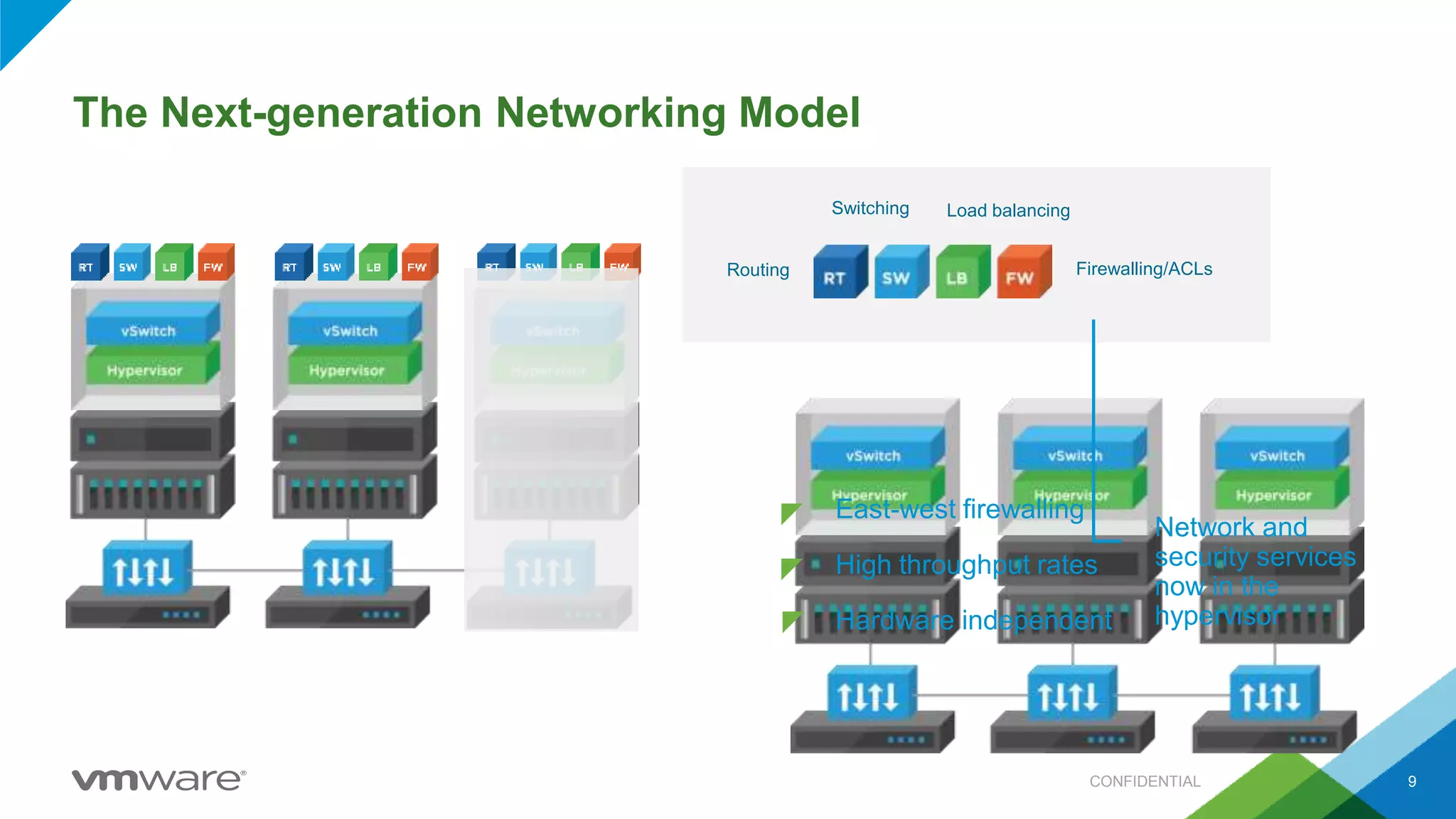
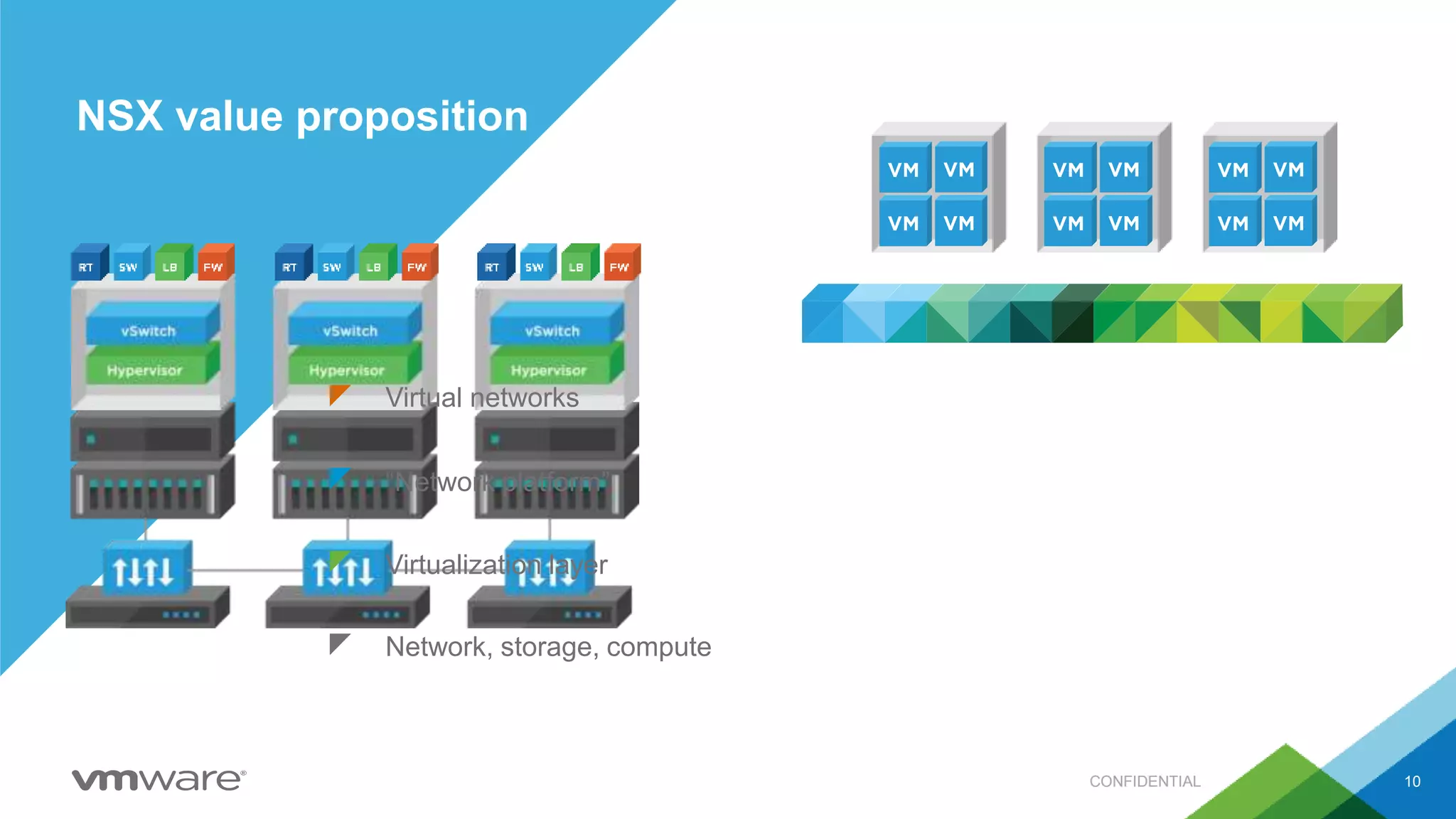
- VMware promotes a software-defined data center approach using technologies like NSX for network virtualization, vSphere for compute virtualization, and vSAN for storage virtualization.
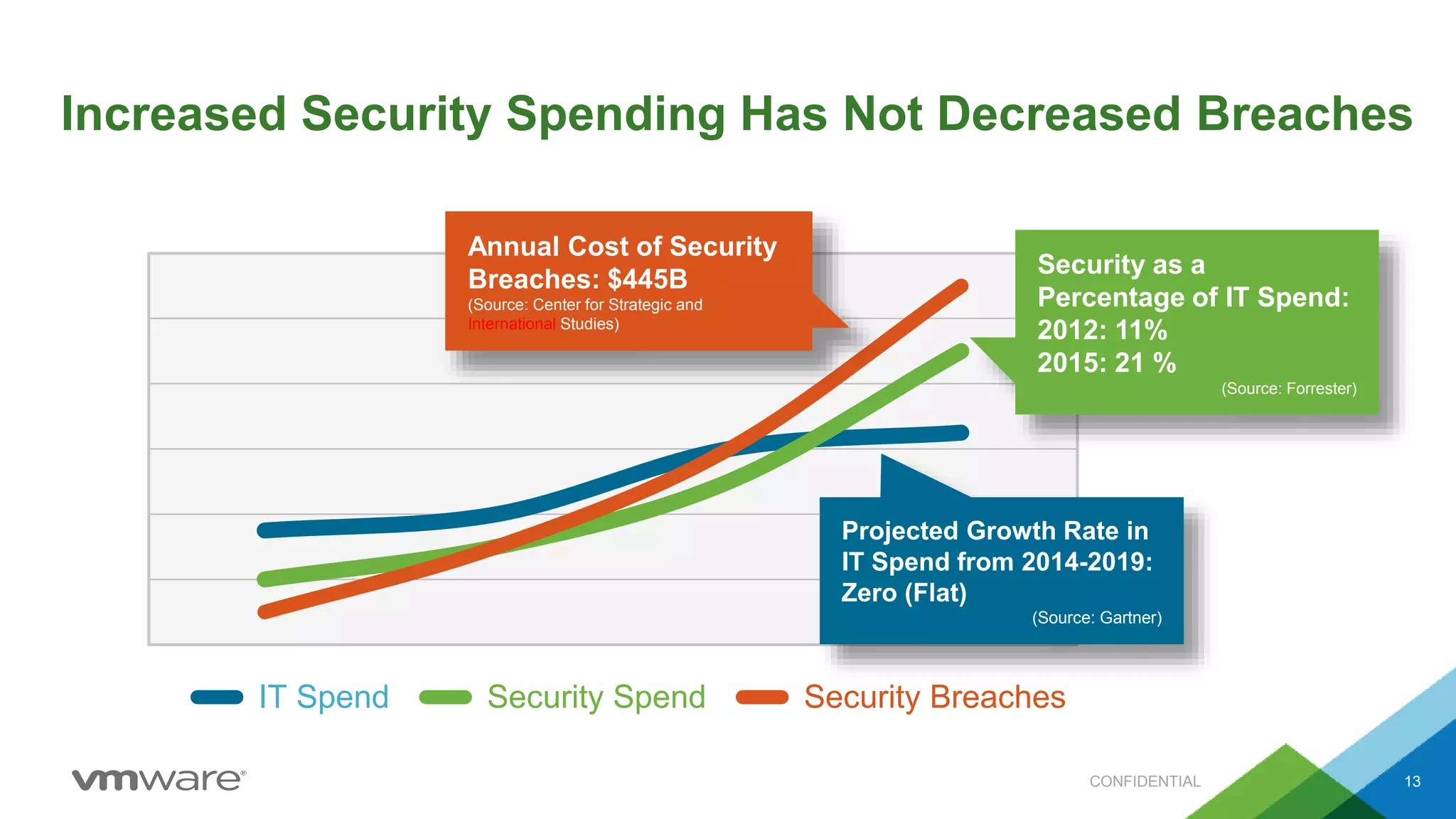
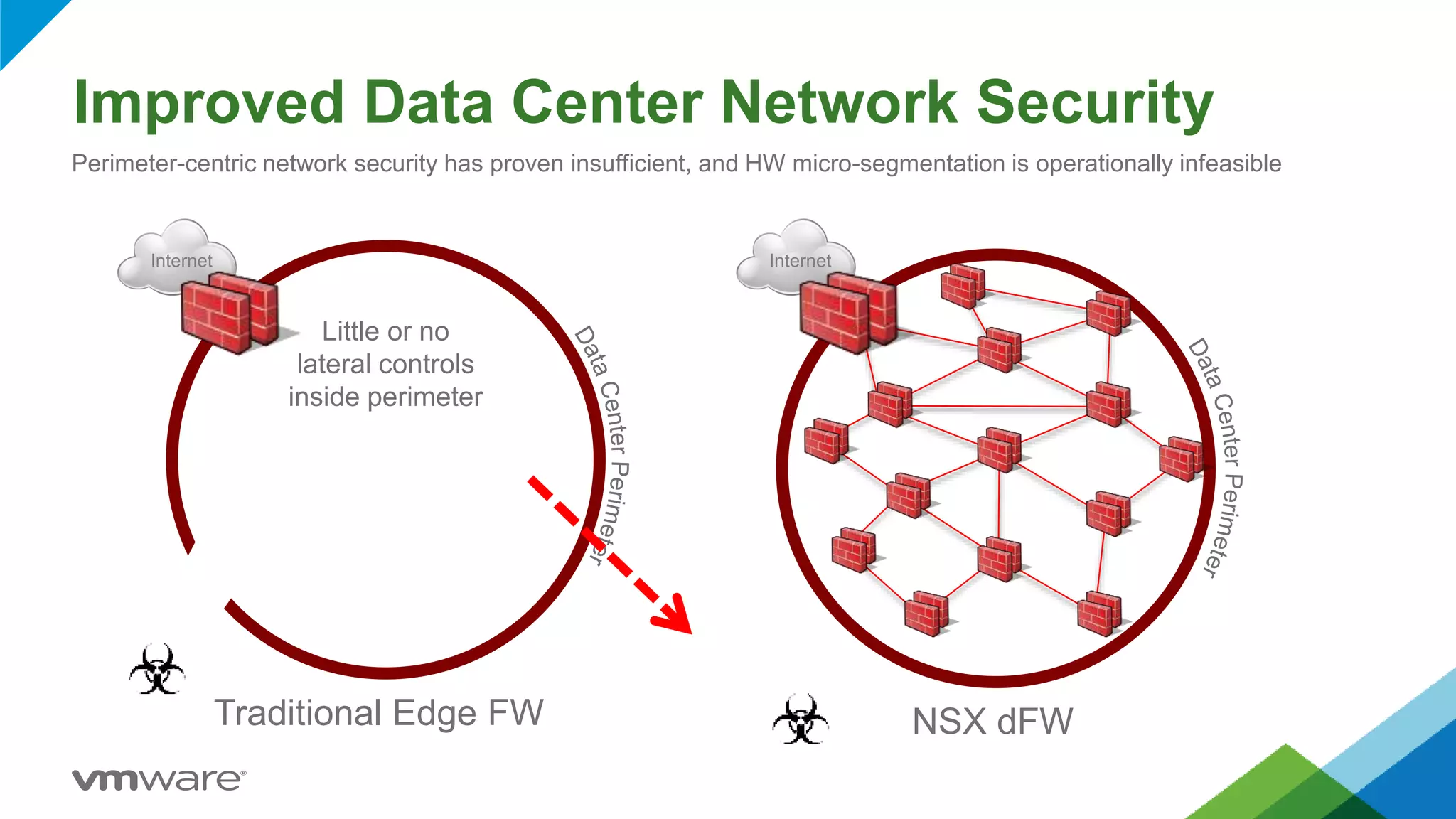
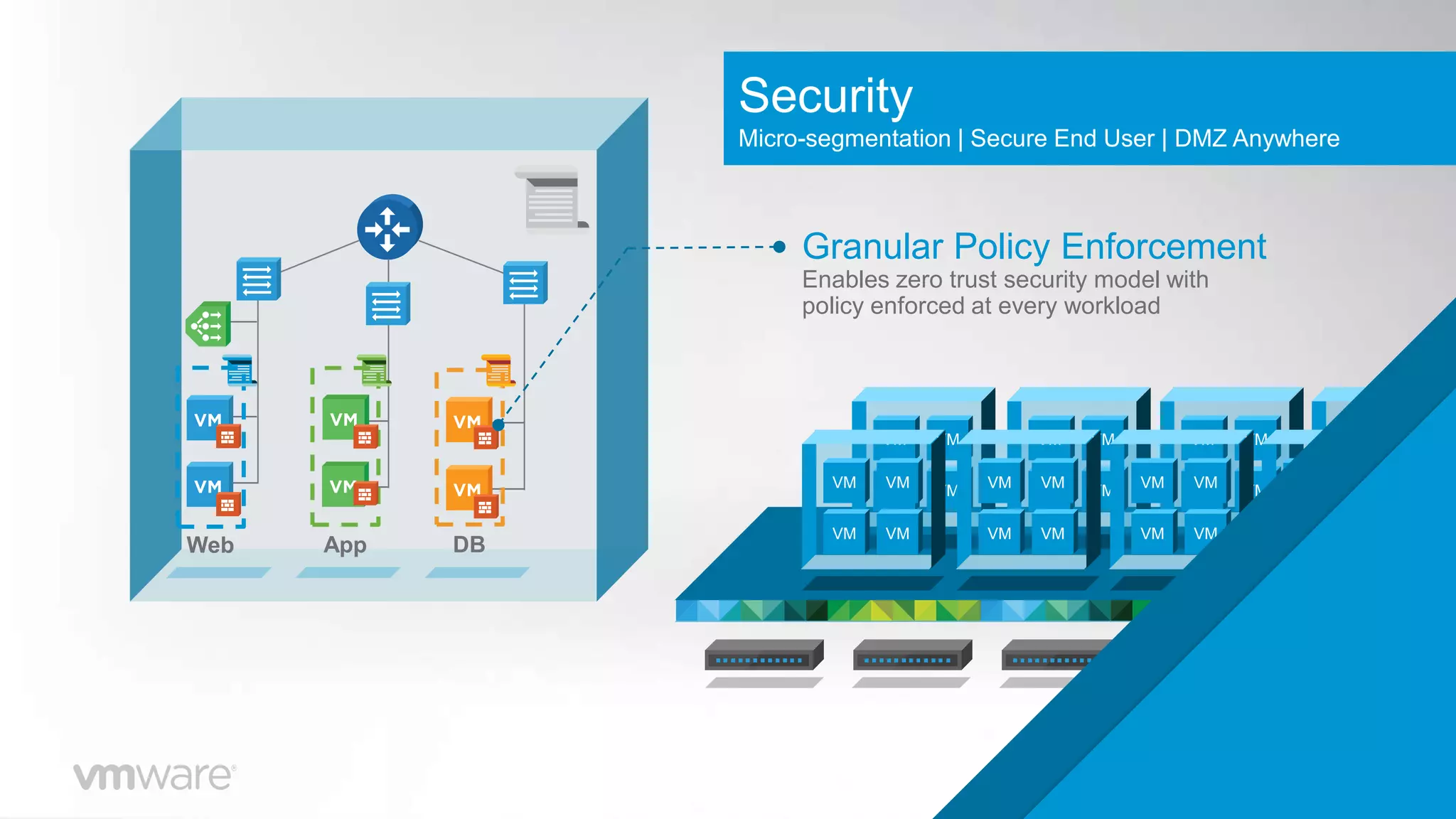
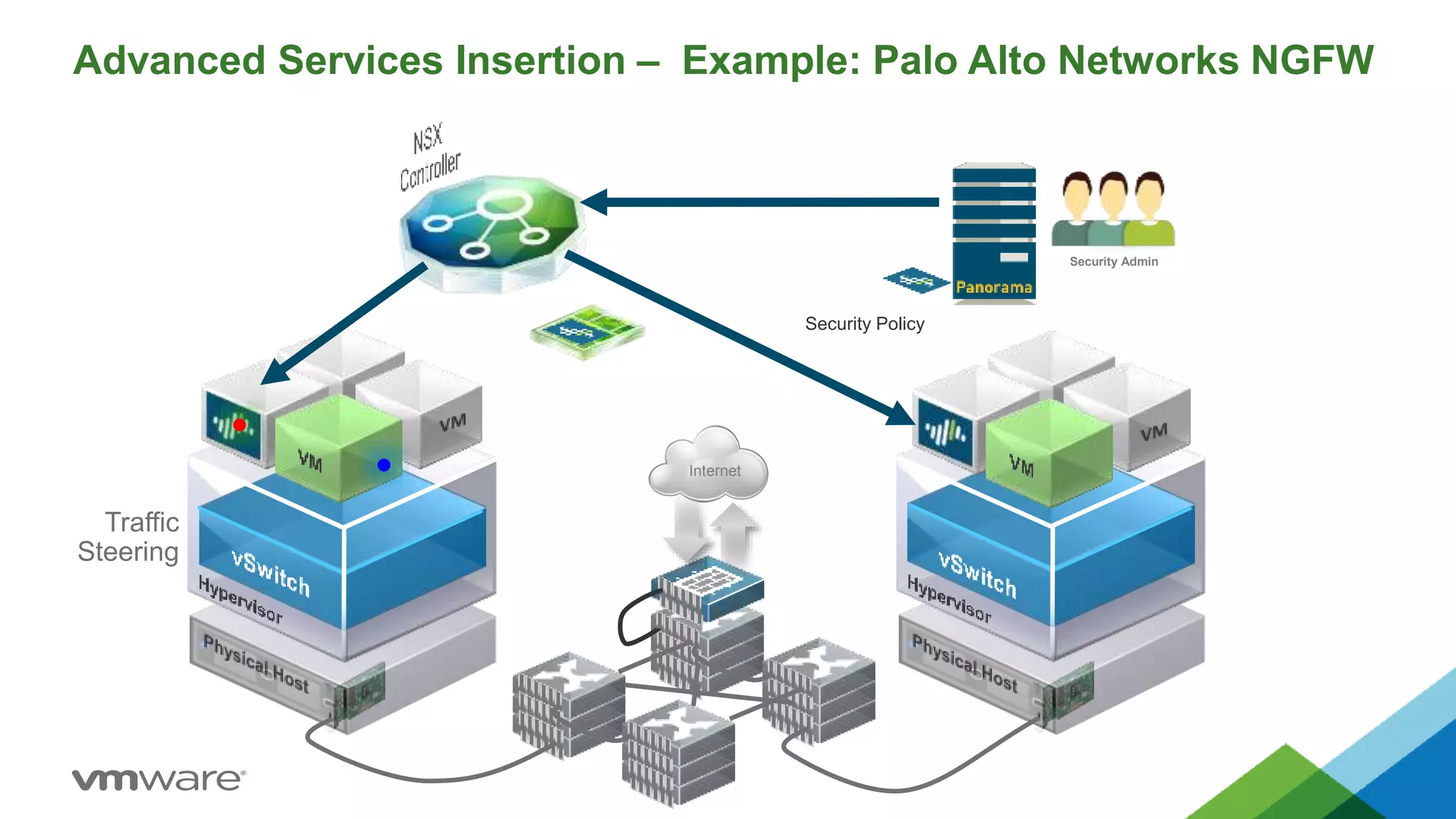
- NSX allows for micro-segmentation within the data center, enabling granular security policies to be applied at the workload level for improved security compared to traditional perimeter-based approaches.
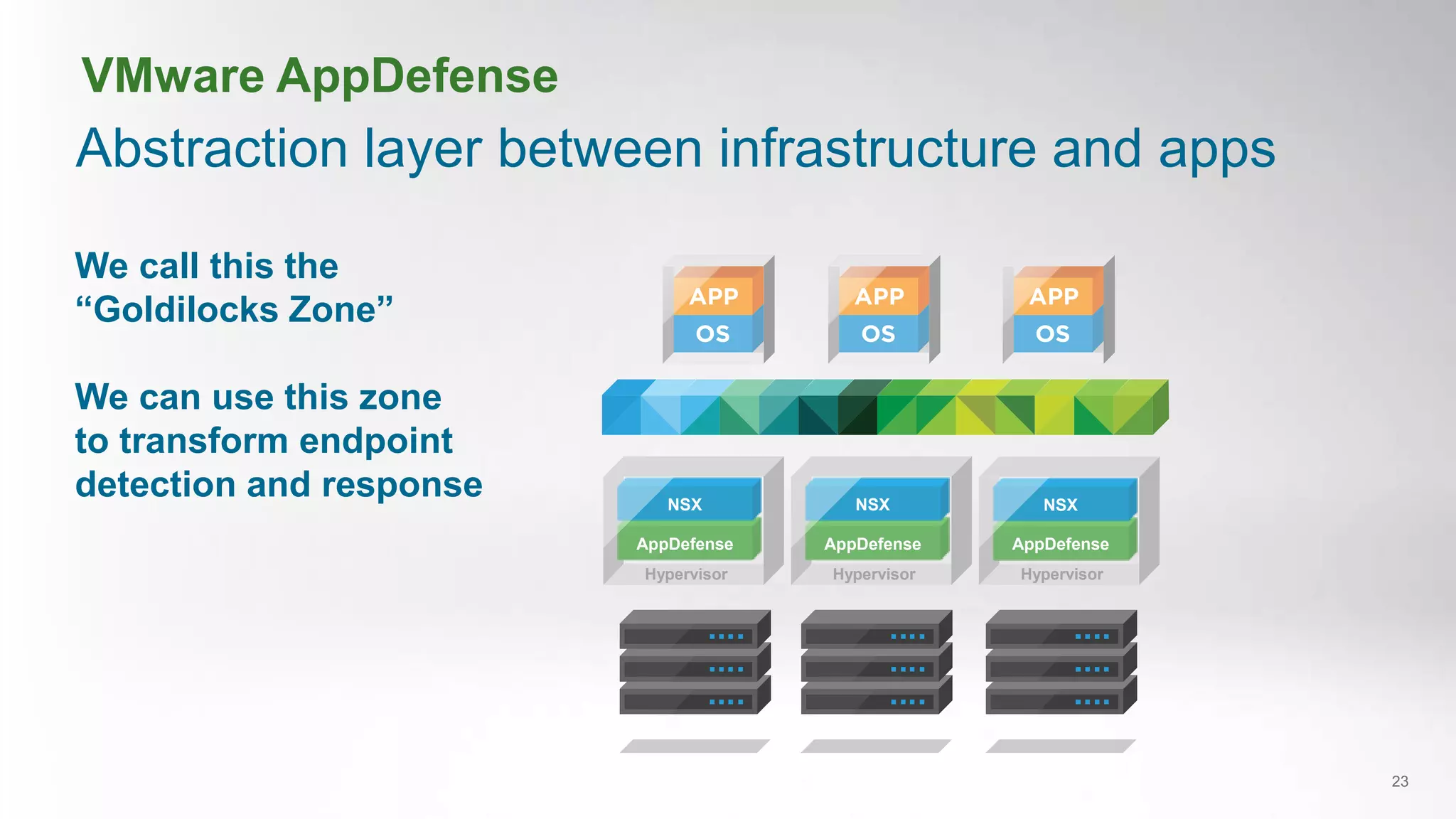
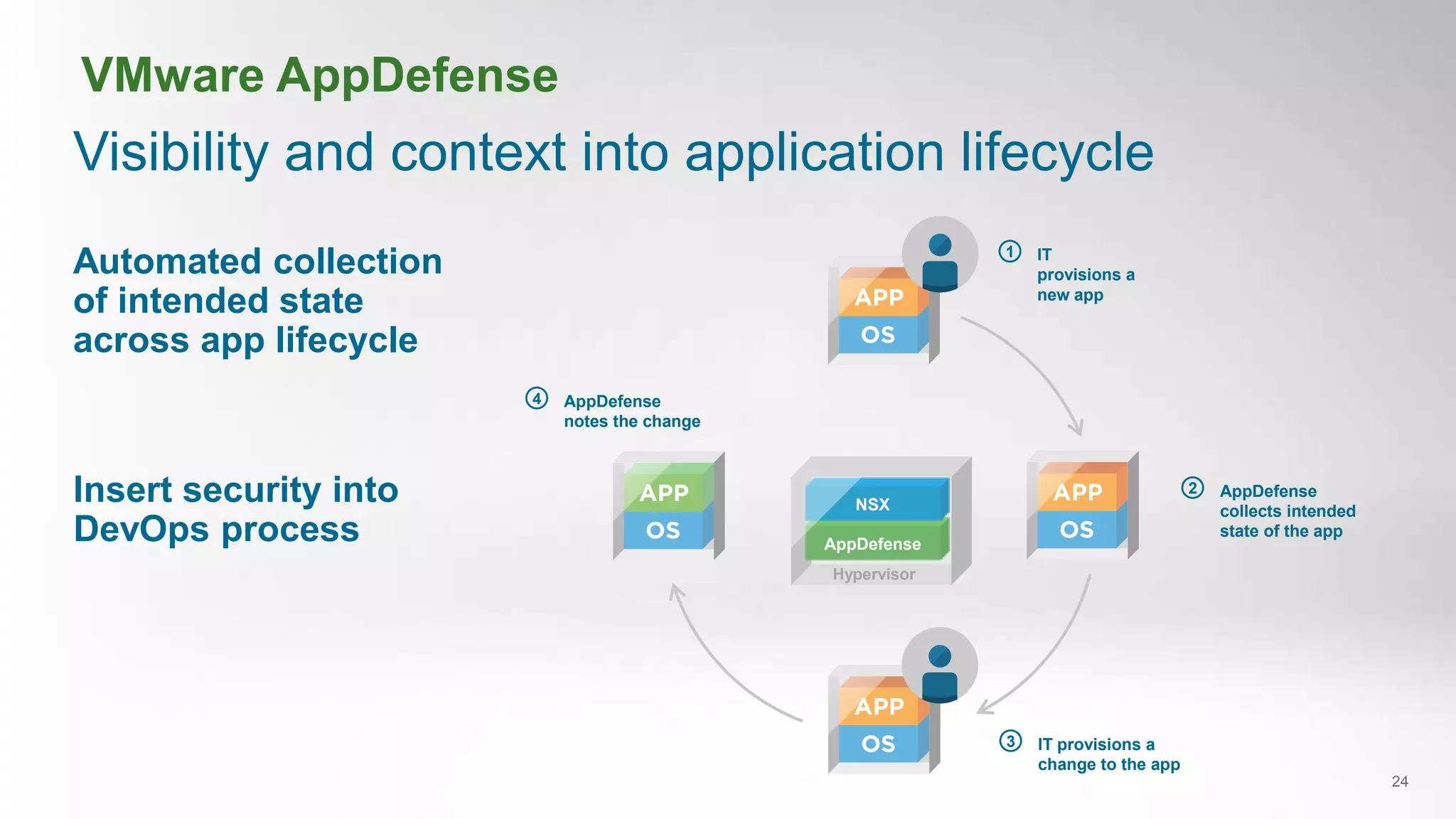
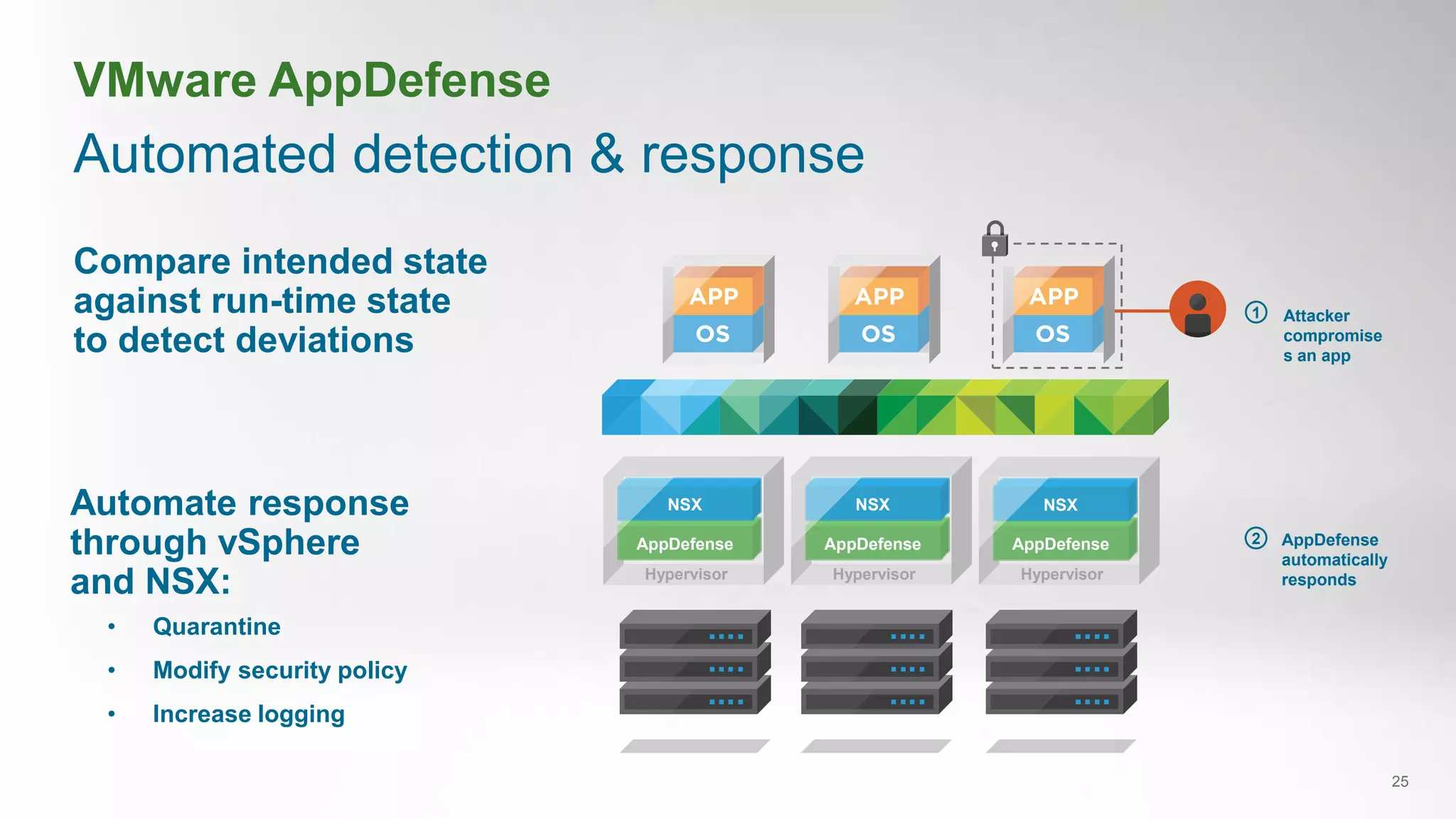
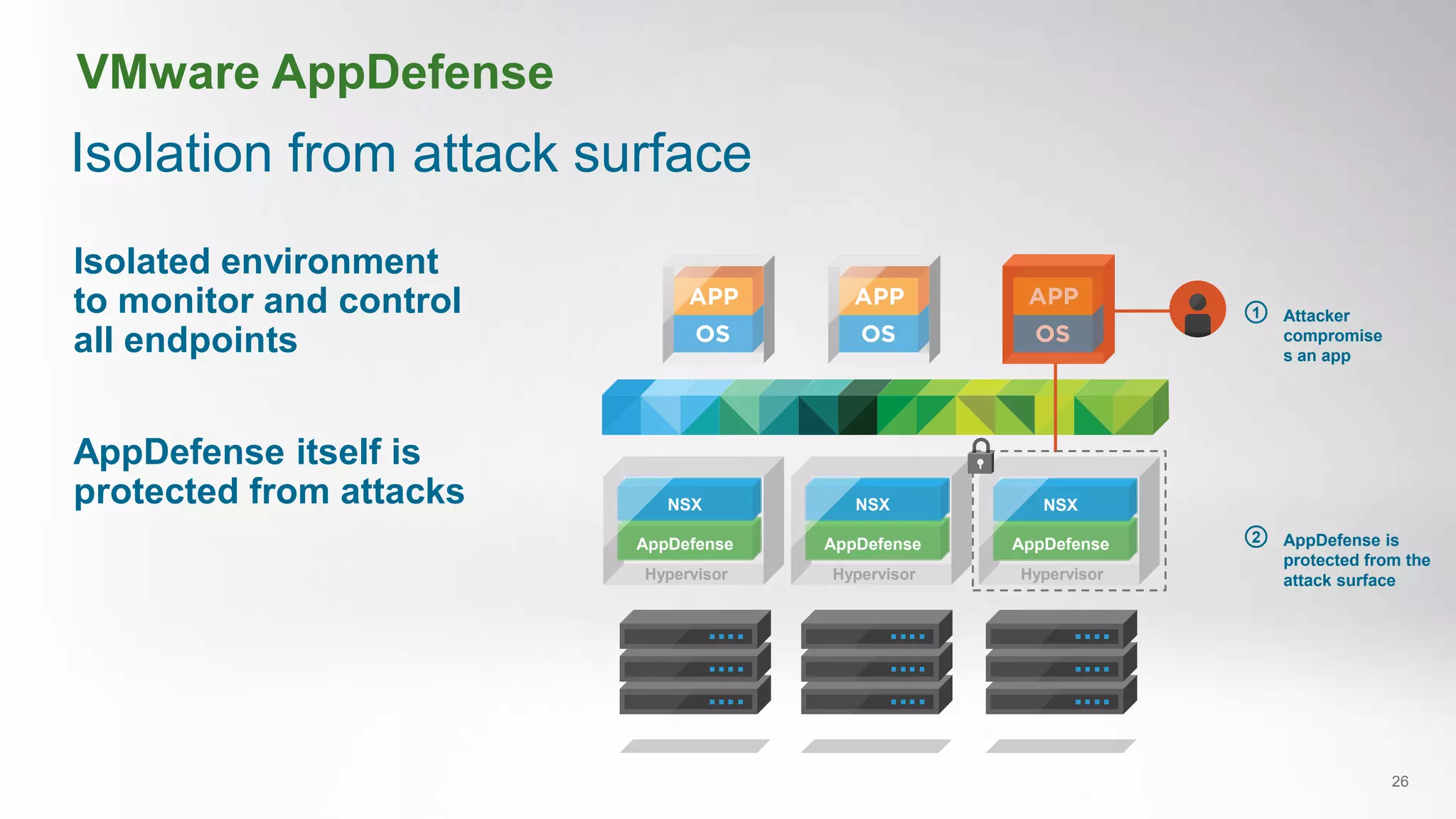
- VMware AppDefense provides visibility and control over the application lifecycle to detect deviations from intended application behavior and automate security responses.