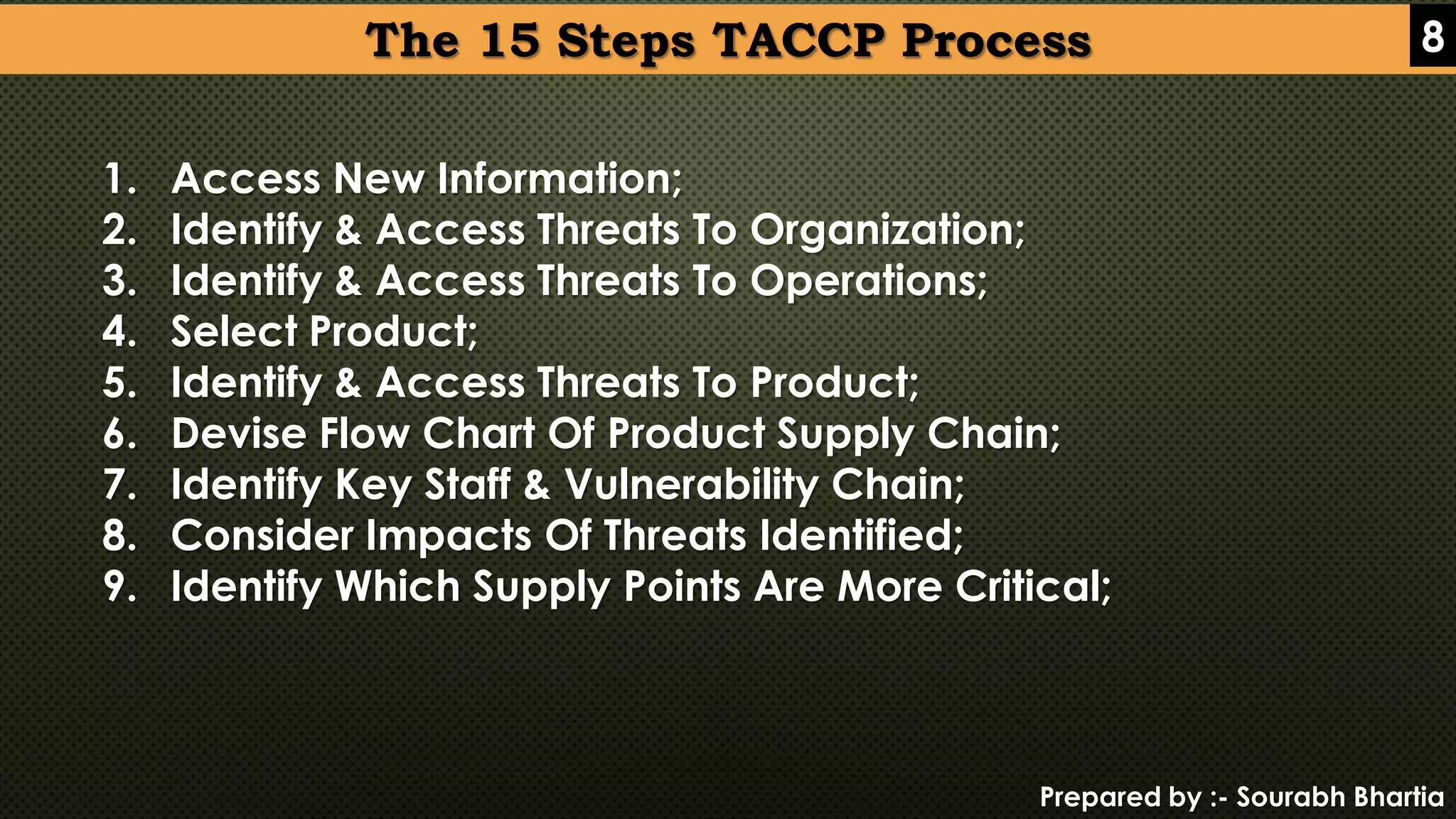
This document provides an overview of critical control points (CCP), Hazard Analysis and Critical Control Points (HACCP), Threat Assessment Critical Control Points (TACCP), and Vulnerability Assessment Critical Control Points (VACCP). CCP refers to key points in food processing that require control to prevent safety issues. HACCP focuses on food safety hazards while TACCP and VACCP aim to reduce risks of deliberate attacks and vulnerabilities like food fraud that could impact food quality. The document outlines the principles and processes for each system to identify and control potential risks at critical stages of food production.