Content based filtering
•Download as PPTX, PDF•
10 likes•8,561 views
This document discusses content-based recommendation techniques. It explains that content-based recommendation systems learn a user's preferences based on item attributes and characteristics to recommend similar items. It describes representing items and user profiles as vectors of keywords and computing similarity using metrics like cosine similarity. Finally, it briefly outlines probabilistic recommendation methods and linear classifiers for recommendations.
Report
Share
Report
Share
Recommended
Recommender systems: Content-based and collaborative filtering

Recommender systems: Content-based and collaborative filtering
An introduction to Recommender Systems

An introduction to Recommender Systems (2014-12-04) -- Lecture slides
Recommendation System Explained

What really are recommendations engines nowadays?
This presentation introduces the foundations of recommendation algorithms, and covers common approaches as well as some of the most advanced techniques. Although more focused on efficiency than theoretical properties, basics of matrix algebra and optimization-based machine learning are used through the presentation.
Table of Contents:
1. Collaborative Filtering
1.1 User-User
1.2 Item-Item
1.3 User-Item
* Matrix Factorization
* Stochastic Gradient Descent (SGD)
* Truncated Singular Value Decomposition (SVD)
* Alternating Least Square (ALS)
* Deep Learning
2. Content Extraction
* Item-Item Similarities
* Deep Content Extraction: NLP, CNN, LSTM
3. Hybrid Models
4. In Production
4.1 Problematics
4.2 Solutions
4.3 Tools
Recommender Systems

Recommender Systems represent one of the most widespread and impactful applications of predictive machine learning models.
Amazon, YouTube, Netflix, Facebook and many other companies generate an important fraction of their revenues thanks to their ability to model and accurately predict users ratings and preferences.
In this presentation we cover the following points:
→ introduction to recommender systems
→ working with explicit vs implicit feedback
→ content-based vs collaborative filtering approaches
→ user-based and item-item methods
→ machine learning and deep learning models
→ pros & cons of the methods: scalability, accuracy, explainability
Recommended
Recommender systems: Content-based and collaborative filtering

Recommender systems: Content-based and collaborative filtering
An introduction to Recommender Systems

An introduction to Recommender Systems (2014-12-04) -- Lecture slides
Recommendation System Explained

What really are recommendations engines nowadays?
This presentation introduces the foundations of recommendation algorithms, and covers common approaches as well as some of the most advanced techniques. Although more focused on efficiency than theoretical properties, basics of matrix algebra and optimization-based machine learning are used through the presentation.
Table of Contents:
1. Collaborative Filtering
1.1 User-User
1.2 Item-Item
1.3 User-Item
* Matrix Factorization
* Stochastic Gradient Descent (SGD)
* Truncated Singular Value Decomposition (SVD)
* Alternating Least Square (ALS)
* Deep Learning
2. Content Extraction
* Item-Item Similarities
* Deep Content Extraction: NLP, CNN, LSTM
3. Hybrid Models
4. In Production
4.1 Problematics
4.2 Solutions
4.3 Tools
Recommender Systems

Recommender Systems represent one of the most widespread and impactful applications of predictive machine learning models.
Amazon, YouTube, Netflix, Facebook and many other companies generate an important fraction of their revenues thanks to their ability to model and accurately predict users ratings and preferences.
In this presentation we cover the following points:
→ introduction to recommender systems
→ working with explicit vs implicit feedback
→ content-based vs collaborative filtering approaches
→ user-based and item-item methods
→ machine learning and deep learning models
→ pros & cons of the methods: scalability, accuracy, explainability
Recommender system

Overview of the Recommender system or recommendation system. RFM Concepts in brief. Collaborative Filtering in Item and User based. Content-based Recommendation also described.Product Association Recommender System. Stereotype Recommendation described with advantage and limitations.Customer Lifetime. Recommender System Analysis and Solving Cycle.
Recommender Systems

Part of the course "Algorithmic Methods of Data Science". Sapienza University of Rome, 2015.
http://aris.me/index.php/data-mining-ds-2015
Content based recommendation systems

Combining content based and collaborative filtering techniques and methods
Recommendation System

Recommendation System in the field of E-commerce, Online Streaming media, and in Our Day Today Life
Context-aware Recommendation: A Quick View

Very basic introduction about Context-aware Recommendation.
Recent advances in deep recommender systems

In this lecture, I will first cover the recent advances in neural recommender systems such as autoencoder-based and MLP-based recommender systems. Then, I will introduce the recent achievement for automatic playlist continuation in music recommendation.
A Hybrid Recommendation system

Analysis and details of the various recommendation systems.
Authored by: Arnaud De Bruyn
Recommender systems

Recommender systems are software tools and techniques providing suggestions for items to be of interest to a user. Recommender systems have proved in recent years to be a valuable means of helping Web users by providing useful and effective recommendations or suggestions.
Movie recommendation system using collaborative filtering system 

Movie recommendation system using collaborative filtering system
More info:+91 9082136766
Recommendation system

Recommendation systems are widely used in Web and Digital marketing.
Presentation includes basic concepts in recommendation.
Recommender Systems - A Review and Recent Research Trends

Recommender Systems - A Review and Recent Research Trends
[Final]collaborative filtering and recommender systems![[Final]collaborative filtering and recommender systems](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Final]collaborative filtering and recommender systems](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Collaborative filtering and recommender systems.
Movie recommendation project

Machine Learning based Hybrid Recommendation System
• Developed a Hybrid Movie Recommendation System using both Collaborative and Content-based methods
• Used linear regression framework for determining optimal feature weights from collaborative data
• Recommends movie with maximum similarity score of content-based data
Introduction to Recommendation Systems

1) Recommendation Systems in Practice
2) Types of Recommendation Systems
3) Building Data Pipeline for Video Recommendation System
How to build a recommender system?

By Coen Stevens, Lead Recommendations Engineer at Wakoopa. Presented at http://recked.org
Collaborative filtering

Types of recommender systems in information retrieval. Collaborative filtering is a very widely used method in recommendation systems. Content based filtering and collaborative filtering are two major approaches. Hybrid systems are now being employed to get better recommendations. One such method is content-boosted collaborative filtering.
Deep Learning for Personalized Search and Recommender Systems

Slide deck presented for a tutorial at KDD2017.
https://engineering.linkedin.com/data/publications/kdd-2017/deep-learning-tutorial
How to build a Recommender System

This presentation show the method to build a Recommender System with Collaborative FIltering method.
More Related Content
What's hot
Recommender system

Overview of the Recommender system or recommendation system. RFM Concepts in brief. Collaborative Filtering in Item and User based. Content-based Recommendation also described.Product Association Recommender System. Stereotype Recommendation described with advantage and limitations.Customer Lifetime. Recommender System Analysis and Solving Cycle.
Recommender Systems

Part of the course "Algorithmic Methods of Data Science". Sapienza University of Rome, 2015.
http://aris.me/index.php/data-mining-ds-2015
Content based recommendation systems

Combining content based and collaborative filtering techniques and methods
Recommendation System

Recommendation System in the field of E-commerce, Online Streaming media, and in Our Day Today Life
Context-aware Recommendation: A Quick View

Very basic introduction about Context-aware Recommendation.
Recent advances in deep recommender systems

In this lecture, I will first cover the recent advances in neural recommender systems such as autoencoder-based and MLP-based recommender systems. Then, I will introduce the recent achievement for automatic playlist continuation in music recommendation.
A Hybrid Recommendation system

Analysis and details of the various recommendation systems.
Authored by: Arnaud De Bruyn
Recommender systems

Recommender systems are software tools and techniques providing suggestions for items to be of interest to a user. Recommender systems have proved in recent years to be a valuable means of helping Web users by providing useful and effective recommendations or suggestions.
Movie recommendation system using collaborative filtering system 

Movie recommendation system using collaborative filtering system
More info:+91 9082136766
Recommendation system

Recommendation systems are widely used in Web and Digital marketing.
Presentation includes basic concepts in recommendation.
Recommender Systems - A Review and Recent Research Trends

Recommender Systems - A Review and Recent Research Trends
[Final]collaborative filtering and recommender systems![[Final]collaborative filtering and recommender systems](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Final]collaborative filtering and recommender systems](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Collaborative filtering and recommender systems.
Movie recommendation project

Machine Learning based Hybrid Recommendation System
• Developed a Hybrid Movie Recommendation System using both Collaborative and Content-based methods
• Used linear regression framework for determining optimal feature weights from collaborative data
• Recommends movie with maximum similarity score of content-based data
Introduction to Recommendation Systems

1) Recommendation Systems in Practice
2) Types of Recommendation Systems
3) Building Data Pipeline for Video Recommendation System
How to build a recommender system?

By Coen Stevens, Lead Recommendations Engineer at Wakoopa. Presented at http://recked.org
Collaborative filtering

Types of recommender systems in information retrieval. Collaborative filtering is a very widely used method in recommendation systems. Content based filtering and collaborative filtering are two major approaches. Hybrid systems are now being employed to get better recommendations. One such method is content-boosted collaborative filtering.
Deep Learning for Personalized Search and Recommender Systems

Slide deck presented for a tutorial at KDD2017.
https://engineering.linkedin.com/data/publications/kdd-2017/deep-learning-tutorial
What's hot (20)
Movie recommendation system using collaborative filtering system 

Movie recommendation system using collaborative filtering system
Recommender Systems - A Review and Recent Research Trends

Recommender Systems - A Review and Recent Research Trends
[Final]collaborative filtering and recommender systems![[Final]collaborative filtering and recommender systems](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Final]collaborative filtering and recommender systems](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Final]collaborative filtering and recommender systems
Deep Learning for Personalized Search and Recommender Systems

Deep Learning for Personalized Search and Recommender Systems
Viewers also liked
How to build a Recommender System

This presentation show the method to build a Recommender System with Collaborative FIltering method.
How to Build Recommender System with Content based Filtering

How to build recommender system. Content based filtering method for recommender system. Feature weighting and feature measure function.
Rekomendujemy - Szybkie wprowadzenie do systemów rekomendacji oraz trochę wie...

Rekomendujemy - Szybkie wprowadzenie do systemów rekomendacji oraz trochę wie...Bartlomiej Twardowski
W zalewie informacji odnalezienie tych które nas rzeczywiście interesują staje się bardzo trudne. Wspomagają nas w tym systemy IR, np. w postaci wyszukiwarek internetowych. O krok dalej idą systemy rekomendacji, próbując odgadnąć preferencje użytkownika i zaoferować najlepiej spersonalizowane treści automatycznie.
Podejście do problemu rekomendacji użytkownikowi najbardziej dopasowanych informacji zmieniało się w czasie. Aktualnie do wyboru mamy szereg gotowych do zastosowania metod: od prostego opisu podobieństwa użytkowników, kończąc na złożonych modelach trenowanych przez metody ML. Trudność zaczyna stanowić poprawne zrozumienie problemu/domeny, odpowiednie dobranie metody rekomendacji oraz sposób jej pomiaru.
Na prezentacji zostanie przedstawione krótkie wprowadzenie do tematyki systemów rekomendacji. Omówione zostaną metod rekomendacji oraz sposoby ich ewaluacja. Zaprezentowane zostanie podejście do problemu jako "ranking top-N" najlepszych ofert. Całość uzupełniona zostanie doświadczeniami i ciekawymi problemami z implementacji platformy rekomendacyjnej dla największego serwisu e-commerce w Polsce.Collaborative filtering for recommendation systems in Python, Nicolas Hug

Collaborative filtering for recommendation systems in Python, Nicolas HugPôle Systematic Paris-Region
PyParis 2017
http://pyparis.org Viewers also liked (6)
How to Build Recommender System with Content based Filtering

How to Build Recommender System with Content based Filtering
Rekomendujemy - Szybkie wprowadzenie do systemów rekomendacji oraz trochę wie...

Rekomendujemy - Szybkie wprowadzenie do systemów rekomendacji oraz trochę wie...
Collaborative filtering for recommendation systems in Python, Nicolas Hug

Collaborative filtering for recommendation systems in Python, Nicolas Hug
Similar to Content based filtering
Book Recommendation Engine

This is a book recommendation engine using item based and user based collaborative filtering using GoodReads ratings.
Recommenders.ppt

Data Analyst, Data Scientist, and Data Engineer are three distinct roles within the field of data and analytics, each with its own set of responsibilities and skill requirements. Here's a brief overview of each role:
Digital Image Processing.pptx

Introduction:
Introduction to basic techniques. x
• Quantitative descriptors (e.g. area, length…).
• Patterns arranged in vectors.
– Structural techniques.
• Qualitative descriptors (relational descriptors for repetitive structures, e.g. staircase).
• Patterns arranged in strings or trees.
• Central idea: Learning from sample patterns
Scalable Recommendation Algorithms with LSH

- Scalable recommendation algorithm based on Locality Sensitive Hashing (LSH) and Collaborative Filtering.
- Distributed implementation of LSH with Apache Spark.
[系列活動] 人工智慧與機器學習在推薦系統上的應用![[系列活動] 人工智慧與機器學習在推薦系統上的應用](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[系列活動] 人工智慧與機器學習在推薦系統上的應用](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
本課程特別邀請到臺大資工系林守德教授,利用六小時的課程簡介人工智慧的歷史演進以及其與機器學習的關聯,同時也會介紹在實務上如何訓練好的機器學習模型,及如何應用相關技術建立智慧推薦系統。本課程由四個部分組成,包括人工智慧與機器學習簡介、內容為本推薦系統、協同過濾系統與進階推薦系統。
Models for Information Retrieval and Recommendation

Online information services personalize the user experience by applying recommendation systems to identify the information that is most relevant to the user. The question how to estimate relevance has been the core concept in the field of information retrieval for many years. Not so surprisingly then, it turns out that the methods used in online recommendation systems are closely related to the models developed in the information retrieval area. In this lecture, I present a unified approach to information retrieval and collaborative filtering, and demonstrate how this let’s us turn a standard information retrieval system into a state-of-the-art recommendation system.
Textual Document Categorization using Bigram Maximum Likelihood and KNN

In recent year’s text mining has evolved as a vast field of research in machine learning and artificial intelligence. Text Mining is a difficult task to conduct with an unstructured data format. This research work focuses on the classification of textual data of three different literature books. The collection of data is extracted from books entitled: Oliver Twist, Don Quixote, Pride and Prejudge. We used two different algorithms: KNN and Bigram based Maximum Likelihood for the mentioned purpose and the evaluation of accuracy is done using the confusion matrix. The results suggest that the text mining using bigram based maximum likelihood logic performs well.
Similar to Content based filtering (20)
Publish or Perish: Towards a Ranking of Scientists using Bibliographic Data ...

Publish or Perish: Towards a Ranking of Scientists using Bibliographic Data ...
Models for Information Retrieval and Recommendation

Models for Information Retrieval and Recommendation
Textual Document Categorization using Bigram Maximum Likelihood and KNN

Textual Document Categorization using Bigram Maximum Likelihood and KNN
Recently uploaded
Mind map of terminologies used in context of Generative AI

Mind map of common terms used in context of Generative AI.
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
20240607 QFM018 Elixir Reading List May 2024

Everything I found interesting about the Elixir programming ecosystem in May 2024
How to Get CNIC Information System with Paksim Ga.pptx

Pakdata Cf is a groundbreaking system designed to streamline and facilitate access to CNIC information. This innovative platform leverages advanced technology to provide users with efficient and secure access to their CNIC details.
zkStudyClub - Reef: Fast Succinct Non-Interactive Zero-Knowledge Regex Proofs

This paper presents Reef, a system for generating publicly verifiable succinct non-interactive zero-knowledge proofs that a committed document matches or does not match a regular expression. We describe applications such as proving the strength of passwords, the provenance of email despite redactions, the validity of oblivious DNS queries, and the existence of mutations in DNA. Reef supports the Perl Compatible Regular Expression syntax, including wildcards, alternation, ranges, capture groups, Kleene star, negations, and lookarounds. Reef introduces a new type of automata, Skipping Alternating Finite Automata (SAFA), that skips irrelevant parts of a document when producing proofs without undermining soundness, and instantiates SAFA with a lookup argument. Our experimental evaluation confirms that Reef can generate proofs for documents with 32M characters; the proofs are small and cheap to verify (under a second).
Paper: https://eprint.iacr.org/2023/1886
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

Leonard Jayamohan, Partner & Generative AI Lead, Deloitte
This keynote will reveal how Deloitte leverages Neo4j’s graph power for groundbreaking digital twin solutions, achieving a staggering 100x performance boost. Discover the essential role knowledge graphs play in successful generative AI implementations. Plus, get an exclusive look at an innovative Neo4j + Generative AI solution Deloitte is developing in-house.
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024

Maruthi Prithivirajan, Head of ASEAN & IN Solution Architecture, Neo4j
Get an inside look at the latest Neo4j innovations that enable relationship-driven intelligence at scale. Learn more about the newest cloud integrations and product enhancements that make Neo4j an essential choice for developers building apps with interconnected data and generative AI.
UiPath Test Automation using UiPath Test Suite series, part 6

Welcome to UiPath Test Automation using UiPath Test Suite series part 6. In this session, we will cover Test Automation with generative AI and Open AI.
UiPath Test Automation with generative AI and Open AI webinar offers an in-depth exploration of leveraging cutting-edge technologies for test automation within the UiPath platform. Attendees will delve into the integration of generative AI, a test automation solution, with Open AI advanced natural language processing capabilities.
Throughout the session, participants will discover how this synergy empowers testers to automate repetitive tasks, enhance testing accuracy, and expedite the software testing life cycle. Topics covered include the seamless integration process, practical use cases, and the benefits of harnessing AI-driven automation for UiPath testing initiatives. By attending this webinar, testers, and automation professionals can gain valuable insights into harnessing the power of AI to optimize their test automation workflows within the UiPath ecosystem, ultimately driving efficiency and quality in software development processes.
What will you get from this session?
1. Insights into integrating generative AI.
2. Understanding how this integration enhances test automation within the UiPath platform
3. Practical demonstrations
4. Exploration of real-world use cases illustrating the benefits of AI-driven test automation for UiPath
Topics covered:
What is generative AI
Test Automation with generative AI and Open AI.
UiPath integration with generative AI
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

ここ3000字までしか入らないけどタイトルの方がたくさん文字入ると思います。
GridMate - End to end testing is a critical piece to ensure quality and avoid...

End to end testing is a critical piece to ensure quality and avoid regressions. In this session, we share our journey building an E2E testing pipeline for GridMate components (LWC and Aura) using Cypress, JSForce, FakerJS…
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
Large Language Model (LLM) and it’s Geospatial Applications

Large Language Model (LLM) and it’s Geospatial Applications.
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Recently uploaded (20)
Mind map of terminologies used in context of Generative AI

Mind map of terminologies used in context of Generative AI
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...
How to Get CNIC Information System with Paksim Ga.pptx

How to Get CNIC Information System with Paksim Ga.pptx
Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx

Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx
zkStudyClub - Reef: Fast Succinct Non-Interactive Zero-Knowledge Regex Proofs

zkStudyClub - Reef: Fast Succinct Non-Interactive Zero-Knowledge Regex Proofs
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024

GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024
UiPath Test Automation using UiPath Test Suite series, part 6

UiPath Test Automation using UiPath Test Suite series, part 6
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...
GridMate - End to end testing is a critical piece to ensure quality and avoid...

GridMate - End to end testing is a critical piece to ensure quality and avoid...
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
Large Language Model (LLM) and it’s Geospatial Applications

Large Language Model (LLM) and it’s Geospatial Applications
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
Content based filtering
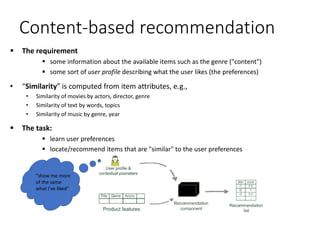
- 1. Content-based recommendation The requirement some information about the available items such as the genre ("content") some sort of user profile describing what the user likes (the preferences) • “Similarity” is computed from item attributes, e.g., • Similarity of movies by actors, director, genre • Similarity of text by words, topics • Similarity of music by genre, year The task: learn user preferences locate/recommend items that are "similar" to the user preferences "show me more of the same what I've liked"
- 2. • Most Content Based-recommendation techniques were applied to recommending text documents. • Like web pages or newsgroup messages for example. • Content of items can also be represented as text documents. • With textual descriptions of their basic characteristics. • Structured: Each item is described by the same set of attributes Title Genre Author Type Price Keywords The Night of the Gun Memoir David Carr Paperback 29.90 Press and journalism, drug addiction, personal memoirs, New York The Lace Reader Fiction, Mystery Brunonia Barry Hardcover 49.90 American contemporary fiction, detective, historical Into the Fire Romance, Suspense Suzanne Brockmann Hardcover 45.90 American fiction, murder, neo-Nazism
- 3. Item representation Content representation and item similarities • Approach • Compute the similarity of an unseen item with the user profile based on the keyword overlap (e.g. using the Dice coefficient) • Or use and combine multiple metrics Title Genre Author Type Price Keywords The Night of the Gun Memoir David Carr Paperback 29.90 Press and journalism, drug addiction, personal memoirs, New York The Lace Reader Fiction, Mystery Brunonia Barry Hardcover 49.90 American contemporary fiction, detective, historical Into the Fire Romance, Suspense Suzanne Brockmann Hardcover 45.90 American fiction, murder, neo- Nazism User profile Title Genre Author Type Price Keywords … Fiction Brunonia, Barry, Ken Follett Paperback 25.65 Detective, murder, New York 𝟐 × 𝒌𝒆𝒚𝒘𝒐𝒓𝒅𝒔 𝒃𝒊 ∩ 𝒌𝒆𝒚𝒘𝒐𝒓𝒅𝒔 𝒃𝒋 𝒌𝒆𝒚𝒘𝒐𝒓𝒅𝒔 𝒃𝒊 + 𝒌𝒆𝒚𝒘𝒐𝒓𝒅𝒔 𝒃𝒋 𝑘𝑒𝑦𝑤𝑜𝑟𝑑𝑠 𝑏𝑗 describes Book 𝑏𝑗 with a set of keywords
- 4. Term-Frequency - Inverse Document Frequency (𝑻𝑭 − 𝑰𝑫𝑭) • Simple keyword representation has its problems • in particular when automatically extracted as • not every word has similar importance • longer documents have a higher chance to have an overlap with the user profile • Standard measure: TF-IDF • Encodes text documents in multi-dimensional Euclidian space • weighted term vector • TF: Measures, how often a term appears (density in a document) • assuming that important terms appear more often • normalization has to be done in order to take document length into account • IDF: Aims to reduce the weight of terms that appear in all documents
- 5. • Given a keyword 𝑖 and a document 𝑗 • 𝑇𝐹 𝑖, 𝑗 • term frequency of keyword 𝑖 in document 𝑗 • 𝐼𝐷𝐹 𝑖 • inverse document frequency calculated as 𝑰𝑫𝑭 𝒊 = 𝒍𝒐𝒈 𝑵 𝒏 𝒊 • 𝑁 : number of all recommendable documents • 𝑛 𝑖 : number of documents from 𝑁 in which keyword 𝑖 appears • 𝑇𝐹 − 𝐼𝐷𝐹 • is calculated as: 𝑻𝑭-𝑰𝑫𝑭 𝒊, 𝒋 = 𝑻𝑭 𝒊, 𝒋 ∗ 𝑰𝑫𝑭 𝒊 Term-Frequency - Inverse Document Frequency (𝑻𝑭 − 𝑰𝑫𝑭)
- 6. Cosine similarity • Usual similarity metric to compare vectors: Cosine similarity (angle) • Cosine similarity is calculated based on the angle between the vectors • 𝑠𝑖𝑚 𝑎, 𝑏 = 𝑎∙𝑏 𝑎 ∗ 𝑏 • Adjusted cosine similarity • take average user ratings into account ( 𝑟𝑢), transform the original ratings • U: set of users who have rated both items a and b • 𝑠𝑖𝑚 𝑎, 𝑏 = 𝑢∈𝑈 𝑟 𝑢,𝑎− 𝑟 𝑢 𝑟 𝑢,𝑏− 𝑟 𝑢 𝑢∈𝑈 𝑟 𝑢,𝑎− 𝑟 𝑢 2 𝑢∈𝑈 𝑟 𝑢,𝑏− 𝑟 𝑢 2
- 7. An example for computing cosine similarity of annotations To calculate cosine similarity between two texts t1 and t2, they are transformed in vectors as shown in the Table
- 9. Calculation of probabilities in simplistic approach Item1 Item2 Item3 Item4 Item5 Alice 1 3 3 2 ? User1 2 4 2 2 4 User2 1 3 3 5 1 User3 4 5 2 3 3 User4 1 1 5 2 1 X = (Item1 =1, Item2=3, Item3= … )
- 10. Item1 Item5 Alice 2 ? User1 1 2 Idea of Slope One predictors is simple and is based on a popularity differential between items for users Example: p(Alice, Item5) = Basic scheme: Take the average of these differences of the co-ratings to make the prediction In general: Find a function of the form f(x) = x + b Slope One predictors - 2 + ( 2 - 1 ) = 3
- 11. Relevant Nonrelevant • Most learning methods aim to find coefficients of a linear model • A simplified classifier with only two dimensions can be represented by a line Other linear classifiers: – Naive Bayes classifier, Rocchio method, Windrow-Hoff algorithm, Support vector machines Linear classifiers The line has the form 𝒘 𝟏 𝒙 𝟏 + 𝒘 𝟐 𝒙 𝟐 = 𝒃 – 𝑥1 and 𝑥2 correspond to the vector representation of a document (using e.g. TF-IDF weights) – 𝑤1, 𝑤2 and 𝑏 are parameters to be learned – Classification of a document based on checking 𝑤1 𝑥1 + 𝑤2 𝑥2 > 𝑏 In n-dimensional space the classification function is 𝑤 𝑇 𝑥 = 𝑏
- 12. – Mean Absolute Error (MAE) computes the deviation between predicted ratings and actual ratings – Root Mean Square Error (RMSE) is similar to MAE, but places more emphasis on larger deviation Metrics Measure Error rate
- 13. Next … • Hybrid recommendation systems • More theories • Boolean and Vector Space Retrieval Models • Clustering • Data mining • And so on
