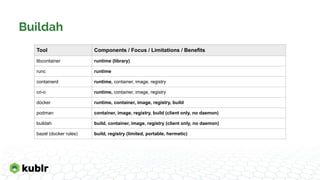
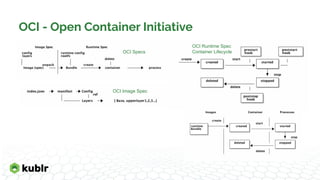
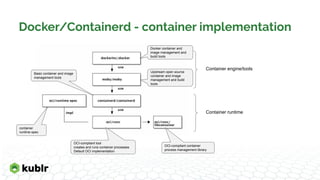
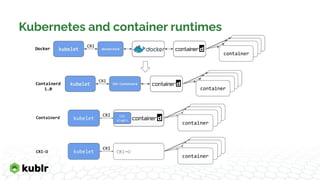
The document discusses the evolution of container runtimes and tooling, starting from Docker's release in 2013 and leading to the establishment of the Open Container Initiative (OCI). It offers a detailed analysis of various container management tools, their specifications, and the broader landscape of container orchestration and runtimes. It also highlights specific tools and commands used in container management, including Docker, containerd, and Podman, along with resources for further reference.






![Docker tools
docker container ps -a
docker run --name cnt1 -it my-img:v1.0
docker stop cnt1
docker kill cnt1
docker rm cnt1
docker image build –-tag my-img:v1.0 .
docker image ls
docker image tag my-img:v1.0 my-repo.com/my-img:v1.0
docker image push my-repo.com/my-img:v1.0
docker image pull kublr/kublr:1.22.2
FROM ubuntu:20.04
ADD file1 file2
RUN apt install curl
ENTRYPOINT ["/bin/bash"]](https://image.slidesharecdn.com/2022-03containerruntimesandtooling-220309191043/85/Container-Runtimes-and-Tooling-10-320.jpg)

![Podman
podman container ps -a
podman run --name cnt1 -it my-img:v1.0
podman stop cnt1
podman kill cnt1
podman rm cnt1
# podman ~ docker
# uses buildah
podman image build –-tag my-img:v1.0 .
podman image ls
podman image tag my-img:v1.0 my-repo.com/my-img:v1.0
podman image push my-repo.com/my-img:v1.0
podman image pull kublr/kublr:1.22.2
# Containerfile/Dockerfile
FROM ubuntu:20.04
ADD file1 file2
RUN apt install curl
ENTRYPOINT ["/bin/bash"]](https://image.slidesharecdn.com/2022-03containerruntimesandtooling-220309191043/85/Container-Runtimes-and-Tooling-12-320.jpg)
![Buildah
container=$(buildah from fedora)
buildah run $container bash
buildah run $container -- dnf -y install java
buildah build -f Dockerfile -t fedora-httpd .
# Containerfile/Dockerfile
FROM ubuntu:20.04
ADD file1 file2
RUN apt install curl
ENTRYPOINT ["/bin/bash"]](https://image.slidesharecdn.com/2022-03containerruntimesandtooling-220309191043/85/Container-Runtimes-and-Tooling-13-320.jpg)
![Bazel
# WORKSPACE
container_pull(
name = "kublr_alpine",
registry = "cr.kublr.com",
repository = "kublr/alpine",
# tag = "3.14.2-6",
digest = "sha256:5363....f164",
)
# BUILD.bazel
pkg_tar(
name = "image-tar-svc",
files = {":svc"},
mode = "0555",
package_dir = "/opt",
strip_prefix = strip_prefix.from_pkg(),
)
container_image(
name = "image",
base = "@kublr_alpine//image",
entrypoint = ["/opt/my-svc", "--port", "8080"],
layers = [":image-layer-swagger"],
ports = ["8080"],
tars = [":image-tar-svc"],
workdir = "/opt",
)](https://image.slidesharecdn.com/2022-03containerruntimesandtooling-220309191043/85/Container-Runtimes-and-Tooling-14-320.jpg)