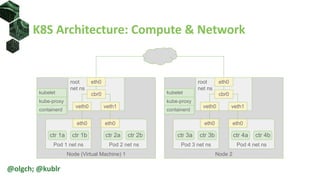
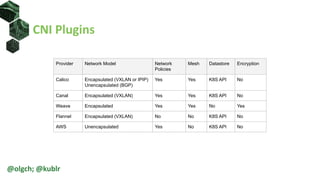
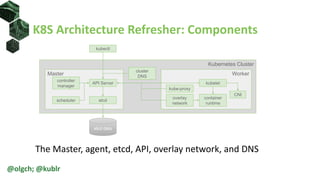
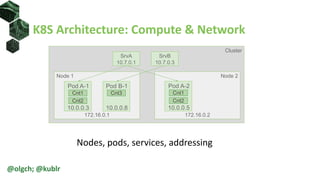
The document provides an overview of Kubernetes networking, including its architecture, network policies, and the use of custom clusters for infrastructure management. It details the roles of various components within a Kubernetes cluster, such as nodes, pods, and services, and describes how network policies can control traffic. Additionally, examples of network policies and test applications are included, highlighting their configurations and operational aspects.




![Network Policy Anatomy
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
namespace: default
spec:
podSelector: { ... }
policyTypes:
- Ingress
- Egress
ingress:
- { ... } # ingress rule 1
...
- { ... } # ingress rule N
egress:
- { ... } # egress rule 1
...
- { ... } # egress rule M
@olgch; @kublr
Metadata
podSelector:
matchLabels:
key1: value1
matchExpression:
- key: key2
operator: In # NotIn, Exists, DoesNotExist
values: [val1, val2]
● pod selector is a standard Label Matcher
● podSelector is required
● empty selector matches any pod
● requirements are AND’ed
# for ingress rules
from: [ peer1, ... , peerN ]
# for egress rules
to: [ peer1, ... , peerN ]
# for both ingress and egress
ports: [ port1, ... , portM ]
Pod Selector
Ingress and Egress Rules
ipBlock:
cidr: 10.0.0.0/24
except: [10.24.0.0/16, ...]
namespaceSelector: { ... }
podSelector: { ... }
NetworkPolicy Peer
● peers and ports are OR’ed
● empty or missing field matches all
port: 8000
endPort: 32000
protocol: TCP # UDP, SCTP
NetworkPolicy Port
● protocol defaults to TCP
● endPort is optional
● endPort is beta (on by default) since K8S 1.22
● SCTP is stable since K8S 1.20
● pod and namespace selectors are standard
Label Matchers
● if no namespaceSelector, podSelector
matches policies in the same namespace](https://image.slidesharecdn.com/kubernetesnetworking101-210929134734/85/Kubernetes-Networking-101-9-320.jpg)