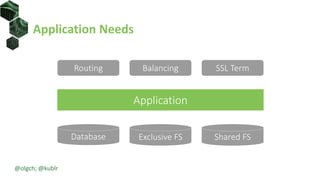
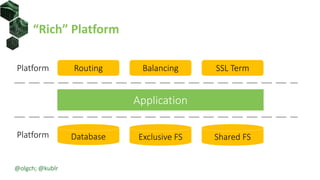
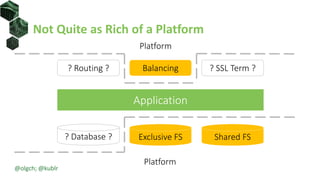
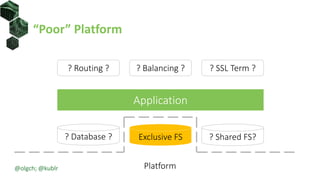
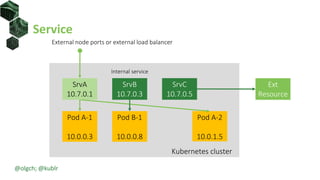
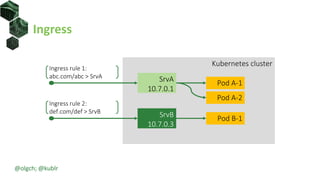
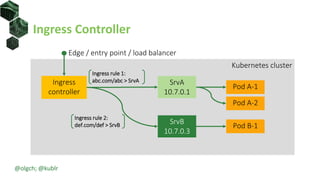
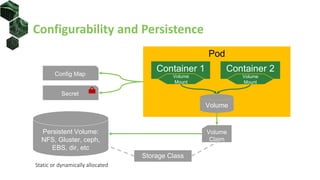
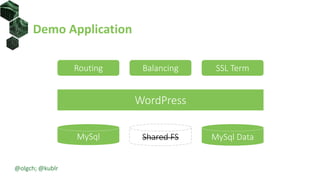
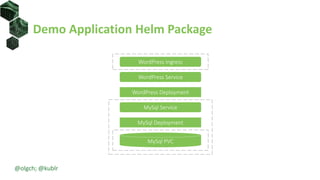
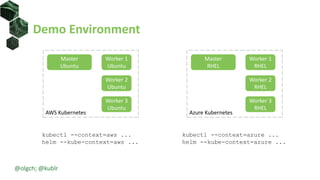
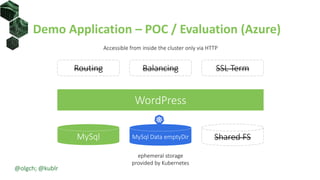
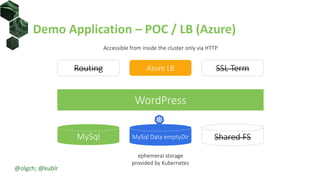
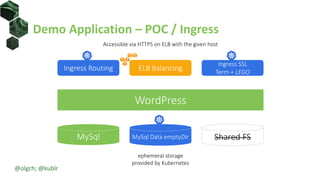
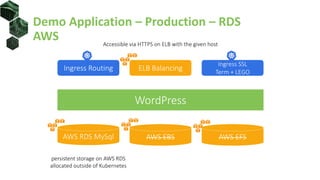
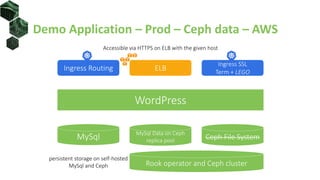
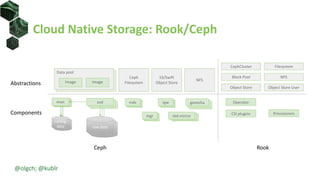
The document discusses best practices for building portable applications using Kubernetes, highlighting the importance of the 12-factor app methodology for dependency management, configuration, and stateless processes. It addresses challenges such as ingress traffic routing and state persistence, while showcasing how Kubernetes provides solutions like configuration templating and abstractions for managing components and storage. Additionally, it compares managed and self-hosted services, emphasizing the considerations necessary for developing cloud-native applications that maintain portability across different environments.