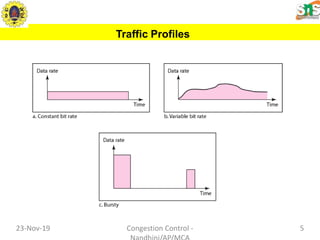
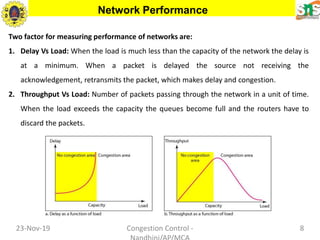
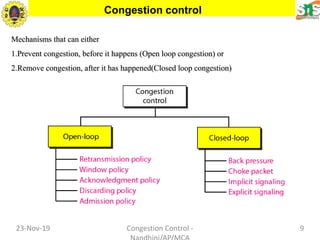
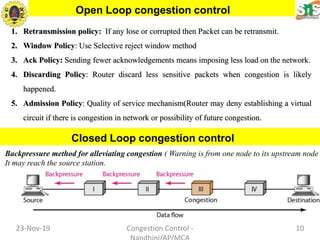
This document discusses congestion control and data traffic. It defines key terms like average data rate, peak data rate, maximum burst size, and effective bandwidth that describe data flow. There are three main types of traffic profiles: constant bit rate, variable bit rate, and bursty data. Congestion occurs when the number of packets sent exceeds network capacity. Congestion control mechanisms aim to prevent or remove congestion using open-loop methods like retransmission policies or closed-loop methods like choke packets or implicit/explicit signaling between nodes. Network performance is measured by delay and throughput as load increases.