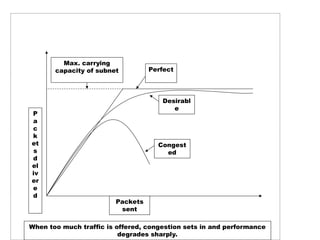
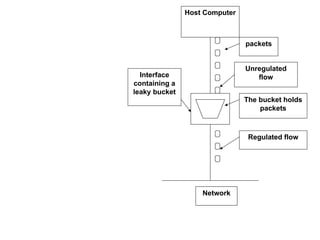
The document discusses congestion control in networks, explaining its causes, differences from flow control, and methods for managing it. Key solutions include open loop and closed loop approaches, as well as traffic shaping techniques like the leaky bucket and token bucket algorithms. The token bucket algorithm allows for more flexible data transmission and prevents data loss, unlike the leaky bucket algorithm, which has stricter output patterns and can discard packets when full.