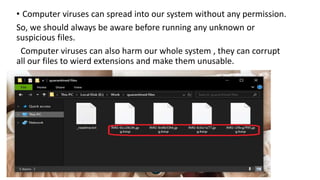
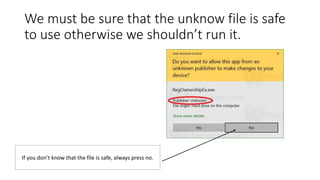
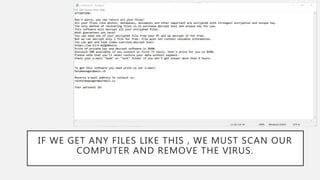
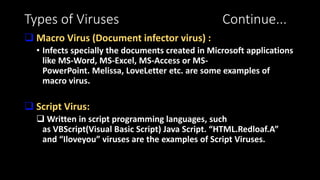
Computer viruses are malicious programs that can spread to computers without permission and disrupt normal functioning. They can corrupt files and make them unusable. It is important to have antivirus software installed like Avast or Kaspersky and to not open unknown or suspicious files. There are different types of viruses like boot sector viruses that infect startup areas and file infecting viruses that affect executable files. Always scan your computer if you receive suspicious files to check for and remove any viruses.