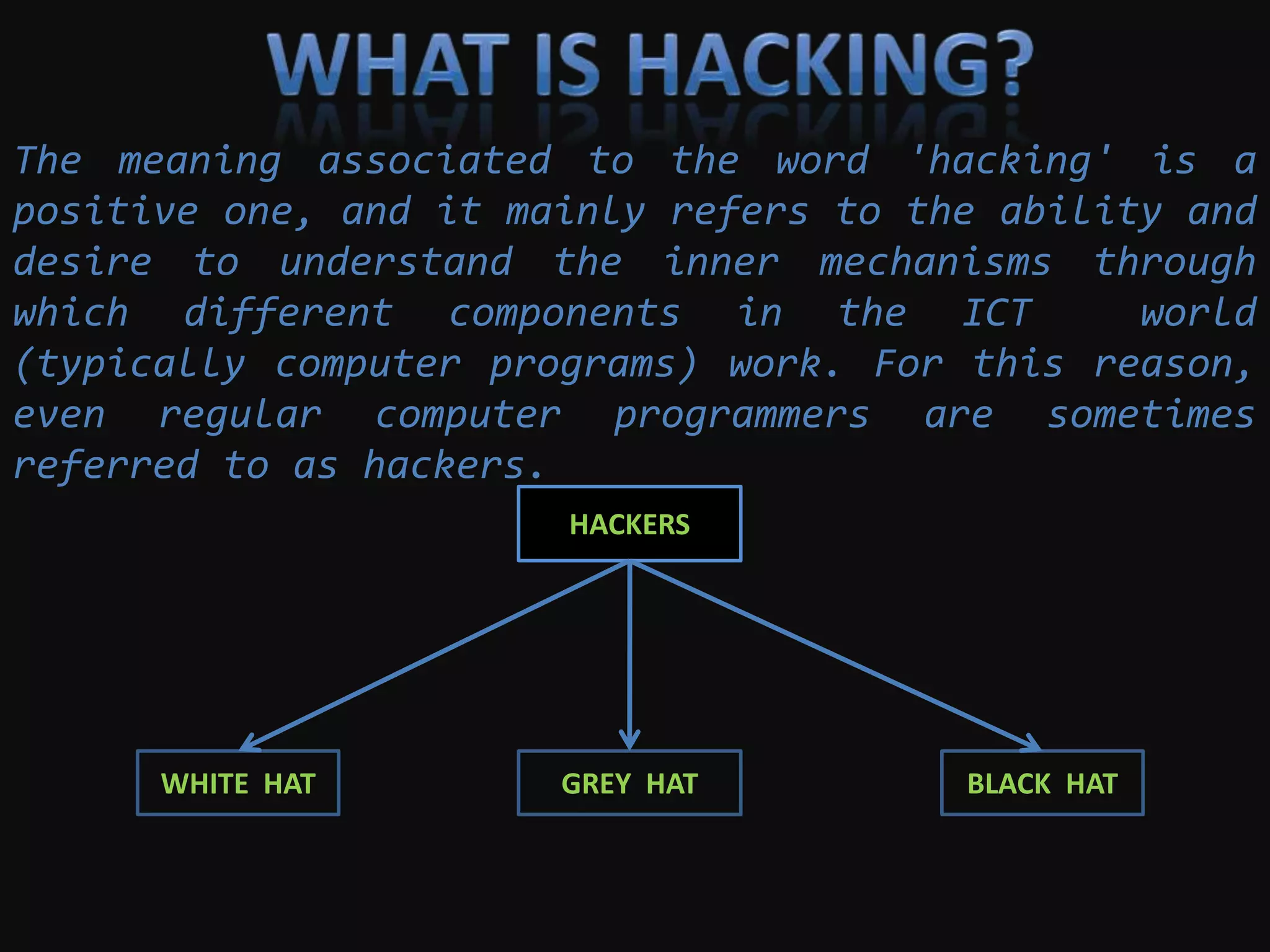
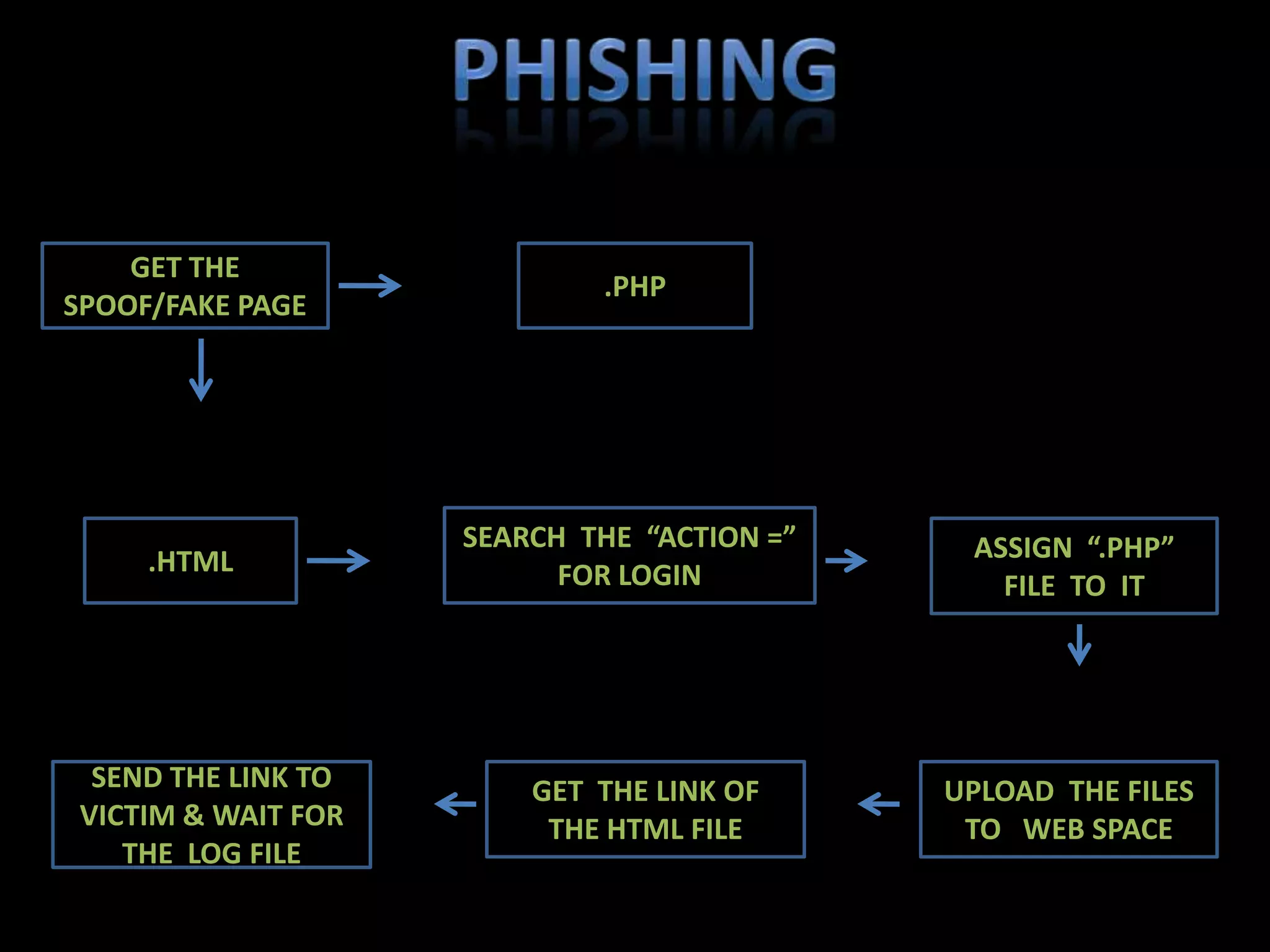
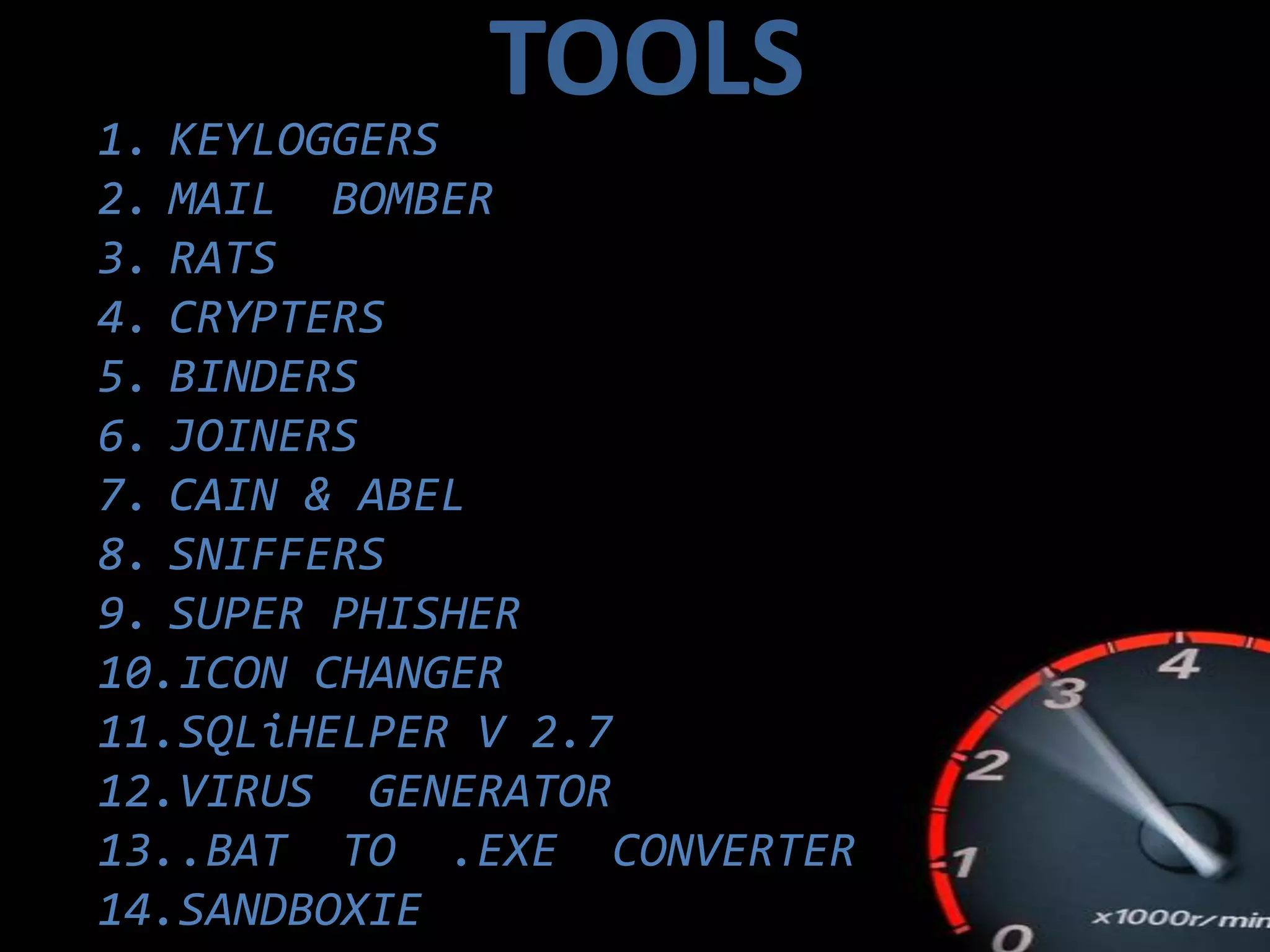
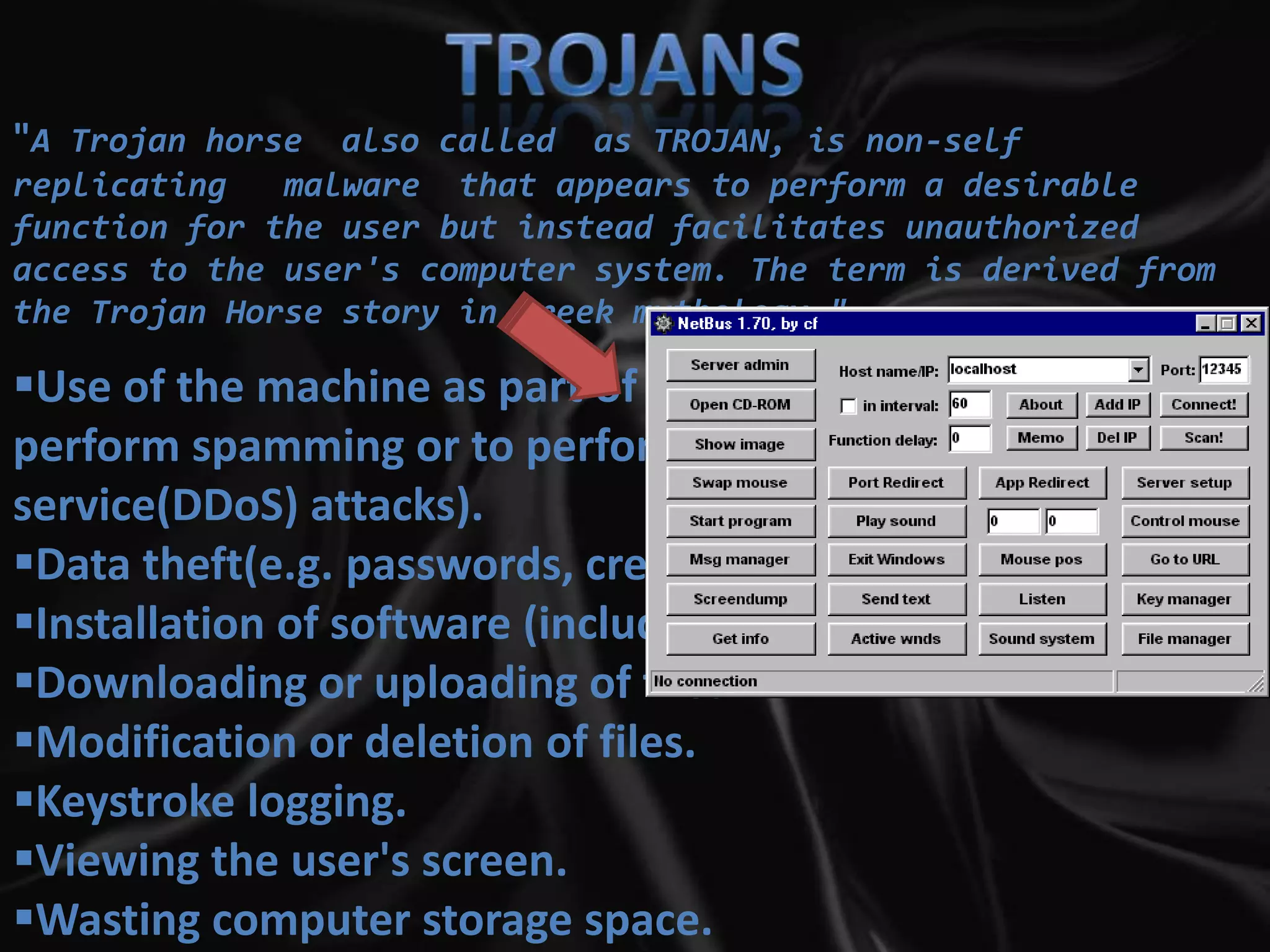
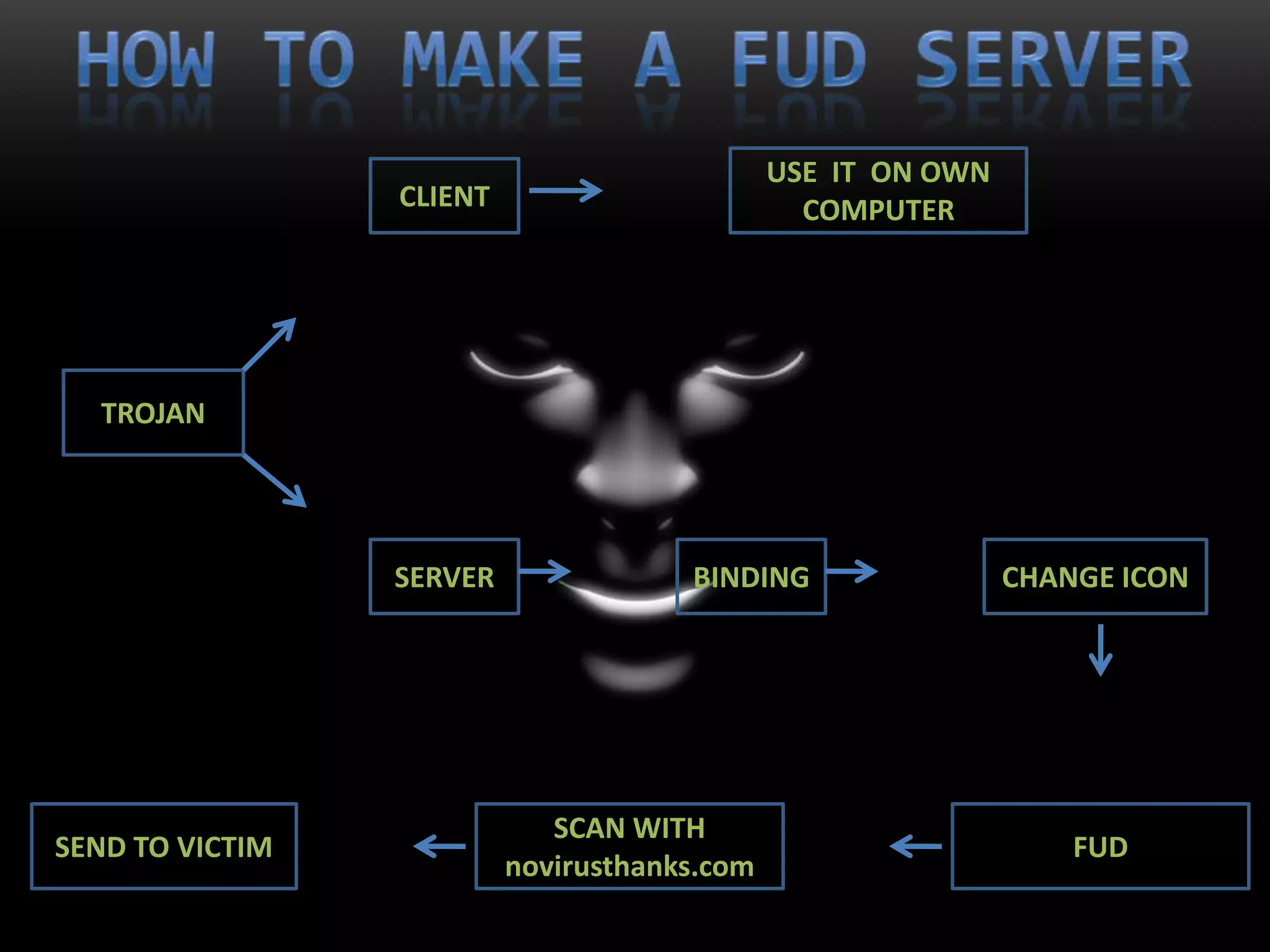
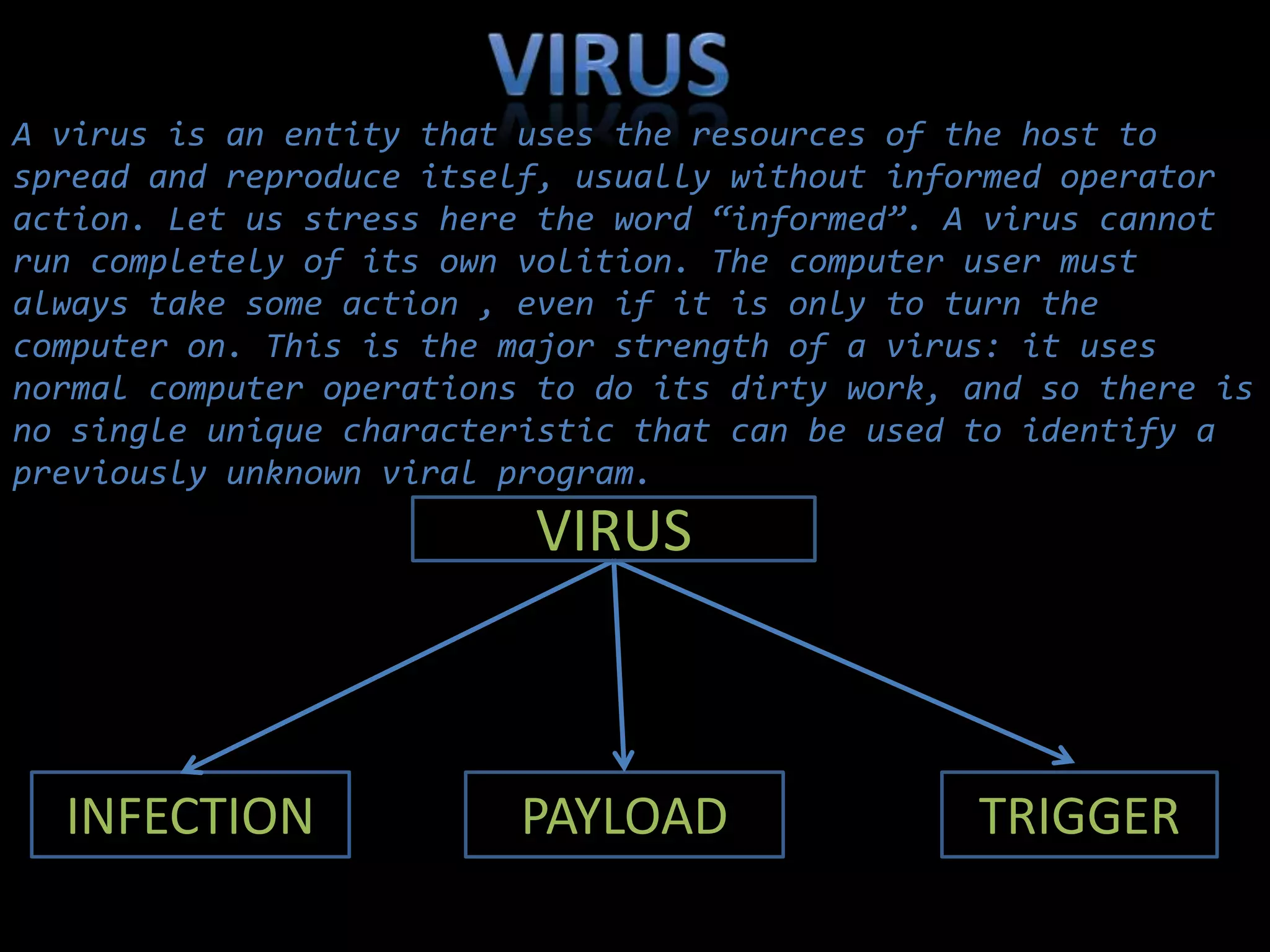
This document summarizes various aspects of computer security including definitions of hacking, types of hackers, common security threats like viruses, trojans, and remote access tools, methods used by hackers like phishing and denial of service attacks, and ways to prevent security breaches like fully undetectable servers and increasing security on one's computer. It outlines topics covered like definitions of computer security and hacking, hacking methods and prevention techniques, common tools used by hackers, details about trojans, viruses, remote access tools, and how to create fully undetectable servers. The document provides an overview of computer security risks and mitigation strategies in under 3 sentences.