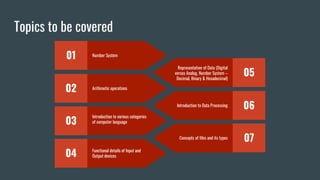
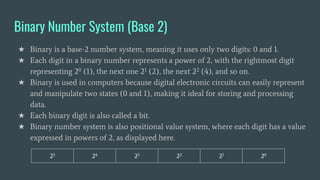
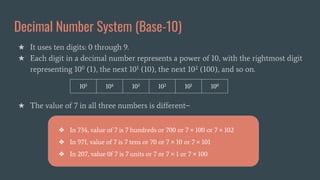
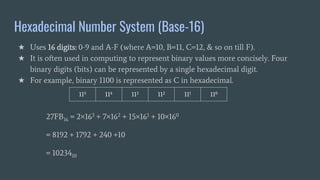
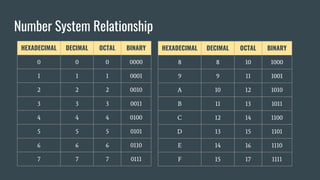
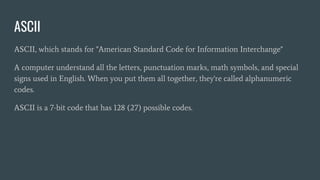
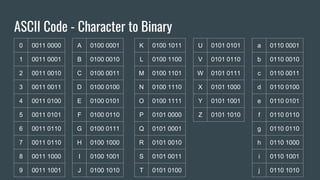
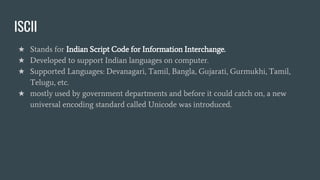
The document provides an overview of computer awareness, covering essential topics such as hardware, software, digital literacy, programming, and emerging technologies. It emphasizes the importance of understanding number systems (binary, octal, decimal, hexadecimal) and includes details on data representation, ASCII, ISCI, and Unicode. Overall, the content highlights the need for computer proficiency in today's digital age to navigate technology effectively and safely.