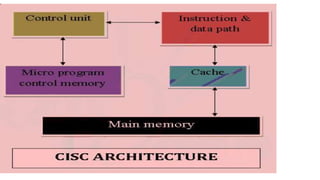
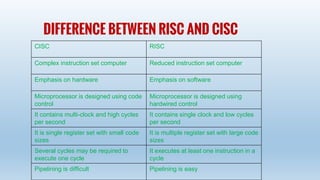
Mr. Abash shah presented on computer architecture. Computer architecture refers to the functionality, organization and implementation of computer systems and includes instruction set architecture design, microarchitecture design, and logic design. The presentation covered the types of computer architectures - RISC and CISC. RISC has advantages like speed and simpler hardware, while CISC has advantages like upward compatibility but is more complex. The differences between RISC and CISC architectures were also outlined.