Comprehensive plans are in place to improve our institutional cyber security
•
0 likes•409 views
Comprehensive plans are in place to improve the institution's cyber security through various measures: 1) Up-skilling all staff, students and visitors on cyber defenses and providing 24/7 online training and support. 2) Senior managers and IT staff routinely monitor internal and external cyber security events to inform best practices and risk management is conducted at central and departmental levels. 3) Clear processes define roles and responsibilities for securely handling incidents, with escalation pathways for major events, and feedback is gathered to improve support processes.
Report
Share
Report
Share
Download to read offline
Recommended
Next-Gen security operation center

Talking about Next-Gen Security Operation Center for IDNIC+APJII as representative from IDSECCONF. People-Centric SOC requires lot of investment on human in terms of quantity and quality, unfortunately, (good) IT security people are getting rare these days. Organisation need to put their investments more on technology, as in Industry 4.0, machines are getting more advanced to support Human on doing continuous and repetitive task.
Moving from “traditional” to next-gen SOC require proper plan, thats what this talk was about.
Cybersecurity trends - What to expect in 2023

Being aware of the trends that are expected to shape the digital landscape is an important step in ensuring the security of your data and online assets.
Amongst others, the webinar covers:
• Top Cyber Trends for 2023
• Cyber Insurance
• Prioritization of Cyber Risk
Presenters:
Colleen Lennox
Colleen Lennox is the Founder of Cyber Job Central, a newly formed job board dedicated to Cybersecurity job openings. Colleen has 25+ years in Technical Recruiting and loves to help other find their next great job!
Madhu Maganti
Madhu is a goal-oriented cybersecurity/IT advisory leader with more than 20 years of comprehensive experience leading high-performance teams with a proven track record of continuous improvement toward objectives. He is highly knowledgeable in both technical and business principles and processes.
Madhu specializes in cybersecurity risk assessments, enterprise risk management, regulatory compliance, Sarbanes-Oxley (SOX) compliance and system and organization controls (SOC) reporting.
Date: January 25, 2023
Tags: ISO, ISO/IEC 27032, Cybersecurity Management
-------------------------------------------------------------------------------
Find out more about ISO training and certification services
Training: https://pecb.com/en/education-and-certification-for-individuals/iso-iec-27032
https://pecb.com/article/cybersecurity-risk-assessment
https://pecb.com/article/a-deeper-understanding-of-cybersecurity
Webinars: https://pecb.com/webinars
Article: https://pecb.com/article
Whitepaper: https://pecb.com/whitepaper
-------------------------------------------------------------------------------
For more information about PECB:
Website: https://pecb.com/
LinkedIn: https://www.linkedin.com/company/pecb/
Facebook: https://www.facebook.com/PECBInternational/
Slideshare: http://www.slideshare.net/PECBCERTIFICATION
YouTube video: https://youtu.be/BAAl_PI9uRc
Why is Cyber Security Important - Importance of Cyber Security - Avantika Uni...

Why is Cyber Security important in today’s digital world? In the present times, everyone and everything is online. So to maintain the privacy, security is needed. Realizing this need, MIT Pune’s Avantika University included cyber security as a chapter in its engineering course. We impart knowledge of cyber security and all other ongoing trends to our students. Avantika University's Engineering College is one of the Top Engineering Colleges in MP, India.
To know more details, visit us at: http://avantikauniversity.edu.in/engineering-colleges/why-is-cyber-security-important-importance-of-cyber-security.php
Cyber Threat Simulation Training

Welcome to Cyber Threat Simulation Training powered by Tonex. Cyber Threat Simulation Training covers standards of cyber threats, progressed cyber fighting and threat simulation standards.
Cyber Threat Simulation Training is splitted into different parts comprising of essential cyber security, progressed cyber security, standards of cyber threat and hands-on threat simulation works out.
Learn about:
Basic cyber threat principles
Principles on threat environment
Principles of cyber simulation and modeling
Cyber threat simulation principles
Web application cyber threat fundamentals
Network and application reconnaissance
Data exfiltration & privilege escalation
Exploit application misconfigurations and more
Firewall and Threat Prevention at work
Tools to model and simulate cyber threat
Tools to monitor attack traffic
Who Should Attend:
Cyber Threat Analysts
Digital Forensic Analysts
Incident Response Team Members
Threat Hunters
Federal Agents
Law Enforcement Officials
Military Officials
Course Modules:
Cyberwarfare and Cyberterrorism
Overview of Global Cyber Threats
Principles of Cyber Threat Simulation
Cyber Threat Intelligence
Simulating Cyber Threats
Incident Detection
Response Threat Simulation
Cyber Threat Simulation Training.Price: $3,999.00 . Length: 3 Days.
Request more info about this Cyber Threat Simulation Training. Call +1-972-665-9786. Visit www.tonex.com/training-courses/cyber-threat-simulation-training/
CHFI v10

CHFI v10 has good coverage on Dark Web, IoT, and Cloud Forensics. Ec-Council took the right decision by upgrading the course from v9 to v10. It was in use for a longer period of time, so it is time to upgrade according to the need for forensics.
The Security Vulnerability Assessment Process & Best Practices

Conducting regular security assessments on the organizational network and computer systems has become a vital part of protecting information-computing assets. Security assessments are a proactive and offensive posture towards information security as compared to the traditional reactive and defensive stance normally implemented with the use of Access Control-Lists (ACLs) and firewalls.
Too effectively conduct a security assessment so it is beneficial to an organization, a proven methodology must be followed so the assessors and assesses are on the same page.
This presentation will evaluate the benefits of credential scanning, scanning in a virtual environment, distributed scanning as well as vulnerability management.
What is cyber resilience?

While some argue that cyber resilience is foundational for managing risk holistically in an increasingly complex world, others deride the concept as little more than the latest buzzword. This presentation provides an overview of what cyber resilience means and how it is being used by governments and corporations across different industries.
Recommended
Next-Gen security operation center

Talking about Next-Gen Security Operation Center for IDNIC+APJII as representative from IDSECCONF. People-Centric SOC requires lot of investment on human in terms of quantity and quality, unfortunately, (good) IT security people are getting rare these days. Organisation need to put their investments more on technology, as in Industry 4.0, machines are getting more advanced to support Human on doing continuous and repetitive task.
Moving from “traditional” to next-gen SOC require proper plan, thats what this talk was about.
Cybersecurity trends - What to expect in 2023

Being aware of the trends that are expected to shape the digital landscape is an important step in ensuring the security of your data and online assets.
Amongst others, the webinar covers:
• Top Cyber Trends for 2023
• Cyber Insurance
• Prioritization of Cyber Risk
Presenters:
Colleen Lennox
Colleen Lennox is the Founder of Cyber Job Central, a newly formed job board dedicated to Cybersecurity job openings. Colleen has 25+ years in Technical Recruiting and loves to help other find their next great job!
Madhu Maganti
Madhu is a goal-oriented cybersecurity/IT advisory leader with more than 20 years of comprehensive experience leading high-performance teams with a proven track record of continuous improvement toward objectives. He is highly knowledgeable in both technical and business principles and processes.
Madhu specializes in cybersecurity risk assessments, enterprise risk management, regulatory compliance, Sarbanes-Oxley (SOX) compliance and system and organization controls (SOC) reporting.
Date: January 25, 2023
Tags: ISO, ISO/IEC 27032, Cybersecurity Management
-------------------------------------------------------------------------------
Find out more about ISO training and certification services
Training: https://pecb.com/en/education-and-certification-for-individuals/iso-iec-27032
https://pecb.com/article/cybersecurity-risk-assessment
https://pecb.com/article/a-deeper-understanding-of-cybersecurity
Webinars: https://pecb.com/webinars
Article: https://pecb.com/article
Whitepaper: https://pecb.com/whitepaper
-------------------------------------------------------------------------------
For more information about PECB:
Website: https://pecb.com/
LinkedIn: https://www.linkedin.com/company/pecb/
Facebook: https://www.facebook.com/PECBInternational/
Slideshare: http://www.slideshare.net/PECBCERTIFICATION
YouTube video: https://youtu.be/BAAl_PI9uRc
Why is Cyber Security Important - Importance of Cyber Security - Avantika Uni...

Why is Cyber Security important in today’s digital world? In the present times, everyone and everything is online. So to maintain the privacy, security is needed. Realizing this need, MIT Pune’s Avantika University included cyber security as a chapter in its engineering course. We impart knowledge of cyber security and all other ongoing trends to our students. Avantika University's Engineering College is one of the Top Engineering Colleges in MP, India.
To know more details, visit us at: http://avantikauniversity.edu.in/engineering-colleges/why-is-cyber-security-important-importance-of-cyber-security.php
Cyber Threat Simulation Training

Welcome to Cyber Threat Simulation Training powered by Tonex. Cyber Threat Simulation Training covers standards of cyber threats, progressed cyber fighting and threat simulation standards.
Cyber Threat Simulation Training is splitted into different parts comprising of essential cyber security, progressed cyber security, standards of cyber threat and hands-on threat simulation works out.
Learn about:
Basic cyber threat principles
Principles on threat environment
Principles of cyber simulation and modeling
Cyber threat simulation principles
Web application cyber threat fundamentals
Network and application reconnaissance
Data exfiltration & privilege escalation
Exploit application misconfigurations and more
Firewall and Threat Prevention at work
Tools to model and simulate cyber threat
Tools to monitor attack traffic
Who Should Attend:
Cyber Threat Analysts
Digital Forensic Analysts
Incident Response Team Members
Threat Hunters
Federal Agents
Law Enforcement Officials
Military Officials
Course Modules:
Cyberwarfare and Cyberterrorism
Overview of Global Cyber Threats
Principles of Cyber Threat Simulation
Cyber Threat Intelligence
Simulating Cyber Threats
Incident Detection
Response Threat Simulation
Cyber Threat Simulation Training.Price: $3,999.00 . Length: 3 Days.
Request more info about this Cyber Threat Simulation Training. Call +1-972-665-9786. Visit www.tonex.com/training-courses/cyber-threat-simulation-training/
CHFI v10

CHFI v10 has good coverage on Dark Web, IoT, and Cloud Forensics. Ec-Council took the right decision by upgrading the course from v9 to v10. It was in use for a longer period of time, so it is time to upgrade according to the need for forensics.
The Security Vulnerability Assessment Process & Best Practices

Conducting regular security assessments on the organizational network and computer systems has become a vital part of protecting information-computing assets. Security assessments are a proactive and offensive posture towards information security as compared to the traditional reactive and defensive stance normally implemented with the use of Access Control-Lists (ACLs) and firewalls.
Too effectively conduct a security assessment so it is beneficial to an organization, a proven methodology must be followed so the assessors and assesses are on the same page.
This presentation will evaluate the benefits of credential scanning, scanning in a virtual environment, distributed scanning as well as vulnerability management.
What is cyber resilience?

While some argue that cyber resilience is foundational for managing risk holistically in an increasingly complex world, others deride the concept as little more than the latest buzzword. This presentation provides an overview of what cyber resilience means and how it is being used by governments and corporations across different industries.
How To Present Cyber Security To Senior Management Complete Deck

This template is useful in presenting cybersecurity plan to higher authority. Cybersecurity officer will present it to top level management. It will help in determining the roles and responsibilities of senior management and executives who are responsible in handling risks. Firm will also optimize its cybersecurity risk framework. Firm will assess the current concerns that are impeding cybersecurity in terms of increase in cybercrimes, data breach and exposure and amount spent on settlements. It will also analyze firm its current cybersecurity framework. Firm will categorize various risk and will assess them on parameters such as risk likelihood and severity. The IT department will also improve their incident handling mechanism. Cybersecurity contingency plan will be initiated by firm. In this plan, firm will build an alternate site for backup maintenance. Backup site selection will be done by keeping certain parameters into consideration such as cost for implementation, duration, location, etc. The other plan essentials include business impact assessment, vital record maintenance, recovery task list maintenance, etc. The template also includes information regarding the role of personnel in terms of role and responsibilities of line managers, senior managers and executives in risk management. It also includes information related to the role of top management in ensuring effective information security governance. The information regarding the budget required for the cybersecurity plan implementation is also provided with staff training cost. https://bit.ly/3iSww5L
NIST Cybersecurity Framework - Mindmap

This post shows the complex NIST Cybersecurity Framework as a Mindmap.It captures the critical components of the NIST Cybersecurity framework which is becoming a defacto standard.
Trends in Information Security

CompTIA’s Trends in Information Security study provides insights into the behaviors, techniques and opportunities with IT security as businesses use new technology.
Cybersecurity Tools | Popular Tools for Cybersecurity Threats | Cybersecurity...

** CyberSecurity Certification Training: https://www.edureka.co/cybersecurity-certification-training **
This Edureka tutorial on "Cybersecurity Tools" gives an introduction to the various tools used in the industry for the purpose of cybersecurity. You get to know different kinds of security tools in today's IT world and how they protect us against cyber threats/attacks. The following tools are discussed in this tutorial:
- BluVector
- Bricata
- Cloud Defender
- Contrast Security
- Digital Guardian
- Intellicta
- Mantix4
- SecBI
Cybersecurity Training Playlist: https://bit.ly/2NqcTQV
What is Cyber Security? | Introduction to Cyber Security | Cyber Security Tra...

** Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training **
This Edureka tutorial on "What is Cyber Security" gives an introduction to the Cyber Security world and talks about its basic concepts. You get to know different kinds of attack in today's IT world and how cybersecurity is the solution to these attacks. Below are the topics covered in this tutorial:
1. Why we need Cyber Security?
2. What is Cyber Security?
3. The CIA Triad
4. Vulnerability, Threat and Risk
5. Cognitive Cyber Security
Cybersecurity Training Playlist: https://bit.ly/2NqcTQV
Cybersecurity Attack Vectors: How to Protect Your Organization

You've seen the headlines. You're beginning to understand the importance of cybersecurity. Where do you begin? It's important to understand the common methods of attack and ways you can begin to protect your organization today. For more information on our cybersecurity education please visit FPOV.com/edu.
Cybersecurity Frameworks | NIST Cybersecurity Framework | Cybersecurity Certi...

** CyberSecurity Certification Training: https://www.edureka.co/cybersecurity-certification-training **
This Edureka tutorial on "Cybersecurity Frameworks" will help you understand why and how the organizations are using the cybersecurity framework to Identify, Protect and Recover from cyber attacks.
Cybersecurity Training Playlist: https://bit.ly/2NqcTQV
DTS Solution - Building a SOC (Security Operations Center)

Building a Security Operations Center - DTS approach.
Advanced persistent threats(APT)

Advanced Persistent Threats (APTs) are a serious concern as they represent a threat to an organization’s intellectual property, financial assets and reputation. In some cases, these threats target critical infrastructure and government institutions, thereby threatening the country’s national security itself.
Cyber Threat Intelligence: Building and maturing an intelligence program that...

Cyber Threat Intelligence: Building and maturing an intelligence program that supports the business, not just the SOC
INCIDENT RESPONSE OVERVIEW

This presentation provides an overview on how to kick start your incident response
Building Security Operation Center

Building Security Operation Center
Denis Batrankov
Solution Architect
NIST Cybersecurity Framework Cross Reference

Consider a logical cross reference or grouping for Cybersecurity Framework subcategories. This could make an assessment easier and more meaningful.
The Cybersecurity Framework identifies categories and subcategories of practice, processes, and activities to be used in a cyber security assessment. But, categories often house unrelated subcategories and subcategories are dependent on other subcategories across various categories.
Cybersecurity Roadmap Development for Executives

Secrets to managing your Duty of Care in an ever- changing world.
How well do you know your risks?
Are you keeping up with your responsibilities to provide Duty of Care?
How well are you prioritising Cybersecurity initiatives?
Liability for Cybersecurity attacks sits with Executives and Board members who may not have the right level of technical security knowledge. This session will outline what practical steps executives can take to implement a Cybersecurity Roadmap that is aligned with its strategic objectives.
Led by Krist Davood, who has spent over 28 years implementing secure mission critical systems for executives. Krist is an expert in protecting the interconnectedness of technology, intellectual property and information systems, as evidenced through his roles at The Good Guys, Court Services Victoria and Schiavello.
The seminar will cover:
• Fiduciary responsibility
• How to efficiently deal with personal liability and the threat of court action
• The role of a Cybersecurity Executive Dashboard and its ability to simplify risk and amplify informed decision making
• How to identify and bridge the gap between your Cybersecurity Compliance Rating and the threat of court action
Bulding Soc In Changing Threat Landscapefinal

my presentation at E-Crime abu dhabi conference about Security operation center Building and measure performance
Industrial control systems cybersecurity.ppt

ICS introduction and concepts, ICS security architecture.
More Related Content
What's hot
How To Present Cyber Security To Senior Management Complete Deck

This template is useful in presenting cybersecurity plan to higher authority. Cybersecurity officer will present it to top level management. It will help in determining the roles and responsibilities of senior management and executives who are responsible in handling risks. Firm will also optimize its cybersecurity risk framework. Firm will assess the current concerns that are impeding cybersecurity in terms of increase in cybercrimes, data breach and exposure and amount spent on settlements. It will also analyze firm its current cybersecurity framework. Firm will categorize various risk and will assess them on parameters such as risk likelihood and severity. The IT department will also improve their incident handling mechanism. Cybersecurity contingency plan will be initiated by firm. In this plan, firm will build an alternate site for backup maintenance. Backup site selection will be done by keeping certain parameters into consideration such as cost for implementation, duration, location, etc. The other plan essentials include business impact assessment, vital record maintenance, recovery task list maintenance, etc. The template also includes information regarding the role of personnel in terms of role and responsibilities of line managers, senior managers and executives in risk management. It also includes information related to the role of top management in ensuring effective information security governance. The information regarding the budget required for the cybersecurity plan implementation is also provided with staff training cost. https://bit.ly/3iSww5L
NIST Cybersecurity Framework - Mindmap

This post shows the complex NIST Cybersecurity Framework as a Mindmap.It captures the critical components of the NIST Cybersecurity framework which is becoming a defacto standard.
Trends in Information Security

CompTIA’s Trends in Information Security study provides insights into the behaviors, techniques and opportunities with IT security as businesses use new technology.
Cybersecurity Tools | Popular Tools for Cybersecurity Threats | Cybersecurity...

** CyberSecurity Certification Training: https://www.edureka.co/cybersecurity-certification-training **
This Edureka tutorial on "Cybersecurity Tools" gives an introduction to the various tools used in the industry for the purpose of cybersecurity. You get to know different kinds of security tools in today's IT world and how they protect us against cyber threats/attacks. The following tools are discussed in this tutorial:
- BluVector
- Bricata
- Cloud Defender
- Contrast Security
- Digital Guardian
- Intellicta
- Mantix4
- SecBI
Cybersecurity Training Playlist: https://bit.ly/2NqcTQV
What is Cyber Security? | Introduction to Cyber Security | Cyber Security Tra...

** Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training **
This Edureka tutorial on "What is Cyber Security" gives an introduction to the Cyber Security world and talks about its basic concepts. You get to know different kinds of attack in today's IT world and how cybersecurity is the solution to these attacks. Below are the topics covered in this tutorial:
1. Why we need Cyber Security?
2. What is Cyber Security?
3. The CIA Triad
4. Vulnerability, Threat and Risk
5. Cognitive Cyber Security
Cybersecurity Training Playlist: https://bit.ly/2NqcTQV
Cybersecurity Attack Vectors: How to Protect Your Organization

You've seen the headlines. You're beginning to understand the importance of cybersecurity. Where do you begin? It's important to understand the common methods of attack and ways you can begin to protect your organization today. For more information on our cybersecurity education please visit FPOV.com/edu.
Cybersecurity Frameworks | NIST Cybersecurity Framework | Cybersecurity Certi...

** CyberSecurity Certification Training: https://www.edureka.co/cybersecurity-certification-training **
This Edureka tutorial on "Cybersecurity Frameworks" will help you understand why and how the organizations are using the cybersecurity framework to Identify, Protect and Recover from cyber attacks.
Cybersecurity Training Playlist: https://bit.ly/2NqcTQV
DTS Solution - Building a SOC (Security Operations Center)

Building a Security Operations Center - DTS approach.
Advanced persistent threats(APT)

Advanced Persistent Threats (APTs) are a serious concern as they represent a threat to an organization’s intellectual property, financial assets and reputation. In some cases, these threats target critical infrastructure and government institutions, thereby threatening the country’s national security itself.
Cyber Threat Intelligence: Building and maturing an intelligence program that...

Cyber Threat Intelligence: Building and maturing an intelligence program that supports the business, not just the SOC
INCIDENT RESPONSE OVERVIEW

This presentation provides an overview on how to kick start your incident response
Building Security Operation Center

Building Security Operation Center
Denis Batrankov
Solution Architect
NIST Cybersecurity Framework Cross Reference

Consider a logical cross reference or grouping for Cybersecurity Framework subcategories. This could make an assessment easier and more meaningful.
The Cybersecurity Framework identifies categories and subcategories of practice, processes, and activities to be used in a cyber security assessment. But, categories often house unrelated subcategories and subcategories are dependent on other subcategories across various categories.
Cybersecurity Roadmap Development for Executives

Secrets to managing your Duty of Care in an ever- changing world.
How well do you know your risks?
Are you keeping up with your responsibilities to provide Duty of Care?
How well are you prioritising Cybersecurity initiatives?
Liability for Cybersecurity attacks sits with Executives and Board members who may not have the right level of technical security knowledge. This session will outline what practical steps executives can take to implement a Cybersecurity Roadmap that is aligned with its strategic objectives.
Led by Krist Davood, who has spent over 28 years implementing secure mission critical systems for executives. Krist is an expert in protecting the interconnectedness of technology, intellectual property and information systems, as evidenced through his roles at The Good Guys, Court Services Victoria and Schiavello.
The seminar will cover:
• Fiduciary responsibility
• How to efficiently deal with personal liability and the threat of court action
• The role of a Cybersecurity Executive Dashboard and its ability to simplify risk and amplify informed decision making
• How to identify and bridge the gap between your Cybersecurity Compliance Rating and the threat of court action
Bulding Soc In Changing Threat Landscapefinal

my presentation at E-Crime abu dhabi conference about Security operation center Building and measure performance
Industrial control systems cybersecurity.ppt

ICS introduction and concepts, ICS security architecture.
What's hot (20)
How To Present Cyber Security To Senior Management Complete Deck

How To Present Cyber Security To Senior Management Complete Deck
Cybersecurity Tools | Popular Tools for Cybersecurity Threats | Cybersecurity...

Cybersecurity Tools | Popular Tools for Cybersecurity Threats | Cybersecurity...
What is Cyber Security? | Introduction to Cyber Security | Cyber Security Tra...

What is Cyber Security? | Introduction to Cyber Security | Cyber Security Tra...
Cybersecurity Attack Vectors: How to Protect Your Organization

Cybersecurity Attack Vectors: How to Protect Your Organization
Cybersecurity Frameworks | NIST Cybersecurity Framework | Cybersecurity Certi...

Cybersecurity Frameworks | NIST Cybersecurity Framework | Cybersecurity Certi...
DTS Solution - Building a SOC (Security Operations Center)

DTS Solution - Building a SOC (Security Operations Center)
Cyber Threat Intelligence: Building and maturing an intelligence program that...

Cyber Threat Intelligence: Building and maturing an intelligence program that...
Similar to Comprehensive plans are in place to improve our institutional cyber security
Why implement a robust cyber security policy?

A presentation from the Jisc security conference 2018, but Dr Ken Thomson, principal and chief executive, Forth Valley College
Empowering Employees for Cyber Resilience: A Guide to Strengthening Your Orga...

This comprehensive guide focuses on empowering employees to contribute to their organization's cybersecurity posture. It outlines the importance of investing in cybersecurity skills and training, implementing strong security controls, understanding incident response plans, monitoring the work environment for threats, and continuously educating employees about cybersecurity best practices. By fostering a security-conscious workforce and encouraging active participation in cybersecurity efforts, organizations can significantly reduce the risk of cyberattacks and build a more robust and resilient defense against potential breaches.
Information Security Analyst- Infosec train

The information has more exceptional value in today's highly competitive world. It helps organizations in many ways. From making accurate decisions to set up strategies to achieve their business goals, organizations rely extensively on the information system.
MCGlobalTech Consulting Service Presentation

MCGlobalTech Consulting Service helps government and business leaders effectively and efficiently manage their security and technology.
chapter 1. Introduction to Information Security 

This training creates the awareness of the security threats facing individuals, business owner’s, and corporations in today’s society and induces a’ plan-protection’ attitude. It enriches individuals, students’, business owners’ and workers’ approach to handling these threats and responding appropriately when these threats occur.
Assuring Digital Strategic Initiatives by 

Mrs Bianca Pasipanodya, the Group ICT executive for First Mutual Group an esteemed speaker at the ISACA Harare Chapter, gives her remarks about the implementation of an effective Information Security Management System” in Zimbabwe.
How does cyber security work.pdf

Cybersecurity works by implementing a combination of strategies, technologies, and practices to protect computer systems, networks, and data from cyber threats. If you want to learn Diploma course in cyber security field, you nust start your career from today. Bytecode Security offers best cyber security course online and offline.
Leaarn more : https://www.bytec0de.com/cybersecurity/
How to make employees aware and responsible towards security of the Company's...

How to make employees aware and responsible towards security of the Company's...CommLab India – Rapid eLearning Solutions
A section of security breaches are caused by employees, whether accidentally or deliberately. To prevent security breaches of any kind, organizations should strengthen and solidify all their security systems and technologies.The Crucial Role of Security Testing Services in Ensuring a Secure and Effici...

In today's digital landscape, organizations face increasing cybersecurity threats that can compromise their valuable assets and disrupt business operations. The digital workforce, comprising remote employees, contractors, and freelancers, relies heavily on digital technologies, making it essential to establish robust security measures. One vital component of a comprehensive security strategy is security testing services. In this blog post, we will explore the crucial role of Security Testing Services in ensuring a secure and efficient digital workforce.
Tech 2 Tech: increasing security posture and threat intelligence sharing

Presentation by John Chapman and Joe Pitt for the Tech 2 Tech event on 31 August 2021
Cyber Safety Awareness Training (Brochure)

Safety, trust and security are core to customer
retention, growth, and the long term
success of every company. While companies
must continually look for new ways to
increase efficiency and productivity, security
of accounts and sensitive customer
information is a top priority. For more info: www.nafcu.org/cyveillance
Similar to Comprehensive plans are in place to improve our institutional cyber security (20)
Best Practices for Security Awareness and Training

Best Practices for Security Awareness and Training
Empowering Employees for Cyber Resilience: A Guide to Strengthening Your Orga...

Empowering Employees for Cyber Resilience: A Guide to Strengthening Your Orga...
Step by-step for risk analysis and management-yaser aljohani

Step by-step for risk analysis and management-yaser aljohani
Step by-step for risk analysis and management-yaser aljohani

Step by-step for risk analysis and management-yaser aljohani
How to make employees aware and responsible towards security of the Company's...

How to make employees aware and responsible towards security of the Company's...
The Crucial Role of Security Testing Services in Ensuring a Secure and Effici...

The Crucial Role of Security Testing Services in Ensuring a Secure and Effici...
Tech 2 Tech: increasing security posture and threat intelligence sharing

Tech 2 Tech: increasing security posture and threat intelligence sharing
Fissea09 mgupta-day3-panel process-program-build-effective-training

Fissea09 mgupta-day3-panel process-program-build-effective-training
Recently uploaded
First Steps with Globus Compute Multi-User Endpoints

In this presentation we will share our experiences around getting started with the Globus Compute multi-user endpoint. Working with the Pharmacology group at the University of Auckland, we have previously written an application using Globus Compute that can offload computationally expensive steps in the researcher's workflows, which they wish to manage from their familiar Windows environments, onto the NeSI (New Zealand eScience Infrastructure) cluster. Some of the challenges we have encountered were that each researcher had to set up and manage their own single-user globus compute endpoint and that the workloads had varying resource requirements (CPUs, memory and wall time) between different runs. We hope that the multi-user endpoint will help to address these challenges and share an update on our progress here.
Innovating Inference - Remote Triggering of Large Language Models on HPC Clus...

Large Language Models (LLMs) are currently the center of attention in the tech world, particularly for their potential to advance research. In this presentation, we'll explore a straightforward and effective method for quickly initiating inference runs on supercomputers using the vLLM tool with Globus Compute, specifically on the Polaris system at ALCF. We'll begin by briefly discussing the popularity and applications of LLMs in various fields. Following this, we will introduce the vLLM tool, and explain how it integrates with Globus Compute to efficiently manage LLM operations on Polaris. Attendees will learn the practical aspects of setting up and remotely triggering LLMs from local machines, focusing on ease of use and efficiency. This talk is ideal for researchers and practitioners looking to leverage the power of LLMs in their work, offering a clear guide to harnessing supercomputing resources for quick and effective LLM inference.
Cracking the code review at SpringIO 2024

Code reviews are vital for ensuring good code quality. They serve as one of our last lines of defense against bugs and subpar code reaching production.
Yet, they often turn into annoying tasks riddled with frustration, hostility, unclear feedback and lack of standards. How can we improve this crucial process?
In this session we will cover:
- The Art of Effective Code Reviews
- Streamlining the Review Process
- Elevating Reviews with Automated Tools
By the end of this presentation, you'll have the knowledge on how to organize and improve your code review proces
Lecture 1 Introduction to games development

Software engineering
Game Development
unity Game Development
Climate Science Flows: Enabling Petabyte-Scale Climate Analysis with the Eart...

The Earth System Grid Federation (ESGF) is a global network of data servers that archives and distributes the planet’s largest collection of Earth system model output for thousands of climate and environmental scientists worldwide. Many of these petabyte-scale data archives are located in proximity to large high-performance computing (HPC) or cloud computing resources, but the primary workflow for data users consists of transferring data, and applying computations on a different system. As a part of the ESGF 2.0 US project (funded by the United States Department of Energy Office of Science), we developed pre-defined data workflows, which can be run on-demand, capable of applying many data reduction and data analysis to the large ESGF data archives, transferring only the resultant analysis (ex. visualizations, smaller data files). In this talk, we will showcase a few of these workflows, highlighting how Globus Flows can be used for petabyte-scale climate analysis.
Top Features to Include in Your Winzo Clone App for Business Growth (4).pptx

Discover the essential features to incorporate in your Winzo clone app to boost business growth, enhance user engagement, and drive revenue. Learn how to create a compelling gaming experience that stands out in the competitive market.
How to Position Your Globus Data Portal for Success Ten Good Practices

Science gateways allow science and engineering communities to access shared data, software, computing services, and instruments. Science gateways have gained a lot of traction in the last twenty years, as evidenced by projects such as the Science Gateways Community Institute (SGCI) and the Center of Excellence on Science Gateways (SGX3) in the US, The Australian Research Data Commons (ARDC) and its platforms in Australia, and the projects around Virtual Research Environments in Europe. A few mature frameworks have evolved with their different strengths and foci and have been taken up by a larger community such as the Globus Data Portal, Hubzero, Tapis, and Galaxy. However, even when gateways are built on successful frameworks, they continue to face the challenges of ongoing maintenance costs and how to meet the ever-expanding needs of the community they serve with enhanced features. It is not uncommon that gateways with compelling use cases are nonetheless unable to get past the prototype phase and become a full production service, or if they do, they don't survive more than a couple of years. While there is no guaranteed pathway to success, it seems likely that for any gateway there is a need for a strong community and/or solid funding streams to create and sustain its success. With over twenty years of examples to draw from, this presentation goes into detail for ten factors common to successful and enduring gateways that effectively serve as best practices for any new or developing gateway.
OpenFOAM solver for Helmholtz equation, helmholtzFoam / helmholtzBubbleFoam

In this slide, we show the simulation example and the way to compile this solver.
In this solver, the Helmholtz equation can be solved by helmholtzFoam. Also, the Helmholtz equation with uniformly dispersed bubbles can be simulated by helmholtzBubbleFoam.
Enterprise Resource Planning System in Telangana

Enterprise Resource Planning System includes various modules that reduce any business's workload. Additionally, it organizes the workflows, which drives towards enhancing productivity. Here are a detailed explanation of the ERP modules. Going through the points will help you understand how the software is changing the work dynamics.
To know more details here: https://blogs.nyggs.com/nyggs/enterprise-resource-planning-erp-system-modules/
APIs for Browser Automation (MoT Meetup 2024)

APIs for Browser Automation:
Selenium, Cypress, Puppeteer, and Playwright. Ministry of Testing Athens. Meetup on the Beach. 30 May 2024.
Launch Your Streaming Platforms in Minutes

The claim of launching a streaming platform in minutes might be a bit of an exaggeration, but there are services that can significantly streamline the process. Here's a breakdown:
Pros of Speedy Streaming Platform Launch Services:
No coding required: These services often use drag-and-drop interfaces or pre-built templates, eliminating the need for programming knowledge.
Faster setup: Compared to building from scratch, these platforms can get you up and running much quicker.
All-in-one solutions: Many services offer features like content management systems (CMS), video players, and monetization tools, reducing the need for multiple integrations.
Things to Consider:
Limited customization: These platforms may offer less flexibility in design and functionality compared to custom-built solutions.
Scalability: As your audience grows, you might need to upgrade to a more robust platform or encounter limitations with the "quick launch" option.
Features: Carefully evaluate which features are included and if they meet your specific needs (e.g., live streaming, subscription options).
Examples of Services for Launching Streaming Platforms:
Muvi [muvi com]
Uscreen [usencreen tv]
Alternatives to Consider:
Existing Streaming platforms: Platforms like YouTube or Twitch might be suitable for basic streaming needs, though monetization options might be limited.
Custom Development: While more time-consuming, custom development offers the most control and flexibility for your platform.
Overall, launching a streaming platform in minutes might not be entirely realistic, but these services can significantly speed up the process compared to building from scratch. Carefully consider your needs and budget when choosing the best option for you.
Text-Summarization-of-Breaking-News-Using-Fine-tuning-BART-Model.pptx

Text summarization of braking news using fine tuning BART model
Introduction to Pygame (Lecture 7 Python Game Development)

Introduction to Pygame (Lecture 7 Python Game Development)
Dominate Social Media with TubeTrivia AI’s Addictive Quiz Videos.pdf

Dominate Social Media with TubeTrivia AI’s Addictive Quiz Videos
https://www.amb-review.com/tubetrivia-ai
Exclusive Features:
AI-Powered Questions,
Wide Range of Categories,
Adaptive Difficulty,
User-Friendly Interface,
Multiplayer Mode,
Regular Updates.
#TubeTriviaAI
#QuizVideoMagic
#ViralQuizVideos
#AIQuizGenerator
#EngageExciteExplode
#MarketingRevolution
#BoostYourTraffic
#SocialMediaSuccess
#AIContentCreation
#UnlimitedTraffic
Developing Distributed High-performance Computing Capabilities of an Open Sci...

COVID-19 had an unprecedented impact on scientific collaboration. The pandemic and its broad response from the scientific community has forged new relationships among public health practitioners, mathematical modelers, and scientific computing specialists, while revealing critical gaps in exploiting advanced computing systems to support urgent decision making. Informed by our team’s work in applying high-performance computing in support of public health decision makers during the COVID-19 pandemic, we present how Globus technologies are enabling the development of an open science platform for robust epidemic analysis, with the goal of collaborative, secure, distributed, on-demand, and fast time-to-solution analyses to support public health.
Vitthal Shirke Java Microservices Resume.pdf

Software Engineering, Software Consulting, Tech Lead, Spring Boot, Spring Cloud, Spring Core, Spring JDBC, Spring Transaction, Spring MVC, OpenShift Cloud Platform, Kafka, REST, SOAP, LLD & HLD.
Navigating the Metaverse: A Journey into Virtual Evolution"

Join us for an exploration of the Metaverse's evolution, where innovation meets imagination. Discover new dimensions of virtual events, engage with thought-provoking discussions, and witness the transformative power of digital realms."
Top 7 Unique WhatsApp API Benefits | Saudi Arabia

Discover the transformative power of the WhatsApp API in our latest SlideShare presentation, "Top 7 Unique WhatsApp API Benefits." In today's fast-paced digital era, effective communication is crucial for both personal and professional success. Whether you're a small business looking to enhance customer interactions or an individual seeking seamless communication with loved ones, the WhatsApp API offers robust capabilities that can significantly elevate your experience.
In this presentation, we delve into the top 7 distinctive benefits of the WhatsApp API, provided by the leading WhatsApp API service provider in Saudi Arabia. Learn how to streamline customer support, automate notifications, leverage rich media messaging, run scalable marketing campaigns, integrate secure payments, synchronize with CRM systems, and ensure enhanced security and privacy.
Prosigns: Transforming Business with Tailored Technology Solutions

Unlocking Business Potential: Tailored Technology Solutions by Prosigns
Discover how Prosigns, a leading technology solutions provider, partners with businesses to drive innovation and success. Our presentation showcases our comprehensive range of services, including custom software development, web and mobile app development, AI & ML solutions, blockchain integration, DevOps services, and Microsoft Dynamics 365 support.
Custom Software Development: Prosigns specializes in creating bespoke software solutions that cater to your unique business needs. Our team of experts works closely with you to understand your requirements and deliver tailor-made software that enhances efficiency and drives growth.
Web and Mobile App Development: From responsive websites to intuitive mobile applications, Prosigns develops cutting-edge solutions that engage users and deliver seamless experiences across devices.
AI & ML Solutions: Harnessing the power of Artificial Intelligence and Machine Learning, Prosigns provides smart solutions that automate processes, provide valuable insights, and drive informed decision-making.
Blockchain Integration: Prosigns offers comprehensive blockchain solutions, including development, integration, and consulting services, enabling businesses to leverage blockchain technology for enhanced security, transparency, and efficiency.
DevOps Services: Prosigns' DevOps services streamline development and operations processes, ensuring faster and more reliable software delivery through automation and continuous integration.
Microsoft Dynamics 365 Support: Prosigns provides comprehensive support and maintenance services for Microsoft Dynamics 365, ensuring your system is always up-to-date, secure, and running smoothly.
Learn how our collaborative approach and dedication to excellence help businesses achieve their goals and stay ahead in today's digital landscape. From concept to deployment, Prosigns is your trusted partner for transforming ideas into reality and unlocking the full potential of your business.
Join us on a journey of innovation and growth. Let's partner for success with Prosigns.
Recently uploaded (20)
First Steps with Globus Compute Multi-User Endpoints

First Steps with Globus Compute Multi-User Endpoints
Innovating Inference - Remote Triggering of Large Language Models on HPC Clus...

Innovating Inference - Remote Triggering of Large Language Models on HPC Clus...
Climate Science Flows: Enabling Petabyte-Scale Climate Analysis with the Eart...

Climate Science Flows: Enabling Petabyte-Scale Climate Analysis with the Eart...
Top Features to Include in Your Winzo Clone App for Business Growth (4).pptx

Top Features to Include in Your Winzo Clone App for Business Growth (4).pptx
How to Position Your Globus Data Portal for Success Ten Good Practices

How to Position Your Globus Data Portal for Success Ten Good Practices
OpenFOAM solver for Helmholtz equation, helmholtzFoam / helmholtzBubbleFoam

OpenFOAM solver for Helmholtz equation, helmholtzFoam / helmholtzBubbleFoam
Text-Summarization-of-Breaking-News-Using-Fine-tuning-BART-Model.pptx

Text-Summarization-of-Breaking-News-Using-Fine-tuning-BART-Model.pptx
Introduction to Pygame (Lecture 7 Python Game Development)

Introduction to Pygame (Lecture 7 Python Game Development)
Dominate Social Media with TubeTrivia AI’s Addictive Quiz Videos.pdf

Dominate Social Media with TubeTrivia AI’s Addictive Quiz Videos.pdf
Developing Distributed High-performance Computing Capabilities of an Open Sci...

Developing Distributed High-performance Computing Capabilities of an Open Sci...
Navigating the Metaverse: A Journey into Virtual Evolution"

Navigating the Metaverse: A Journey into Virtual Evolution"
Prosigns: Transforming Business with Tailored Technology Solutions

Prosigns: Transforming Business with Tailored Technology Solutions
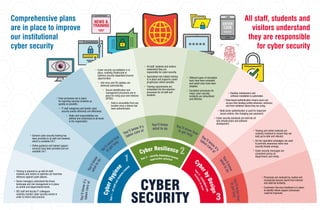
Comprehensive plans are in place to improve our institutional cyber security
- 1. • Training is planned to up-skill all staff, students and visitors to optimise our front-line defences against cyber-attacks. • Senior managers understand the threat landscape and risk management is in place at central and departmental levels. • ISD staff and faculty IT colleagues routinely monitor cyber security events in order to inform best practice. • Processes are reviewed by routine and incorporate lessons learnt from internal and external incidents. • Customers Services feedback is in place to identify where support processes could be improved. • Training and online materials are routinely reviewed to ensure they are kept up-to-date and relevant. • Ad hoc specialist campaigns are used to promote awareness when new security threats emerge. • Cyber security messages are consistent across all departments and media. • All staff, students and visitors understand they are responsible for cyber security. • Specialised role-related training is in place and supports career progression where sensible. • Training requirements are embedded into the induction processes for all staff and students. • Different types of simulation tests have been evaluated and useful ones have been adopted. • Escalation processes for major cyber security incidents are streamlined and effective. • General cyber security training has been provided to all staff and students which is available 24/7. • Online guidance and trained support services have been provided and are available 24/7. • Clear processes are in place for reporting security incidents as quickly as possible. • IT staff categorise and handle cyber security events efficiently and effectively. • Roles and responsibilities are defined and understood at all levels in the organisation. CYBER SECURITY 1 2 3 Y o u ’ l l k n o w i t ’ s Y o u ’ l l k n o w Y o u ’ll know how You’ll know it’s You’ll know You’ll know how You’ll know i t ’ s Y o u ’ l l k n o w Y o u ’ l l k n o w h o w t a k e n c a r e o f w h a t t o d o t o get help taken care of what to do to get help taken care o f w h a t t o d o t o g e t h e l p opportunities optimised b u s i n e s s a s u s u a l Y e a r 1 – a l l s t a f f a n d s t u d e n t s t r ained Year 2 – security dependent income Y e a r 3 – e m b e d d e d i n t o • Cyber security accreditation is in place, enabling Strathclyde to optimise security dependent income opportunities. • Anti-virus and OS updates are delivered automatically. • Secure identification and management processes are in place for bring-your-own-devices (BYOD). • Data is accessible from any location once a device has been authenticated. • Desktop maintenance and software installation is automated. Comprehensive plans are in place to improve our institutional cyber security All staff, students and visitors understand they are responsible for cyber security • Role-based authentication means users can access their desktop profile whenever, wherever, and from whatever device they are using. • Multi-factor authentication is used for important secure actions, like changing your password. • Cyber security standards are built into all new infrastructure and software development. 3 C y b e r H y g i e n e Cyber Resilience Cy b e r b y D e s i g n
- 2. Comprehensive plans are in place to improve our institutional cyber security All staff, students and visitors understand they are responsible for cyber security 1 • Senior managers understand the threat landscape and risk management is in place at central and departmental levels. • All IT staff understand the threat landscape and routinely contribute to risk assessments and management. • Comprehensive plans are in place to up-skill all staff, students and visitors to optimise our front-line defences against cyber-attacks. • ISD staff work with faculty IT colleagues to routinely monitor cyber security events, both internally and externally, in order to inform best practice. • Comprehensive plans are in place to improve our institutional cyber security. • General cyber security training has been provided to all staff and students which is available 24/7. • Online guidance and trained support services have been provided and are available 24/7. • Lightweight awareness and training has been provided for visitors and 3rd parties. • ISD Cyber Security Team disseminate ad hoc messages relating to end-user cyber security practice. • Clear processes are in place for reporting security incidents (and/or events?) as quickly as possible. • IT staff categorise and handle cyber security events efficiently and effectively. • Escalation processes for major cyber security incidents are in place and documented. • Roles and responsibilities are defined and understood at all levels in the organisation. Y o u ’ l l k n o w i t’s You’ll know what Yo u ’ l l k n o w h o w t a k e n c a r e of to do t o g e t h e l p Cyber Hygiene Year 1 – all staff and students trained
- 3. Comprehensive plans are in place to improve our institutional cyber security All staff, students and visitors understand they are responsible for cyber security 2 • Cyber security accreditation is in place, enabling Strathclyde to optimise security dependent income opportunities. • Secure identification and management processes are in place for bring-your-own-devices (BYOD). • Data is accessible from any location once a device has been authenticated. • Anti-virus and OS updates are delivered automatically. • Apps are installed automatically from a single catalogue. • Management information drawn from the app catalogue is used to define role-based standard build profiles and optimise software license costs. • Robust processes are in place to support changes in role ensuring that end-users can access data when, where and for the duration they need to as quickly as possible. • Processes for desktop management have been reviewed and consolidated to achieve standardisation where sensible. • All staff, students and visitors understand they are responsible for cyber security. • Specialised role-related training is in place and supports career progression where sensible. • Training requirements are understood and driven by policy. • Training requirements are embedded into the induction processes for all staff and students. • Training materials and online guidance have been optimised to reflect feedback from Year 1. • Different types of simulation tests have been evaluated anduseful ones have been adopted. • Escalation proces ses for major cyber security incidents are efficient and effective. • Processes are in place for raising awareness of lessons to be learnt from breaches reported in the news. Y o u ’ l l k n o w i t’s You’ll know what Yo u ’ l l k n o w h o w t a k e n c a r e of to do t o g e t h e l p Cyber Resilience Year 2 – security dependent income opportunities optimised
- 4. Comprehensive plans are in place to improve our institutional cyber security All staff, students and visitors understand they are responsible for cyber security • Training and online materials are routinely reviewed to ensure they are kept up-to-date and relevant. • A network of departmental contacts liaises with ISD Cyber Security Team to escalate concerns, manage training and disseminate key information updates about cyber security practice. • Ad hoc specialist campaigns are used to promoteawareness when new security threats emerge. • Refresher training requirements are understood and driven by policy. • Cyber security messages are consistent across all departments and media. • Processes are reviewed by routine and incorporate lessons learnt from internal and external incidents. • Customers Services feedback is in place to identify where support processes could be improved. Y o u ’ l l k n o w i t’s You’ll know what Yo u ’ l l k n o w h o w t a k e n c a r e of to do t o g e t h e l p 3 • Desktop maintenance and software installation is automated so admin rights have been restricted to user accounts with specialist requirements (VIP). • Devices are a portal to access and work with data – not the place where data is stored. • Role-based standard build profiles that automatically deliver user-related software and services are in place. • Role-based authentication is in place so that end-users can access their standard build profile whenever, wherever, and from whatever device they log into. • Multi-factor authentication is in place for important secure actions, like changing your password. • Agreed cyber security standards are built into all new infrastructure and software development. • The threat landscape is routinely reviewed and the risk management of emerging issues is built into the University planning round. Cyber by Design Year 3 – embedded into business as usual