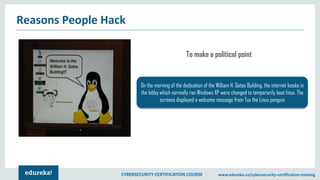
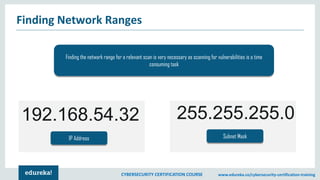
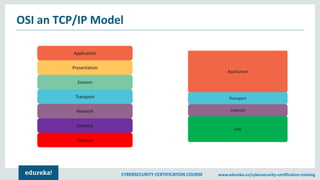
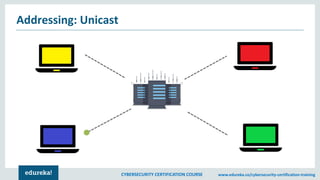
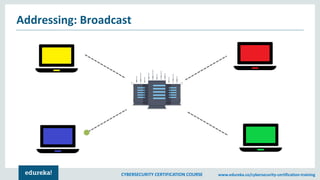
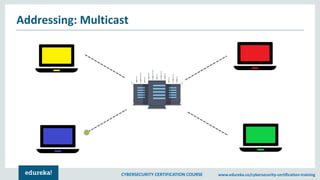
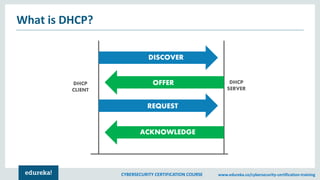
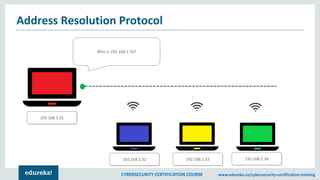
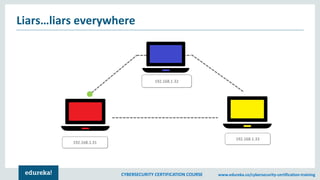
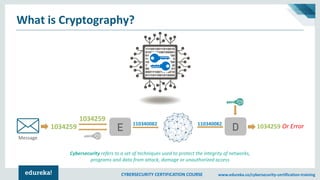
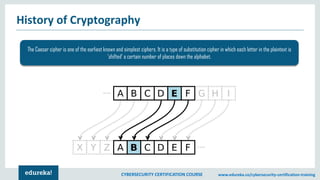
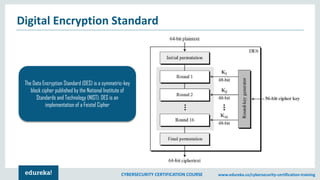
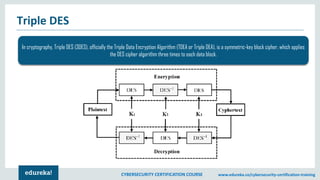
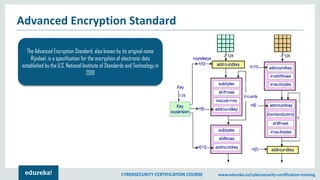
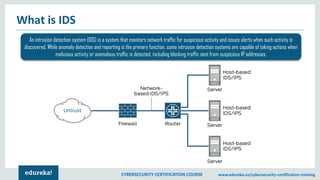
The document provides an extensive overview of a cybersecurity certification course covering fundamental topics such as penetration testing, network scanning, and cryptography. It discusses the history of hacking, types of hackers, and necessary skills and tools for cybersecurity professionals. The course also highlights practical methods for assessing security vulnerabilities and techniques used by hackers, as well as various types of attacks and defensive strategies.